Compare commits
219 Commits
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
4c1e4fef7a | ||
|
|
ddd4824567 | ||
|
|
22bb143820 | ||
|
|
78b918087e | ||
|
|
91ce709d7b | ||
|
|
214ec0c5a5 | ||
|
|
0cb9254e63 | ||
|
|
4bbb339844 | ||
|
|
92b081c076 | ||
|
|
32ab0267fb | ||
|
|
8a0f190474 | ||
|
|
a189a4c754 | ||
|
|
b7b765c16e | ||
|
|
7713c6c21d | ||
|
|
c49184dcb1 | ||
|
|
fc3803991a | ||
|
|
f6011543c0 | ||
|
|
7390bb58c5 | ||
|
|
81482b47f4 | ||
|
|
6cb1dcaa43 | ||
|
|
78e4a4899c | ||
|
|
d15997cca0 | ||
|
|
1558f4ffe4 | ||
|
|
764cca73d1 | ||
|
|
1757eb5bec | ||
|
|
6cfac57162 | ||
|
|
d36d330244 | ||
|
|
4203de6d3f | ||
|
|
098e3c709a | ||
|
|
1a8e151efb | ||
|
|
6c8d22d396 | ||
|
|
a0ee1d886a | ||
|
|
bf6f1625ec | ||
|
|
3271377b7e | ||
|
|
f36bb65b45 | ||
|
|
c722982c39 | ||
|
|
e1109fff15 | ||
|
|
59c6567ff3 | ||
|
|
61f6901767 | ||
|
|
8277c80860 | ||
|
|
4093ba169c | ||
|
|
e3a9d253f7 | ||
|
|
80c67c8aa8 | ||
|
|
421969c3da | ||
|
|
e15b79750b | ||
|
|
37abe596c7 | ||
|
|
e6b44e1461 | ||
|
|
b9cb961da6 | ||
|
|
55c4b777fb | ||
|
|
2231727adb | ||
|
|
0a7e29d92f | ||
|
|
a105a42519 | ||
|
|
d20c2c786b | ||
|
|
14abed44a5 | ||
|
|
65fee64132 | ||
|
|
348688b5ce | ||
|
|
0cb84fc531 | ||
|
|
8a36c459d5 | ||
|
|
c7414ab070 | ||
|
|
d16f9e7ad8 | ||
|
|
3cbd2ed013 | ||
|
|
398f518b2f | ||
|
|
97a62def11 | ||
|
|
7ed49126a4 | ||
|
|
d976a34705 | ||
|
|
8b01c71819 | ||
|
|
1ee5e368f6 | ||
|
|
8fc71aae66 | ||
|
|
0589cc2f0c | ||
|
|
931a66498f | ||
|
|
8ec0a0289a | ||
|
|
2d8ce475f8 | ||
|
|
f8766722d4 | ||
|
|
1319e0b17b | ||
|
|
5e17bf0736 | ||
|
|
ca50bddc56 | ||
|
|
c78fc583b0 | ||
|
|
04cafc4181 | ||
|
|
f8300fa587 | ||
|
|
407ca567f1 | ||
|
|
320fd5c2dd | ||
|
|
e4c616245a | ||
|
|
5986130dfa | ||
|
|
19610479bd | ||
|
|
e3d2151bad | ||
|
|
89d205e946 | ||
|
|
15d13af7d5 | ||
|
|
3df8ed13a4 | ||
|
|
5a4a364250 | ||
|
|
00bee04c2c | ||
|
|
4475e8c24c | ||
|
|
5a49987338 | ||
|
|
76f1f1dcf3 | ||
|
|
0175cfbfb6 | ||
|
|
48483a5c99 | ||
|
|
71e4cc9413 | ||
|
|
a00c0117a2 | ||
|
|
c1bc81c664 | ||
|
|
1b7ef30a50 | ||
|
|
efad2b96db | ||
|
|
56a200499e | ||
|
|
1c58f1d623 | ||
|
|
6cdd56e22f | ||
|
|
53acb847bc | ||
|
|
2b006457c7 | ||
|
|
fbc1672e3d | ||
|
|
542123ce04 | ||
|
|
59eb7f7935 | ||
|
|
74482d6e2c | ||
|
|
529ac2f778 | ||
|
|
b73c3228e4 | ||
|
|
26f7c1f9d1 | ||
|
|
f078232499 | ||
|
|
8cd91f6df3 | ||
|
|
5670c0f975 | ||
|
|
99d4177e89 | ||
|
|
d07b1c86be | ||
|
|
fe494c52b1 | ||
|
|
bc50328006 | ||
|
|
90afe204b1 | ||
|
|
d981b77ed7 | ||
|
|
541a9a55b5 | ||
|
|
cd3fc15bcb | ||
|
|
4e50038b41 | ||
|
|
a8354ee38f | ||
|
|
c4907c8ce5 | ||
|
|
3c3c680b00 | ||
|
|
3a32f45334 | ||
|
|
8e1843f90b | ||
|
|
dc01de98dc | ||
|
|
971061d231 | ||
|
|
d04dd831e4 | ||
|
|
8dcfda9787 | ||
|
|
c938021bef | ||
|
|
3fcf0fb72a | ||
|
|
e99406fbe4 | ||
|
|
60073be993 | ||
|
|
d3df4c7020 | ||
|
|
adce92e312 | ||
|
|
4973545fe1 | ||
|
|
8425c97102 | ||
|
|
1876b8bdc7 | ||
|
|
99ff3a8e45 | ||
|
|
cae251905c | ||
|
|
f738ce90e0 | ||
|
|
2f2bb20550 | ||
|
|
591ede0507 | ||
|
|
09665fead3 | ||
|
|
60ee2f1c2b | ||
|
|
d6d8197869 | ||
|
|
b1da42b543 | ||
|
|
e874550d29 | ||
|
|
6cd9657446 | ||
|
|
2790c613aa | ||
|
|
7b868bc60b | ||
|
|
c1b3511c06 | ||
|
|
1e3c859ae0 | ||
|
|
faab67800f | ||
|
|
7f9d92cbe9 | ||
|
|
4e287a0231 | ||
|
|
8c9c331d7e | ||
|
|
37ce54051e | ||
|
|
f31b047671 | ||
|
|
aaff616332 | ||
|
|
cfc1b73c74 | ||
|
|
0d2967423b | ||
|
|
cb3681ffdd | ||
|
|
4c343c6f34 | ||
|
|
ff158add1f | ||
|
|
2c64cd5cce | ||
|
|
c43ab28fb0 | ||
|
|
dd00e1f55a | ||
|
|
2b3acee97c | ||
|
|
d96558c3df | ||
|
|
b8db557ffe | ||
|
|
300256b196 | ||
|
|
7ba1b316f7 | ||
|
|
822d41e885 | ||
|
|
0253572975 | ||
|
|
0328c1de81 | ||
|
|
c6ee9dedb9 | ||
|
|
88136811b9 | ||
|
|
7c816d0822 | ||
|
|
a5fe62e502 | ||
|
|
892be42988 | ||
|
|
c0eb98c3f9 | ||
|
|
1ddbd0aa4e | ||
|
|
4f1e505a7a | ||
|
|
dcec804681 | ||
|
|
a127f46a06 | ||
|
|
c8d277c51d | ||
|
|
42477d6893 | ||
|
|
4c1fb826be | ||
|
|
a0c29d1174 | ||
|
|
2f0b340fe0 | ||
|
|
cbe242bb94 | ||
|
|
a088c6dbd3 | ||
|
|
036aba2420 | ||
|
|
60269c7777 | ||
|
|
e90f561584 | ||
|
|
4bd18c1386 | ||
|
|
fe51185f74 | ||
|
|
a35395bd51 | ||
|
|
f1225b1ff3 | ||
|
|
63d727d5c5 | ||
|
|
46864ee23a | ||
|
|
46728d8bc3 | ||
|
|
daa9a7c012 | ||
|
|
0f595b8cbf | ||
|
|
26b001a5fc | ||
|
|
3704d2520d | ||
|
|
41e89605f0 | ||
|
|
065ea59114 | ||
|
|
64bb2ed101 | ||
|
|
c48c73909d | ||
|
|
68d113f335 | ||
|
|
8bb66b53e0 | ||
|
|
84c36f1789 | ||
|
|
2214c1dee3 |
5
.github/ISSUE_TEMPLATE/bug_report.md
vendored
@@ -28,6 +28,11 @@ A clear and concise description of what you expected to happen.
|
||||
- Protocol used
|
||||
- Remote server version and name
|
||||
|
||||
## Log
|
||||
|
||||
Report the snippet of the log file containing the unexpected behaviour.
|
||||
If there is any information you consider to be confidential, shadow it.
|
||||
|
||||
## Additional information
|
||||
|
||||
Add any other context about the problem here.
|
||||
|
||||
23
.github/ISSUE_TEMPLATE/security.md
vendored
Normal file
@@ -0,0 +1,23 @@
|
||||
---
|
||||
name: Security report
|
||||
about: Create a report of a security vulnerability
|
||||
title: "[SECURITY] - ISSUE_TITLE"
|
||||
labels: security
|
||||
assignees: veeso
|
||||
|
||||
---
|
||||
|
||||
## Description
|
||||
|
||||
Severity:
|
||||
|
||||
- [ ] **critical**
|
||||
- [ ] high
|
||||
- [ ] medium
|
||||
- [ ] low
|
||||
|
||||
A clear and concise description of the security vulnerability.
|
||||
|
||||
## Additional information
|
||||
|
||||
Add any other context about the problem here.
|
||||
6
.github/PULL_REQUEST_TEMPLATE.md
vendored
@@ -32,3 +32,9 @@ Please select relevant options.
|
||||
- [ ] I have introduced no new *C-bindings*
|
||||
- [ ] The changes I've made are Windows, MacOS, UNIX, Linux compatible (or I've handled them using `cfg target_os`)
|
||||
- [ ] I increased or maintained the code coverage for the project, compared to the previous commit
|
||||
|
||||
## Acceptance tests
|
||||
|
||||
wait for a *project maintainer* to fulfill this section...
|
||||
|
||||
- [ ] regression test: ...
|
||||
|
||||
15
.github/actions-rs/grcov.yml
vendored
Normal file
@@ -0,0 +1,15 @@
|
||||
branch: false
|
||||
ignore-not-existing: true
|
||||
llvm: true
|
||||
output-type: lcov
|
||||
ignore:
|
||||
- "/*"
|
||||
- "C:/*"
|
||||
- "../*"
|
||||
- src/main.rs
|
||||
- src/lib.rs
|
||||
- src/activity_manager.rs
|
||||
- src/support.rs
|
||||
- "src/ui/activities/*"
|
||||
- src/ui/context.rs
|
||||
- src/ui/input.rs
|
||||
21
.github/workflows/aur-pub.yml
vendored
@@ -1,21 +0,0 @@
|
||||
name: aur-pub
|
||||
on:
|
||||
push:
|
||||
tags:
|
||||
- "*"
|
||||
jobs:
|
||||
aur-publish:
|
||||
runs-on: ubuntu-latest
|
||||
steps:
|
||||
- uses: actions/checkout@v2
|
||||
|
||||
- name: Publish AUR package
|
||||
uses: KSXGitHub/github-actions-deploy-aur@v2.2.3
|
||||
with:
|
||||
pkgname: termscp
|
||||
pkgbuild: ./dist/pkgs/arch/PKGBUILD
|
||||
commit_username: ${{ secrets.AUR_USERNAME }}
|
||||
commit_email: ${{ secrets.AUR_EMAIL }}
|
||||
ssh_private_key: ${{ secrets.AUR_KEY }}
|
||||
commit_message: Update AUR package
|
||||
ssh_keyscan_types: rsa,dsa,ecdsa,ed25519
|
||||
39
.github/workflows/coverage.yml
vendored
@@ -1,4 +1,4 @@
|
||||
name: coverage
|
||||
name: Coverage
|
||||
|
||||
on: [push, pull_request]
|
||||
|
||||
@@ -6,17 +6,32 @@ env:
|
||||
CARGO_TERM_COLOR: always
|
||||
|
||||
jobs:
|
||||
coverage:
|
||||
name: Generate coverage
|
||||
build:
|
||||
runs-on: ubuntu-latest
|
||||
|
||||
steps:
|
||||
- name: Checkout repository
|
||||
uses: actions/checkout@v2
|
||||
|
||||
- name: Run cargo-tarpaulin
|
||||
uses: actions-rs/tarpaulin@v0.1
|
||||
- uses: actions/checkout@v2
|
||||
- name: Setup containers
|
||||
run: docker-compose -f "tests/docker-compose.yml" up -d --build
|
||||
- name: Setup nightly toolchain
|
||||
uses: actions-rs/toolchain@v1
|
||||
with:
|
||||
args: "--ignore-tests -- --test-threads 1"
|
||||
|
||||
- name: Upload to codecov.io
|
||||
uses: codecov/codecov-action@v1
|
||||
toolchain: nightly
|
||||
override: true
|
||||
- name: Run tests (nightly)
|
||||
uses: actions-rs/cargo@v1
|
||||
with:
|
||||
command: test
|
||||
args: --lib --no-default-features --features github-actions --features with-containers --no-fail-fast
|
||||
env:
|
||||
CARGO_INCREMENTAL: "0"
|
||||
RUSTFLAGS: "-Zprofile -Ccodegen-units=1 -Cinline-threshold=0 -Clink-dead-code -Coverflow-checks=off -Cpanic=abort -Zpanic_abort_tests"
|
||||
RUSTDOCFLAGS: "-Zprofile -Ccodegen-units=1 -Cinline-threshold=0 -Clink-dead-code -Coverflow-checks=off -Cpanic=abort -Zpanic_abort_tests"
|
||||
- name: Coverage with grcov
|
||||
id: coverage
|
||||
uses: actions-rs/grcov@v0.1
|
||||
- name: Coveralls
|
||||
uses: coverallsapp/github-action@v1.1.1
|
||||
with:
|
||||
github-token: ${{ secrets.GITHUB_TOKEN }}
|
||||
path-to-lcov: ${{ steps.coverage.outputs.report }}
|
||||
|
||||
22
.github/workflows/freebsd.yml
vendored
Normal file
@@ -0,0 +1,22 @@
|
||||
name: FreeBSD
|
||||
|
||||
on: [push, pull_request]
|
||||
|
||||
jobs:
|
||||
build:
|
||||
runs-on: macos-latest
|
||||
steps:
|
||||
- uses: actions/checkout@v2
|
||||
- name: FreeBSD build
|
||||
id: test
|
||||
uses: vmactions/freebsd-vm@v0.1.4
|
||||
with:
|
||||
usesh: true
|
||||
prepare: pkg install -y curl wget libssh gcc vim
|
||||
run: |
|
||||
curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs > /tmp/rustup.sh && \
|
||||
chmod +x /tmp/rustup.sh && \
|
||||
/tmp/rustup.sh -y
|
||||
. $HOME/.cargo/env
|
||||
cargo build --no-default-features
|
||||
cargo test --no-default-features --verbose --lib --features github-actions -- --test-threads 1
|
||||
7
.github/workflows/linux.yml
vendored
@@ -11,15 +11,18 @@ jobs:
|
||||
|
||||
steps:
|
||||
- uses: actions/checkout@v2
|
||||
- name: Setup containers
|
||||
run: docker-compose -f "tests/docker-compose.yml" up -d --build
|
||||
- uses: actions-rs/toolchain@v1
|
||||
with:
|
||||
toolchain: stable
|
||||
override: true
|
||||
components: rustfmt, clippy
|
||||
- uses: actions-rs/cargo@v1
|
||||
- name: Run tests
|
||||
uses: actions-rs/cargo@v1
|
||||
with:
|
||||
command: test
|
||||
args: --all-features --no-fail-fast
|
||||
args: --lib --no-default-features --features github-actions --features with-containers --no-fail-fast
|
||||
- name: Format
|
||||
run: cargo fmt --all -- --check
|
||||
- name: Clippy
|
||||
|
||||
4
.github/workflows/macos.yml
vendored
@@ -12,8 +12,8 @@ jobs:
|
||||
steps:
|
||||
- uses: actions/checkout@v2
|
||||
- name: Build
|
||||
run: cargo build --verbose
|
||||
run: cargo build
|
||||
- name: Run tests
|
||||
run: cargo test --verbose --features githubActions -- --test-threads 1
|
||||
run: cargo test --verbose --lib --features github-actions -- --test-threads 1
|
||||
- name: Clippy
|
||||
run: cargo clippy
|
||||
|
||||
4
.github/workflows/windows.yml
vendored
@@ -12,8 +12,8 @@ jobs:
|
||||
steps:
|
||||
- uses: actions/checkout@v2
|
||||
- name: Build
|
||||
run: cargo build --verbose
|
||||
run: cargo build
|
||||
- name: Run tests
|
||||
run: cargo test --verbose --features githubActions -- --test-threads 1
|
||||
run: cargo test --verbose --lib --features github-actions -- --test-threads 1
|
||||
- name: Clippy
|
||||
run: cargo clippy
|
||||
|
||||
147
CHANGELOG.md
@@ -1,6 +1,10 @@
|
||||
# Changelog
|
||||
|
||||
- [Changelog](#changelog)
|
||||
- [0.6.1](#061)
|
||||
- [0.6.0](#060)
|
||||
- [0.5.1](#051)
|
||||
- [0.5.0](#050)
|
||||
- [0.4.2](#042)
|
||||
- [0.4.1](#041)
|
||||
- [0.4.0](#040)
|
||||
@@ -16,6 +20,147 @@
|
||||
|
||||
---
|
||||
|
||||
## 0.6.1
|
||||
|
||||
Released on 31/08/2021
|
||||
|
||||
- Enhancements:
|
||||
- Now that tui-rs supports title alignment, UI has been improved
|
||||
- Added new `Directory already exists` variant for file transfer errors
|
||||
- Bugfix:
|
||||
- Fixed [Issue 58](https://github.com/veeso/termscp/issues/58):When uploading a directory, create directory only if it doesn't exist
|
||||
- Fixed [Issue 59](https://github.com/veeso/termscp/issues/59): When copying files with tricky copy, the upper progress bar shows no text
|
||||
- Dependencies:
|
||||
- Updated `bitflags` to `1.3.2`
|
||||
- Updated `bytesize` to `1.1.0`
|
||||
- Updated `crossterm` to `0.20`
|
||||
- Updated `open` to `2.0.1`
|
||||
- Added `tui-realm-stdlib 0.6.0`
|
||||
- Replaced `ftp4` with `suppaftp 4.1.2`
|
||||
- Updated `tui-realm` to `0.6.0`
|
||||
|
||||
## 0.6.0
|
||||
|
||||
Released on 23/07/2021
|
||||
|
||||
> 🍹 Summer update 2021 🍨
|
||||
|
||||
- **Open any file** in explorer:
|
||||
- Open file with default program for file type with `<V>`
|
||||
- Open file with a specific program with `<W>`
|
||||
- **Themes**:
|
||||
- You can now set colors for 26 elements in the application
|
||||
- Colors can be any RGB, also **CSS colors** syntax is supported (e.g. `aquamarine`)
|
||||
- Configure theme from settings or import from CLI using the `-t <theme file>` argument
|
||||
- You can find several themes in the `themes/` directory
|
||||
- **Keyring support for Linux**
|
||||
- From now on keyring will be available for Linux only
|
||||
- Read the manual to find out if your system supports the keyring and how you can enable it
|
||||
- libdbus is now a dependency
|
||||
- added `with-keyring` feature
|
||||
- **❗ BREAKING CHANGE ❗**: if you start using keyring on Linux, all the saved password will be lost
|
||||
- **In-app release notes**
|
||||
- Possibility to see the release note of the new available release whenever a new version is available
|
||||
- Just press `<CTRL+R>` when a new version is available from the auth activity to read the release notes
|
||||
- **Installation script**:
|
||||
- From now on, in case cargo is used to install termscp, all the cargo dependencies will be installed
|
||||
- **Start termscp from configuration**: Start termscp with `-c` or `--config` to start termscp from configuration page
|
||||
- Enhancements:
|
||||
- Show a "wait" message when deleting, copying and moving files and when executing commands
|
||||
- Replaced all `...` with `…` in texts
|
||||
- Check if remote host is valid in authentication form
|
||||
- Check if port number is valid in authentication form
|
||||
- From now on, if you try to leave setup without making any change, you won't be prompted whether to save configuration or not
|
||||
- Bugfix:
|
||||
- Fixed broken input cursor when typing UTF8 characters (tui-realm 0.3.2)
|
||||
- Fixed save bookmark dialog: you could switch out from dialog with `<TAB>`
|
||||
- Fixed transfer interruption: it was not possible to abort a transfer if the size of the file was less than 65k
|
||||
- Changed `Remote address` to `Remote host` in authentication form
|
||||
- Dependencies:
|
||||
- Added `argh 0.1.5`
|
||||
- Added `open 1.7.0`
|
||||
- Removed `getopts`
|
||||
- Updated `rand` to `0.8.4`
|
||||
- Updated `textwrap` to `0.14.2`
|
||||
- Updated `tui-realm` to `0.4.3`
|
||||
|
||||
## 0.5.1
|
||||
|
||||
Released on 21/06/2021
|
||||
|
||||
- Enhancements:
|
||||
- **CI now uses containers to test file transfers (SSH/FTP)**
|
||||
- Improved coverage
|
||||
- Found many bugs which has now been fixed
|
||||
- Build in CI won't fail due to test servers not responding
|
||||
- We're now able to test all the functionalities of the file transfers
|
||||
- **Status bar improvements**
|
||||
- "Show hidden files" in status bar
|
||||
- Status bar has now been splitted into two, one for each explorer tab
|
||||
- **Error message if terminal window is too small**
|
||||
- If the terminal window has less than 24 lines, then an error message is displayed in the auth activity
|
||||
- Changed auth layout to absolute sizes
|
||||
- Bugfix:
|
||||
- Fixed UI not showing connection errors
|
||||
- Fixed termscp on Windows dying whenever opening a file with text editor
|
||||
- Fixed broken input cursor when typing UTF8 characters (tui-realm 0.3.2)
|
||||
- Fixed [Issue 44](https://github.com/veeso/termscp/issues/44): Could not move files to other paths in FTP
|
||||
- Fixed [Issue 43](https://github.com/veeso/termscp/issues/43): Could not remove non-empty directories in FTP
|
||||
- Fixed [Issue 39](https://github.com/veeso/termscp/issues/39): Help panels as `ScrollTable` to allow displaying entire content on small screens
|
||||
- Fixed [Issue 38](https://github.com/veeso/termscp/issues/38): Transfer size was wrong when transferring "selected" files (with mark)
|
||||
- Fixed [Issue 37](https://github.com/veeso/termscp/issues/37): progress bar not visible when editing remote files
|
||||
- Dependencies:
|
||||
- Updated `textwrap` to `0.14.0`
|
||||
- Updated `tui-realm` to `0.4.2`
|
||||
|
||||
## 0.5.0
|
||||
|
||||
Released on 23/05/2021
|
||||
|
||||
> 🌸 Spring Update 2021 🌷
|
||||
|
||||
- **Synchronized browsing**:
|
||||
- Added the possibility to enabled the synchronized brower navigation
|
||||
- when you enter a directory, the same directory will be entered on the other tab
|
||||
- Enable sync browser with `<Y>`
|
||||
- Read more on manual: [Synchronized browsing](docs/man.md#Synchronized-browsing-)
|
||||
- **Remote and Local hosts file formatter**:
|
||||
- Added the possibility to set different formatters for local and remote hosts
|
||||
- **Work on multiple files**:
|
||||
- Added the possibility to work on **multiple files simultaneously**
|
||||
- Select a file with `<M>`, the file when selected will have a `*` prepended to its name
|
||||
- Select all files in the current directory with `<CTRL+A>`
|
||||
- Read more on manual: [Work on multiple files](docs/man.md#Work-on-multiple-files-)
|
||||
- **Logging**:
|
||||
- termscp now writes a log file, useful to debug and to contribute to fix issues.
|
||||
- Read more on [manual](docs/man.md)
|
||||
- **File transfer changes**
|
||||
- *SFTP*
|
||||
- Added **COPY** command to SFTP (Please note that Copy command is not supported by SFTP natively, so here it just uses the `cp` shell command as it does in SCP).
|
||||
- *FTP*
|
||||
- Added support for file copy (achieved through *tricky-copy*: the file is first downloaded, then uploaded with a different file name)
|
||||
- **Double progress bar**:
|
||||
- From now one two progress bar will be displayed:
|
||||
- the first, on top, displays the full transfer state (e.g. when downloading a directory of 10 files, the progress of the entire transfer)
|
||||
- the second, on bottom, displays the transfer of the individual file being written (as happened for the old versions)
|
||||
- changed the progress bar colour from `LightGreen` to `Green`
|
||||
- Enhancements
|
||||
- Added a status bar in the file explorer showing whether the sync browser is enabled and which file sorting mode is selected
|
||||
- Removed the goold old figlet title
|
||||
- Protocol input as first field in UI
|
||||
- Port is now updated to standard for selected protocol
|
||||
- when you change the protocol in the authentication form and the current port is standard (`< 1024`), the port will be automatically changed to default value for the selected protocol (e.g. current port: `123`, protocol changed to `FTP`, port becomes `21`)
|
||||
- Bugfix:
|
||||
- Fixed wrong text wrap in log box
|
||||
- Fixed empty bookmark name causing termscp to crash
|
||||
- Fixed error message not being shown after an upload failure
|
||||
- Fixed default protocol not being loaded from config
|
||||
- [Issue 23](https://github.com/veeso/termscp/issues/23): Remove created file if transfer failed or was abrupted
|
||||
- Dependencies:
|
||||
- Added `tui-realm 0.3.0`
|
||||
- Removed `tui` (as direct dependency)
|
||||
- Updated `regex` to `1.5.4`
|
||||
|
||||
## 0.4.2
|
||||
|
||||
Released on 13/04/2021
|
||||
@@ -88,7 +233,7 @@ Released on 28/02/2021
|
||||
- Added `EXTRA` and `LENGTH` parameters to format keys.
|
||||
- Now keys are provided with this syntax `{KEY_NAME[:LEN[:EXTRA]}`
|
||||
- **Check for updates**:
|
||||
- TermSCP will now check for updates on startup and will show in the main page if there is a new version available
|
||||
- termscp will now check for updates on startup and will show in the main page if there is a new version available
|
||||
- This feature may be disabled from setup (Check for updates => No)
|
||||
- Enhancements:
|
||||
- Default choice for deleting file set to "NO" (way too easy to delete files by mistake)
|
||||
|
||||
@@ -19,16 +19,16 @@ Please note we have a [code of conduct](CODE_OF_CONDUCT.md), please follow it in
|
||||
|
||||
## Project mission
|
||||
|
||||
TermSCP was born because, as a terminal lover and Linux user, I wanted something like WinSCP on Linux and on terminal. I my previous job I used SFTP/SCP pratically everyday and that made me to desire an application like termscp so much, that eventually I started to work on it in the spare time. I saw there was a very cool library to create terminal user interface (`tui-rs`), so I started to code it. I wrote termscp as an experiment, I designed kinda nothing at the time. I just said
|
||||
termscp was born because, as a terminal lover and Linux user, I wanted something like WinSCP on Linux and on terminal. I my previous job I used SFTP/SCP pratically everyday and that made me to desire an application like termscp so much, that eventually I started to work on it in the spare time. I saw there was a very cool library to create terminal user interface (`tui-rs`), so I started to code it. I wrote termscp as an experiment, I designed kinda nothing at the time. I just said
|
||||
|
||||
> Ok, there must be a `FileTransfer` trait somehow, I'll have more views, so I'll use something like Android activities, and there must be a module to interact with the local host".
|
||||
|
||||
And so in december 2020 I had the first version of termscp running and it worked, but was very simple, raw and minimal.
|
||||
A lot of things have changed since them, both the features the project provides and my personal view of this project.
|
||||
|
||||
Today I don't see TermSCP as a WinSCP clone anymore. I've also thought about changing the name as the time passed by, but I liked it and it would be hard to change the name on the registries, etc.
|
||||
Today I don't see termscp as a WinSCP clone anymore. I've also thought about changing the name as the time passed by, but I liked it and it would be hard to change the name on the registries, etc.
|
||||
|
||||
Right now I see TermSCP as a **rich-featured file transfer client for terminals**. All I want is to provide all the features users need to use it correctly, I want it to be **safe and reliable** and eventually I want people to consider termscp **the first choice as a file transfer client**.
|
||||
Right now I see termscp as a **rich-featured file transfer client for terminals**. All I want is to provide all the features users need to use it correctly, I want it to be **safe and reliable** and eventually I want people to consider termscp **the first choice as a file transfer client**.
|
||||
|
||||
### Project goals
|
||||
|
||||
@@ -61,6 +61,7 @@ Don't set other labels to your issue, not even priority.
|
||||
|
||||
When you open a bug try to be the most precise as possible in describing your issue. I'm not saying you should always be that precise, since sometimes it's very easy for maintainers to understand what you're talking about. Just try to be reasonable to understand sometimes we might not know what you're talking about or we just don't have the technical knowledge you might think.
|
||||
Please always provide the environment you're working on and consider that we don't provide any support for older version of termscp, at least for those not classified as LTS (if we'll ever have them).
|
||||
If you can, provide the log file or the snippet involving your issue. You can find in the [user manual](docs/man.md) the location of the log file.
|
||||
Last but not least: the template I've written must be used. Full stop.
|
||||
|
||||
Maintainers will may add additional labels to your issue:
|
||||
@@ -68,7 +69,7 @@ Maintainers will may add additional labels to your issue:
|
||||
- **duplicate**: the issue is duplicated; the reference to the related issue will be added to your description. Your issue will be closed.
|
||||
- **priority**: this must be fixed asap
|
||||
- **sorcery**: it is not possible to find out what's causing your bug, nor is reproducible on our test environments.
|
||||
- **wontfix**: your bug has a very high ratio between the probability to encounter it and the difficult to fix it, or it just isn't a bug, but a feature.
|
||||
- **wontfix**: your bug has a very high ratio between the difficulty to fix it and the probability to encounter it, or it just isn't a bug, but a feature.
|
||||
|
||||
### Feature requests
|
||||
|
||||
@@ -99,7 +100,6 @@ At the moment, these kind of contributions are more appreciated and should be pr
|
||||
- New file transfers: for further details see [Implementing File Transfer](#implementing-file-transfers)
|
||||
- Code optimizations: any optimization to the code is welcome
|
||||
- See also features described in [Upcoming features](./README.md##upcoming-features-). Open an issue first though.
|
||||
- A **logo** for the project: I'd really love to have a logo for termscp 💛
|
||||
|
||||
For any other kind of contribution, especially for new features, please submit a new issue first.
|
||||
|
||||
@@ -115,7 +115,9 @@ Let's make it simple and clear:
|
||||
6. Report changes to the PR you opened, writing a report of what you changed and what you have introduced.
|
||||
7. Update the `CHANGELOG.md` file with details of changes to the application. In changelog report changes under a chapter called `PR{PULL_REQUEST_NUMBER}` (e.g. PR12).
|
||||
8. Assign a maintainer to the reviewers.
|
||||
9. Request maintainers to merge your changes.
|
||||
9. Wait for a maintainer to fullfil the acceptance tests
|
||||
10. Wait for a maintainer to complete the acceptance tests
|
||||
11. Request maintainers to merge your changes.
|
||||
|
||||
### Software guidelines
|
||||
|
||||
|
||||
626
Cargo.lock
generated
60
Cargo.toml
@@ -1,17 +1,17 @@
|
||||
[package]
|
||||
authors = ["Christian Visintin"]
|
||||
categories = ["command-line-utilities"]
|
||||
description = "TermSCP is a SCP/SFTP/FTPS client for command line with an integrated UI to explore the remote file system. Basically WinSCP on a terminal."
|
||||
description = "termscp is a feature rich terminal file transfer and explorer with support for SCP/SFTP/FTP"
|
||||
documentation = "https://docs.rs/termscp"
|
||||
edition = "2018"
|
||||
homepage = "https://github.com/veeso/termscp"
|
||||
homepage = "https://veeso.github.io/termscp/"
|
||||
include = ["src/**/*", "LICENSE", "README.md", "CHANGELOG.md"]
|
||||
keywords = ["scp-client", "sftp-client", "ftp-client", "winscp", "command-line-utility"]
|
||||
license = "MIT"
|
||||
name = "termscp"
|
||||
readme = "README.md"
|
||||
repository = "https://github.com/veeso/termscp"
|
||||
version = "0.4.2"
|
||||
version = "0.6.1"
|
||||
|
||||
[package.metadata.rpm]
|
||||
package = "termscp"
|
||||
@@ -27,56 +27,50 @@ name = "termscp"
|
||||
path = "src/main.rs"
|
||||
|
||||
[dependencies]
|
||||
bitflags = "1.2.1"
|
||||
bytesize = "1.0.1"
|
||||
argh = "0.1.5"
|
||||
bitflags = "1.3.2"
|
||||
bytesize = "1.1.0"
|
||||
chrono = "0.4.19"
|
||||
content_inspector = "0.2.4"
|
||||
crossterm = "0.19.0"
|
||||
crossterm = "0.20"
|
||||
dirs = "3.0.1"
|
||||
edit = "0.1.3"
|
||||
getopts = "0.2.21"
|
||||
hostname = "0.3.1"
|
||||
keyring = { version = "0.10.1", optional = true }
|
||||
lazy_static = "1.4.0"
|
||||
log = "0.4.14"
|
||||
magic-crypt = "3.1.7"
|
||||
rand = "0.8.3"
|
||||
regex = "1.4.5"
|
||||
open = "2.0.1"
|
||||
rand = "0.8.4"
|
||||
regex = "1.5.4"
|
||||
rpassword = "5.0.1"
|
||||
serde = { version = "^1.0.0", features = [ "derive" ] }
|
||||
simplelog = "0.10.0"
|
||||
ssh2 = "0.9.0"
|
||||
suppaftp = { version = "4.1.2", features = [ "secure" ] }
|
||||
tempfile = "3.1.0"
|
||||
textwrap = "0.13.4"
|
||||
textwrap = "0.14.2"
|
||||
thiserror = "^1.0.0"
|
||||
toml = "0.5.8"
|
||||
tui-realm-stdlib = "0.6.0"
|
||||
tuirealm = "0.6.0"
|
||||
ureq = { version = "2.1.0", features = [ "json" ] }
|
||||
whoami = "1.1.1"
|
||||
wildmatch = "2.0.0"
|
||||
|
||||
[dependencies.ftp4]
|
||||
features = ["secure"]
|
||||
version = "^4.0.2"
|
||||
|
||||
[dependencies.serde]
|
||||
features = ["derive"]
|
||||
version = "^1.0.0"
|
||||
|
||||
[dependencies.tui]
|
||||
default-features = false
|
||||
features = ["crossterm"]
|
||||
version = "0.14.0"
|
||||
|
||||
[dependencies.ureq]
|
||||
features = ["json"]
|
||||
version = "2.1.0"
|
||||
[dev-dependencies]
|
||||
pretty_assertions = "0.7.2"
|
||||
|
||||
[features]
|
||||
githubActions = []
|
||||
default = [ "with-keyring" ]
|
||||
github-actions = []
|
||||
with-containers = []
|
||||
with-keyring = [ "keyring" ]
|
||||
|
||||
[target."cfg(any(target_os = \"unix\", target_os = \"macos\", target_os = \"linux\"))"]
|
||||
[target."cfg(any(target_os = \"unix\", target_os = \"macos\", target_os = \"linux\"))".dependencies]
|
||||
[target."cfg(target_family = \"unix\")"]
|
||||
[target."cfg(target_family = \"unix\")".dependencies]
|
||||
users = "0.11.0"
|
||||
|
||||
[target."cfg(any(target_os = \"windows\", target_os = \"macos\"))"]
|
||||
[target."cfg(any(target_os = \"windows\", target_os = \"macos\"))".dependencies]
|
||||
keyring = "0.10.1"
|
||||
|
||||
[target."cfg(target_os = \"windows\")"]
|
||||
[target."cfg(target_os = \"windows\")".dependencies]
|
||||
path-slash = "0.1.4"
|
||||
|
||||
434
README.md
@@ -1,370 +1,106 @@
|
||||
# TermSCP
|
||||
# termscp
|
||||
|
||||
[](https://opensource.org/licenses/MIT) [](https://github.com/veeso/termscp) [](https://crates.io/crates/termscp) [](https://crates.io/crates/termscp) [](https://docs.rs/termscp)
|
||||
<p align="center">
|
||||
<img src="/assets/images/termscp.svg" width="256" height="256" />
|
||||
</p>
|
||||
|
||||
[](https://github.com/veeso/termscp/actions) [](https://github.com/veeso/termscp/actions) [](https://github.com/veeso/termscp/actions)
|
||||
<p align="center">~ A feature rich terminal file transfer ~</p>
|
||||
<p align="center">
|
||||
<a href="https://veeso.github.io/termscp/" target="_blank">Website</a>
|
||||
·
|
||||
<a href="https://veeso.github.io/termscp/#get-started" target="_blank">Installation</a>
|
||||
·
|
||||
<a href="https://veeso.github.io/termscp/#user-manual" target="_blank">User manual</a>
|
||||
</p>
|
||||
|
||||
~ Basically, WinSCP on a terminal ~
|
||||
Developed by Christian Visintin
|
||||
Current version: 0.4.2 (13/04/2021)
|
||||
<p align="center">Developed by <a href="https://veeso.github.io/">@veeso</a></p>
|
||||
<p align="center">Current version: 0.6.1 (31/08/2021)</p>
|
||||
|
||||
[](https://opensource.org/licenses/MIT) [](https://github.com/veeso/termscp) [](https://crates.io/crates/termscp) [](https://crates.io/crates/termscp) [](https://docs.rs/termscp)
|
||||
|
||||
[](https://github.com/veeso/termscp/actions) [](https://github.com/veeso/termscp/actions) [](https://github.com/veeso/termscp/actions) [](https://github.com/veeso/termscp/actions) [](https://coveralls.io/github/veeso/termscp)
|
||||
|
||||
---
|
||||
|
||||
- [TermSCP](#termscp)
|
||||
- [About TermSCP 🖥](#about-termscp-)
|
||||
- [Why TermSCP 🤔](#why-termscp-)
|
||||
- [Features 🎁](#features-)
|
||||
- [Installation 🛠](#installation-)
|
||||
- [Cargo 🦀](#cargo-)
|
||||
- [Deb package 📦](#deb-package-)
|
||||
- [RPM package 📦](#rpm-package-)
|
||||
- [AUR Package 🔼](#aur-package-)
|
||||
- [Chocolatey 🍫](#chocolatey-)
|
||||
- [Brew 🍻](#brew-)
|
||||
- [Usage ❓](#usage-)
|
||||
- [Address argument 🌎](#address-argument-)
|
||||
- [How Password can be provided 🔐](#how-password-can-be-provided-)
|
||||
- [Bookmarks ⭐](#bookmarks-)
|
||||
- [Are my passwords Safe 😈](#are-my-passwords-safe-)
|
||||
- [Text Editor ✏](#text-editor-)
|
||||
- [How do I configure the text editor 🦥](#how-do-i-configure-the-text-editor-)
|
||||
- [Configuration ⚙️](#configuration-️)
|
||||
- [SSH Key Storage 🔐](#ssh-key-storage-)
|
||||
- [File Explorer Format](#file-explorer-format)
|
||||
- [Keybindings ⌨](#keybindings-)
|
||||
- [Documentation 📚](#documentation-)
|
||||
- [Known issues 🧻](#known-issues-)
|
||||
- [Upcoming Features 🧪](#upcoming-features-)
|
||||
- [Contributing and issues 🤝🏻](#contributing-and-issues-)
|
||||
- [Changelog ⏳](#changelog-)
|
||||
- [Powered by 🚀](#powered-by-)
|
||||
- [Gallery 🎬](#gallery-)
|
||||
- [Buy me a coffee ☕](#buy-me-a-coffee-)
|
||||
- [License 📃](#license-)
|
||||
## About termscp 🖥
|
||||
|
||||
---
|
||||
|
||||
## About TermSCP 🖥
|
||||
|
||||
TermSCP is basically a porting of WinSCP to terminal. So basically is a terminal utility with an TUI to connect to a remote server to retrieve and upload files and to interact with the local file system. It works both on **Linux**, **MacOS**, **BSD** and **Windows** and supports SFTP, SCP, FTP and FTPS.
|
||||
Termscp is a feature rich terminal file transfer and explorer, with support for SCP/SFTP/FTP. So basically is a terminal utility with an TUI to connect to a remote server to retrieve and upload files and to interact with the local file system. It is **Linux**, **MacOS**, **BSD** and **Windows** compatible and supports SFTP, SCP, FTP and FTPS.
|
||||
|
||||

|
||||
|
||||
---
|
||||
|
||||
### Why TermSCP 🤔
|
||||
|
||||
It happens quite often to me, when using SCP at work to forget the path of a file on a remote machine, which forces me to connect through SSH, gather the file path and finally download it through SCP. I could use WinSCP, but I use Linux and I pratically use the terminal for everything, so I wanted something like WinSCP on my terminal. Yeah, I know there is midnight commander too, but actually I don't like it very much tbh (and hasn't a decent support for scp).
|
||||
|
||||
## Features 🎁
|
||||
|
||||
- Different communication protocols support
|
||||
- 📁 Different communication protocols
|
||||
- SFTP
|
||||
- SCP
|
||||
- FTP and FTPS
|
||||
- Compatible with Windows, Linux, BSD and MacOS
|
||||
- Handy user interface to explore and operate on the remote and on the local machine file system
|
||||
- 🖥 Explore and operate on the remote and on the local machine file system with a handy UI
|
||||
- Create, remove, rename, search, view and edit files
|
||||
- Bookmarks and recent connections can be saved to access quickly to your favourite hosts
|
||||
- Supports text editors to view and edit text files
|
||||
- Supports both SFTP/SCP authentication through SSH keys and username/password
|
||||
- Customizations:
|
||||
- ⭐ Connect to your favourite hosts through built-in bookmarks and recent connections
|
||||
- 📝 View and edit text files with your favourite text editor
|
||||
- 💁 SFTP/SCP authentication through SSH keys and username/password
|
||||
- 🐧 Compatible with Windows, Linux, BSD and MacOS
|
||||
- ✏ Customizable
|
||||
- Themes
|
||||
- Custom file explorer format
|
||||
- Customizable text editor
|
||||
- Customizable file sorting
|
||||
- SSH key storage
|
||||
- Written in Rust
|
||||
- Easy to extend with new file transfers protocols
|
||||
- Developed keeping an eye on performance
|
||||
- 🔐 Save your password in your operating system key vault
|
||||
- 🦀 Rust-powered
|
||||
- 🤝 Easy to extend with new file transfers protocols
|
||||
- 👀 Developed keeping an eye on performance
|
||||
- 🦄 Frequent awesome updates
|
||||
|
||||
---
|
||||
|
||||
## Installation 🛠
|
||||
## Get started 🚀
|
||||
|
||||
If you're considering to install TermSCP I want to thank you 💛 ! I hope you will enjoy TermSCP!
|
||||
If you're considering to install termscp I want to thank you 💜 ! I hope you will enjoy termscp!
|
||||
If you want to contribute to this project, don't forget to check out our contribute guide. [Read More](CONTRIBUTING.md)
|
||||
|
||||
### Cargo 🦀
|
||||
If you are a Linux, a FreeBSD or a MacOS user this simple shell script will install termscp on your system with a single command:
|
||||
|
||||
```sh
|
||||
# Install termscp through cargo
|
||||
cargo install termscp
|
||||
curl --proto '=https' --tlsv1.2 -sSLf "https://git.io/JBhDb" | sh
|
||||
```
|
||||
|
||||
Requirements:
|
||||
while if you're a Windows user, you can install termscp with [Chocolatey](https://chocolatey.org/).
|
||||
|
||||
- Linux
|
||||
- pkg-config
|
||||
- libssh2
|
||||
- openssl
|
||||
For more information or other platforms, please visit [veeso.github.io](https://veeso.github.io/termscp/#get-started) to view all installation methods.
|
||||
|
||||
### Deb package 📦
|
||||
### Requirements ❗
|
||||
|
||||
Get `deb` package from [HERE](https://github.com/veeso/termscp/releases/latest/download/termscp_0.4.2_amd64.deb)
|
||||
or run `wget https://github.com/veeso/termscp/releases/latest/download/termscp_0.4.2_amd64.deb`
|
||||
- **Linux** users:
|
||||
- libssh
|
||||
- libdbus-1
|
||||
- **BSD** users:
|
||||
- libssh
|
||||
|
||||
then install through dpkg:
|
||||
### Optional Requirements ✔️
|
||||
|
||||
```sh
|
||||
dpkg -i termscp_*.deb
|
||||
# Or even better with gdebi
|
||||
gdebi termscp_*.deb
|
||||
```
|
||||
These requirements are not forcely required to run termscp, but to enjoy all of its features
|
||||
|
||||
### RPM package 📦
|
||||
|
||||
Get `rpm` package from [HERE](https://github.com/veeso/termscp/releases/latest/download/termscp-0.4.2-1.x86_64.rpm)
|
||||
or run `wget https://github.com/veeso/termscp/releases/latest/download/termscp-0.4.2-1.x86_64.rpm`
|
||||
|
||||
then install through rpm:
|
||||
|
||||
```sh
|
||||
rpm -U termscp_*.rpm
|
||||
```
|
||||
|
||||
### AUR Package 🔼
|
||||
|
||||
On Arch Linux based distribution, you can install termscp using for istance [yay](https://github.com/Jguer/yay), which I recommend to install AUR packages.
|
||||
|
||||
```sh
|
||||
yay -S termscp
|
||||
```
|
||||
|
||||
### Chocolatey 🍫
|
||||
|
||||
You can install TermSCP on Windows using [chocolatey](https://chocolatey.org/)
|
||||
|
||||
Start PowerShell as administrator and run
|
||||
|
||||
```ps
|
||||
choco install termscp
|
||||
```
|
||||
|
||||
Alternatively you can download the ZIP file from [HERE](https://github.com/veeso/termscp/releases/latest/download/termscp.0.4.2.nupkg)
|
||||
|
||||
and then with PowerShell started with administrator previleges, run:
|
||||
|
||||
```ps
|
||||
choco install termscp -s .
|
||||
```
|
||||
|
||||
### Brew 🍻
|
||||
|
||||
You can install TermSCP on MacOS using [brew](https://brew.sh/)
|
||||
|
||||
From your terminal run
|
||||
|
||||
```sh
|
||||
brew install veeso/termscp/termscp
|
||||
```
|
||||
- **Linux/BSD** users:
|
||||
- To **open** files via `V` (at least one of these)
|
||||
- *xdg-open*
|
||||
- *gio*
|
||||
- *gnome-open*
|
||||
- *kde-open*
|
||||
- **Linux** users:
|
||||
- A keyring manager: read more in the [User manual](docs/man.md#linux-keyring)
|
||||
- **WSL** users
|
||||
- To **open** files via `V` (at least one of these)
|
||||
- [wslu](https://github.com/wslutilities/wslu)
|
||||
|
||||
---
|
||||
|
||||
## Usage ❓
|
||||
## Buy me a coffee ☕
|
||||
|
||||
TermSCP can be started with the following options:
|
||||
If you like termscp and you'd love to see the project to grow, please consider a little donation 🥳
|
||||
|
||||
`termscp [options]... [protocol://user@address:port:wrkdir] [local-wrkdir]`
|
||||
|
||||
- `-P, --password <password>` if address is provided, password will be this argument
|
||||
- `-v, --version` Print version info
|
||||
- `-h, --help` Print help page
|
||||
|
||||
TermSCP can be started in two different mode, if no extra arguments is provided, TermSCP will show the authentication form, where the user will be able to provide the parameters required to connect to the remote peer.
|
||||
|
||||
Alternatively, the user can provide an address as argument to skip the authentication form and starting directly the connection to the remote server.
|
||||
|
||||
If address argument is provided you can also provide the start working directory for local host
|
||||
|
||||
### Address argument 🌎
|
||||
|
||||
The address argument has the following syntax:
|
||||
|
||||
```txt
|
||||
[protocol://][username@]<address>[:port][:wrkdir]
|
||||
```
|
||||
|
||||
Let's see some example of this particular syntax, since it's very comfortable and you'll probably going to use this instead of the other one...
|
||||
|
||||
- Connect using default protocol (*defined in configuration*) to 192.168.1.31, port if not provided is default for the selected protocol (in this case depends on your configuration); username is current user's name
|
||||
|
||||
```sh
|
||||
termscp 192.168.1.31
|
||||
```
|
||||
|
||||
- Connect using default protocol (*defined in configuration*) to 192.168.1.31; username is `root`
|
||||
|
||||
```sh
|
||||
termscp root@192.168.1.31
|
||||
```
|
||||
|
||||
- Connect using scp to 192.168.1.31, port is 4022; username is `omar`
|
||||
|
||||
```sh
|
||||
termscp scp://omar@192.168.1.31:4022
|
||||
```
|
||||
|
||||
- Connect using scp to 192.168.1.31, port is 4022; username is `omar`. You will start in directory `/tmp`
|
||||
|
||||
```sh
|
||||
termscp scp://omar@192.168.1.31:4022:/tmp
|
||||
```
|
||||
|
||||
#### How Password can be provided 🔐
|
||||
|
||||
You have probably noticed, that, when providing the address as argument, there's no way to provide the password.
|
||||
Password can be basically provided through 3 ways when address argument is provided:
|
||||
|
||||
- `-P, --password` option: just use this CLI option providing the password. I strongly unrecommend this method, since it's very unsecure (since you might keep the password in the shell history)
|
||||
- Via `sshpass`: you can provide password via `sshpass`, e.g. `sshpass -f ~/.ssh/topsecret.key termscp cvisintin@192.168.1.31`
|
||||
- You will be prompted for it: if you don't use any of the previous methods, you will be prompted for the password, as happens with the more classics tools such as `scp`, `ssh`, etc.
|
||||
|
||||
---
|
||||
|
||||
## Bookmarks ⭐
|
||||
|
||||
In TermSCP it is possible to save favourites hosts, which can be then loaded quickly from the main layout of termscp.
|
||||
TermSCP will also save the last 16 hosts you connected to.
|
||||
This feature allows you to load all the parameters required to connect to a certain remote, simply selecting the bookmark in the tab under the authentication form.
|
||||
|
||||
Bookmarks will be saved, if possible at:
|
||||
|
||||
- `$HOME/.config/termscp/` on Linux/BSD
|
||||
- `$HOME/Library/Application Support/termscp` on MacOs
|
||||
- `FOLDERID_RoamingAppData\termscp\` on Windows
|
||||
|
||||
For bookmarks only (this won't apply to recent hosts) it is also possible to save the password used to authenticate. The password is not saved by default and must be specified through the prompt when saving a new Bookmark.
|
||||
|
||||
> I was very undecided about storing passwords in termscp. The reason? Saving a password on your computer might give access to a hacker to any server you've registered. But I must admit by myself that for many machines typing the password everytime is really boring, also many times I have to work with machines in LAN, which wouldn't provide any advantage to an attacker, So I came out with a good compromise for passwords.
|
||||
|
||||
I warmly suggest you to follow these guidelines in order to decide whether you should or you shouldn't save passwords:
|
||||
|
||||
- **DON'T** save passwords for machines which are exposed on the internet, save passwords only for machines in LAN
|
||||
- Make sure your machine is protected by attackers. If possible encrypt your disk and don't leave your PC unlocked while you're away.
|
||||
- Preferably, save passwords only when a compromising of the target machine wouldn't be a problem.
|
||||
|
||||
To create a bookmark, just fulfill the authentication form and then input `<CTRL+S>`; you'll then be asked to give a name to your bookmark, and tadah, the bookmark has been created.
|
||||
If you go to [gallery](#gallery-), there is a GIF showing how bookmarks work 💪.
|
||||
|
||||
### Are my passwords Safe 😈
|
||||
|
||||
Well, kinda.
|
||||
As said before, bookmarks are saved in your configuration directory along with passwords. Passwords are obviously not plain text, they are encrypted with **AES-128**. Does this make them safe? Well, depends on your operating system:
|
||||
|
||||
On Windows and MacOS the passwords are stored, if possible (but should be), in respectively the Windows Vault and the Keychain. This is actually super-safe and is directly managed by your operating system.
|
||||
|
||||
On Linux and BSD, on the other hand, the key used to encrypt your passwords is stored on your drive (at $HOME/.config/termscp). It is then, still possible to retrieve the key to decrypt passwords. Luckily, the location of the key guarantees your key can't be read by users different from yours, but yeah, I still wouldn't save the password for a server exposed on the internet 😉.
|
||||
Actually [keyring-rs](https://github.com/hwchen/keyring-rs), supports Linux, but for different reasons I preferred not to make it available for this configuration. If you want to read more about my decision read [this issue](https://github.com/veeso/termscp/issues/2), while if you think this might have been implemented differently feel free to open an issue with your proposal.
|
||||
|
||||
---
|
||||
|
||||
## Text Editor ✏
|
||||
|
||||
TermSCP has, as you might have noticed, many features, one of these is the possibility to view and edit text file. It doesn't matter if the file is located on the local host or on the remote host, termscp provides the possibility to open a file in your favourite text editor.
|
||||
In case the file is located on remote host, the file will be first downloaded into your temporary file directory and then, **only** if changes were made to the file, re-uploaded to the remote host. TermSCP checks if you made changes to the file verifying the last modification time of the file.
|
||||
|
||||
Just a reminder: **you can edit only textual file**; binary files are not supported.
|
||||
|
||||
### How do I configure the text editor 🦥
|
||||
|
||||
Text editor is automatically found using this [awesome crate](https://github.com/milkey-mouse/edit), if you want to change the text editor to use, change it in termscp configuration. [View more](#configuration-️)
|
||||
|
||||
---
|
||||
|
||||
## Configuration ⚙️
|
||||
|
||||
TermSCP supports some user defined parameters, which can be defined in the configuration.
|
||||
Underhood termscp has a TOML file and some other directories where all the parameters will be saved, but don't worry, you won't touch any of these files, since I made possible to configure termscp from its user interface entirely.
|
||||
|
||||
termscp, like for bookmarks, just requires to have these paths accessible:
|
||||
|
||||
- `$HOME/.config/termscp/` on Linux/BSD
|
||||
- `$HOME/Library/Application Support/termscp` on MacOs
|
||||
- `FOLDERID_RoamingAppData\termscp\` on Windows
|
||||
|
||||
To access configuration, you just have to press `<CTRL+C>` from the home of termscp.
|
||||
|
||||
These parameters can be changed:
|
||||
|
||||
- **Default Protocol**: the default protocol is the default value for the file transfer protocol to be used in termscp. This applies for the login page and for the address CLI argument.
|
||||
- **Text Editor**: the text editor to use. By default termscp will find the default editor for you; with this option you can force an editor to be used (e.g. `vim`). **Also GUI editors are supported**, unless they `nohup` from the parent process so if you ask: yes, you can use `notepad.exe`, and no: **Visual Studio Code doesn't work**.
|
||||
- **Show Hidden Files**: select whether hidden files shall be displayed by default. You will be able to decide whether to show or not hidden files at runtime pressing `A` anyway.
|
||||
- **Check for updates**: if set to `yes`, termscp will fetch the Github API to check if there is a new version of termscp available.
|
||||
- **Group Dirs**: select whether directories should be groupped or not in file explorers. If `Display first` is selected, directories will be sorted using the configured method but displayed before files, viceversa if `Display last` is selected.
|
||||
|
||||
### SSH Key Storage 🔐
|
||||
|
||||
Along with configuration, termscp provides also an **essential** feature for **SFTP/SCP clients**: the SSH key storage.
|
||||
|
||||
You can access the SSH key storage, from configuration moving to the `SSH Keys` tab, once there you can:
|
||||
|
||||
- **Add a new key**: just press `<CTRL+N>` and you will be prompted to create a new key. Provide the hostname/ip address and the username associated to the key and finally a text editor will open up: paste the **PRIVATE** ssh key into the text editor, save and quit.
|
||||
- **Remove an existing key**: just press `<DEL>` or `<CTRL+E>` on the key you want to remove, to delete persistently the key from termscp.
|
||||
- **Edit an existing key**: just press `<ENTER>` on the key you want to edit, to change the private key.
|
||||
|
||||
> Q: Wait, my private key is protected with password, can I use it?
|
||||
> A: Of course you can. The password provided for authentication in termscp, is valid both for username/password authentication and for RSA key authentication.
|
||||
|
||||
### File Explorer Format
|
||||
|
||||
It is possible through configuration to define a custom format for the file explorer. This field, with name `File formatter syntax` will define how the file entries will be displayed in the file explorer.
|
||||
The syntax for the formatter is the following `{KEY1}... {KEY2:LENGTH}... {KEY3:LENGTH:EXTRA} {KEYn}...`.
|
||||
Each key in bracket will be replaced with the related attribute, while everything outside brackets will be left unchanged.
|
||||
|
||||
- The key name is mandatory and must be one of the keys below
|
||||
- The length describes the length reserved to display the field. Static attributes doesn't support this (GROUP, PEX, SIZE, USER)
|
||||
- Extra is supported only by some parameters and is an additional options. See keys to check if extra is supported.
|
||||
|
||||
These are the keys supported by the formatter:
|
||||
|
||||
- `ATIME`: Last access time (with default syntax `%b %d %Y %H:%M`); Extra might be provided as the time syntax (e.g. `{ATIME:8:%H:%M}`)
|
||||
- `CTIME`: Creation time (with syntax `%b %d %Y %H:%M`); Extra might be provided as the time syntax (e.g. `{CTIME:8:%H:%M}`)
|
||||
- `GROUP`: Owner group
|
||||
- `MTIME`: Last change time (with syntax `%b %d %Y %H:%M`); Extra might be provided as the time syntax (e.g. `{MTIME:8:%H:%M}`)
|
||||
- `NAME`: File name (Elided if longer than 24)
|
||||
- `PEX`: File permissions (UNIX format)
|
||||
- `SIZE`: File size (omitted for directories)
|
||||
- `SYMLINK`: Symlink (if any `-> {FILE_PATH}`)
|
||||
- `USER`: Owner user
|
||||
|
||||
If left empty, the default formatter syntax will be used: `{NAME:24} {PEX} {USER} {SIZE} {MTIME:17:%b %d %Y %H:%M}`
|
||||
|
||||
---
|
||||
|
||||
## Keybindings ⌨
|
||||
|
||||
| Key | Command | Reminder |
|
||||
|---------------|-------------------------------------------------------|-------------|
|
||||
| `<ESC>` | Disconnect from remote; return to authentication page | |
|
||||
| `<TAB>` | Switch between log tab and explorer | |
|
||||
| `<BACKSPACE>` | Go to previous directory in stack | |
|
||||
| `<RIGHT>` | Move to remote explorer tab | |
|
||||
| `<LEFT>` | Move to local explorer tab | |
|
||||
| `<UP>` | Move up in selected list | |
|
||||
| `<DOWN>` | Move down in selected list | |
|
||||
| `<PGUP>` | Move up in selected list by 8 rows | |
|
||||
| `<PGDOWN>` | Move down in selected list by 8 rows | |
|
||||
| `<ENTER>` | Enter directory | |
|
||||
| `<SPACE>` | Upload / download selected file | |
|
||||
| `<A>` | Toggle hidden files | All |
|
||||
| `<B>` | Sort files by | Bubblesort? |
|
||||
| `<C>` | Copy file/directory | Copy |
|
||||
| `<D>` | Make directory | Directory |
|
||||
| `<E>` | Delete file (Same as `DEL`) | Erase |
|
||||
| `<F>` | Search for files (wild match is supported) | Find |
|
||||
| `<G>` | Go to supplied path | Go to |
|
||||
| `<H>` | Show help | Help |
|
||||
| `<I>` | Show info about selected file or directory | Info |
|
||||
| `<L>` | Reload current directory's content | List |
|
||||
| `<N>` | Create new file with provided name | New |
|
||||
| `<O>` | Edit file; see [Text editor](#text-editor-) | Open |
|
||||
| `<Q>` | Quit TermSCP | Quit |
|
||||
| `<R>` | Rename file | Rename |
|
||||
| `<S>` | Save file as... | Save |
|
||||
| `<U>` | Go to parent directory | Upper |
|
||||
| `<X>` | Execute a command | eXecute |
|
||||
| `<DEL>` | Delete file | |
|
||||
| `<CTRL+C>` | Abort file transfer process | |
|
||||
[](https://www.buymeacoffee.com/veeso)
|
||||
|
||||
---
|
||||
|
||||
@@ -376,25 +112,26 @@ The developer documentation can be found on Rust Docs at <https://docs.rs/termsc
|
||||
|
||||
## Known issues 🧻
|
||||
|
||||
- `NoSuchFileOrDirectory` on connect (WSL): I know about this issue and it's a glitch of WSL I guess. Don't worry about it, just move the termscp executable into another PATH location, such as `/usr/bin`, or install it through the appropriate package format (e.g. deb).
|
||||
- `NoSuchFileOrDirectory` on connect (WSL1): I know about this issue and it's a glitch of WSL I guess. Don't worry about it, just move the termscp executable into another PATH location, such as `/usr/bin`, or install it through the appropriate package format (e.g. deb).
|
||||
|
||||
---
|
||||
|
||||
## Upcoming Features 🧪
|
||||
|
||||
- **Themes provider 🎨**: I'm still thinking about how I will implement this, but basically the idea is to have a configuration file where it will be possible
|
||||
to define the color schema for the entire application. I haven't planned this release yet
|
||||
- **Local and remote file explorer format 🃏**: From 0.5.0 you will be able to customize the file format for both local and remote hosts.
|
||||
- **Synchronized browsing of local and remote directories ⌚**: See [Issue 8](https://github.com/veeso/termscp/issues/8)
|
||||
- **Group file select 🤩**: Possibility to select a group of files in explorers to operate on
|
||||
Major termscp releases will now be seasonal, so expect 4 major updates during the year.
|
||||
|
||||
No other new feature is planned at the moment. I actually think that termscp is getting mature and now I should focus upcoming updates more on bug fixing and
|
||||
code/performance improvements than on new features.
|
||||
Anyway there are some ideas which I'd like to implement. If you want to start working on them, feel free to open a PR:
|
||||
Planned for *🍁 Autumn update 🍇*:
|
||||
|
||||
- Amazon S3 support
|
||||
- Samba support
|
||||
- Themes provider
|
||||
- **Self-update ⬇️**: In order to increase users updating termscp, I want to provide the possibility to update termscp directly from application, when a new update is available.
|
||||
- **AWS S3 support 🪣**: I'll use `rust-s3` library to implement this. This is really big **Maybe** for the autumn update and might be moved to the Winter update.
|
||||
- **Prompt before replacing files ☢️**: Possibility to configure whether a prompt should be displayed before replacing files.
|
||||
|
||||
Planned for *❄️ Winter update ⛄*:
|
||||
|
||||
- **SMB Support 🎉**: This will require a long time to be implemented, since I'm currently working on a Rust native SMB library, since I don't want to add new C-bindings. ~~Fear the 🦚~~
|
||||
- **Configuration profile for bookmarks 📚**: Basically this feature adds the possibility to have a specific setup for a certain host, instead of having only one global configuration.
|
||||
|
||||
Along to new features, termscp developments is now focused on UX and performance improvements, so if you have any suggestion, feel free to open an issue.
|
||||
|
||||
---
|
||||
|
||||
@@ -409,24 +146,27 @@ Please follow [our contributing guidelines](CONTRIBUTING.md)
|
||||
|
||||
## Changelog ⏳
|
||||
|
||||
View TermSCP's changelog [HERE](CHANGELOG.md)
|
||||
View termscp's changelog [HERE](CHANGELOG.md)
|
||||
|
||||
---
|
||||
|
||||
## Powered by 🚀
|
||||
## Powered by 💪
|
||||
|
||||
TermSCP is powered by these aweseome projects:
|
||||
termscp is powered by these aweseome projects:
|
||||
|
||||
- [bytesize](https://github.com/hyunsik/bytesize)
|
||||
- [crossterm](https://github.com/crossterm-rs/crossterm)
|
||||
- [edit](https://github.com/milkey-mouse/edit)
|
||||
- [keyring-rs](https://github.com/hwchen/keyring-rs)
|
||||
- [open-rs](https://github.com/Byron/open-rs)
|
||||
- [rpassword](https://github.com/conradkleinespel/rpassword)
|
||||
- [rust-ftp](https://github.com/mattnenterprise/rust-ftp)
|
||||
- [ssh2-rs](https://github.com/alexcrichton/ssh2-rs)
|
||||
- [suppaftp](https://github.com/veeso/suppaftp)
|
||||
- [textwrap](https://github.com/mgeisler/textwrap)
|
||||
- [tui-rs](https://github.com/fdehau/tui-rs)
|
||||
- [tui-realm](https://github.com/veeso/tui-realm)
|
||||
- [whoami](https://github.com/libcala/whoami)
|
||||
- [wildmatch](https://github.com/becheran/wildmatch)
|
||||
|
||||
---
|
||||
|
||||
@@ -450,18 +190,8 @@ TermSCP is powered by these aweseome projects:
|
||||
|
||||
---
|
||||
|
||||
## Buy me a coffee ☕
|
||||
|
||||
If you like termscp and you'd love to see the project to grow, please consider a little donation 🥳
|
||||
|
||||
[](https://www.buymeacoffee.com/veeso)
|
||||
|
||||
---
|
||||
|
||||
## License 📃
|
||||
|
||||
termscp is licensed under the MIT license since version 0.4.0.
|
||||
termscp is licensed under the MIT license.
|
||||
|
||||
You can read the entire license [HERE](LICENSE)
|
||||
|
||||
*Older version (0.1.0 ~ 0.3.3) are licensed under the [GPL-V3](http://www.gnu.org/licenses/gpl-3.0.txt) license*
|
||||
|
||||
10
SECURITY.md
Normal file
@@ -0,0 +1,10 @@
|
||||
# Security Policy
|
||||
|
||||
## Supported Versions
|
||||
|
||||
Only latst version of termscp has the latest security updates.
|
||||
Because of that, **you should always consider updating termscp to the latest version**.
|
||||
|
||||
## Reporting a Vulnerability
|
||||
|
||||
If you have any security vulnerability or concern to report, please open an issue using the `Security report` template.
|
||||
|
Before Width: | Height: | Size: 212 KiB After Width: | Height: | Size: 190 KiB |
|
Before Width: | Height: | Size: 223 KiB After Width: | Height: | Size: 231 KiB |
|
Before Width: | Height: | Size: 473 KiB After Width: | Height: | Size: 313 KiB |
|
Before Width: | Height: | Size: 504 KiB After Width: | Height: | Size: 2.1 MiB |
BIN
assets/images/termscp-128.png
Normal file
|
After Width: | Height: | Size: 2.2 KiB |
BIN
assets/images/termscp-512.png
Normal file
|
After Width: | Height: | Size: 11 KiB |
BIN
assets/images/termscp-64.png
Normal file
|
After Width: | Height: | Size: 1.3 KiB |
BIN
assets/images/termscp-96.png
Normal file
|
After Width: | Height: | Size: 1.8 KiB |
1
assets/images/termscp.svg
Normal file
@@ -0,0 +1 @@
|
||||
<svg xmlns="http://www.w3.org/2000/svg" xmlns:bx="https://boxy-svg.com" viewBox="0 0 500 500"><path style="fill:#404040" d="M 15 0 H 484 A 16 16 0 0 1 500 16 V 47.312 H 0 V 15 A 15 15 0 0 1 15 0 Z" bx:shape="rect 0 0 500 47.312 15 16 0 0 1@05baa068"/><circle style="fill:#ea4444" cx="29.473" cy="23.011" r="7.344"/><circle style="fill:#eac944" cx="58.177" cy="22.543" r="7.344" transform="matrix(1, 0, 0, 1.031863, -5.389861, -0.016285)"/><circle style="fill:#34b938" cx="58.177" cy="22.543" r="7.344" transform="matrix(1, 0, 0, 1.031863, 17.888227, -0.016285)"/><rect width="500" height="452.688" y="47.312" style="fill:#31363b"/><polygon style="stroke:#000;fill:#f0f0f0" points="71.581 100 224.35 252.769 77.119 400 25.235 348.115 122.193 251.156 22.129 151.093"/><rect style="fill:#f0f0f0" width="242.408" height="49.262" x="235.188" y="381.519" rx="10" ry="10"/><g transform="matrix(0.513677, 0, 0, 0.513677, 257.101013, 152.253387)"><polygon style="fill:#f0f0f0" points="196.4 0 292 49.2 388 98 292 147.2 196.4 196.4 100.8 147.2 4.8 98 100.8 49.2"/><polygon style="fill:#31363b" points="316 179.6 316 135.2 268 159.6 268 204 294.4 171.6"/><polygon style="fill:#f0f0f0" points="196.4 196.4 196.4 392.8 388 294.8 388 98 316 135.2 314.4 136 314.4 179.2 294.4 171.6 268 204 268 159.6"/><polygon style="fill:#f0f0f0" points="196.4 392.8 196.4 196.4 100.8 147.2 4.8 98 4.8 294.8"/><polygon style="fill:#31363b" points="76.8 61.2 268 159.6 314.4 136 316 135.2 124.8 36.8 100.8 49.2"/></g></svg>
|
||||
|
After Width: | Height: | Size: 1.5 KiB |
BIN
assets/images/themes.gif
Normal file
|
After Width: | Height: | Size: 227 KiB |
@@ -1,7 +0,0 @@
|
||||
ignore:
|
||||
- src/main.rs
|
||||
- src/lib.rs
|
||||
- src/activity_manager.rs
|
||||
- src/ui/activities/
|
||||
- src/ui/context.rs
|
||||
- src/ui/input.rs
|
||||
15
dist/build/deploy.sh
vendored
@@ -28,20 +28,5 @@ cd -
|
||||
mkdir -p ${PKGS_DIR}/rpm/
|
||||
CONTAINER_NAME=$(docker create termscp-${VERSION}-x86_64_centos7 termscp-${VERSION}-x86_64_centos7)
|
||||
docker cp ${CONTAINER_NAME}:/usr/src/termscp/target/release/rpmbuild/RPMS/x86_64/termscp-${VERSION}-1.el7.x86_64.rpm ${PKGS_DIR}/rpm/termscp-${VERSION}-1.x86_64.rpm
|
||||
# Build x86_64_archlinux
|
||||
|
||||
##################### TEMP REMOVED ###################################
|
||||
# cd x86_64_archlinux/
|
||||
# docker build --tag termscp-${VERSION}-x86_64_archlinux .
|
||||
# # Create container and get AUR pkg
|
||||
# cd -
|
||||
# mkdir -p ${PKGS_DIR}/arch/
|
||||
# CONTAINER_NAME=$(docker create termscp-${VERSION}-x86_64_archlinux termscp-${VERSION}-x86_64_archlinux)
|
||||
# docker cp ${CONTAINER_NAME}:/usr/src/termscp/termscp-${VERSION}-x86_64.tar.gz ${PKGS_DIR}/arch/
|
||||
# docker cp ${CONTAINER_NAME}:/usr/src/termscp/PKGBUILD ${PKGS_DIR}/arch/
|
||||
# docker cp ${CONTAINER_NAME}:/usr/src/termscp/.SRCINFO ${PKGS_DIR}/arch/
|
||||
# # Replace termscp-bin with termscp in PKGBUILD
|
||||
# sed -i 's/termscp-bin/termscp/g' ${PKGS_DIR}/arch/PKGBUILD
|
||||
##################### TEMP REMOVED ###################################
|
||||
|
||||
exit $?
|
||||
|
||||
33
dist/build/x86_64_archlinux/Dockerfile
vendored
@@ -1,33 +0,0 @@
|
||||
FROM archlinux:base-20210120.0.13969 as builder
|
||||
|
||||
WORKDIR /usr/src/
|
||||
# Install dependencies
|
||||
RUN pacman -Syu --noconfirm \
|
||||
git \
|
||||
gcc \
|
||||
openssl \
|
||||
pkg-config \
|
||||
sudo
|
||||
# Install rust
|
||||
RUN curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs > /tmp/rust.sh && \
|
||||
chmod +x /tmp/rust.sh && \
|
||||
/tmp/rust.sh -y
|
||||
# Create build user
|
||||
RUN useradd build -m && \
|
||||
passwd -d build && \
|
||||
mkdir -p termscp && \
|
||||
chown -R build.build termscp/
|
||||
# Clone repository
|
||||
RUN git clone https://github.com/veeso/termscp.git
|
||||
# Set workdir to termscp
|
||||
WORKDIR /usr/src/termscp/
|
||||
# Install cargo arxch
|
||||
RUN source $HOME/.cargo/env && cargo install cargo-aur
|
||||
# Build for x86_64
|
||||
RUN source $HOME/.cargo/env && cargo build --release
|
||||
# Build pkgs
|
||||
RUN source $HOME/.cargo/env && cargo aur
|
||||
# Create SRCINFO
|
||||
RUN chown -R build.build ../termscp/ && sudo -u build bash -c 'makepkg --printsrcinfo > .SRCINFO'
|
||||
|
||||
CMD ["sh"]
|
||||
1
dist/build/x86_64_centos7/Dockerfile
vendored
@@ -7,6 +7,7 @@ RUN yum -y install \
|
||||
gcc \
|
||||
openssl \
|
||||
pkgconfig \
|
||||
dbus-devel \
|
||||
openssl-devel
|
||||
# Install rust
|
||||
RUN curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs > /tmp/rust.sh && \
|
||||
|
||||
1
dist/build/x86_64_debian8/Dockerfile
vendored
@@ -8,6 +8,7 @@ RUN apt update && apt install -y \
|
||||
pkg-config \
|
||||
libssl-dev \
|
||||
libssh2-1-dev \
|
||||
libdbus-1-dev \
|
||||
curl
|
||||
|
||||
# Install rust
|
||||
|
||||
1
dist/build/x86_64_debian9/Dockerfile
vendored
@@ -8,6 +8,7 @@ RUN apt update && apt install -y \
|
||||
pkg-config \
|
||||
libssl-dev \
|
||||
libssh2-1-dev \
|
||||
libdbus-1-dev \
|
||||
curl
|
||||
|
||||
# Install rust
|
||||
|
||||
14
dist/pkgs/arch/.SRCINFO
vendored
@@ -1,14 +0,0 @@
|
||||
pkgbase = termscp
|
||||
pkgdesc = TermSCP is a SCP/SFTP/FTPS client for command line with an integrated UI to explore the remote file system. Basically WinSCP on a terminal.
|
||||
pkgver = 0.4.2
|
||||
pkgrel = 1
|
||||
url = https://github.com/veeso/termscp
|
||||
arch = x86_64
|
||||
license = MIT
|
||||
provides = termscp
|
||||
options = strip
|
||||
source = https://github.com/veeso/termscp/releases/download/v0.4.2/termscp-0.4.2-x86_64.tar.gz
|
||||
sha256sums = c72f78a4707402f7f970a883899f4f1583fd9eca6166cb7f7616be97cabf768a
|
||||
|
||||
pkgname = termscp
|
||||
|
||||
16
dist/pkgs/arch/PKGBUILD
vendored
@@ -1,16 +0,0 @@
|
||||
# Maintainer: Christian Visintin
|
||||
pkgname=termscp
|
||||
pkgver=0.4.2
|
||||
pkgrel=1
|
||||
pkgdesc="TermSCP is a SCP/SFTP/FTPS client for command line with an integrated UI to explore the remote file system. Basically WinSCP on a terminal."
|
||||
url="https://github.com/veeso/termscp"
|
||||
license=("MIT")
|
||||
arch=("x86_64")
|
||||
provides=("termscp")
|
||||
options=("strip")
|
||||
source=("https://github.com/veeso/termscp/releases/download/v$pkgver/termscp-$pkgver-x86_64.tar.gz")
|
||||
sha256sums=("c72f78a4707402f7f970a883899f4f1583fd9eca6166cb7f7616be97cabf768a")
|
||||
|
||||
package() {
|
||||
install -Dm755 termscp -t "$pkgdir/usr/bin/"
|
||||
}
|
||||
17
dist/pkgs/freebsd/manifest
vendored
Normal file
@@ -0,0 +1,17 @@
|
||||
name: "termscp"
|
||||
version: 0.6.1
|
||||
origin: veeso/termscp
|
||||
comment: "A feature rich terminal UI file transfer and explorer with support for SCP/SFTP/FTP"
|
||||
desc: <<EOD
|
||||
A feature rich terminal UI file transfer and explorer with support for SCP/SFTP/FTP
|
||||
EOD
|
||||
arch: "amd64"
|
||||
www: "https://veeso.github.io/termscp/"
|
||||
maintainer: "christian.visintin1997@gmail.com"
|
||||
prefix: "/usr/local/bin"
|
||||
deps: {
|
||||
libssh: {origin: security/libssh, version: 0.9.5}
|
||||
}
|
||||
files: {
|
||||
/usr/local/bin/termscp: "87543d13b11b6e601ba8cdde9d704c80dc3515f1681fbf71fd0b31d7206efc09"
|
||||
}
|
||||
@@ -1,35 +0,0 @@
|
||||
# Deploy checklist
|
||||
|
||||
Document audience: project maintainers
|
||||
|
||||
- [Deploy checklist](#deploy-checklist)
|
||||
- [Description](#description)
|
||||
- [Checklist](#checklist)
|
||||
|
||||
## Description
|
||||
|
||||
This document describes the checklist that must be fulfilled before releasing a new version of termscp.
|
||||
|
||||
## Checklist
|
||||
|
||||
- [ ] The latest build didn't report any error in the CI
|
||||
- [ ] All commands when using SFTP work
|
||||
- [ ] All commands when using SCP work
|
||||
- [ ] All commands when using FTP work
|
||||
- [ ] It is possible to load bookmarks
|
||||
- [ ] Recent connections get saved
|
||||
- [ ] Update versions and release date in readme, changelog and cargo.toml
|
||||
- [ ] Build on MacOS
|
||||
- [ ] Update sha256 and version on homebrew repository
|
||||
- [ ] Build on Windows
|
||||
- [ ] Update sha256 and version in chocolatey repository
|
||||
- [ ] Create chocolatey package
|
||||
- [ ] Build Linux version using docker from `dist/build/build.sh`
|
||||
- [ ] Update sha256 and version in AUR files
|
||||
- [ ] Create release and attach the following artifacts
|
||||
- [ ] Deb package
|
||||
- [ ] RPM package
|
||||
- [ ] MacOs tar.gz
|
||||
- [ ] Windows nupkg
|
||||
- [ ] Windows zip
|
||||
- [ ] AUR tar.gz
|
||||
@@ -3,18 +3,28 @@
|
||||
Document audience: developers
|
||||
|
||||
- [Developer Manual](#developer-manual)
|
||||
- [How TermSCP works](#how-termscp-works)
|
||||
- [How to test](#how-to-test)
|
||||
- [How termscp works](#how-termscp-works)
|
||||
- [Activities](#activities)
|
||||
- [The Context](#the-context)
|
||||
- [Tests fails due to receivers](#tests-fails-due-to-receivers)
|
||||
- [Implementing File Transfers](#implementing-file-transfers)
|
||||
|
||||
Welcome to the developer manual for TermSCP. This chapter DOESN'T contain the documentation for TermSCP modules, which can instead be found on Rust Docs at <https://docs.rs/termscp>
|
||||
This chapter describes how TermSCP works and the guide lines to implement stuff such as file transfers and add features to the user interface.
|
||||
Welcome to the developer manual for termscp. This chapter DOESN'T contain the documentation for termscp modules, which can instead be found on Rust Docs at <https://docs.rs/termscp>
|
||||
This chapter describes how termscp works and the guide lines to implement stuff such as file transfers and add features to the user interface.
|
||||
|
||||
## How TermSCP works
|
||||
## How to test
|
||||
|
||||
TermSCP is basically made up of 4 components:
|
||||
First an introduction to tests.
|
||||
|
||||
Usually it's enough to run `cargo test`, but please note that whenever you're working on file transfer you'll need one more step.
|
||||
In order to run tests with file transfers, you need to start the file transfer server containers, which can be started via `docker`.
|
||||
|
||||
To run all tests with file transfers just run: `./tests/test.sh`
|
||||
|
||||
---
|
||||
|
||||
## How termscp works
|
||||
|
||||
termscp is basically made up of 4 components:
|
||||
|
||||
- the **filetransfer**: the filetransfer takes care of managing the remote file system; it provides function to establish a connection with the remote, operating on the remote server file system (e.g. remove files, make directories, rename files, ...), read files and write files. The FileTransfer, as we'll see later, is actually a trait, and for each protocol a FileTransfer must be implement the trait.
|
||||
- the **host**: the host module provides functions to interact with the local host file system.
|
||||
@@ -61,146 +71,3 @@ The context basically holds the following data:
|
||||
- The **Terminal**: the terminal is used to view the tui on the terminal
|
||||
|
||||
---
|
||||
|
||||
## Tests fails due to receivers
|
||||
|
||||
Yes. This happens quite often and is related to the fact that I'm using public SSH/SFTP/FTP server to test file receivers and sometimes this server go down for even a day or more. If your tests don't pass due to this, don't worry, submit the pull request and I'll take care of testing them by myself.
|
||||
|
||||
---
|
||||
|
||||
## Implementing File Transfers
|
||||
|
||||
This chapter describes how to implement a file transfer in TermSCP. A file transfer is a module which implements the `FileTransfer` trait. The file transfer provides different modules to interact with a remote server, which in addition to the most obvious methods, used to download and upload files, provides also methods to list files, delete files, create directories etc.
|
||||
|
||||
In the following steps I will describe how to implement a new file transfer, in this case I will be implementing the SCP file transfer (which I'm actually implementing the moment I'm writing this lines).
|
||||
|
||||
1. Add the Scp protocol to the `FileTransferProtocol` enum.
|
||||
|
||||
Move to `src/filetransfer/mod.rs` and add `Scp` to the `FileTransferProtocol` enum
|
||||
|
||||
```rs
|
||||
/// ## FileTransferProtocol
|
||||
///
|
||||
/// This enum defines the different transfer protocol available in TermSCP
|
||||
#[derive(std::cmp::PartialEq, std::fmt::Debug, std::clone::Clone)]
|
||||
pub enum FileTransferProtocol {
|
||||
Sftp,
|
||||
Ftp(bool), // Bool is for secure (true => ftps)
|
||||
Scp, // <-- here
|
||||
}
|
||||
```
|
||||
|
||||
In this case Scp is a "plain" enum type. If you need particular options, follow the implementation of `Ftp` which uses a boolean flag for indicating if using FTPS or FTP.
|
||||
|
||||
2. Implement the FileTransfer struct
|
||||
|
||||
Create a file at `src/filetransfer/mytransfer.rs`
|
||||
|
||||
Declare your file transfer struct
|
||||
|
||||
```rs
|
||||
/// ## ScpFileTransfer
|
||||
///
|
||||
/// SFTP file transfer structure
|
||||
pub struct ScpFileTransfer {
|
||||
session: Option<Session>,
|
||||
sftp: Option<Sftp>,
|
||||
wrkdir: PathBuf,
|
||||
}
|
||||
```
|
||||
|
||||
3. Implement the `FileTransfer` trait for it
|
||||
|
||||
You'll have to implement the following methods for your file transfer:
|
||||
|
||||
- connect: connect to remote server
|
||||
- disconnect: disconnect from remote server
|
||||
- is_connected: returns whether the file transfer is connected to remote
|
||||
- pwd: get working directory
|
||||
- change_dir: change working directory.
|
||||
- list_dir: get files and directories at a certain path
|
||||
- mkdir: make a new directory. Return an error in case the directory already exists
|
||||
- remove: remove a file or a directory. In case the protocol doesn't support recursive removing of directories you MUST implement this through a recursive algorithm
|
||||
- rename: rename a file or a directory
|
||||
- stat: returns detail for a certain path
|
||||
- send_file: opens a stream to a remote path for write purposes (write a remote file)
|
||||
- recv_file: opens a stream to a remote path for read purposes (write a local file)
|
||||
- on_sent: finalize a stream when writing a remote file. In case it's not necessary just return `Ok(())`
|
||||
- on_recv: fianlize a stream when reading a remote file. In case it's not necessary just return `Ok(())`
|
||||
|
||||
In case the protocol you're working on doesn't support any of this features, just return `Err(FileTransferError::new(FileTransferErrorType::UnsupportedFeature))`
|
||||
|
||||
4. Add your transfer to filetransfers:
|
||||
|
||||
Move to `src/filetransfer/mod.rs` and declare your file transfer:
|
||||
|
||||
```rs
|
||||
// Transfers
|
||||
pub mod ftp_transfer;
|
||||
pub mod scp_transfer; // <-- here
|
||||
pub mod sftp_transfer;
|
||||
```
|
||||
|
||||
5. Handle FileTransfer in `FileTransferActivity::new`
|
||||
|
||||
Move to `src/ui/activities/filetransfer_activity/mod.rs` and add the new protocol to the client match
|
||||
|
||||
```rs
|
||||
client: match protocol {
|
||||
FileTransferProtocol::Sftp => Box::new(SftpFileTransfer::new()),
|
||||
FileTransferProtocol::Ftp(ftps) => Box::new(FtpFileTransfer::new(ftps)),
|
||||
FileTransferProtocol::Scp => Box::new(ScpFileTransfer::new()), // <--- here
|
||||
},
|
||||
```
|
||||
|
||||
6. Handle right/left input events in `AuthActivity`:
|
||||
|
||||
Move to `src/ui/activities/auth_activity.rs` and handle the new protocol in `handle_input_event_mode_text` for `KeyCode::Left` and `KeyCode::Right`.
|
||||
Consider that the order they "rotate" must match the way they will be drawned in the interface.
|
||||
For newer protocols, please put them always at the end of the list. In this list I won't, because Scp is more important than Ftp imo.
|
||||
|
||||
```rs
|
||||
KeyCode::Left => {
|
||||
// If current field is Protocol handle event... (move element left)
|
||||
if self.selected_field == InputField::Protocol {
|
||||
self.protocol = match self.protocol {
|
||||
FileTransferProtocol::Sftp => FileTransferProtocol::Ftp(true), // End of list (wrap)
|
||||
FileTransferProtocol::Scp => FileTransferProtocol::Sftp,
|
||||
FileTransferProtocol::Ftp(ftps) => match ftps {
|
||||
false => FileTransferProtocol::Scp,
|
||||
true => FileTransferProtocol::Ftp(false),
|
||||
}
|
||||
};
|
||||
}
|
||||
}
|
||||
KeyCode::Right => {
|
||||
// If current field is Protocol handle event... ( move element right )
|
||||
if self.selected_field == InputField::Protocol {
|
||||
self.protocol = match self.protocol {
|
||||
FileTransferProtocol::Sftp => FileTransferProtocol::Scp,
|
||||
FileTransferProtocol::Scp => FileTransferProtocol::Ftp(false),
|
||||
FileTransferProtocol::Ftp(ftps) => match ftps {
|
||||
false => FileTransferProtocol::Ftp(true),
|
||||
true => FileTransferProtocol::Sftp, // End of list (wrap)
|
||||
}
|
||||
};
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
7. Add your new file transfer to the protocol input field
|
||||
|
||||
Move to `AuthActivity::draw_protocol_select` method.
|
||||
Here add your new protocol to the `Spans` vector and to the match case, which chooses which element to highlight.
|
||||
|
||||
```rs
|
||||
let protocols: Vec<Spans> = vec![Spans::from("SFTP"), Spans::from("SCP"), Spans::from("FTP"), Spans::from("FTPS")];
|
||||
let index: usize = match self.protocol {
|
||||
FileTransferProtocol::Sftp => 0,
|
||||
FileTransferProtocol::Scp => 1,
|
||||
FileTransferProtocol::Ftp(ftps) => match ftps {
|
||||
false => 2,
|
||||
true => 3,
|
||||
}
|
||||
};
|
||||
```
|
||||
|
||||
418
docs/man.md
Normal file
@@ -0,0 +1,418 @@
|
||||
# User manual 🎓
|
||||
|
||||
- [User manual 🎓](#user-manual-)
|
||||
- [Usage ❓](#usage-)
|
||||
- [Address argument 🌎](#address-argument-)
|
||||
- [How Password can be provided 🔐](#how-password-can-be-provided-)
|
||||
- [File explorer 📂](#file-explorer-)
|
||||
- [Keybindings ⌨](#keybindings-)
|
||||
- [Work on multiple files 🥷](#work-on-multiple-files-)
|
||||
- [Synchronized browsing ⏲️](#synchronized-browsing-️)
|
||||
- [Open and Open With 🚪](#open-and-open-with-)
|
||||
- [Bookmarks ⭐](#bookmarks-)
|
||||
- [Are my passwords Safe 😈](#are-my-passwords-safe-)
|
||||
- [Linux Keyring](#linux-keyring)
|
||||
- [KeepassXC setup for termscp](#keepassxc-setup-for-termscp)
|
||||
- [Configuration ⚙️](#configuration-️)
|
||||
- [SSH Key Storage 🔐](#ssh-key-storage-)
|
||||
- [File Explorer Format](#file-explorer-format)
|
||||
- [Themes 🎨](#themes-)
|
||||
- [Styles 💈](#styles-)
|
||||
- [Authentication page](#authentication-page)
|
||||
- [Transfer page](#transfer-page)
|
||||
- [Misc](#misc)
|
||||
- [Text Editor ✏](#text-editor-)
|
||||
- [How do I configure the text editor 🦥](#how-do-i-configure-the-text-editor-)
|
||||
- [Logging 🩺](#logging-)
|
||||
|
||||
## Usage ❓
|
||||
|
||||
termscp can be started with the following options:
|
||||
|
||||
`termscp [options]... [protocol://user@address:port:wrkdir] [local-wrkdir]`
|
||||
|
||||
- `-P, --password <password>` if address is provided, password will be this argument
|
||||
- `-c, --config` Open termscp starting from the configuration page
|
||||
- `-q, --quiet` Disable logging
|
||||
- `-t, --theme <path>` Import specified theme
|
||||
- `-v, --version` Print version info
|
||||
- `-h, --help` Print help page
|
||||
|
||||
termscp can be started in two different mode, if no extra arguments is provided, termscp will show the authentication form, where the user will be able to provide the parameters required to connect to the remote peer.
|
||||
|
||||
Alternatively, the user can provide an address as argument to skip the authentication form and starting directly the connection to the remote server.
|
||||
|
||||
If address argument is provided you can also provide the start working directory for local host
|
||||
|
||||
### Address argument 🌎
|
||||
|
||||
The address argument has the following syntax:
|
||||
|
||||
```txt
|
||||
[protocol://][username@]<address>[:port][:wrkdir]
|
||||
```
|
||||
|
||||
Let's see some example of this particular syntax, since it's very comfortable and you'll probably going to use this instead of the other one...
|
||||
|
||||
- Connect using default protocol (*defined in configuration*) to 192.168.1.31, port if not provided is default for the selected protocol (in this case depends on your configuration); username is current user's name
|
||||
|
||||
```sh
|
||||
termscp 192.168.1.31
|
||||
```
|
||||
|
||||
- Connect using default protocol (*defined in configuration*) to 192.168.1.31; username is `root`
|
||||
|
||||
```sh
|
||||
termscp root@192.168.1.31
|
||||
```
|
||||
|
||||
- Connect using scp to 192.168.1.31, port is 4022; username is `omar`
|
||||
|
||||
```sh
|
||||
termscp scp://omar@192.168.1.31:4022
|
||||
```
|
||||
|
||||
- Connect using scp to 192.168.1.31, port is 4022; username is `omar`. You will start in directory `/tmp`
|
||||
|
||||
```sh
|
||||
termscp scp://omar@192.168.1.31:4022:/tmp
|
||||
```
|
||||
|
||||
#### How Password can be provided 🔐
|
||||
|
||||
You have probably noticed, that, when providing the address as argument, there's no way to provide the password.
|
||||
Password can be basically provided through 3 ways when address argument is provided:
|
||||
|
||||
- `-P, --password` option: just use this CLI option providing the password. I strongly unrecommend this method, since it's very unsecure (since you might keep the password in the shell history)
|
||||
- Via `sshpass`: you can provide password via `sshpass`, e.g. `sshpass -f ~/.ssh/topsecret.key termscp cvisintin@192.168.1.31`
|
||||
- You will be prompted for it: if you don't use any of the previous methods, you will be prompted for the password, as happens with the more classics tools such as `scp`, `ssh`, etc.
|
||||
|
||||
---
|
||||
|
||||
## File explorer 📂
|
||||
|
||||
When we refer to file explorers in termscp, we refer to the panels you can see after establishing a connection with the remote.
|
||||
These panels are basically 3 (yes, three actually):
|
||||
|
||||
- Local explorer panel: it is displayed on the left of your screen and shows the current directory entries for localhost
|
||||
- Remote explorer panel: it is displayed on the right of your screen and shows the current directory entries for the remote host.
|
||||
- Find results panel: depending on where you're searching for files (local/remote) it will replace the local or the explorer panel. This panel shows the entries matching the search query you performed.
|
||||
|
||||
In order to change panel you need to type `<LEFT>` to move the remote explorer panel and `<RIGHT>` to move back to the local explorer panel. Whenever you are in the find results panel, you need to press `<ESC>` to exit panel and go back to the previous panel.
|
||||
|
||||
### Keybindings ⌨
|
||||
|
||||
| Key | Command | Reminder |
|
||||
|---------------|-------------------------------------------------------|-------------|
|
||||
| `<ESC>` | Disconnect from remote; return to authentication page | |
|
||||
| `<TAB>` | Switch between log tab and explorer | |
|
||||
| `<BACKSPACE>` | Go to previous directory in stack | |
|
||||
| `<RIGHT>` | Move to remote explorer tab | |
|
||||
| `<LEFT>` | Move to local explorer tab | |
|
||||
| `<UP>` | Move up in selected list | |
|
||||
| `<DOWN>` | Move down in selected list | |
|
||||
| `<PGUP>` | Move up in selected list by 8 rows | |
|
||||
| `<PGDOWN>` | Move down in selected list by 8 rows | |
|
||||
| `<ENTER>` | Enter directory | |
|
||||
| `<SPACE>` | Upload / download selected file | |
|
||||
| `<A>` | Toggle hidden files | All |
|
||||
| `<B>` | Sort files by | Bubblesort? |
|
||||
| `<C>` | Copy file/directory | Copy |
|
||||
| `<D>` | Make directory | Directory |
|
||||
| `<E>` | Delete file (Same as `DEL`) | Erase |
|
||||
| `<F>` | Search for files (wild match is supported) | Find |
|
||||
| `<G>` | Go to supplied path | Go to |
|
||||
| `<H>` | Show help | Help |
|
||||
| `<I>` | Show info about selected file or directory | Info |
|
||||
| `<L>` | Reload current directory's content / Clear selection | List |
|
||||
| `<M>` | Select a file | Mark |
|
||||
| `<N>` | Create new file with provided name | New |
|
||||
| `<O>` | Edit file; see Text editor | Open |
|
||||
| `<Q>` | Quit termscp | Quit |
|
||||
| `<R>` | Rename file | Rename |
|
||||
| `<S>` | Save file as... | Save |
|
||||
| `<U>` | Go to parent directory | Upper |
|
||||
| `<V>` | Open file with default program for filetype | View |
|
||||
| `<W>` | Open file with provided program | With |
|
||||
| `<X>` | Execute a command | eXecute |
|
||||
| `<Y>` | Toggle synchronized browsing | sYnc |
|
||||
| `<DEL>` | Delete file | |
|
||||
| `<CTRL+A>` | Select all files | |
|
||||
| `<CTRL+C>` | Abort file transfer process | |
|
||||
|
||||
### Work on multiple files 🥷
|
||||
|
||||
You can opt to work on multiple files, selecting them pressing `<M>`, in order to select the current file, or pressing `<CTRL+A>`, which will select all the files in the working directory.
|
||||
Once a file is marked for selection, it will be displayed with a `*` on the left.
|
||||
When working on selection, only selected file will be processed for actions, while the current highlighted item will be ignored.
|
||||
It is possible to work on multiple files also when in the find result panel.
|
||||
All the actions are available when working with multiple files, but be aware that some actions work in a slightly different way. Let's dive in:
|
||||
|
||||
- *Copy*: whenever you copy a file, you'll be prompted to insert the destination name. When working with multiple file, this name refers to the destination directory where all these files will be copied.
|
||||
- *Rename*: same as copy, but will move files there.
|
||||
- *Save as*: same as copy, but will write them there.
|
||||
|
||||
### Synchronized browsing ⏲️
|
||||
|
||||
When enabled, synchronized browsing, will allow you to synchronize the navigation between the two panels.
|
||||
This means that whenever you'll change the working directory on one panel, the same action will be reproduced on the other panel. If you want to enable synchronized browsing just press `<Y>`; press twice to disable. While enabled, the synchronized browising state will be reported on the status bar on `ON`.
|
||||
|
||||
*Warning*: at the moment, whenever you try to access an unexisting directory, you won't be prompted to create it. This might change in a future update.
|
||||
|
||||
### Open and Open With 🚪
|
||||
|
||||
Open and open with commands are powered by [open-rs](https://docs.rs/crate/open/1.7.0).
|
||||
When opening files with View command (`<V>`), the system default application for the file type will be used. To do so, the default operting system service will be used, so be sure to have at least one of these installed on your system:
|
||||
|
||||
- **Windows** users: you don't have to worry about it, since the crate will use the `start` command.
|
||||
- **MacOS** users: you don't have to worry either, since the crate will use `open`, which is already installed on your system.
|
||||
- **Linux** users: one of these should be installed
|
||||
- *xdg-open*
|
||||
- *gio*
|
||||
- *gnome-open*
|
||||
- *kde-open*
|
||||
- **WSL** users: *wslview* is required, you must install [wslu](https://github.com/wslutilities/wslu).
|
||||
|
||||
> Q: Can I edit remote files using the view command?
|
||||
> A: No, at least not directly from the "remote panel". You have to download it to a local directory first, that's due to the fact that when you open a remote file, the file is downloaded into a temporary directory, but there's no way to create a watcher for the file to check when the program you used to open it was closed, so termscp is not able to know when you're done editing the file.
|
||||
|
||||
---
|
||||
|
||||
## Bookmarks ⭐
|
||||
|
||||
In termscp it is possible to save favourites hosts, which can be then loaded quickly from the main layout of termscp.
|
||||
termscp will also save the last 16 hosts you connected to.
|
||||
This feature allows you to load all the parameters required to connect to a certain remote, simply selecting the bookmark in the tab under the authentication form.
|
||||
|
||||
Bookmarks will be saved, if possible at:
|
||||
|
||||
- `$HOME/.config/termscp/` on Linux/BSD
|
||||
- `$HOME/Library/Application Support/termscp` on MacOs
|
||||
- `FOLDERID_RoamingAppData\termscp\` on Windows
|
||||
|
||||
For bookmarks only (this won't apply to recent hosts) it is also possible to save the password used to authenticate. The password is not saved by default and must be specified through the prompt when saving a new Bookmark.
|
||||
|
||||
> I was very undecided about storing passwords in termscp. The reason? Saving a password on your computer might give access to a hacker to any server you've registered. But I must admit by myself that for many machines typing the password everytime is really boring, also many times I have to work with machines in LAN, which wouldn't provide any advantage to an attacker, So I came out with a good compromise for passwords.
|
||||
|
||||
I warmly suggest you to follow these guidelines in order to decide whether you should or you shouldn't save passwords:
|
||||
|
||||
- **DON'T** save passwords for machines which are exposed on the internet, save passwords only for machines in LAN
|
||||
- Make sure your machine is protected by attackers. If possible encrypt your disk and don't leave your PC unlocked while you're away.
|
||||
- Preferably, save passwords only when a compromising of the target machine wouldn't be a problem.
|
||||
|
||||
In order to create a new bookmark, just follow these steps:
|
||||
|
||||
1. Type in the authentication form the parameters to connect to your remote server
|
||||
2. Press `<CTRL+S>`
|
||||
3. Type in the name you want to give to the bookmark
|
||||
4. Choose whether to remind the password or not
|
||||
5. Press `<ENTER>` to submit
|
||||
|
||||
whenever you want to use the previously saved connection, just press `<TAB>` to navigate to the bookmarks list and load the bookmark parameters into the form pressing `<ENTER>`.
|
||||
|
||||
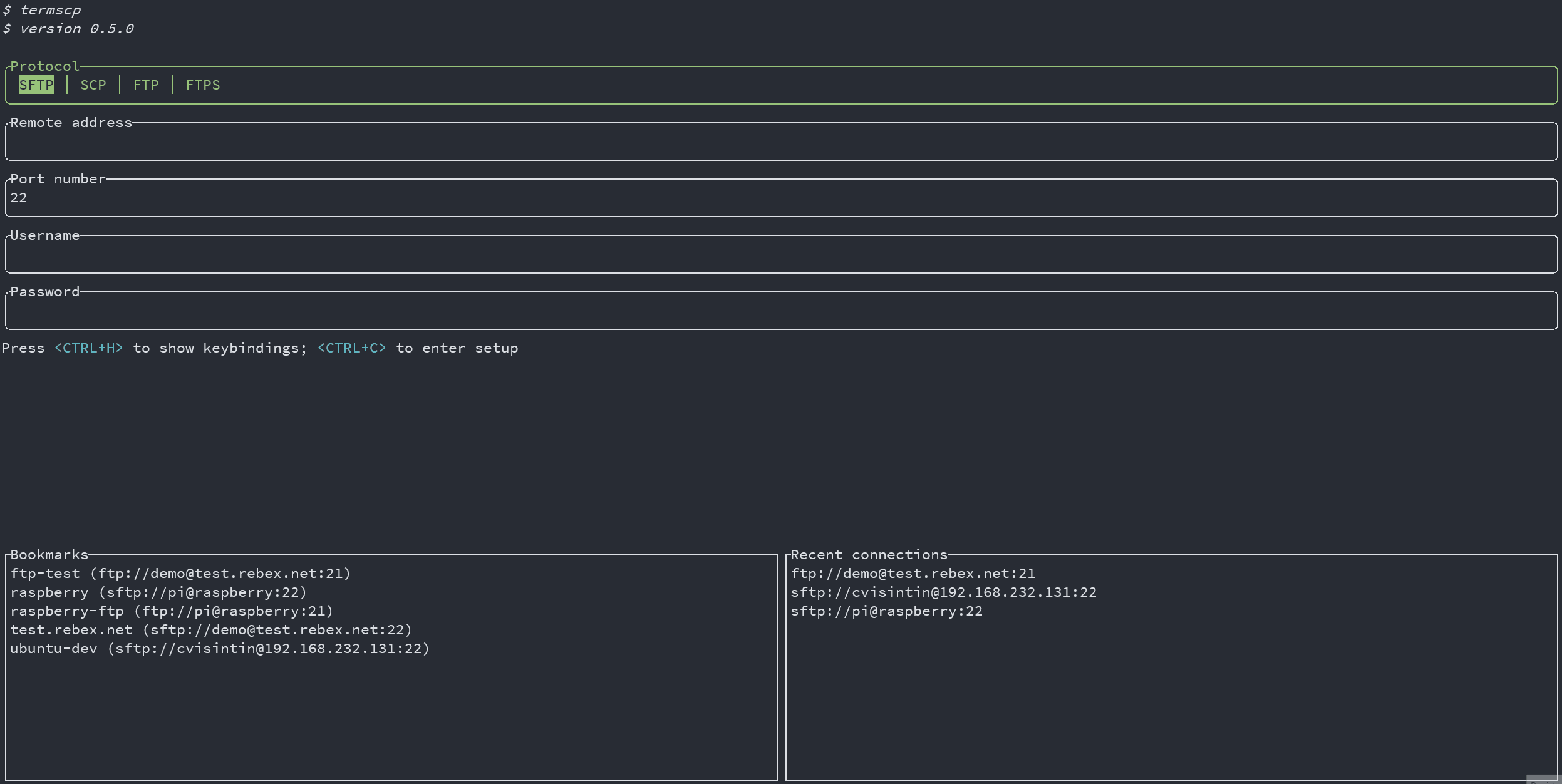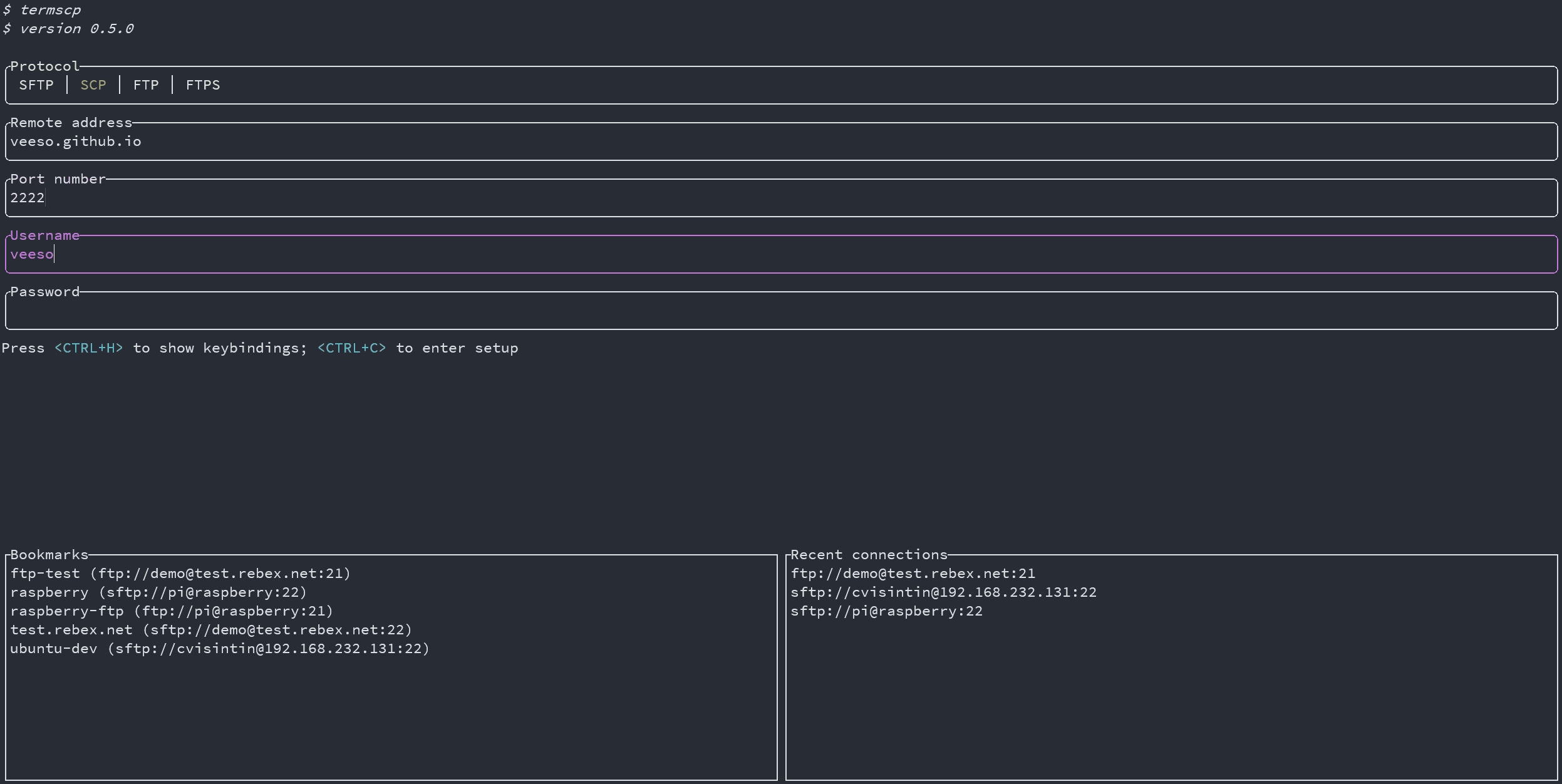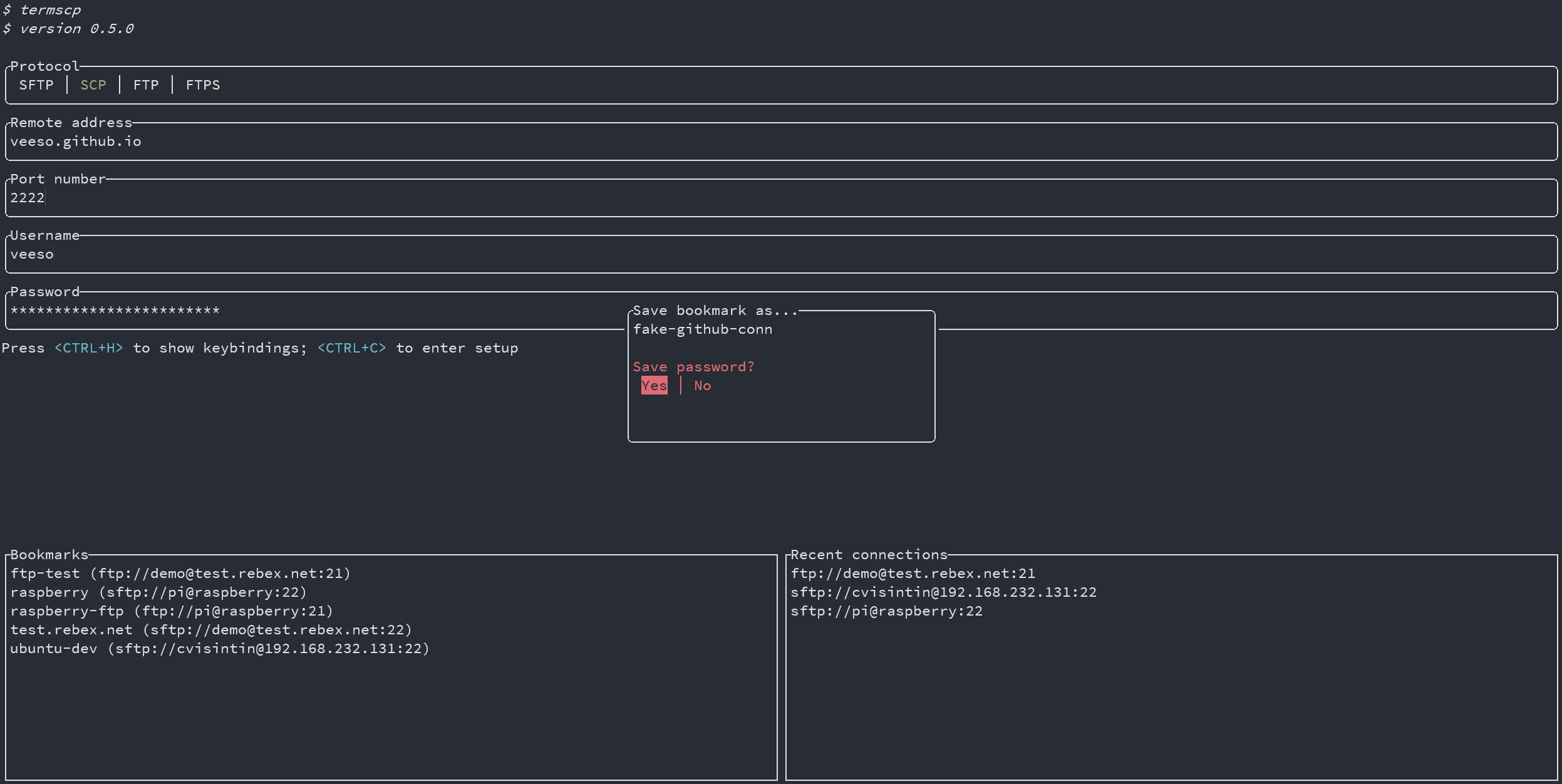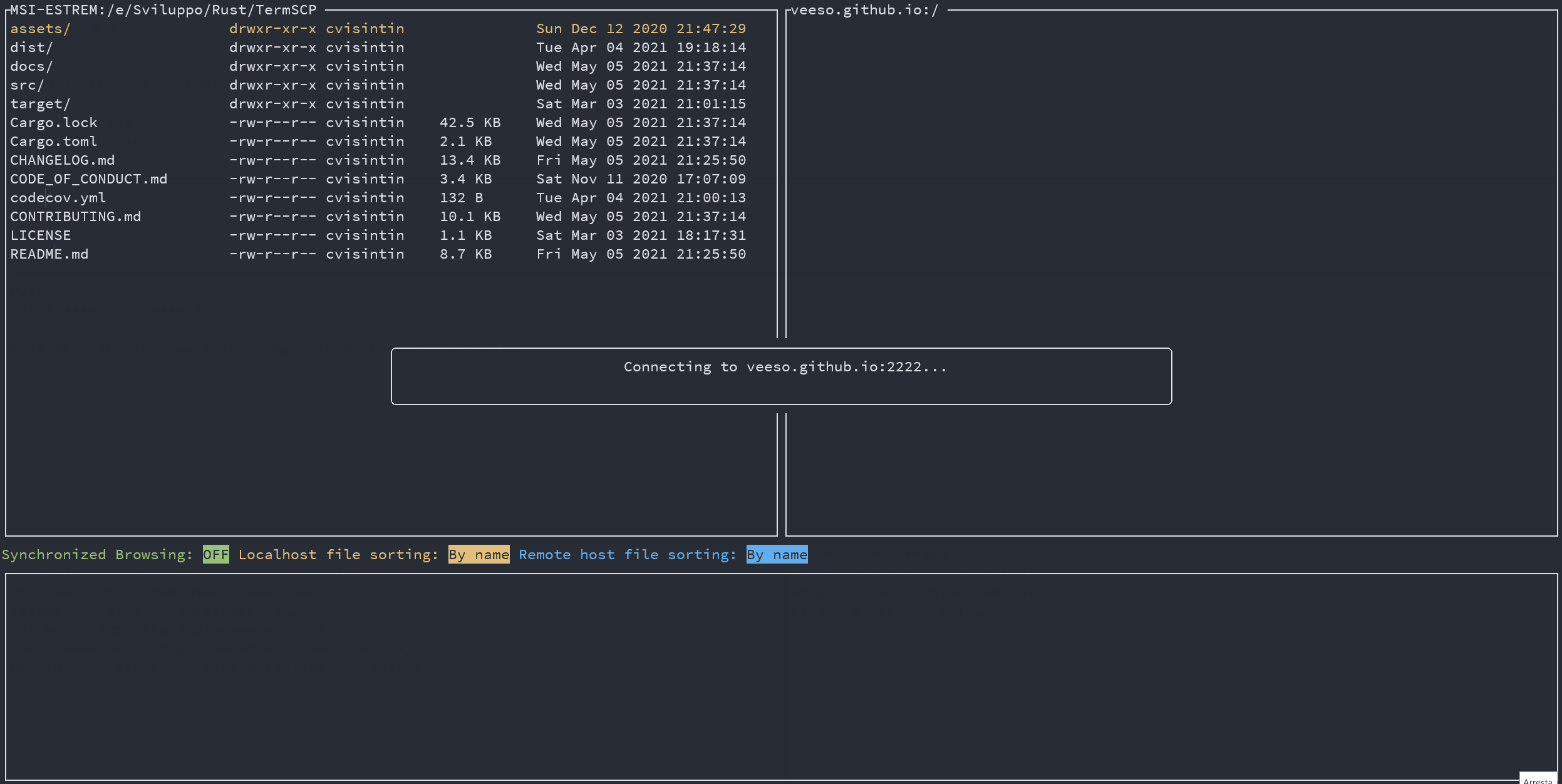
|
||||
|
||||
### Are my passwords Safe 😈
|
||||
|
||||
Well, Yep 😉.
|
||||
As said before, bookmarks are saved in your configuration directory along with passwords. Passwords are obviously not plain text, they are encrypted with **AES-128**. Does this make them safe? Absolutely! (except for BSD and WSL users 😢)
|
||||
|
||||
On **Windows**, **Linux** and **MacOS** the passwords are stored, if possible (but should be), respectively in the *Windows Vault*, in the *system keyring* and into the *Keychain*. This is actually super-safe and is directly managed by your operating system.
|
||||
|
||||
❗ Please, notice that if you're a Linux user, you should really read the [chapter below 👀](#linux-keyring), because the keyring might not be enabled or supported on your system!
|
||||
|
||||
On *BSD* and *WSL*, on the other hand, the key used to encrypt your passwords is stored on your drive (at $HOME/.config/termscp). It is then, still possible to retrieve the key to decrypt passwords. Luckily, the location of the key guarantees your key can't be read by users different from yours, but yeah, I still wouldn't save the password for a server exposed on the internet 😉.
|
||||
|
||||
#### Linux Keyring
|
||||
|
||||
We all love Linux thanks to the freedom it gives to the users. You can basically do anything you want as a Linux user, but this has also some cons, such as the fact that often there is no standard applications across different distributions. And this involves keyring too.
|
||||
This means that on Linux there might be no keyring installed on your system. Unfortunately the library we use to work with the key storage requires a service which exposes `org.freedesktop.secrets` on D-BUS and the worst fact is that there only two services exposing it.
|
||||
|
||||
- ❗ If you use GNOME as desktop environment (e.g. ubuntu users), you should already be fine, since keyring is already provided by `gnome-keyring` and everything should already be working.
|
||||
- ❗ For other desktop environment users there is a nice program you can use to get a keyring which is [KeepassXC](https://keepassxc.org/), which I use on my Manjaro installation (with KDE) and works fine. The only problem is that you have to setup it to be used along with termscp (but it's quite simple). To get started with KeepassXC read more [here](#keepassxc-setup-for-termscp).
|
||||
- ❗ What about you don't want to install any of these services? Well, there's no problem! **termscp will keep working as usual**, but it will save the key in a file, as it usually does for BSD and WSL.
|
||||
|
||||
##### KeepassXC setup for termscp
|
||||
|
||||
Follow these steps in order to setup keepassXC for termscp:
|
||||
|
||||
1. Install KeepassXC
|
||||
2. Go to "tools" > "settings" in toolbar
|
||||
3. Select "Secret service integration" and toggle "Enable KeepassXC freedesktop.org secret service integration"
|
||||
4. Create a database, if you don't have one yet: from toolbar "Database" > "New database"
|
||||
5. From toolbar: "Database" > "Database settings"
|
||||
6. Select "Secret service integration" and toggle "Expose entries under this group"
|
||||
7. Select the group in the list where you want the termscp secret to be kept. Remember that this group might be used by any other application to store secrets via DBUS.
|
||||
|
||||
---
|
||||
|
||||
## Configuration ⚙️
|
||||
|
||||
termscp supports some user defined parameters, which can be defined in the configuration.
|
||||
Underhood termscp has a TOML file and some other directories where all the parameters will be saved, but don't worry, you won't touch any of these files manually, since I made possible to configure termscp from its user interface entirely.
|
||||
|
||||
termscp, like for bookmarks, just requires to have these paths accessible:
|
||||
|
||||
- `$HOME/.config/termscp/` on Linux/BSD
|
||||
- `$HOME/Library/Application Support/termscp` on MacOs
|
||||
- `FOLDERID_RoamingAppData\termscp\` on Windows
|
||||
|
||||
To access configuration, you just have to press `<CTRL+C>` from the home of termscp.
|
||||
|
||||
These parameters can be changed:
|
||||
|
||||
- **Text Editor**: the text editor to use. By default termscp will find the default editor for you; with this option you can force an editor to be used (e.g. `vim`). **Also GUI editors are supported**, unless they `nohup` from the parent process so if you ask: yes, you can use `notepad.exe`, and no: **Visual Studio Code doesn't work**.
|
||||
- **Default Protocol**: the default protocol is the default value for the file transfer protocol to be used in termscp. This applies for the login page and for the address CLI argument.
|
||||
- **Show Hidden Files**: select whether hidden files shall be displayed by default. You will be able to decide whether to show or not hidden files at runtime pressing `A` anyway.
|
||||
- **Check for updates**: if set to `yes`, termscp will fetch the Github API to check if there is a new version of termscp available.
|
||||
- **Group Dirs**: select whether directories should be groupped or not in file explorers. If `Display first` is selected, directories will be sorted using the configured method but displayed before files, viceversa if `Display last` is selected.
|
||||
- **Remote File formatter syntax**: syntax to display file info for each file in the remote explorer. See [File explorer format](#file-explorer-format)
|
||||
- **Local File formatter syntax**: syntax to display file info for each file in the local explorer. See [File explorer format](#file-explorer-format)
|
||||
|
||||
### SSH Key Storage 🔐
|
||||
|
||||
Along with configuration, termscp provides also an **essential** feature for **SFTP/SCP clients**: the SSH key storage.
|
||||
|
||||
You can access the SSH key storage, from configuration moving to the `SSH Keys` tab, once there you can:
|
||||
|
||||
- **Add a new key**: just press `<CTRL+N>` and you will be prompted to create a new key. Provide the hostname/ip address and the username associated to the key and finally a text editor will open up: paste the **PRIVATE** ssh key into the text editor, save and quit.
|
||||
- **Remove an existing key**: just press `<DEL>` or `<CTRL+E>` on the key you want to remove, to delete persistently the key from termscp.
|
||||
- **Edit an existing key**: just press `<ENTER>` on the key you want to edit, to change the private key.
|
||||
|
||||
> Q: Wait, my private key is protected with password, can I use it?
|
||||
> A: Of course you can. The password provided for authentication in termscp, is valid both for username/password authentication and for RSA key authentication.
|
||||
|
||||
### File Explorer Format
|
||||
|
||||
It is possible through configuration to define a custom format for the file explorer. This is possible both for local and remote host, so you can have two different syntax in use. These fields, with name `File formatter syntax (local)` and `File formatter syntax (remote)` will define how the file entries will be displayed in the file explorer.
|
||||
The syntax for the formatter is the following `{KEY1}... {KEY2:LENGTH}... {KEY3:LENGTH:EXTRA} {KEYn}...`.
|
||||
Each key in bracket will be replaced with the related attribute, while everything outside brackets will be left unchanged.
|
||||
|
||||
- The key name is mandatory and must be one of the keys below
|
||||
- The length describes the length reserved to display the field. Static attributes doesn't support this (GROUP, PEX, SIZE, USER)
|
||||
- Extra is supported only by some parameters and is an additional options. See keys to check if extra is supported.
|
||||
|
||||
These are the keys supported by the formatter:
|
||||
|
||||
- `ATIME`: Last access time (with default syntax `%b %d %Y %H:%M`); Extra might be provided as the time syntax (e.g. `{ATIME:8:%H:%M}`)
|
||||
- `CTIME`: Creation time (with syntax `%b %d %Y %H:%M`); Extra might be provided as the time syntax (e.g. `{CTIME:8:%H:%M}`)
|
||||
- `GROUP`: Owner group
|
||||
- `MTIME`: Last change time (with syntax `%b %d %Y %H:%M`); Extra might be provided as the time syntax (e.g. `{MTIME:8:%H:%M}`)
|
||||
- `NAME`: File name (Elided if longer than 24)
|
||||
- `PEX`: File permissions (UNIX format)
|
||||
- `SIZE`: File size (omitted for directories)
|
||||
- `SYMLINK`: Symlink (if any `-> {FILE_PATH}`)
|
||||
- `USER`: Owner user
|
||||
|
||||
If left empty, the default formatter syntax will be used: `{NAME:24} {PEX} {USER} {SIZE} {MTIME:17:%b %d %Y %H:%M}`
|
||||
|
||||
---
|
||||
|
||||
## Themes 🎨
|
||||
|
||||
Termscp provides you with an awesome feature: the possibility to set the colors for several components in the application.
|
||||
If you want to customize termscp there are two available ways to do so:
|
||||
|
||||
- From the **configuration menu**
|
||||
- Importing a **theme file**
|
||||
|
||||
In order to create your own customization from termscp, all you have to do so is to enter the configuration from the auth activity, pressing `<CTRL+C>` and then `<TAB>` twice. You should have now moved to the `themes` panel.
|
||||
|
||||
Here you can move with `<UP>` and `<DOWN>` to change the style you want to change, as shown in the gif below:
|
||||
|
||||

|
||||
|
||||
termscp supports both the traditional explicit hex (`#rrggbb`) and rgb `rgb(r, g, b)` syntax to provide colors, but also **[css colors](https://www.w3schools.com/cssref/css_colors.asp)** (such as `crimson`) are accepted 😉. There is also a special keywork which is `Default`. Default means that the color used will be the default foreground or background color based on the situation (foreground for texts and lines, background for well, guess what).
|
||||
|
||||
As said before, you can also import theme files. You can take inspiration from or directly use one of the themes provided along with termscp, located in the `themes/` directory of this repository and import them running termscp as `termscp -t <theme_file>`. If everything was fine, it should tell you the theme has successfully been imported.
|
||||
|
||||
### Styles 💈
|
||||
|
||||
You can find in the table below, the description for each style field.
|
||||
Please, notice that **styles won't apply to configuration page**, in order to make it always accessible in case you mess everything up
|
||||
|
||||
#### Authentication page
|
||||
|
||||
| Key | Description |
|
||||
|----------------|------------------------------------------|
|
||||
| auth_address | Color of the input field for IP address |
|
||||
| auth_bookmarks | Color of the bookmarks panel |
|
||||
| auth_password | Color of the input field for password |
|
||||
| auth_port | Color of the input field for port number |
|
||||
| auth_protocol | Color of the radio group for protocol |
|
||||
| auth_recents | Color of the recents panel |
|
||||
| auth_username | Color of the input field for username |
|
||||
|
||||
#### Transfer page
|
||||
|
||||
| Key | Description |
|
||||
|--------------------------------------|---------------------------------------------------------------------------|
|
||||
| transfer_local_explorer_background | Background color of localhost explorer |
|
||||
| transfer_local_explorer_foreground | Foreground coloor of localhost explorer |
|
||||
| transfer_local_explorer_highlighted | Border and highlighted color for localhost explorer |
|
||||
| transfer_remote_explorer_background | Background color of remote explorer |
|
||||
| transfer_remote_explorer_foreground | Foreground coloor of remote explorer |
|
||||
| transfer_remote_explorer_highlighted | Border and highlighted color for remote explorer |
|
||||
| transfer_log_background | Background color for log panel |
|
||||
| transfer_log_window | Window color for log panel |
|
||||
| transfer_progress_bar_partial | Partial progress bar color |
|
||||
| transfer_progress_bar_total | Total progress bar color |
|
||||
| transfer_status_hidden | Color for status bar "hidden" label |
|
||||
| transfer_status_sorting | Color for status bar "sorting" label; applies also to file sorting dialog |
|
||||
| transfer_status_sync_browsing | Color for status bar "sync browsing" label |
|
||||
|
||||
#### Misc
|
||||
|
||||
These styles applie to different part of the application.
|
||||
|
||||
| Key | Description |
|
||||
|-------------------|---------------------------------------------|
|
||||
| misc_error_dialog | Color for error messages |
|
||||
| misc_input_dialog | Color for input dialogs (such as copy file) |
|
||||
| misc_keys | Color of text for key strokes |
|
||||
| misc_quit_dialog | Color for quit dialogs |
|
||||
| misc_save_dialog | Color for save dialogs |
|
||||
| misc_warn_dialog | Color for warn dialogs |
|
||||
|
||||
---
|
||||
|
||||
## Text Editor ✏
|
||||
|
||||
termscp has, as you might have noticed, many features, one of these is the possibility to view and edit text file. It doesn't matter if the file is located on the local host or on the remote host, termscp provides the possibility to open a file in your favourite text editor.
|
||||
In case the file is located on remote host, the file will be first downloaded into your temporary file directory and then, **only** if changes were made to the file, re-uploaded to the remote host. termscp checks if you made changes to the file verifying the last modification time of the file.
|
||||
|
||||
Just a reminder: **you can edit only textual file**; binary files are not supported.
|
||||
|
||||
### How do I configure the text editor 🦥
|
||||
|
||||
Text editor is automatically found using this [awesome crate](https://github.com/milkey-mouse/edit), if you want to change the text editor to use, change it in termscp configuration. [Read more](#configuration-️)
|
||||
|
||||
---
|
||||
|
||||
## Logging 🩺
|
||||
|
||||
termscp writes a log file for each session, which is written at
|
||||
|
||||
- `$HOME/.config/termscp/termscp.log` on Linux/BSD
|
||||
- `$HOME/Library/Application Support/termscp/termscp.log` on MacOs
|
||||
- `FOLDERID_RoamingAppData\termscp\termscp.log` on Windows
|
||||
|
||||
the log won't be rotated, but will just be truncated after each launch of termscp, so if you want to report an issue and you want to attach your log file, keep in mind to save the log file in a safe place before using termscp again.
|
||||
The log file always reports in *trace* level, so it is kinda verbose.
|
||||
I know you might have some questions regarding log files, so I made a kind of a Q/A:
|
||||
|
||||
> Is it possible to reduce verbosity?
|
||||
|
||||
No. The reason is quite simple: when an issue happens, you must be able to know what's causing it and the only way to do that, is to have the log file with the maximum verbosity level set.
|
||||
|
||||
> If trace level is set for logging, is the file going to reach a huge size?
|
||||
|
||||
Probably not, unless you never quit termscp, but I think that's likely to happne. A long session may produce up to 10MB of log files (I said a long session), but I think a normal session won't exceed 2MB.
|
||||
|
||||
> I don't want logging, can I turn it off?
|
||||
|
||||
Yes, you can. Just start termscp with `-q or --quiet` option. You can alias termscp to make it persistent. Remember that logging is used to diagnose issues, so since behind every open source project, there should always be this kind of mutual help, keeping log files might be your way to support the project 😉. I don't want you to feel guilty, but just to say.
|
||||
|
||||
> Is logging safe?
|
||||
|
||||
If you're concerned about security, the log file doesn't contain any plain password, so don't worry and exposes the same information the sibling file `bookmarks` reports.
|
||||
454
install.sh
Executable file
@@ -0,0 +1,454 @@
|
||||
#!/usr/bin/env sh
|
||||
|
||||
# Options
|
||||
#
|
||||
# -V, --verbose
|
||||
# Enable verbose output for the installer
|
||||
#
|
||||
# -f, -y, --force, --yes
|
||||
# Skip the confirmation prompt during installation
|
||||
|
||||
TERMSCP_VERSION="0.6.1"
|
||||
GITHUB_URL="https://github.com/veeso/termscp/releases/download/v${TERMSCP_VERSION}"
|
||||
DEB_URL="${GITHUB_URL}/termscp_${TERMSCP_VERSION}_amd64.deb"
|
||||
RPM_URL="${GITHUB_URL}/termscp-${TERMSCP_VERSION}-1.x86_64.rpm"
|
||||
|
||||
set -eu
|
||||
printf "\n"
|
||||
|
||||
BOLD="$(tput bold 2>/dev/null || printf '')"
|
||||
GREY="$(tput setaf 0 2>/dev/null || printf '')"
|
||||
UNDERLINE="$(tput smul 2>/dev/null || printf '')"
|
||||
RED="$(tput setaf 1 2>/dev/null || printf '')"
|
||||
GREEN="$(tput setaf 2 2>/dev/null || printf '')"
|
||||
YELLOW="$(tput setaf 3 2>/dev/null || printf '')"
|
||||
BLUE="$(tput setaf 4 2>/dev/null || printf '')"
|
||||
MAGENTA="$(tput setaf 5 2>/dev/null || printf '')"
|
||||
NO_COLOR="$(tput sgr0 2>/dev/null || printf '')"
|
||||
|
||||
# Functions
|
||||
|
||||
info() {
|
||||
printf '%s\n' "${BOLD}${GREY}>${NO_COLOR} $*"
|
||||
}
|
||||
|
||||
warn() {
|
||||
printf '%s\n' "${YELLOW}! $*${NO_COLOR}"
|
||||
}
|
||||
|
||||
error() {
|
||||
printf '%s\n' "${RED}x $*${NO_COLOR}" >&2
|
||||
}
|
||||
|
||||
completed() {
|
||||
printf '%s\n' "${GREEN}✓${NO_COLOR} $*"
|
||||
}
|
||||
|
||||
has() {
|
||||
command -v "$1" 1>/dev/null 2>&1
|
||||
}
|
||||
|
||||
get_tmpfile() {
|
||||
local suffix
|
||||
suffix="$1"
|
||||
if has mktemp; then
|
||||
printf "%s.%s" "$(mktemp)" "${suffix}"
|
||||
else
|
||||
# No really good options here--let's pick a default + hope
|
||||
printf "/tmp/termscp.%s" "${suffix}"
|
||||
fi
|
||||
}
|
||||
|
||||
download() {
|
||||
output="$1"
|
||||
url="$2"
|
||||
|
||||
if has curl; then
|
||||
cmd="curl --fail --silent --location --output $output $url"
|
||||
elif has wget; then
|
||||
cmd="wget --quiet --output-document=$output $url"
|
||||
elif has fetch; then
|
||||
cmd="fetch --quiet --output=$output $url"
|
||||
else
|
||||
error "No HTTP download program (curl, wget, fetch) found, exiting…"
|
||||
return 1
|
||||
fi
|
||||
$cmd && return 0 || rc=$?
|
||||
|
||||
error "Command failed (exit code $rc): ${BLUE}${cmd}${NO_COLOR}"
|
||||
warn "If you believe this is a bug, please report immediately an issue to <https://github.com/veeso/termscp/issues/new>"
|
||||
return $rc
|
||||
}
|
||||
|
||||
test_writeable() {
|
||||
local path
|
||||
path="${1:-}/test.txt"
|
||||
if touch "${path}" 2>/dev/null; then
|
||||
rm "${path}"
|
||||
return 0
|
||||
else
|
||||
return 1
|
||||
fi
|
||||
}
|
||||
|
||||
elevate_priv() {
|
||||
if ! has sudo; then
|
||||
error 'Could not find the command "sudo", needed to install termscp on your system.'
|
||||
info "If you are on Windows, please run your shell as an administrator, then"
|
||||
info "rerun this script. Otherwise, please run this script as root, or install"
|
||||
info "sudo."
|
||||
exit 1
|
||||
fi
|
||||
if ! sudo -v; then
|
||||
error "Superuser not granted, aborting installation"
|
||||
exit 1
|
||||
fi
|
||||
}
|
||||
|
||||
elevate_priv_ex() {
|
||||
check_dir="$1"
|
||||
if test_writeable "$check_dir"; then
|
||||
sudo=""
|
||||
else
|
||||
warn "Root permissions are required to install dependecies"
|
||||
elevate_priv
|
||||
sudo="sudo"
|
||||
fi
|
||||
echo $sudo
|
||||
}
|
||||
|
||||
# Currently supporting:
|
||||
# - macos
|
||||
# - linux
|
||||
# - freebsd
|
||||
detect_platform() {
|
||||
local platform
|
||||
platform="$(uname -s | tr '[:upper:]' '[:lower:]')"
|
||||
|
||||
case "${platform}" in
|
||||
linux) platform="linux" ;;
|
||||
darwin) platform="macos" ;;
|
||||
freebsd) platform="freebsd" ;;
|
||||
esac
|
||||
|
||||
printf '%s' "${platform}"
|
||||
}
|
||||
|
||||
# Currently supporting:
|
||||
# - x86_64
|
||||
detect_arch() {
|
||||
local arch
|
||||
arch="$(uname -m | tr '[:upper:]' '[:lower:]')"
|
||||
|
||||
case "${arch}" in
|
||||
amd64) arch="x86_64" ;;
|
||||
armv*) arch="arm" ;;
|
||||
arm64) arch="aarch64" ;;
|
||||
esac
|
||||
|
||||
# `uname -m` in some cases mis-reports 32-bit OS as 64-bit, so double check
|
||||
if [ "${arch}" = "x86_64" ] && [ "$(getconf LONG_BIT)" -eq 32 ]; then
|
||||
arch="i686"
|
||||
elif [ "${arch}" = "aarch64" ] && [ "$(getconf LONG_BIT)" -eq 32 ]; then
|
||||
arch="arm"
|
||||
fi
|
||||
|
||||
if [ "${arch}" != "x86_64" ]; then
|
||||
error "Unsupported arch ${arch}"
|
||||
return 1
|
||||
fi
|
||||
|
||||
printf '%s' "${arch}"
|
||||
}
|
||||
|
||||
confirm() {
|
||||
if [ -z "${FORCE-}" ]; then
|
||||
printf "%s " "${MAGENTA}?${NO_COLOR} $* ${BOLD}[y/N]${NO_COLOR}"
|
||||
set +e
|
||||
read -r yn </dev/tty
|
||||
rc=$?
|
||||
set -e
|
||||
if [ $rc -ne 0 ]; then
|
||||
error "Error reading from prompt (please re-run with the '--yes' option)"
|
||||
exit 1
|
||||
fi
|
||||
if [ "$yn" != "y" ] && [ "$yn" != "yes" ]; then
|
||||
error 'Aborting (please answer "yes" to continue)'
|
||||
exit 1
|
||||
fi
|
||||
fi
|
||||
}
|
||||
|
||||
# Installers
|
||||
|
||||
install_on_bsd() {
|
||||
try_with_cargo "packages for freeBSD are distribuited no more. Only cargo installations are supported."
|
||||
}
|
||||
|
||||
install_on_arch_linux() {
|
||||
pkg="$1"
|
||||
info "Detected ${YELLOW}${pkg}${NO_COLOR} on your system"
|
||||
confirm "${YELLOW}rust${NO_COLOR} is required to install ${GREEN}termscp${NO_COLOR}; would you like to proceed?"
|
||||
$pkg -S rust
|
||||
info "Installing ${GREEN}termscp${NO_COLOR} AUR package…"
|
||||
$pkg -S termscp
|
||||
}
|
||||
|
||||
install_on_linux() {
|
||||
local msg
|
||||
local sudo
|
||||
local archive
|
||||
if has yay; then
|
||||
install_on_arch_linux yay
|
||||
elif has pakku; then
|
||||
install_on_arch_linux pakku
|
||||
elif has paru; then
|
||||
install_on_arch_linux paru
|
||||
elif has aurutils; then
|
||||
install_on_arch_linux aurutils
|
||||
elif has pamac; then
|
||||
install_on_arch_linux pamac
|
||||
elif has pikaur; then
|
||||
install_on_arch_linux pikaur
|
||||
elif has dpkg; then
|
||||
if [ "${ARCH}" != "x86_64" ]; then # It's okay on AUR; not on other distros
|
||||
try_with_cargo "we don't distribute packages for ${ARCH} at the moment"
|
||||
else
|
||||
info "Detected dpkg on your system"
|
||||
info "Installing ${GREEN}termscp${NO_COLOR} via Debian package"
|
||||
archive=$(get_tmpfile "deb")
|
||||
download "${archive}" "${DEB_URL}"
|
||||
info "Downloaded debian package to ${archive}"
|
||||
if test_writeable "/usr/bin"; then
|
||||
sudo=""
|
||||
msg="Installing ${GREEN}termscp${NO_COLOR}, please wait…"
|
||||
else
|
||||
warn "Root permissions are required to install ${GREEN}termscp${NO_COLOR}…"
|
||||
elevate_priv
|
||||
sudo="sudo"
|
||||
msg="Installing ${GREEN}termscp${NO_COLOR} as root, please wait…"
|
||||
fi
|
||||
info "$msg"
|
||||
$sudo dpkg -i "${archive}"
|
||||
fi
|
||||
elif has rpm; then
|
||||
if [ "${ARCH}" != "x86_64" ]; then # It's okay on AUR; not on other distros
|
||||
try_with_cargo "we don't distribute packages for ${ARCH} at the moment"
|
||||
else
|
||||
info "Detected rpm on your system"
|
||||
info "Installing ${GREEN}termscp${NO_COLOR} via RPM package"
|
||||
archive=$(get_tmpfile "rpm")
|
||||
download "${archive}" "${RPM_URL}"
|
||||
info "Downloaded rpm package to ${archive}"
|
||||
if test_writeable "/usr/bin"; then
|
||||
sudo=""
|
||||
msg="Installing ${GREEN}termscp${NO_COLOR}, please wait…"
|
||||
else
|
||||
warn "Root permissions are required to install ${GREEN}termscp${NO_COLOR}…"
|
||||
elevate_priv
|
||||
sudo="sudo"
|
||||
msg="Installing ${GREEN}termscp${NO_COLOR} as root, please wait…"
|
||||
fi
|
||||
info "$msg"
|
||||
$sudo rpm -U "${archive}"
|
||||
fi
|
||||
else
|
||||
try_with_cargo "No suitable installation method found for your Linux distribution; if you're running on Arch linux, please install an AUR package manager (such as yay). Currently only Arch, Debian based and Red Hat based distros are supported"
|
||||
fi
|
||||
}
|
||||
|
||||
install_on_macos() {
|
||||
if has brew; then
|
||||
if has termscp; then
|
||||
info "Upgrading ${GREEN}termscp${NO_COLOR}…"
|
||||
# The OR is used since someone could have installed via cargo previously
|
||||
brew update && brew upgrade termscp || brew install veeso/termscp/termscp
|
||||
else
|
||||
info "Installing ${GREEN}termscp${NO_COLOR}…"
|
||||
brew install veeso/termscp/termscp
|
||||
fi
|
||||
else
|
||||
try_with_cargo "brew is missing on your system; please install it from <https://brew.sh/>"
|
||||
fi
|
||||
}
|
||||
|
||||
# -- cargo installation
|
||||
|
||||
install_bsd_cargo_deps() {
|
||||
set -e
|
||||
confirm "${YELLOW}libssh, gcc${NO_COLOR} are required to install ${GREEN}termscp${NO_COLOR}; would you like to proceed?"
|
||||
sudo="$(elevate_priv_ex /usr/local/bin)"
|
||||
$sudo pkg install -y curl wget libssh gcc
|
||||
info "Dependencies installed successfully"
|
||||
}
|
||||
|
||||
install_linux_cargo_deps() {
|
||||
local debian_deps="gcc pkg-config libssl-dev libssh2-1-dev libdbus-1-dev"
|
||||
local rpm_deps="gcc openssl pkgconfig libdbus-devel openssl-devel"
|
||||
local arch_deps="gcc openssl pkg-config dbus"
|
||||
local deps_cmd=""
|
||||
# Get pkg manager
|
||||
if has apt; then
|
||||
deps_cmd="apt install -y $debian_deps"
|
||||
elif has apt-get; then
|
||||
deps_cmd="apt-get install -y $debian_deps"
|
||||
elif has yum; then
|
||||
deps_cmd="yum -y install $rpm_deps"
|
||||
elif has dnf; then
|
||||
deps_cmd="dnf -y install $rpm_deps"
|
||||
elif has pacman; then
|
||||
deps_cmd="pacman -S --noconfirm $arch_deps"
|
||||
else
|
||||
error "Could not find any suitable package manager for your linux distro 🙄"
|
||||
error "Supported package manager are: 'apt', 'apt-get', 'yum', 'dnf', 'pacman'"
|
||||
exit 1
|
||||
fi
|
||||
set -e
|
||||
confirm "${YELLOW}libssh, gcc, openssl, pkg-config, libdbus${NO_COLOR} are required to install ${GREEN}termscp${NO_COLOR}. The following command will be used to install the dependencies: '${BOLD}${YELLOW}${deps_cmd}${NO_COLOR}'. Would you like to proceed?"
|
||||
sudo="$(elevate_priv_ex /usr/local/bin)"
|
||||
$sudo $deps_cmd
|
||||
info "Dependencies installed successfully"
|
||||
}
|
||||
|
||||
install_cargo() {
|
||||
if has cargo; then
|
||||
return 0
|
||||
fi
|
||||
cargo_env="$HOME/.cargo/env"
|
||||
# Check if cargo is already installed (actually), but not loaded
|
||||
if [ -f $cargo_env ]; then
|
||||
. $cargo_env
|
||||
fi
|
||||
# Check again cargo
|
||||
if has cargo; then
|
||||
return 0
|
||||
else
|
||||
confirm "${YELLOW}rust${NO_COLOR} is required to build termscp with cargo; would you like to install it now?"
|
||||
set -e
|
||||
rustup=$(get_tmpfile "sh")
|
||||
info "Downloading rustup.sh…"
|
||||
download "${rustup}" "https://sh.rustup.rs"
|
||||
chmod +x $rustup
|
||||
$rustup -y
|
||||
info "Rust installed with success"
|
||||
. $cargo_env
|
||||
fi
|
||||
|
||||
}
|
||||
|
||||
try_with_cargo() {
|
||||
err="$1"
|
||||
# Install cargo
|
||||
install_cargo
|
||||
if has cargo; then
|
||||
info "Installing ${GREEN}termscp${NO_COLOR} via Cargo…"
|
||||
case $PLATFORM in
|
||||
"freebsd")
|
||||
install_bsd_cargo_deps
|
||||
cargo install --no-default-features termscp
|
||||
;;
|
||||
|
||||
"linux")
|
||||
install_linux_cargo_deps
|
||||
cargo install termscp
|
||||
;;
|
||||
|
||||
*)
|
||||
cargo install termscp
|
||||
;;
|
||||
|
||||
esac
|
||||
else
|
||||
error "$err"
|
||||
error "Alternatively you can opt for installing Cargo <https://www.rust-lang.org/tools/install>"
|
||||
return 1
|
||||
fi
|
||||
}
|
||||
|
||||
# defaults
|
||||
if [ -z "${PLATFORM-}" ]; then
|
||||
PLATFORM="$(detect_platform)"
|
||||
fi
|
||||
|
||||
if [ -z "${BIN_DIR-}" ]; then
|
||||
BIN_DIR=/usr/local/bin
|
||||
fi
|
||||
|
||||
if [ -z "${ARCH-}" ]; then
|
||||
ARCH="$(detect_arch)"
|
||||
fi
|
||||
|
||||
if [ -z "${BASE_URL-}" ]; then
|
||||
BASE_URL="https://github.com/starship/starship/releases"
|
||||
fi
|
||||
|
||||
# parse argv variables
|
||||
while [ "$#" -gt 0 ]; do
|
||||
case "$1" in
|
||||
|
||||
-V | --verbose)
|
||||
VERBOSE=1
|
||||
shift 1
|
||||
;;
|
||||
-f | -y | --force | --yes)
|
||||
FORCE=1
|
||||
shift 1
|
||||
;;
|
||||
-V=* | --verbose=*)
|
||||
VERBOSE="${1#*=}"
|
||||
shift 1
|
||||
;;
|
||||
-f=* | -y=* | --force=* | --yes=*)
|
||||
FORCE="${1#*=}"
|
||||
shift 1
|
||||
;;
|
||||
|
||||
*)
|
||||
error "Unknown option: $1"
|
||||
exit 1
|
||||
;;
|
||||
esac
|
||||
done
|
||||
|
||||
printf " %s\n" "${UNDERLINE}Termscp configuration${NO_COLOR}"
|
||||
info "${BOLD}Platform${NO_COLOR}: ${GREEN}${PLATFORM}${NO_COLOR}"
|
||||
info "${BOLD}Arch${NO_COLOR}: ${GREEN}${ARCH}${NO_COLOR}"
|
||||
|
||||
# non-empty VERBOSE enables verbose untarring
|
||||
if [ -n "${VERBOSE-}" ]; then
|
||||
VERBOSE=v
|
||||
info "${BOLD}Verbose${NO_COLOR}: yes"
|
||||
else
|
||||
VERBOSE=
|
||||
fi
|
||||
|
||||
printf "\n"
|
||||
|
||||
confirm "Install ${GREEN}termscp ${TERMSCP_VERSION}${NO_COLOR}?"
|
||||
|
||||
# Installation based on arch
|
||||
case $PLATFORM in
|
||||
"freebsd")
|
||||
install_on_bsd
|
||||
;;
|
||||
"linux")
|
||||
install_on_linux
|
||||
;;
|
||||
"macos")
|
||||
install_on_macos
|
||||
;;
|
||||
*)
|
||||
error "${PLATFORM} is not supported by this installer"
|
||||
exit 1
|
||||
;;
|
||||
esac
|
||||
|
||||
completed "Congratulations! Termscp has successfully been installed on your system!"
|
||||
info "If you're a new user, you might be interested in reading the user manual <https://veeso.github.io/termscp/#user-manual>"
|
||||
info "While if you've just updated your termscp version, you can find the changelog at this link <https://veeso.github.io/termscp/#changelog>"
|
||||
info "Remember that if you encounter any issue, you can report them on Github <https://github.com/veeso/termscp/issues/new>"
|
||||
info "Feel free to open an issue also if you have an idea which could improve the project"
|
||||
info "If you want to support the project, please, consider a little donation <https://www.buymeacoffee.com/veeso>"
|
||||
info "I hope you'll enjoy using termscp :D"
|
||||
|
||||
exit 0
|
||||
@@ -26,15 +26,16 @@
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// Deps
|
||||
use crate::filetransfer::FileTransferProtocol;
|
||||
use crate::filetransfer::{FileTransferParams, FileTransferProtocol};
|
||||
use crate::host::{HostError, Localhost};
|
||||
use crate::system::config_client::ConfigClient;
|
||||
use crate::system::environment;
|
||||
use crate::system::theme_provider::ThemeProvider;
|
||||
use crate::ui::activities::{
|
||||
auth_activity::AuthActivity, filetransfer_activity::FileTransferActivity,
|
||||
setup_activity::SetupActivity, Activity, ExitReason,
|
||||
auth::AuthActivity, filetransfer::FileTransferActivity, setup::SetupActivity, Activity,
|
||||
ExitReason,
|
||||
};
|
||||
use crate::ui::context::{Context, FileTransferParams};
|
||||
use crate::ui::context::Context;
|
||||
|
||||
// Namespaces
|
||||
use std::path::{Path, PathBuf};
|
||||
@@ -56,6 +57,7 @@ pub enum NextActivity {
|
||||
pub struct ActivityManager {
|
||||
context: Option<Context>,
|
||||
interval: Duration,
|
||||
local_dir: PathBuf,
|
||||
}
|
||||
|
||||
impl ActivityManager {
|
||||
@@ -64,19 +66,20 @@ impl ActivityManager {
|
||||
/// Initializes a new Activity Manager
|
||||
pub fn new(local_dir: &Path, interval: Duration) -> Result<ActivityManager, HostError> {
|
||||
// Prepare Context
|
||||
let host: Localhost = match Localhost::new(local_dir.to_path_buf()) {
|
||||
Ok(h) => h,
|
||||
Err(e) => return Err(e),
|
||||
};
|
||||
// Initialize configuration client
|
||||
let (config_client, error): (Option<ConfigClient>, Option<String>) =
|
||||
let (config_client, error): (ConfigClient, Option<String>) =
|
||||
match Self::init_config_client() {
|
||||
Ok(cli) => (Some(cli), None),
|
||||
Err(err) => (None, Some(err)),
|
||||
Ok(cli) => (cli, None),
|
||||
Err(err) => {
|
||||
error!("Failed to initialize config client: {}", err);
|
||||
(ConfigClient::degraded(), Some(err))
|
||||
}
|
||||
};
|
||||
let ctx: Context = Context::new(host, config_client, error);
|
||||
let theme_provider: ThemeProvider = Self::init_theme_provider();
|
||||
let ctx: Context = Context::new(config_client, theme_provider, error);
|
||||
Ok(ActivityManager {
|
||||
context: Some(ctx),
|
||||
local_dir: local_dir.to_path_buf(),
|
||||
interval,
|
||||
})
|
||||
}
|
||||
@@ -84,24 +87,9 @@ impl ActivityManager {
|
||||
/// ### set_filetransfer_params
|
||||
///
|
||||
/// Set file transfer params
|
||||
pub fn set_filetransfer_params(
|
||||
&mut self,
|
||||
address: String,
|
||||
port: u16,
|
||||
protocol: FileTransferProtocol,
|
||||
username: Option<String>,
|
||||
password: Option<String>,
|
||||
entry_directory: Option<PathBuf>,
|
||||
) {
|
||||
pub fn set_filetransfer_params(&mut self, params: FileTransferParams) {
|
||||
// Put params into the context
|
||||
self.context.as_mut().unwrap().ft_params = Some(FileTransferParams {
|
||||
address,
|
||||
port,
|
||||
protocol,
|
||||
username,
|
||||
password,
|
||||
entry_directory,
|
||||
});
|
||||
self.context.as_mut().unwrap().set_ftparams(params);
|
||||
}
|
||||
|
||||
/// ### run
|
||||
@@ -133,6 +121,7 @@ impl ActivityManager {
|
||||
/// Returns when activity terminates.
|
||||
/// Returns the next activity to run
|
||||
fn run_authentication(&mut self) -> Option<NextActivity> {
|
||||
info!("Starting AuthActivity...");
|
||||
// Prepare activity
|
||||
let mut activity: AuthActivity = AuthActivity::default();
|
||||
// Prepare result
|
||||
@@ -140,7 +129,10 @@ impl ActivityManager {
|
||||
// Get context
|
||||
let ctx: Context = match self.context.take() {
|
||||
Some(ctx) => ctx,
|
||||
None => return None,
|
||||
None => {
|
||||
error!("Failed to start AuthActivity: context is None");
|
||||
return None;
|
||||
}
|
||||
};
|
||||
// Create activity
|
||||
activity.on_create(ctx);
|
||||
@@ -151,16 +143,19 @@ impl ActivityManager {
|
||||
if let Some(exit_reason) = activity.will_umount() {
|
||||
match exit_reason {
|
||||
ExitReason::Quit => {
|
||||
info!("AuthActivity terminated due to 'Quit'");
|
||||
result = None;
|
||||
break;
|
||||
}
|
||||
ExitReason::EnterSetup => {
|
||||
// User requested activity
|
||||
info!("AuthActivity terminated due to 'EnterSetup'");
|
||||
result = Some(NextActivity::SetupActivity);
|
||||
break;
|
||||
}
|
||||
ExitReason::Connect => {
|
||||
// User submitted, set next activity
|
||||
info!("AuthActivity terminated due to 'Connect'");
|
||||
result = Some(NextActivity::FileTransfer);
|
||||
break;
|
||||
}
|
||||
@@ -172,6 +167,7 @@ impl ActivityManager {
|
||||
}
|
||||
// Destroy activity
|
||||
self.context = activity.on_destroy();
|
||||
info!("AuthActivity destroyed");
|
||||
result
|
||||
}
|
||||
|
||||
@@ -181,19 +177,35 @@ impl ActivityManager {
|
||||
/// Returns when activity terminates.
|
||||
/// Returns the next activity to run
|
||||
fn run_filetransfer(&mut self) -> Option<NextActivity> {
|
||||
info!("Starting FileTransferActivity");
|
||||
// Get context
|
||||
let ctx: Context = match self.context.take() {
|
||||
let mut ctx: Context = match self.context.take() {
|
||||
Some(ctx) => ctx,
|
||||
None => return None,
|
||||
None => {
|
||||
error!("Failed to start FileTransferActivity: context is None");
|
||||
return None;
|
||||
}
|
||||
};
|
||||
// If ft params is None, return None
|
||||
let ft_params: &FileTransferParams = match ctx.ft_params.as_ref() {
|
||||
Some(ft_params) => &ft_params,
|
||||
None => return None,
|
||||
let ft_params: &FileTransferParams = match ctx.ft_params() {
|
||||
Some(ft_params) => ft_params,
|
||||
None => {
|
||||
error!("Failed to start FileTransferActivity: file transfer params is None");
|
||||
return None;
|
||||
}
|
||||
};
|
||||
// Prepare activity
|
||||
let protocol: FileTransferProtocol = ft_params.protocol;
|
||||
let mut activity: FileTransferActivity = FileTransferActivity::new(protocol);
|
||||
let host: Localhost = match Localhost::new(self.local_dir.clone()) {
|
||||
Ok(host) => host,
|
||||
Err(err) => {
|
||||
// Set error in context
|
||||
error!("Failed to initialize localhost: {}", err);
|
||||
ctx.set_error(format!("Could not initialize localhost: {}", err));
|
||||
return None;
|
||||
}
|
||||
};
|
||||
let mut activity: FileTransferActivity = FileTransferActivity::new(host, protocol);
|
||||
// Prepare result
|
||||
let result: Option<NextActivity>;
|
||||
// Create activity
|
||||
@@ -205,11 +217,13 @@ impl ActivityManager {
|
||||
if let Some(exit_reason) = activity.will_umount() {
|
||||
match exit_reason {
|
||||
ExitReason::Quit => {
|
||||
info!("FileTransferActivity terminated due to 'Quit'");
|
||||
result = None;
|
||||
break;
|
||||
}
|
||||
ExitReason::Disconnect => {
|
||||
// User disconnected, set next activity to authentication
|
||||
info!("FileTransferActivity terminated due to 'Authentication'");
|
||||
result = Some(NextActivity::Authentication);
|
||||
break;
|
||||
}
|
||||
@@ -235,7 +249,10 @@ impl ActivityManager {
|
||||
// Get context
|
||||
let ctx: Context = match self.context.take() {
|
||||
Some(ctx) => ctx,
|
||||
None => return None,
|
||||
None => {
|
||||
error!("Failed to start SetupActivity: context is None");
|
||||
return None;
|
||||
}
|
||||
};
|
||||
// Create activity
|
||||
activity.on_create(ctx);
|
||||
@@ -244,6 +261,7 @@ impl ActivityManager {
|
||||
activity.on_draw();
|
||||
// Check if activity has terminated
|
||||
if let Some(ExitReason::Quit) = activity.will_umount() {
|
||||
info!("SetupActivity terminated due to 'Quit'");
|
||||
break;
|
||||
}
|
||||
// Sleep for ticks
|
||||
@@ -275,7 +293,7 @@ impl ActivityManager {
|
||||
}
|
||||
}
|
||||
None => Err(String::from(
|
||||
"Your system doesn't support configuration paths",
|
||||
"Your system doesn't provide a configuration directory",
|
||||
)),
|
||||
}
|
||||
}
|
||||
@@ -285,4 +303,32 @@ impl ActivityManager {
|
||||
)),
|
||||
}
|
||||
}
|
||||
|
||||
fn init_theme_provider() -> ThemeProvider {
|
||||
match environment::init_config_dir() {
|
||||
Ok(config_dir) => {
|
||||
match config_dir {
|
||||
Some(config_dir) => {
|
||||
// Get config client paths
|
||||
let theme_path: PathBuf = environment::get_theme_path(config_dir.as_path());
|
||||
match ThemeProvider::new(theme_path.as_path()) {
|
||||
Ok(provider) => provider,
|
||||
Err(err) => {
|
||||
error!("Could not initialize theme provider with file '{}': {}; using theme provider in degraded mode", theme_path.display(), err);
|
||||
ThemeProvider::degraded()
|
||||
}
|
||||
}
|
||||
}
|
||||
None => {
|
||||
error!("This system doesn't provide a configuration directory; using theme provider in degraded mode");
|
||||
ThemeProvider::degraded()
|
||||
}
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
error!("Could not initialize configuration directory: {}; using theme provider in degraded mode", err);
|
||||
ThemeProvider::degraded()
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
@@ -1,222 +0,0 @@
|
||||
//! ## Serializer
|
||||
//!
|
||||
//! `serializer` is the module which provides the serializer/deserializer for bookmarks
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
use super::{SerializerError, SerializerErrorKind, UserHosts};
|
||||
|
||||
use std::io::{Read, Write};
|
||||
|
||||
pub struct BookmarkSerializer;
|
||||
|
||||
impl BookmarkSerializer {
|
||||
/// ### serialize
|
||||
///
|
||||
/// Serialize `UserHosts` into TOML and write content to writable
|
||||
pub fn serialize(
|
||||
&self,
|
||||
mut writable: Box<dyn Write>,
|
||||
hosts: &UserHosts,
|
||||
) -> Result<(), SerializerError> {
|
||||
// Serialize content
|
||||
let data: String = match toml::ser::to_string(hosts) {
|
||||
Ok(dt) => dt,
|
||||
Err(err) => {
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::SerializationError,
|
||||
err.to_string(),
|
||||
))
|
||||
}
|
||||
};
|
||||
// Write file
|
||||
match writable.write_all(data.as_bytes()) {
|
||||
Ok(_) => Ok(()),
|
||||
Err(err) => Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::IoError,
|
||||
err.to_string(),
|
||||
)),
|
||||
}
|
||||
}
|
||||
|
||||
/// ### deserialize
|
||||
///
|
||||
/// Read data from readable and deserialize its content as TOML
|
||||
pub fn deserialize(&self, mut readable: Box<dyn Read>) -> Result<UserHosts, SerializerError> {
|
||||
// Read file content
|
||||
let mut data: String = String::new();
|
||||
if let Err(err) = readable.read_to_string(&mut data) {
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::IoError,
|
||||
err.to_string(),
|
||||
));
|
||||
}
|
||||
// Deserialize
|
||||
match toml::de::from_str(data.as_str()) {
|
||||
Ok(hosts) => Ok(hosts),
|
||||
Err(err) => Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::SyntaxError,
|
||||
err.to_string(),
|
||||
)),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// Tests
|
||||
|
||||
#[cfg(test)]
|
||||
mod tests {
|
||||
|
||||
use super::super::Bookmark;
|
||||
use super::*;
|
||||
|
||||
use std::collections::HashMap;
|
||||
use std::io::{Seek, SeekFrom};
|
||||
|
||||
#[test]
|
||||
fn test_bookmarks_serializer_deserialize_ok() {
|
||||
let toml_file: tempfile::NamedTempFile = create_good_toml();
|
||||
toml_file.as_file().sync_all().unwrap();
|
||||
toml_file.as_file().seek(SeekFrom::Start(0)).unwrap();
|
||||
// Parse
|
||||
let deserializer: BookmarkSerializer = BookmarkSerializer {};
|
||||
let hosts = deserializer.deserialize(Box::new(toml_file));
|
||||
assert!(hosts.is_ok());
|
||||
let hosts: UserHosts = hosts.ok().unwrap();
|
||||
// Verify hosts
|
||||
// Verify recents
|
||||
assert_eq!(hosts.recents.len(), 1);
|
||||
let host: &Bookmark = hosts.recents.get("ISO20201215T094000Z").unwrap();
|
||||
assert_eq!(host.address, String::from("172.16.104.10"));
|
||||
assert_eq!(host.port, 22);
|
||||
assert_eq!(host.protocol, String::from("SCP"));
|
||||
assert_eq!(host.username, String::from("root"));
|
||||
assert_eq!(host.password, None);
|
||||
// Verify bookmarks
|
||||
assert_eq!(hosts.bookmarks.len(), 3);
|
||||
let host: &Bookmark = hosts.bookmarks.get("raspberrypi2").unwrap();
|
||||
assert_eq!(host.address, String::from("192.168.1.31"));
|
||||
assert_eq!(host.port, 22);
|
||||
assert_eq!(host.protocol, String::from("SFTP"));
|
||||
assert_eq!(host.username, String::from("root"));
|
||||
assert_eq!(*host.password.as_ref().unwrap(), String::from("mypassword"));
|
||||
let host: &Bookmark = hosts.bookmarks.get("msi-estrem").unwrap();
|
||||
assert_eq!(host.address, String::from("192.168.1.30"));
|
||||
assert_eq!(host.port, 22);
|
||||
assert_eq!(host.protocol, String::from("SFTP"));
|
||||
assert_eq!(host.username, String::from("cvisintin"));
|
||||
assert_eq!(*host.password.as_ref().unwrap(), String::from("mysecret"));
|
||||
let host: &Bookmark = hosts.bookmarks.get("aws-server-prod1").unwrap();
|
||||
assert_eq!(host.address, String::from("51.23.67.12"));
|
||||
assert_eq!(host.port, 21);
|
||||
assert_eq!(host.protocol, String::from("FTPS"));
|
||||
assert_eq!(host.username, String::from("aws001"));
|
||||
assert_eq!(host.password, None);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_bookmarks_serializer_deserialize_nok() {
|
||||
let toml_file: tempfile::NamedTempFile = create_bad_toml();
|
||||
toml_file.as_file().sync_all().unwrap();
|
||||
toml_file.as_file().seek(SeekFrom::Start(0)).unwrap();
|
||||
// Parse
|
||||
let deserializer: BookmarkSerializer = BookmarkSerializer {};
|
||||
assert!(deserializer.deserialize(Box::new(toml_file)).is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_bookmarks_serializer_serialize() {
|
||||
let mut bookmarks: HashMap<String, Bookmark> = HashMap::with_capacity(2);
|
||||
// Push two samples
|
||||
bookmarks.insert(
|
||||
String::from("raspberrypi2"),
|
||||
Bookmark {
|
||||
address: String::from("192.168.1.31"),
|
||||
port: 22,
|
||||
protocol: String::from("SFTP"),
|
||||
username: String::from("root"),
|
||||
password: None,
|
||||
},
|
||||
);
|
||||
bookmarks.insert(
|
||||
String::from("msi-estrem"),
|
||||
Bookmark {
|
||||
address: String::from("192.168.1.30"),
|
||||
port: 4022,
|
||||
protocol: String::from("SFTP"),
|
||||
username: String::from("cvisintin"),
|
||||
password: Some(String::from("password")),
|
||||
},
|
||||
);
|
||||
let mut recents: HashMap<String, Bookmark> = HashMap::with_capacity(1);
|
||||
recents.insert(
|
||||
String::from("ISO20201215T094000Z"),
|
||||
Bookmark {
|
||||
address: String::from("192.168.1.254"),
|
||||
port: 3022,
|
||||
protocol: String::from("SCP"),
|
||||
username: String::from("omar"),
|
||||
password: Some(String::from("aaa")),
|
||||
},
|
||||
);
|
||||
let tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
// Serialize
|
||||
let deserializer: BookmarkSerializer = BookmarkSerializer {};
|
||||
let hosts: UserHosts = UserHosts { bookmarks, recents };
|
||||
assert!(deserializer.serialize(Box::new(tmpfile), &hosts).is_ok());
|
||||
}
|
||||
|
||||
fn create_good_toml() -> tempfile::NamedTempFile {
|
||||
// Write
|
||||
let mut tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
let file_content: &str = r#"
|
||||
[bookmarks]
|
||||
raspberrypi2 = { address = "192.168.1.31", port = 22, protocol = "SFTP", username = "root", password = "mypassword" }
|
||||
msi-estrem = { address = "192.168.1.30", port = 22, protocol = "SFTP", username = "cvisintin", password = "mysecret" }
|
||||
aws-server-prod1 = { address = "51.23.67.12", port = 21, protocol = "FTPS", username = "aws001" }
|
||||
|
||||
[recents]
|
||||
ISO20201215T094000Z = { address = "172.16.104.10", port = 22, protocol = "SCP", username = "root" }
|
||||
"#;
|
||||
tmpfile.write_all(file_content.as_bytes()).unwrap();
|
||||
//write!(tmpfile, "[bookmarks]\nraspberrypi2 = {{ address = \"192.168.1.31\", port = 22, protocol = \"SFTP\", username = \"root\" }}\nmsi-estrem = {{ address = \"192.168.1.30\", port = 22, protocol = \"SFTP\", username = \"cvisintin\" }}\naws-server-prod1 = {{ address = \"51.23.67.12\", port = 21, protocol = \"FTPS\", username = \"aws001\" }}\n\n[recents]\nISO20201215T094000Z = {{ address = \"172.16.104.10\", port = 22, protocol = \"SCP\", username = \"root\" }}\n");
|
||||
tmpfile
|
||||
}
|
||||
|
||||
fn create_bad_toml() -> tempfile::NamedTempFile {
|
||||
// Write
|
||||
let mut tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
let file_content: &str = r#"
|
||||
[bookmarks]
|
||||
raspberrypi2 = { address = "192.168.1.31", port = 22, protocol = "SFTP", username = "root"}
|
||||
msi-estrem = { address = "192.168.1.30", port = 22, protocol = "SFTP" }
|
||||
aws-server-prod1 = { address = "51.23.67.12", port = 21, protocol = "FTPS", username = "aws001" }
|
||||
|
||||
[recents]
|
||||
ISO20201215T094000Z = { address = "172.16.104.10", protocol = "SCP", username = "root", port = 22 }
|
||||
"#;
|
||||
tmpfile.write_all(file_content.as_bytes()).unwrap();
|
||||
tmpfile
|
||||
}
|
||||
}
|
||||
@@ -25,11 +25,8 @@
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
pub mod serializer;
|
||||
|
||||
use serde::{Deserialize, Serialize};
|
||||
use std::collections::HashMap;
|
||||
use thiserror::Error;
|
||||
|
||||
#[derive(Deserialize, Serialize, std::fmt::Debug)]
|
||||
/// ## UserHosts
|
||||
@@ -53,72 +50,29 @@ pub struct Bookmark {
|
||||
pub password: Option<String>, // Password is optional; base64, aes-128 encrypted password
|
||||
}
|
||||
|
||||
// Errors
|
||||
|
||||
/// ## SerializerError
|
||||
///
|
||||
/// Contains the error for serializer/deserializer
|
||||
#[derive(std::fmt::Debug)]
|
||||
pub struct SerializerError {
|
||||
kind: SerializerErrorKind,
|
||||
msg: Option<String>,
|
||||
}
|
||||
|
||||
/// ## SerializerErrorKind
|
||||
///
|
||||
/// Describes the kind of error for the serializer/deserializer
|
||||
#[derive(Error, Debug)]
|
||||
pub enum SerializerErrorKind {
|
||||
#[error("IO error")]
|
||||
IoError,
|
||||
#[error("Serialization error")]
|
||||
SerializationError,
|
||||
#[error("Syntax error")]
|
||||
SyntaxError,
|
||||
}
|
||||
|
||||
impl Default for UserHosts {
|
||||
fn default() -> Self {
|
||||
UserHosts {
|
||||
Self {
|
||||
bookmarks: HashMap::new(),
|
||||
recents: HashMap::new(),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
impl SerializerError {
|
||||
/// ### new
|
||||
///
|
||||
/// Instantiate a new `SerializerError`
|
||||
pub fn new(kind: SerializerErrorKind) -> SerializerError {
|
||||
SerializerError { kind, msg: None }
|
||||
}
|
||||
|
||||
/// ### new_ex
|
||||
///
|
||||
/// Instantiates a new `SerializerError` with description message
|
||||
pub fn new_ex(kind: SerializerErrorKind, msg: String) -> SerializerError {
|
||||
let mut err: SerializerError = SerializerError::new(kind);
|
||||
err.msg = Some(msg);
|
||||
err
|
||||
}
|
||||
}
|
||||
|
||||
impl std::fmt::Display for SerializerError {
|
||||
fn fmt(&self, f: &mut std::fmt::Formatter) -> std::fmt::Result {
|
||||
match &self.msg {
|
||||
Some(msg) => write!(f, "{} ({})", self.kind, msg),
|
||||
None => write!(f, "{}", self.kind),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// Tests
|
||||
|
||||
#[cfg(test)]
|
||||
mod tests {
|
||||
|
||||
use super::*;
|
||||
use pretty_assertions::assert_eq;
|
||||
|
||||
#[test]
|
||||
fn test_bookmarks_default() {
|
||||
let bookmarks: UserHosts = UserHosts::default();
|
||||
assert_eq!(bookmarks.bookmarks.len(), 0);
|
||||
assert_eq!(bookmarks.recents.len(), 0);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_bookmarks_bookmark_new() {
|
||||
@@ -167,30 +121,4 @@ mod tests {
|
||||
String::from("password")
|
||||
);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_bookmarks_bookmark_errors() {
|
||||
let error: SerializerError = SerializerError::new(SerializerErrorKind::SyntaxError);
|
||||
assert!(error.msg.is_none());
|
||||
assert_eq!(format!("{}", error), String::from("Syntax error"));
|
||||
let error: SerializerError =
|
||||
SerializerError::new_ex(SerializerErrorKind::SyntaxError, String::from("bad syntax"));
|
||||
assert!(error.msg.is_some());
|
||||
assert_eq!(
|
||||
format!("{}", error),
|
||||
String::from("Syntax error (bad syntax)")
|
||||
);
|
||||
// Fmt
|
||||
assert_eq!(
|
||||
format!("{}", SerializerError::new(SerializerErrorKind::IoError)),
|
||||
String::from("IO error")
|
||||
);
|
||||
assert_eq!(
|
||||
format!(
|
||||
"{}",
|
||||
SerializerError::new(SerializerErrorKind::SerializationError)
|
||||
),
|
||||
String::from("Serialization error")
|
||||
);
|
||||
}
|
||||
}
|
||||
@@ -1,6 +1,6 @@
|
||||
//! ## Config
|
||||
//!
|
||||
//! `config` is the module which provides access to termscp configuration
|
||||
//! `config` is the module which provides access to all the termscp configurations
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
@@ -25,224 +25,10 @@
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// Modules
|
||||
pub mod serializer;
|
||||
// export
|
||||
pub use params::*;
|
||||
|
||||
// Deps
|
||||
extern crate edit;
|
||||
|
||||
// Locals
|
||||
use crate::filetransfer::FileTransferProtocol;
|
||||
|
||||
// Ext
|
||||
use serde::{Deserialize, Serialize};
|
||||
use std::collections::HashMap;
|
||||
use std::path::PathBuf;
|
||||
use thiserror::Error;
|
||||
|
||||
#[derive(Deserialize, Serialize, std::fmt::Debug)]
|
||||
/// ## UserConfig
|
||||
///
|
||||
/// UserConfig contains all the configurations for the user,
|
||||
/// supported by termscp
|
||||
pub struct UserConfig {
|
||||
pub user_interface: UserInterfaceConfig,
|
||||
pub remote: RemoteConfig,
|
||||
}
|
||||
|
||||
#[derive(Deserialize, Serialize, std::fmt::Debug)]
|
||||
/// ## UserInterfaceConfig
|
||||
///
|
||||
/// UserInterfaceConfig provides all the keys to configure the user interface
|
||||
pub struct UserInterfaceConfig {
|
||||
pub text_editor: PathBuf,
|
||||
pub default_protocol: String,
|
||||
pub show_hidden_files: bool,
|
||||
pub check_for_updates: Option<bool>, // @! Since 0.3.3
|
||||
pub group_dirs: Option<String>,
|
||||
pub file_fmt: Option<String>,
|
||||
}
|
||||
|
||||
#[derive(Deserialize, Serialize, std::fmt::Debug)]
|
||||
/// ## RemoteConfig
|
||||
///
|
||||
/// Contains configuratio related to remote hosts
|
||||
pub struct RemoteConfig {
|
||||
pub ssh_keys: HashMap<String, PathBuf>, // Association between host name and path to private key
|
||||
}
|
||||
|
||||
impl Default for UserConfig {
|
||||
fn default() -> Self {
|
||||
UserConfig {
|
||||
user_interface: UserInterfaceConfig::default(),
|
||||
remote: RemoteConfig::default(),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
impl Default for UserInterfaceConfig {
|
||||
fn default() -> Self {
|
||||
UserInterfaceConfig {
|
||||
text_editor: match edit::get_editor() {
|
||||
Ok(p) => p,
|
||||
Err(_) => PathBuf::from("nano"), // Default to nano
|
||||
},
|
||||
default_protocol: FileTransferProtocol::Sftp.to_string(),
|
||||
show_hidden_files: false,
|
||||
check_for_updates: Some(true),
|
||||
group_dirs: None,
|
||||
file_fmt: None,
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
impl Default for RemoteConfig {
|
||||
fn default() -> Self {
|
||||
RemoteConfig {
|
||||
ssh_keys: HashMap::new(),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// Errors
|
||||
|
||||
/// ## SerializerError
|
||||
///
|
||||
/// Contains the error for serializer/deserializer
|
||||
#[derive(std::fmt::Debug)]
|
||||
pub struct SerializerError {
|
||||
kind: SerializerErrorKind,
|
||||
msg: Option<String>,
|
||||
}
|
||||
|
||||
/// ## SerializerErrorKind
|
||||
///
|
||||
/// Describes the kind of error for the serializer/deserializer
|
||||
#[derive(Error, Debug)]
|
||||
pub enum SerializerErrorKind {
|
||||
#[error("IO error")]
|
||||
IoError,
|
||||
#[error("Serialization error")]
|
||||
SerializationError,
|
||||
#[error("Syntax error")]
|
||||
SyntaxError,
|
||||
}
|
||||
|
||||
impl SerializerError {
|
||||
/// ### new
|
||||
///
|
||||
/// Instantiate a new `SerializerError`
|
||||
pub fn new(kind: SerializerErrorKind) -> SerializerError {
|
||||
SerializerError { kind, msg: None }
|
||||
}
|
||||
|
||||
/// ### new_ex
|
||||
///
|
||||
/// Instantiates a new `SerializerError` with description message
|
||||
pub fn new_ex(kind: SerializerErrorKind, msg: String) -> SerializerError {
|
||||
let mut err: SerializerError = SerializerError::new(kind);
|
||||
err.msg = Some(msg);
|
||||
err
|
||||
}
|
||||
}
|
||||
|
||||
impl std::fmt::Display for SerializerError {
|
||||
fn fmt(&self, f: &mut std::fmt::Formatter) -> std::fmt::Result {
|
||||
match &self.msg {
|
||||
Some(msg) => write!(f, "{} ({})", self.kind, msg),
|
||||
None => write!(f, "{}", self.kind),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// Tests
|
||||
|
||||
#[cfg(test)]
|
||||
mod tests {
|
||||
|
||||
use super::*;
|
||||
use std::env;
|
||||
|
||||
#[test]
|
||||
fn test_config_mod_new() {
|
||||
let mut keys: HashMap<String, PathBuf> = HashMap::with_capacity(1);
|
||||
keys.insert(
|
||||
String::from("192.168.1.31"),
|
||||
PathBuf::from("/tmp/private.key"),
|
||||
);
|
||||
let remote: RemoteConfig = RemoteConfig { ssh_keys: keys };
|
||||
let ui: UserInterfaceConfig = UserInterfaceConfig {
|
||||
default_protocol: String::from("SFTP"),
|
||||
text_editor: PathBuf::from("nano"),
|
||||
show_hidden_files: true,
|
||||
check_for_updates: Some(true),
|
||||
group_dirs: Some(String::from("first")),
|
||||
file_fmt: Some(String::from("{NAME}")),
|
||||
};
|
||||
let cfg: UserConfig = UserConfig {
|
||||
user_interface: ui,
|
||||
remote: remote,
|
||||
};
|
||||
assert_eq!(
|
||||
*cfg.remote
|
||||
.ssh_keys
|
||||
.get(&String::from("192.168.1.31"))
|
||||
.unwrap(),
|
||||
PathBuf::from("/tmp/private.key")
|
||||
);
|
||||
assert_eq!(cfg.user_interface.default_protocol, String::from("SFTP"));
|
||||
assert_eq!(cfg.user_interface.text_editor, PathBuf::from("nano"));
|
||||
assert_eq!(cfg.user_interface.show_hidden_files, true);
|
||||
assert_eq!(cfg.user_interface.check_for_updates, Some(true));
|
||||
assert_eq!(cfg.user_interface.group_dirs, Some(String::from("first")));
|
||||
assert_eq!(cfg.user_interface.file_fmt, Some(String::from("{NAME}")));
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_config_mod_new_default() {
|
||||
// Force vim editor
|
||||
env::set_var(String::from("EDITOR"), String::from("vim"));
|
||||
// Get default
|
||||
let cfg: UserConfig = UserConfig::default();
|
||||
assert_eq!(cfg.user_interface.default_protocol, String::from("SFTP"));
|
||||
// Text editor
|
||||
#[cfg(target_os = "windows")]
|
||||
assert_eq!(
|
||||
PathBuf::from(cfg.user_interface.text_editor.file_name().unwrap()), // NOTE: since edit 0.1.3 real path is used
|
||||
PathBuf::from("vim.EXE")
|
||||
);
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
assert_eq!(
|
||||
PathBuf::from(cfg.user_interface.text_editor.file_name().unwrap()), // NOTE: since edit 0.1.3 real path is used
|
||||
PathBuf::from("vim")
|
||||
);
|
||||
assert_eq!(cfg.user_interface.check_for_updates.unwrap(), true);
|
||||
assert_eq!(cfg.remote.ssh_keys.len(), 0);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_config_mod_errors() {
|
||||
let error: SerializerError = SerializerError::new(SerializerErrorKind::SyntaxError);
|
||||
assert!(error.msg.is_none());
|
||||
assert_eq!(format!("{}", error), String::from("Syntax error"));
|
||||
let error: SerializerError =
|
||||
SerializerError::new_ex(SerializerErrorKind::SyntaxError, String::from("bad syntax"));
|
||||
assert!(error.msg.is_some());
|
||||
assert_eq!(
|
||||
format!("{}", error),
|
||||
String::from("Syntax error (bad syntax)")
|
||||
);
|
||||
// Fmt
|
||||
assert_eq!(
|
||||
format!("{}", SerializerError::new(SerializerErrorKind::IoError)),
|
||||
String::from("IO error")
|
||||
);
|
||||
assert_eq!(
|
||||
format!(
|
||||
"{}",
|
||||
SerializerError::new(SerializerErrorKind::SerializationError)
|
||||
),
|
||||
String::from("Serialization error")
|
||||
);
|
||||
}
|
||||
}
|
||||
pub mod bookmarks;
|
||||
pub mod params;
|
||||
pub mod serialization;
|
||||
pub mod themes;
|
||||
|
||||
155
src/config/params.rs
Normal file
@@ -0,0 +1,155 @@
|
||||
//! ## Config
|
||||
//!
|
||||
//! `config` is the module which provides access to termscp configuration
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// Locals
|
||||
use crate::filetransfer::FileTransferProtocol;
|
||||
|
||||
// Ext
|
||||
use serde::{Deserialize, Serialize};
|
||||
use std::collections::HashMap;
|
||||
use std::path::PathBuf;
|
||||
|
||||
#[derive(Deserialize, Serialize, std::fmt::Debug)]
|
||||
/// ## UserConfig
|
||||
///
|
||||
/// UserConfig contains all the configurations for the user,
|
||||
/// supported by termscp
|
||||
pub struct UserConfig {
|
||||
pub user_interface: UserInterfaceConfig,
|
||||
pub remote: RemoteConfig,
|
||||
}
|
||||
|
||||
#[derive(Deserialize, Serialize, std::fmt::Debug)]
|
||||
/// ## UserInterfaceConfig
|
||||
///
|
||||
/// UserInterfaceConfig provides all the keys to configure the user interface
|
||||
pub struct UserInterfaceConfig {
|
||||
pub text_editor: PathBuf,
|
||||
pub default_protocol: String,
|
||||
pub show_hidden_files: bool,
|
||||
pub check_for_updates: Option<bool>, // @! Since 0.3.3
|
||||
pub group_dirs: Option<String>,
|
||||
pub file_fmt: Option<String>, // Refers to local host (for backward compatibility)
|
||||
pub remote_file_fmt: Option<String>, // @! Since 0.5.0
|
||||
}
|
||||
|
||||
#[derive(Deserialize, Serialize, std::fmt::Debug)]
|
||||
/// ## RemoteConfig
|
||||
///
|
||||
/// Contains configuratio related to remote hosts
|
||||
pub struct RemoteConfig {
|
||||
pub ssh_keys: HashMap<String, PathBuf>, // Association between host name and path to private key
|
||||
}
|
||||
|
||||
impl Default for UserConfig {
|
||||
fn default() -> Self {
|
||||
UserConfig {
|
||||
user_interface: UserInterfaceConfig::default(),
|
||||
remote: RemoteConfig::default(),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
impl Default for UserInterfaceConfig {
|
||||
fn default() -> Self {
|
||||
UserInterfaceConfig {
|
||||
text_editor: match edit::get_editor() {
|
||||
Ok(p) => p,
|
||||
Err(_) => PathBuf::from("nano"), // Default to nano
|
||||
},
|
||||
default_protocol: FileTransferProtocol::Sftp.to_string(),
|
||||
show_hidden_files: false,
|
||||
check_for_updates: Some(true),
|
||||
group_dirs: None,
|
||||
file_fmt: None,
|
||||
remote_file_fmt: None,
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
impl Default for RemoteConfig {
|
||||
fn default() -> Self {
|
||||
RemoteConfig {
|
||||
ssh_keys: HashMap::new(),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// Tests
|
||||
|
||||
#[cfg(test)]
|
||||
mod tests {
|
||||
|
||||
use super::*;
|
||||
use pretty_assertions::assert_eq;
|
||||
|
||||
#[test]
|
||||
fn test_config_mod_new() {
|
||||
let mut keys: HashMap<String, PathBuf> = HashMap::with_capacity(1);
|
||||
keys.insert(
|
||||
String::from("192.168.1.31"),
|
||||
PathBuf::from("/tmp/private.key"),
|
||||
);
|
||||
let remote: RemoteConfig = RemoteConfig { ssh_keys: keys };
|
||||
let ui: UserInterfaceConfig = UserInterfaceConfig {
|
||||
default_protocol: String::from("SFTP"),
|
||||
text_editor: PathBuf::from("nano"),
|
||||
show_hidden_files: true,
|
||||
check_for_updates: Some(true),
|
||||
group_dirs: Some(String::from("first")),
|
||||
file_fmt: Some(String::from("{NAME}")),
|
||||
remote_file_fmt: Some(String::from("{USER}")),
|
||||
};
|
||||
assert_eq!(ui.default_protocol, String::from("SFTP"));
|
||||
assert_eq!(ui.text_editor, PathBuf::from("nano"));
|
||||
assert_eq!(ui.show_hidden_files, true);
|
||||
assert_eq!(ui.check_for_updates, Some(true));
|
||||
assert_eq!(ui.group_dirs, Some(String::from("first")));
|
||||
assert_eq!(ui.file_fmt, Some(String::from("{NAME}")));
|
||||
let cfg: UserConfig = UserConfig {
|
||||
user_interface: ui,
|
||||
remote: remote,
|
||||
};
|
||||
assert_eq!(
|
||||
*cfg.remote
|
||||
.ssh_keys
|
||||
.get(&String::from("192.168.1.31"))
|
||||
.unwrap(),
|
||||
PathBuf::from("/tmp/private.key")
|
||||
);
|
||||
assert_eq!(cfg.user_interface.default_protocol, String::from("SFTP"));
|
||||
assert_eq!(cfg.user_interface.text_editor, PathBuf::from("nano"));
|
||||
assert_eq!(cfg.user_interface.show_hidden_files, true);
|
||||
assert_eq!(cfg.user_interface.check_for_updates, Some(true));
|
||||
assert_eq!(cfg.user_interface.group_dirs, Some(String::from("first")));
|
||||
assert_eq!(cfg.user_interface.file_fmt, Some(String::from("{NAME}")));
|
||||
assert_eq!(
|
||||
cfg.user_interface.remote_file_fmt,
|
||||
Some(String::from("{USER}"))
|
||||
);
|
||||
}
|
||||
}
|
||||
572
src/config/serialization.rs
Normal file
@@ -0,0 +1,572 @@
|
||||
//! ## Serialization
|
||||
//!
|
||||
//! `serialization` provides serialization and deserialization for configurations
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
use serde::{de::DeserializeOwned, Serialize};
|
||||
use std::io::{Read, Write};
|
||||
use thiserror::Error;
|
||||
|
||||
/// ## SerializerError
|
||||
///
|
||||
/// Contains the error for serializer/deserializer
|
||||
#[derive(std::fmt::Debug)]
|
||||
pub struct SerializerError {
|
||||
kind: SerializerErrorKind,
|
||||
msg: Option<String>,
|
||||
}
|
||||
|
||||
/// ## SerializerErrorKind
|
||||
///
|
||||
/// Describes the kind of error for the serializer/deserializer
|
||||
#[derive(Error, Debug)]
|
||||
pub enum SerializerErrorKind {
|
||||
#[error("Operation failed")]
|
||||
Generic,
|
||||
#[error("IO error")]
|
||||
Io,
|
||||
#[error("Serialization error")]
|
||||
Serialization,
|
||||
#[error("Syntax error")]
|
||||
Syntax,
|
||||
}
|
||||
|
||||
impl SerializerError {
|
||||
/// ### new
|
||||
///
|
||||
/// Instantiate a new `SerializerError`
|
||||
pub fn new(kind: SerializerErrorKind) -> SerializerError {
|
||||
SerializerError { kind, msg: None }
|
||||
}
|
||||
|
||||
/// ### new_ex
|
||||
///
|
||||
/// Instantiates a new `SerializerError` with description message
|
||||
pub fn new_ex(kind: SerializerErrorKind, msg: String) -> SerializerError {
|
||||
let mut err: SerializerError = SerializerError::new(kind);
|
||||
err.msg = Some(msg);
|
||||
err
|
||||
}
|
||||
}
|
||||
|
||||
impl std::fmt::Display for SerializerError {
|
||||
fn fmt(&self, f: &mut std::fmt::Formatter) -> std::fmt::Result {
|
||||
match &self.msg {
|
||||
Some(msg) => write!(f, "{} ({})", self.kind, msg),
|
||||
None => write!(f, "{}", self.kind),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### serialize
|
||||
///
|
||||
/// Serialize `UserHosts` into TOML and write content to writable
|
||||
pub fn serialize<S>(serializable: &S, mut writable: Box<dyn Write>) -> Result<(), SerializerError>
|
||||
where
|
||||
S: Serialize + Sized,
|
||||
{
|
||||
// Serialize content
|
||||
let data: String = match toml::ser::to_string(serializable) {
|
||||
Ok(dt) => dt,
|
||||
Err(err) => {
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Serialization,
|
||||
err.to_string(),
|
||||
))
|
||||
}
|
||||
};
|
||||
trace!("Serialized new bookmarks data: {}", data);
|
||||
// Write file
|
||||
match writable.write_all(data.as_bytes()) {
|
||||
Ok(_) => Ok(()),
|
||||
Err(err) => Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Io,
|
||||
err.to_string(),
|
||||
)),
|
||||
}
|
||||
}
|
||||
|
||||
/// ### deserialize
|
||||
///
|
||||
/// Read data from readable and deserialize its content as TOML
|
||||
pub fn deserialize<S>(mut readable: Box<dyn Read>) -> Result<S, SerializerError>
|
||||
where
|
||||
S: DeserializeOwned + Sized + std::fmt::Debug,
|
||||
{
|
||||
// Read file content
|
||||
let mut data: String = String::new();
|
||||
if let Err(err) = readable.read_to_string(&mut data) {
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Io,
|
||||
err.to_string(),
|
||||
));
|
||||
}
|
||||
trace!("Read bookmarks from file: {}", data);
|
||||
// Deserialize
|
||||
match toml::de::from_str(data.as_str()) {
|
||||
Ok(deserialized) => {
|
||||
debug!("Read bookmarks from file {:?}", deserialized);
|
||||
Ok(deserialized)
|
||||
}
|
||||
Err(err) => Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Syntax,
|
||||
err.to_string(),
|
||||
)),
|
||||
}
|
||||
}
|
||||
|
||||
#[cfg(test)]
|
||||
mod tests {
|
||||
|
||||
use super::*;
|
||||
use pretty_assertions::assert_eq;
|
||||
use std::collections::HashMap;
|
||||
use std::io::{Seek, SeekFrom};
|
||||
use std::path::PathBuf;
|
||||
use tuirealm::tui::style::Color;
|
||||
|
||||
use crate::config::bookmarks::{Bookmark, UserHosts};
|
||||
use crate::config::params::UserConfig;
|
||||
use crate::config::themes::Theme;
|
||||
use crate::utils::test_helpers::create_file_ioers;
|
||||
|
||||
#[test]
|
||||
fn test_config_serialization_errors() {
|
||||
let error: SerializerError = SerializerError::new(SerializerErrorKind::Syntax);
|
||||
assert!(error.msg.is_none());
|
||||
assert_eq!(format!("{}", error), String::from("Syntax error"));
|
||||
let error: SerializerError =
|
||||
SerializerError::new_ex(SerializerErrorKind::Syntax, String::from("bad syntax"));
|
||||
assert!(error.msg.is_some());
|
||||
assert_eq!(
|
||||
format!("{}", error),
|
||||
String::from("Syntax error (bad syntax)")
|
||||
);
|
||||
// Fmt
|
||||
assert_eq!(
|
||||
format!("{}", SerializerError::new(SerializerErrorKind::Generic)),
|
||||
String::from("Operation failed")
|
||||
);
|
||||
assert_eq!(
|
||||
format!("{}", SerializerError::new(SerializerErrorKind::Io)),
|
||||
String::from("IO error")
|
||||
);
|
||||
assert_eq!(
|
||||
format!(
|
||||
"{}",
|
||||
SerializerError::new(SerializerErrorKind::Serialization)
|
||||
),
|
||||
String::from("Serialization error")
|
||||
);
|
||||
}
|
||||
|
||||
// -- Serialization of params
|
||||
|
||||
#[test]
|
||||
fn test_config_serialization_params_deserialize_ok() {
|
||||
let toml_file: tempfile::NamedTempFile = create_good_toml_bookmarks_params();
|
||||
toml_file.as_file().sync_all().unwrap();
|
||||
toml_file.as_file().seek(SeekFrom::Start(0)).unwrap();
|
||||
// Parse
|
||||
let cfg = deserialize(Box::new(toml_file));
|
||||
assert!(cfg.is_ok());
|
||||
let cfg: UserConfig = cfg.ok().unwrap();
|
||||
// Verify configuration
|
||||
// Verify ui
|
||||
assert_eq!(cfg.user_interface.default_protocol, String::from("SCP"));
|
||||
assert_eq!(cfg.user_interface.text_editor, PathBuf::from("vim"));
|
||||
assert_eq!(cfg.user_interface.show_hidden_files, true);
|
||||
assert_eq!(cfg.user_interface.check_for_updates.unwrap(), true);
|
||||
assert_eq!(cfg.user_interface.group_dirs, Some(String::from("last")));
|
||||
assert_eq!(
|
||||
cfg.user_interface.file_fmt,
|
||||
Some(String::from("{NAME} {PEX}"))
|
||||
);
|
||||
assert_eq!(
|
||||
cfg.user_interface.remote_file_fmt,
|
||||
Some(String::from("{NAME} {USER}")),
|
||||
);
|
||||
// Verify keys
|
||||
assert_eq!(
|
||||
*cfg.remote
|
||||
.ssh_keys
|
||||
.get(&String::from("192.168.1.31"))
|
||||
.unwrap(),
|
||||
PathBuf::from("/home/omar/.ssh/raspberry.key")
|
||||
);
|
||||
assert_eq!(
|
||||
*cfg.remote
|
||||
.ssh_keys
|
||||
.get(&String::from("192.168.1.32"))
|
||||
.unwrap(),
|
||||
PathBuf::from("/home/omar/.ssh/beaglebone.key")
|
||||
);
|
||||
assert!(cfg.remote.ssh_keys.get(&String::from("1.1.1.1")).is_none());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_config_serialization_params_deserialize_ok_no_opts() {
|
||||
let toml_file: tempfile::NamedTempFile = create_good_toml_bookmarks_params_no_opts();
|
||||
toml_file.as_file().sync_all().unwrap();
|
||||
toml_file.as_file().seek(SeekFrom::Start(0)).unwrap();
|
||||
// Parse
|
||||
let cfg = deserialize(Box::new(toml_file));
|
||||
assert!(cfg.is_ok());
|
||||
let cfg: UserConfig = cfg.ok().unwrap();
|
||||
// Verify configuration
|
||||
// Verify ui
|
||||
assert_eq!(cfg.user_interface.default_protocol, String::from("SCP"));
|
||||
assert_eq!(cfg.user_interface.text_editor, PathBuf::from("vim"));
|
||||
assert_eq!(cfg.user_interface.show_hidden_files, true);
|
||||
assert_eq!(cfg.user_interface.group_dirs, None);
|
||||
assert!(cfg.user_interface.check_for_updates.is_none());
|
||||
assert!(cfg.user_interface.file_fmt.is_none());
|
||||
assert!(cfg.user_interface.remote_file_fmt.is_none());
|
||||
// Verify keys
|
||||
assert_eq!(
|
||||
*cfg.remote
|
||||
.ssh_keys
|
||||
.get(&String::from("192.168.1.31"))
|
||||
.unwrap(),
|
||||
PathBuf::from("/home/omar/.ssh/raspberry.key")
|
||||
);
|
||||
assert_eq!(
|
||||
*cfg.remote
|
||||
.ssh_keys
|
||||
.get(&String::from("192.168.1.32"))
|
||||
.unwrap(),
|
||||
PathBuf::from("/home/omar/.ssh/beaglebone.key")
|
||||
);
|
||||
assert!(cfg.remote.ssh_keys.get(&String::from("1.1.1.1")).is_none());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_config_serialization_params_deserialize_nok() {
|
||||
let toml_file: tempfile::NamedTempFile = create_bad_toml_bookmarks_params();
|
||||
toml_file.as_file().sync_all().unwrap();
|
||||
toml_file.as_file().seek(SeekFrom::Start(0)).unwrap();
|
||||
// Parse
|
||||
assert!(deserialize::<UserConfig>(Box::new(toml_file)).is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_config_serialization_params_serialize() {
|
||||
let mut cfg: UserConfig = UserConfig::default();
|
||||
let toml_file: tempfile::NamedTempFile = tempfile::NamedTempFile::new().ok().unwrap();
|
||||
// Insert key
|
||||
cfg.remote.ssh_keys.insert(
|
||||
String::from("192.168.1.31"),
|
||||
PathBuf::from("/home/omar/.ssh/id_rsa"),
|
||||
);
|
||||
// Serialize
|
||||
let writer: Box<dyn Write> = Box::new(std::fs::File::create(toml_file.path()).unwrap());
|
||||
assert!(serialize(&cfg, writer).is_ok());
|
||||
// Reload configuration and check if it's ok
|
||||
toml_file.as_file().sync_all().unwrap();
|
||||
toml_file.as_file().seek(SeekFrom::Start(0)).unwrap();
|
||||
assert!(deserialize::<UserConfig>(Box::new(toml_file)).is_ok());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_config_serialization_params_fail_write() {
|
||||
let toml_file: tempfile::NamedTempFile = tempfile::NamedTempFile::new().ok().unwrap();
|
||||
let writer: Box<dyn Write> = Box::new(std::fs::File::open(toml_file.path()).unwrap());
|
||||
// Try to write unexisting file
|
||||
let cfg: UserConfig = UserConfig::default();
|
||||
assert!(serialize(&cfg, writer).is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_config_serialization_params_fail_read() {
|
||||
let toml_file: tempfile::NamedTempFile = tempfile::NamedTempFile::new().ok().unwrap();
|
||||
let reader: Box<dyn Read> = Box::new(std::fs::File::open(toml_file.path()).unwrap());
|
||||
// Try to write unexisting file
|
||||
assert!(deserialize::<UserConfig>(reader).is_err());
|
||||
}
|
||||
|
||||
fn create_good_toml_bookmarks_params() -> tempfile::NamedTempFile {
|
||||
// Write
|
||||
let mut tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
let file_content: &str = r#"
|
||||
[user_interface]
|
||||
default_protocol = "SCP"
|
||||
text_editor = "vim"
|
||||
show_hidden_files = true
|
||||
check_for_updates = true
|
||||
group_dirs = "last"
|
||||
file_fmt = "{NAME} {PEX}"
|
||||
remote_file_fmt = "{NAME} {USER}"
|
||||
|
||||
[remote.ssh_keys]
|
||||
"192.168.1.31" = "/home/omar/.ssh/raspberry.key"
|
||||
"192.168.1.32" = "/home/omar/.ssh/beaglebone.key"
|
||||
"#;
|
||||
tmpfile.write_all(file_content.as_bytes()).unwrap();
|
||||
tmpfile
|
||||
}
|
||||
|
||||
fn create_good_toml_bookmarks_params_no_opts() -> tempfile::NamedTempFile {
|
||||
// Write
|
||||
let mut tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
let file_content: &str = r#"
|
||||
[user_interface]
|
||||
default_protocol = "SCP"
|
||||
text_editor = "vim"
|
||||
show_hidden_files = true
|
||||
|
||||
[remote.ssh_keys]
|
||||
"192.168.1.31" = "/home/omar/.ssh/raspberry.key"
|
||||
"192.168.1.32" = "/home/omar/.ssh/beaglebone.key"
|
||||
"#;
|
||||
tmpfile.write_all(file_content.as_bytes()).unwrap();
|
||||
tmpfile
|
||||
}
|
||||
|
||||
fn create_bad_toml_bookmarks_params() -> tempfile::NamedTempFile {
|
||||
// Write
|
||||
let mut tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
let file_content: &str = r#"
|
||||
[user_interface]
|
||||
default_protocol = "SFTP"
|
||||
|
||||
[remote.ssh_keys]
|
||||
"192.168.1.31" = "/home/omar/.ssh/raspberry.key"
|
||||
"#;
|
||||
tmpfile.write_all(file_content.as_bytes()).unwrap();
|
||||
tmpfile
|
||||
}
|
||||
|
||||
// -- bookmarks
|
||||
|
||||
#[test]
|
||||
fn test_config_serializer_bookmarks_serializer_deserialize_ok() {
|
||||
let toml_file: tempfile::NamedTempFile = create_good_toml_bookmarks();
|
||||
toml_file.as_file().sync_all().unwrap();
|
||||
toml_file.as_file().seek(SeekFrom::Start(0)).unwrap();
|
||||
// Parse
|
||||
let hosts = deserialize(Box::new(toml_file));
|
||||
assert!(hosts.is_ok());
|
||||
let hosts: UserHosts = hosts.ok().unwrap();
|
||||
// Verify hosts
|
||||
// Verify recents
|
||||
assert_eq!(hosts.recents.len(), 1);
|
||||
let host: &Bookmark = hosts.recents.get("ISO20201215T094000Z").unwrap();
|
||||
assert_eq!(host.address, String::from("172.16.104.10"));
|
||||
assert_eq!(host.port, 22);
|
||||
assert_eq!(host.protocol, String::from("SCP"));
|
||||
assert_eq!(host.username, String::from("root"));
|
||||
assert_eq!(host.password, None);
|
||||
// Verify bookmarks
|
||||
assert_eq!(hosts.bookmarks.len(), 3);
|
||||
let host: &Bookmark = hosts.bookmarks.get("raspberrypi2").unwrap();
|
||||
assert_eq!(host.address, String::from("192.168.1.31"));
|
||||
assert_eq!(host.port, 22);
|
||||
assert_eq!(host.protocol, String::from("SFTP"));
|
||||
assert_eq!(host.username, String::from("root"));
|
||||
assert_eq!(*host.password.as_ref().unwrap(), String::from("mypassword"));
|
||||
let host: &Bookmark = hosts.bookmarks.get("msi-estrem").unwrap();
|
||||
assert_eq!(host.address, String::from("192.168.1.30"));
|
||||
assert_eq!(host.port, 22);
|
||||
assert_eq!(host.protocol, String::from("SFTP"));
|
||||
assert_eq!(host.username, String::from("cvisintin"));
|
||||
assert_eq!(*host.password.as_ref().unwrap(), String::from("mysecret"));
|
||||
let host: &Bookmark = hosts.bookmarks.get("aws-server-prod1").unwrap();
|
||||
assert_eq!(host.address, String::from("51.23.67.12"));
|
||||
assert_eq!(host.port, 21);
|
||||
assert_eq!(host.protocol, String::from("FTPS"));
|
||||
assert_eq!(host.username, String::from("aws001"));
|
||||
assert_eq!(host.password, None);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_config_serializer_bookmarks_serializer_deserialize_nok() {
|
||||
let toml_file: tempfile::NamedTempFile = create_bad_toml_bookmarks();
|
||||
toml_file.as_file().sync_all().unwrap();
|
||||
toml_file.as_file().seek(SeekFrom::Start(0)).unwrap();
|
||||
// Parse
|
||||
assert!(deserialize::<UserHosts>(Box::new(toml_file)).is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_config_serializer_bookmarks_serializer_serialize() {
|
||||
let mut bookmarks: HashMap<String, Bookmark> = HashMap::with_capacity(2);
|
||||
// Push two samples
|
||||
bookmarks.insert(
|
||||
String::from("raspberrypi2"),
|
||||
Bookmark {
|
||||
address: String::from("192.168.1.31"),
|
||||
port: 22,
|
||||
protocol: String::from("SFTP"),
|
||||
username: String::from("root"),
|
||||
password: None,
|
||||
},
|
||||
);
|
||||
bookmarks.insert(
|
||||
String::from("msi-estrem"),
|
||||
Bookmark {
|
||||
address: String::from("192.168.1.30"),
|
||||
port: 4022,
|
||||
protocol: String::from("SFTP"),
|
||||
username: String::from("cvisintin"),
|
||||
password: Some(String::from("password")),
|
||||
},
|
||||
);
|
||||
let mut recents: HashMap<String, Bookmark> = HashMap::with_capacity(1);
|
||||
recents.insert(
|
||||
String::from("ISO20201215T094000Z"),
|
||||
Bookmark {
|
||||
address: String::from("192.168.1.254"),
|
||||
port: 3022,
|
||||
protocol: String::from("SCP"),
|
||||
username: String::from("omar"),
|
||||
password: Some(String::from("aaa")),
|
||||
},
|
||||
);
|
||||
let tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
// Serialize
|
||||
let hosts: UserHosts = UserHosts { bookmarks, recents };
|
||||
assert!(serialize(&hosts, Box::new(tmpfile)).is_ok());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_config_serialization_theme_serialize() {
|
||||
let mut theme: Theme = Theme::default();
|
||||
theme.auth_address = Color::Rgb(240, 240, 240);
|
||||
let tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
let (reader, writer) = create_file_ioers(tmpfile.path());
|
||||
assert!(serialize(&theme, Box::new(writer)).is_ok());
|
||||
// Try to deserialize
|
||||
let deserialized_theme: Theme = deserialize(Box::new(reader)).ok().unwrap();
|
||||
assert_eq!(theme, deserialized_theme);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_config_serialization_theme_deserialize() {
|
||||
let toml_file = create_good_toml_theme();
|
||||
toml_file.as_file().sync_all().unwrap();
|
||||
toml_file.as_file().seek(SeekFrom::Start(0)).unwrap();
|
||||
assert!(deserialize::<Theme>(Box::new(toml_file)).is_ok());
|
||||
let toml_file = create_bad_toml_theme();
|
||||
toml_file.as_file().sync_all().unwrap();
|
||||
toml_file.as_file().seek(SeekFrom::Start(0)).unwrap();
|
||||
assert!(deserialize::<Theme>(Box::new(toml_file)).is_err());
|
||||
}
|
||||
|
||||
fn create_good_toml_bookmarks() -> tempfile::NamedTempFile {
|
||||
// Write
|
||||
let mut tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
let file_content: &str = r#"
|
||||
[bookmarks]
|
||||
raspberrypi2 = { address = "192.168.1.31", port = 22, protocol = "SFTP", username = "root", password = "mypassword" }
|
||||
msi-estrem = { address = "192.168.1.30", port = 22, protocol = "SFTP", username = "cvisintin", password = "mysecret" }
|
||||
aws-server-prod1 = { address = "51.23.67.12", port = 21, protocol = "FTPS", username = "aws001" }
|
||||
|
||||
[recents]
|
||||
ISO20201215T094000Z = { address = "172.16.104.10", port = 22, protocol = "SCP", username = "root" }
|
||||
"#;
|
||||
tmpfile.write_all(file_content.as_bytes()).unwrap();
|
||||
//write!(tmpfile, "[bookmarks]\nraspberrypi2 = {{ address = \"192.168.1.31\", port = 22, protocol = \"SFTP\", username = \"root\" }}\nmsi-estrem = {{ address = \"192.168.1.30\", port = 22, protocol = \"SFTP\", username = \"cvisintin\" }}\naws-server-prod1 = {{ address = \"51.23.67.12\", port = 21, protocol = \"FTPS\", username = \"aws001\" }}\n\n[recents]\nISO20201215T094000Z = {{ address = \"172.16.104.10\", port = 22, protocol = \"SCP\", username = \"root\" }}\n");
|
||||
tmpfile
|
||||
}
|
||||
|
||||
fn create_bad_toml_bookmarks() -> tempfile::NamedTempFile {
|
||||
// Write
|
||||
let mut tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
let file_content: &str = r#"
|
||||
[bookmarks]
|
||||
raspberrypi2 = { address = "192.168.1.31", port = 22, protocol = "SFTP", username = "root"}
|
||||
msi-estrem = { address = "192.168.1.30", port = 22, protocol = "SFTP" }
|
||||
aws-server-prod1 = { address = "51.23.67.12", port = 21, protocol = "FTPS", username = "aws001" }
|
||||
|
||||
[recents]
|
||||
ISO20201215T094000Z = { address = "172.16.104.10", protocol = "SCP", username = "root", port = 22 }
|
||||
"#;
|
||||
tmpfile.write_all(file_content.as_bytes()).unwrap();
|
||||
tmpfile
|
||||
}
|
||||
|
||||
fn create_good_toml_theme() -> tempfile::NamedTempFile {
|
||||
let mut tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
let file_content: &str = r##"auth_address = "Yellow"
|
||||
auth_bookmarks = "LightGreen"
|
||||
auth_password = "LightBlue"
|
||||
auth_port = "LightCyan"
|
||||
auth_protocol = "LightGreen"
|
||||
auth_recents = "LightBlue"
|
||||
auth_username = "LightMagenta"
|
||||
misc_error_dialog = "Red"
|
||||
misc_input_dialog = "240,240,240"
|
||||
misc_keys = "Cyan"
|
||||
misc_quit_dialog = "Yellow"
|
||||
misc_save_dialog = "Cyan"
|
||||
misc_warn_dialog = "LightRed"
|
||||
transfer_local_explorer_background = "rgb(240, 240, 240)"
|
||||
transfer_local_explorer_foreground = "rgb(60, 60, 60)"
|
||||
transfer_local_explorer_highlighted = "Yellow"
|
||||
transfer_log_background = "255, 255, 255"
|
||||
transfer_log_window = "LightGreen"
|
||||
transfer_progress_bar_full = "forestgreen"
|
||||
transfer_progress_bar_partial = "Green"
|
||||
transfer_remote_explorer_background = "#f0f0f0"
|
||||
transfer_remote_explorer_foreground = "rgb(40, 40, 40)"
|
||||
transfer_remote_explorer_highlighted = "LightBlue"
|
||||
transfer_status_hidden = "LightBlue"
|
||||
transfer_status_sorting = "LightYellow"
|
||||
transfer_status_sync_browsing = "LightGreen"
|
||||
"##;
|
||||
tmpfile.write_all(file_content.as_bytes()).unwrap();
|
||||
tmpfile
|
||||
}
|
||||
|
||||
fn create_bad_toml_theme() -> tempfile::NamedTempFile {
|
||||
let mut tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
let file_content: &str = r#"
|
||||
auth_address = "Yellow"
|
||||
auth_bookmarks = "LightGreen"
|
||||
auth_password = "LightBlue"
|
||||
auth_port = "LightCyan"
|
||||
auth_protocol = "LightGreen"
|
||||
auth_recents = "LightBlue"
|
||||
auth_username = "LightMagenta"
|
||||
misc_error_dialog = "Red"
|
||||
misc_input_dialog = "240,240,240"
|
||||
misc_keys = "Cyan"
|
||||
misc_quit_dialog = "Yellow"
|
||||
misc_warn_dialog = "LightRed"
|
||||
transfer_local_explorer_text = "rgb(240, 240, 240)"
|
||||
transfer_local_explorer_window = "Yellow"
|
||||
transfer_log_text = "255, 255, 255"
|
||||
transfer_log_window = "LightGreen"
|
||||
transfer_progress_bar = "Green"
|
||||
transfer_remote_explorer_text = "verdazzurro"
|
||||
transfer_remote_explorer_window = "LightBlue"
|
||||
transfer_status_hidden = "LightBlue"
|
||||
transfer_status_sorting = "LightYellow"
|
||||
transfer_status_sync_browsing = "LightGreen"
|
||||
"#;
|
||||
tmpfile.write_all(file_content.as_bytes()).unwrap();
|
||||
tmpfile
|
||||
}
|
||||
}
|
||||
@@ -1,250 +0,0 @@
|
||||
//! ## Serializer
|
||||
//!
|
||||
//! `serializer` is the module which provides the serializer/deserializer for configuration
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
use super::{SerializerError, SerializerErrorKind, UserConfig};
|
||||
|
||||
use std::io::{Read, Write};
|
||||
|
||||
pub struct ConfigSerializer;
|
||||
|
||||
impl ConfigSerializer {
|
||||
/// ### serialize
|
||||
///
|
||||
/// Serialize `UserConfig` into TOML and write content to writable
|
||||
pub fn serialize(
|
||||
&self,
|
||||
mut writable: Box<dyn Write>,
|
||||
cfg: &UserConfig,
|
||||
) -> Result<(), SerializerError> {
|
||||
// Serialize content
|
||||
let data: String = match toml::ser::to_string(cfg) {
|
||||
Ok(dt) => dt,
|
||||
Err(err) => {
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::SerializationError,
|
||||
err.to_string(),
|
||||
))
|
||||
}
|
||||
};
|
||||
// Write file
|
||||
match writable.write_all(data.as_bytes()) {
|
||||
Ok(_) => Ok(()),
|
||||
Err(err) => Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::IoError,
|
||||
err.to_string(),
|
||||
)),
|
||||
}
|
||||
}
|
||||
|
||||
/// ### deserialize
|
||||
///
|
||||
/// Read data from readable and deserialize its content as TOML
|
||||
pub fn deserialize(&self, mut readable: Box<dyn Read>) -> Result<UserConfig, SerializerError> {
|
||||
// Read file content
|
||||
let mut data: String = String::new();
|
||||
if let Err(err) = readable.read_to_string(&mut data) {
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::IoError,
|
||||
err.to_string(),
|
||||
));
|
||||
}
|
||||
// Deserialize
|
||||
match toml::de::from_str(data.as_str()) {
|
||||
Ok(hosts) => Ok(hosts),
|
||||
Err(err) => Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::SyntaxError,
|
||||
err.to_string(),
|
||||
)),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// Tests
|
||||
|
||||
#[cfg(test)]
|
||||
mod tests {
|
||||
|
||||
use super::*;
|
||||
|
||||
use std::io::{Seek, SeekFrom};
|
||||
use std::path::PathBuf;
|
||||
|
||||
#[test]
|
||||
fn test_config_serializer_deserialize_ok() {
|
||||
let toml_file: tempfile::NamedTempFile = create_good_toml();
|
||||
toml_file.as_file().sync_all().unwrap();
|
||||
toml_file.as_file().seek(SeekFrom::Start(0)).unwrap();
|
||||
// Parse
|
||||
let deserializer: ConfigSerializer = ConfigSerializer {};
|
||||
let cfg = deserializer.deserialize(Box::new(toml_file));
|
||||
assert!(cfg.is_ok());
|
||||
let cfg: UserConfig = cfg.ok().unwrap();
|
||||
// Verify configuration
|
||||
// Verify ui
|
||||
assert_eq!(cfg.user_interface.default_protocol, String::from("SCP"));
|
||||
assert_eq!(cfg.user_interface.text_editor, PathBuf::from("vim"));
|
||||
assert_eq!(cfg.user_interface.show_hidden_files, true);
|
||||
assert_eq!(cfg.user_interface.check_for_updates.unwrap(), true);
|
||||
assert_eq!(cfg.user_interface.group_dirs, Some(String::from("last")));
|
||||
assert_eq!(
|
||||
cfg.user_interface.file_fmt,
|
||||
Some(String::from("{NAME} {PEX}"))
|
||||
);
|
||||
// Verify keys
|
||||
assert_eq!(
|
||||
*cfg.remote
|
||||
.ssh_keys
|
||||
.get(&String::from("192.168.1.31"))
|
||||
.unwrap(),
|
||||
PathBuf::from("/home/omar/.ssh/raspberry.key")
|
||||
);
|
||||
assert_eq!(
|
||||
*cfg.remote
|
||||
.ssh_keys
|
||||
.get(&String::from("192.168.1.32"))
|
||||
.unwrap(),
|
||||
PathBuf::from("/home/omar/.ssh/beaglebone.key")
|
||||
);
|
||||
assert!(cfg.remote.ssh_keys.get(&String::from("1.1.1.1")).is_none());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_config_serializer_deserialize_ok_no_opts() {
|
||||
let toml_file: tempfile::NamedTempFile = create_good_toml_no_opts();
|
||||
toml_file.as_file().sync_all().unwrap();
|
||||
toml_file.as_file().seek(SeekFrom::Start(0)).unwrap();
|
||||
// Parse
|
||||
let deserializer: ConfigSerializer = ConfigSerializer {};
|
||||
let cfg = deserializer.deserialize(Box::new(toml_file));
|
||||
assert!(cfg.is_ok());
|
||||
let cfg: UserConfig = cfg.ok().unwrap();
|
||||
// Verify configuration
|
||||
// Verify ui
|
||||
assert_eq!(cfg.user_interface.default_protocol, String::from("SCP"));
|
||||
assert_eq!(cfg.user_interface.text_editor, PathBuf::from("vim"));
|
||||
assert_eq!(cfg.user_interface.show_hidden_files, true);
|
||||
assert_eq!(cfg.user_interface.group_dirs, None);
|
||||
assert!(cfg.user_interface.check_for_updates.is_none());
|
||||
assert_eq!(cfg.user_interface.file_fmt, None);
|
||||
// Verify keys
|
||||
assert_eq!(
|
||||
*cfg.remote
|
||||
.ssh_keys
|
||||
.get(&String::from("192.168.1.31"))
|
||||
.unwrap(),
|
||||
PathBuf::from("/home/omar/.ssh/raspberry.key")
|
||||
);
|
||||
assert_eq!(
|
||||
*cfg.remote
|
||||
.ssh_keys
|
||||
.get(&String::from("192.168.1.32"))
|
||||
.unwrap(),
|
||||
PathBuf::from("/home/omar/.ssh/beaglebone.key")
|
||||
);
|
||||
assert!(cfg.remote.ssh_keys.get(&String::from("1.1.1.1")).is_none());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_config_serializer_deserialize_nok() {
|
||||
let toml_file: tempfile::NamedTempFile = create_bad_toml();
|
||||
toml_file.as_file().sync_all().unwrap();
|
||||
toml_file.as_file().seek(SeekFrom::Start(0)).unwrap();
|
||||
// Parse
|
||||
let deserializer: ConfigSerializer = ConfigSerializer {};
|
||||
assert!(deserializer.deserialize(Box::new(toml_file)).is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_config_serializer_serialize() {
|
||||
let mut cfg: UserConfig = UserConfig::default();
|
||||
let toml_file: tempfile::NamedTempFile = tempfile::NamedTempFile::new().ok().unwrap();
|
||||
// Insert key
|
||||
cfg.remote.ssh_keys.insert(
|
||||
String::from("192.168.1.31"),
|
||||
PathBuf::from("/home/omar/.ssh/id_rsa"),
|
||||
);
|
||||
// Serialize
|
||||
let serializer: ConfigSerializer = ConfigSerializer {};
|
||||
let writer: Box<dyn Write> = Box::new(std::fs::File::create(toml_file.path()).unwrap());
|
||||
assert!(serializer.serialize(writer, &cfg).is_ok());
|
||||
// Reload configuration and check if it's ok
|
||||
toml_file.as_file().sync_all().unwrap();
|
||||
toml_file.as_file().seek(SeekFrom::Start(0)).unwrap();
|
||||
assert!(serializer.deserialize(Box::new(toml_file)).is_ok());
|
||||
}
|
||||
|
||||
fn create_good_toml() -> tempfile::NamedTempFile {
|
||||
// Write
|
||||
let mut tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
let file_content: &str = r#"
|
||||
[user_interface]
|
||||
default_protocol = "SCP"
|
||||
text_editor = "vim"
|
||||
show_hidden_files = true
|
||||
check_for_updates = true
|
||||
group_dirs = "last"
|
||||
file_fmt = "{NAME} {PEX}"
|
||||
|
||||
[remote.ssh_keys]
|
||||
"192.168.1.31" = "/home/omar/.ssh/raspberry.key"
|
||||
"192.168.1.32" = "/home/omar/.ssh/beaglebone.key"
|
||||
"#;
|
||||
tmpfile.write_all(file_content.as_bytes()).unwrap();
|
||||
tmpfile
|
||||
}
|
||||
|
||||
fn create_good_toml_no_opts() -> tempfile::NamedTempFile {
|
||||
// Write
|
||||
let mut tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
let file_content: &str = r#"
|
||||
[user_interface]
|
||||
default_protocol = "SCP"
|
||||
text_editor = "vim"
|
||||
show_hidden_files = true
|
||||
|
||||
[remote.ssh_keys]
|
||||
"192.168.1.31" = "/home/omar/.ssh/raspberry.key"
|
||||
"192.168.1.32" = "/home/omar/.ssh/beaglebone.key"
|
||||
"#;
|
||||
tmpfile.write_all(file_content.as_bytes()).unwrap();
|
||||
tmpfile
|
||||
}
|
||||
|
||||
fn create_bad_toml() -> tempfile::NamedTempFile {
|
||||
// Write
|
||||
let mut tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
let file_content: &str = r#"
|
||||
[user_interface]
|
||||
default_protocol = "SFTP"
|
||||
|
||||
[remote.ssh_keys]
|
||||
"192.168.1.31" = "/home/omar/.ssh/raspberry.key"
|
||||
"#;
|
||||
tmpfile.write_all(file_content.as_bytes()).unwrap();
|
||||
tmpfile
|
||||
}
|
||||
}
|
||||
267
src/config/themes.rs
Normal file
@@ -0,0 +1,267 @@
|
||||
//! ## Themes
|
||||
//!
|
||||
//! `themes` is the module which provides the themes configurations and the serializers
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use crate::utils::fmt::fmt_color;
|
||||
use crate::utils::parser::parse_color;
|
||||
// ext
|
||||
use serde::{de::Error as DeError, Deserialize, Deserializer, Serialize, Serializer};
|
||||
use tuirealm::tui::style::Color;
|
||||
|
||||
/// ### Theme
|
||||
///
|
||||
/// Theme contains all the colors lookup table for termscp
|
||||
#[derive(Clone, Debug, Deserialize, PartialEq, Serialize)]
|
||||
pub struct Theme {
|
||||
// -- auth
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub auth_address: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub auth_bookmarks: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub auth_password: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub auth_port: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub auth_protocol: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub auth_recents: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub auth_username: Color,
|
||||
// -- misc
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub misc_error_dialog: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub misc_input_dialog: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub misc_keys: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub misc_quit_dialog: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub misc_save_dialog: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub misc_warn_dialog: Color,
|
||||
// -- transfer
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub transfer_local_explorer_background: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub transfer_local_explorer_foreground: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub transfer_local_explorer_highlighted: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub transfer_log_background: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub transfer_log_window: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub transfer_progress_bar_full: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub transfer_progress_bar_partial: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub transfer_remote_explorer_background: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub transfer_remote_explorer_foreground: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub transfer_remote_explorer_highlighted: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub transfer_status_hidden: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub transfer_status_sorting: Color,
|
||||
#[serde(
|
||||
deserialize_with = "deserialize_color",
|
||||
serialize_with = "serialize_color"
|
||||
)]
|
||||
pub transfer_status_sync_browsing: Color,
|
||||
}
|
||||
|
||||
impl Default for Theme {
|
||||
fn default() -> Self {
|
||||
Self {
|
||||
auth_address: Color::Yellow,
|
||||
auth_bookmarks: Color::LightGreen,
|
||||
auth_password: Color::LightBlue,
|
||||
auth_port: Color::LightCyan,
|
||||
auth_protocol: Color::LightGreen,
|
||||
auth_recents: Color::LightBlue,
|
||||
auth_username: Color::LightMagenta,
|
||||
misc_error_dialog: Color::Red,
|
||||
misc_input_dialog: Color::Reset,
|
||||
misc_keys: Color::Cyan,
|
||||
misc_quit_dialog: Color::Yellow,
|
||||
misc_save_dialog: Color::LightCyan,
|
||||
misc_warn_dialog: Color::LightRed,
|
||||
transfer_local_explorer_background: Color::Reset,
|
||||
transfer_local_explorer_foreground: Color::Reset,
|
||||
transfer_local_explorer_highlighted: Color::Yellow,
|
||||
transfer_log_background: Color::Reset,
|
||||
transfer_log_window: Color::LightGreen,
|
||||
transfer_progress_bar_partial: Color::Green,
|
||||
transfer_progress_bar_full: Color::Green,
|
||||
transfer_remote_explorer_background: Color::Reset,
|
||||
transfer_remote_explorer_foreground: Color::Reset,
|
||||
transfer_remote_explorer_highlighted: Color::LightBlue,
|
||||
transfer_status_hidden: Color::LightBlue,
|
||||
transfer_status_sorting: Color::LightYellow,
|
||||
transfer_status_sync_browsing: Color::LightGreen,
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// -- deserializer
|
||||
|
||||
fn deserialize_color<'de, D>(deserializer: D) -> Result<Color, D::Error>
|
||||
where
|
||||
D: Deserializer<'de>,
|
||||
{
|
||||
let s: &str = Deserialize::deserialize(deserializer)?;
|
||||
// Parse color
|
||||
match parse_color(s) {
|
||||
None => Err(DeError::custom("Invalid color")),
|
||||
Some(color) => Ok(color),
|
||||
}
|
||||
}
|
||||
|
||||
fn serialize_color<S>(color: &Color, serializer: S) -> Result<S::Ok, S::Error>
|
||||
where
|
||||
S: Serializer,
|
||||
{
|
||||
// Convert color to string
|
||||
let s: String = fmt_color(color);
|
||||
serializer.serialize_str(s.as_str())
|
||||
}
|
||||
|
||||
#[cfg(test)]
|
||||
mod test {
|
||||
use super::*;
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
|
||||
#[test]
|
||||
fn test_config_themes_default() {
|
||||
let theme: Theme = Theme::default();
|
||||
assert_eq!(theme.auth_address, Color::Yellow);
|
||||
assert_eq!(theme.auth_bookmarks, Color::LightGreen);
|
||||
assert_eq!(theme.auth_password, Color::LightBlue);
|
||||
assert_eq!(theme.auth_port, Color::LightCyan);
|
||||
assert_eq!(theme.auth_protocol, Color::LightGreen);
|
||||
assert_eq!(theme.auth_recents, Color::LightBlue);
|
||||
assert_eq!(theme.auth_username, Color::LightMagenta);
|
||||
assert_eq!(theme.misc_error_dialog, Color::Red);
|
||||
assert_eq!(theme.misc_input_dialog, Color::Reset);
|
||||
assert_eq!(theme.misc_keys, Color::Cyan);
|
||||
assert_eq!(theme.misc_quit_dialog, Color::Yellow);
|
||||
assert_eq!(theme.misc_save_dialog, Color::LightCyan);
|
||||
assert_eq!(theme.misc_warn_dialog, Color::LightRed);
|
||||
assert_eq!(theme.transfer_local_explorer_background, Color::Reset);
|
||||
assert_eq!(theme.transfer_local_explorer_foreground, Color::Reset);
|
||||
assert_eq!(theme.transfer_local_explorer_highlighted, Color::Yellow);
|
||||
assert_eq!(theme.transfer_log_background, Color::Reset);
|
||||
assert_eq!(theme.transfer_log_window, Color::LightGreen);
|
||||
assert_eq!(theme.transfer_progress_bar_full, Color::Green);
|
||||
assert_eq!(theme.transfer_progress_bar_partial, Color::Green);
|
||||
assert_eq!(theme.transfer_remote_explorer_background, Color::Reset);
|
||||
assert_eq!(theme.transfer_remote_explorer_foreground, Color::Reset);
|
||||
assert_eq!(theme.transfer_remote_explorer_highlighted, Color::LightBlue);
|
||||
assert_eq!(theme.transfer_status_hidden, Color::LightBlue);
|
||||
assert_eq!(theme.transfer_status_sorting, Color::LightYellow);
|
||||
assert_eq!(theme.transfer_status_sync_browsing, Color::LightGreen);
|
||||
}
|
||||
}
|
||||
@@ -25,8 +25,6 @@
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// dependencies
|
||||
extern crate wildmatch;
|
||||
// locals
|
||||
use crate::fs::{FsEntry, FsFile};
|
||||
// ext
|
||||
@@ -36,14 +34,17 @@ use thiserror::Error;
|
||||
use wildmatch::WildMatch;
|
||||
// exports
|
||||
pub mod ftp_transfer;
|
||||
pub mod params;
|
||||
pub mod scp_transfer;
|
||||
pub mod sftp_transfer;
|
||||
|
||||
pub use params::FileTransferParams;
|
||||
|
||||
/// ## FileTransferProtocol
|
||||
///
|
||||
/// This enum defines the different transfer protocol available in TermSCP
|
||||
/// This enum defines the different transfer protocol available in termscp
|
||||
|
||||
#[derive(PartialEq, std::fmt::Debug, std::clone::Clone, Copy)]
|
||||
#[derive(PartialEq, Debug, std::clone::Clone, Copy)]
|
||||
pub enum FileTransferProtocol {
|
||||
Sftp,
|
||||
Scp,
|
||||
@@ -53,17 +54,25 @@ pub enum FileTransferProtocol {
|
||||
/// ## FileTransferError
|
||||
///
|
||||
/// FileTransferError defines the possible errors available for a file transfer
|
||||
#[derive(std::fmt::Debug)]
|
||||
#[derive(Debug)]
|
||||
pub struct FileTransferError {
|
||||
code: FileTransferErrorType,
|
||||
msg: Option<String>,
|
||||
}
|
||||
|
||||
impl FileTransferError {
|
||||
/// ### kind
|
||||
///
|
||||
/// Returns the error kind
|
||||
pub fn kind(&self) -> FileTransferErrorType {
|
||||
self.code
|
||||
}
|
||||
}
|
||||
|
||||
/// ## FileTransferErrorType
|
||||
///
|
||||
/// FileTransferErrorType defines the possible errors available for a file transfer
|
||||
#[allow(dead_code)]
|
||||
#[derive(Error, Debug)]
|
||||
#[derive(Error, Debug, Clone, Copy, PartialEq)]
|
||||
pub enum FileTransferErrorType {
|
||||
#[error("Authentication failed")]
|
||||
AuthenticationFailed,
|
||||
@@ -75,10 +84,10 @@ pub enum FileTransferErrorType {
|
||||
SslError,
|
||||
#[error("Could not stat directory")]
|
||||
DirStatFailed,
|
||||
#[error("Directory already exists")]
|
||||
DirectoryAlreadyExists,
|
||||
#[error("Failed to create file")]
|
||||
FileCreateDenied,
|
||||
#[error("IO error: {0}")]
|
||||
IoErr(std::io::Error),
|
||||
#[error("No such file or directory")]
|
||||
NoSuchFileOrDirectory,
|
||||
#[error("Not enough permissions")]
|
||||
@@ -173,7 +182,7 @@ pub trait FileTransfer {
|
||||
/// ### mkdir
|
||||
///
|
||||
/// Make directory
|
||||
/// You must return error in case the directory already exists
|
||||
/// In case the directory already exists, it must return an Error of kind `FileTransferErrorType::DirectoryAlreadyExists`
|
||||
fn mkdir(&mut self, dir: &Path) -> Result<(), FileTransferError>;
|
||||
|
||||
/// ### remove
|
||||
@@ -278,10 +287,7 @@ pub trait FileTransfer {
|
||||
if filter.matches(dir.name.as_str()) {
|
||||
drained.push(FsEntry::Directory(dir.clone()));
|
||||
}
|
||||
match self.iter_search(dir.abs_path.as_path(), filter) {
|
||||
Ok(mut filtered) => drained.append(&mut filtered),
|
||||
Err(err) => return Err(err),
|
||||
}
|
||||
drained.append(&mut self.iter_search(dir.abs_path.as_path(), filter)?);
|
||||
}
|
||||
FsEntry::File(file) => {
|
||||
if filter.matches(file.name.as_str()) {
|
||||
@@ -313,14 +319,14 @@ impl std::string::ToString for FileTransferProtocol {
|
||||
}
|
||||
|
||||
impl std::str::FromStr for FileTransferProtocol {
|
||||
type Err = ();
|
||||
type Err = String;
|
||||
fn from_str(s: &str) -> Result<Self, Self::Err> {
|
||||
match s.to_ascii_uppercase().as_str() {
|
||||
"FTP" => Ok(FileTransferProtocol::Ftp(false)),
|
||||
"FTPS" => Ok(FileTransferProtocol::Ftp(true)),
|
||||
"SCP" => Ok(FileTransferProtocol::Scp),
|
||||
"SFTP" => Ok(FileTransferProtocol::Sftp),
|
||||
_ => Err(()),
|
||||
_ => Err(s.to_string()),
|
||||
}
|
||||
}
|
||||
}
|
||||
@@ -332,6 +338,7 @@ mod tests {
|
||||
|
||||
use super::*;
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
use std::str::FromStr;
|
||||
use std::string::ToString;
|
||||
|
||||
@@ -396,13 +403,13 @@ mod tests {
|
||||
#[test]
|
||||
fn test_filetransfer_mod_error() {
|
||||
let err: FileTransferError = FileTransferError::new_ex(
|
||||
FileTransferErrorType::IoErr(std::io::Error::from(std::io::ErrorKind::AddrInUse)),
|
||||
FileTransferErrorType::NoSuchFileOrDirectory,
|
||||
String::from("non va una mazza"),
|
||||
);
|
||||
assert_eq!(*err.msg.as_ref().unwrap(), String::from("non va una mazza"));
|
||||
assert_eq!(
|
||||
format!("{}", err),
|
||||
String::from("IO error: address in use (non va una mazza)")
|
||||
String::from("No such file or directory (non va una mazza)")
|
||||
);
|
||||
assert_eq!(
|
||||
format!(
|
||||
@@ -481,5 +488,7 @@ mod tests {
|
||||
),
|
||||
String::from("Unsupported feature")
|
||||
);
|
||||
let err = FileTransferError::new(FileTransferErrorType::UnsupportedFeature);
|
||||
assert_eq!(err.kind(), FileTransferErrorType::UnsupportedFeature);
|
||||
}
|
||||
}
|
||||
|
||||
137
src/filetransfer/params.rs
Normal file
@@ -0,0 +1,137 @@
|
||||
//! ## Params
|
||||
//!
|
||||
//! file transfer parameters
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
use super::FileTransferProtocol;
|
||||
|
||||
use std::path::{Path, PathBuf};
|
||||
|
||||
/// ### FileTransferParams
|
||||
///
|
||||
/// Holds connection parameters for file transfers
|
||||
#[derive(Clone)]
|
||||
pub struct FileTransferParams {
|
||||
pub address: String,
|
||||
pub port: u16,
|
||||
pub protocol: FileTransferProtocol,
|
||||
pub username: Option<String>,
|
||||
pub password: Option<String>,
|
||||
pub entry_directory: Option<PathBuf>,
|
||||
}
|
||||
|
||||
impl FileTransferParams {
|
||||
/// ### new
|
||||
///
|
||||
/// Instantiates a new `FileTransferParams`
|
||||
pub fn new<S: AsRef<str>>(address: S) -> Self {
|
||||
Self {
|
||||
address: address.as_ref().to_string(),
|
||||
port: 22,
|
||||
protocol: FileTransferProtocol::Sftp,
|
||||
username: None,
|
||||
password: None,
|
||||
entry_directory: None,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### port
|
||||
///
|
||||
/// Set port for params
|
||||
pub fn port(mut self, port: u16) -> Self {
|
||||
self.port = port;
|
||||
self
|
||||
}
|
||||
|
||||
/// ### protocol
|
||||
///
|
||||
/// Set protocol for params
|
||||
pub fn protocol(mut self, protocol: FileTransferProtocol) -> Self {
|
||||
self.protocol = protocol;
|
||||
self
|
||||
}
|
||||
|
||||
/// ### username
|
||||
///
|
||||
/// Set username for params
|
||||
pub fn username<S: AsRef<str>>(mut self, username: Option<S>) -> Self {
|
||||
self.username = username.map(|x| x.as_ref().to_string());
|
||||
self
|
||||
}
|
||||
|
||||
/// ### password
|
||||
///
|
||||
/// Set password for params
|
||||
pub fn password<S: AsRef<str>>(mut self, password: Option<S>) -> Self {
|
||||
self.password = password.map(|x| x.as_ref().to_string());
|
||||
self
|
||||
}
|
||||
|
||||
/// ### entry_directory
|
||||
///
|
||||
/// Set entry directory
|
||||
pub fn entry_directory<P: AsRef<Path>>(mut self, dir: Option<P>) -> Self {
|
||||
self.entry_directory = dir.map(|x| x.as_ref().to_path_buf());
|
||||
self
|
||||
}
|
||||
}
|
||||
|
||||
impl Default for FileTransferParams {
|
||||
fn default() -> Self {
|
||||
Self::new("localhost")
|
||||
}
|
||||
}
|
||||
|
||||
#[cfg(test)]
|
||||
mod test {
|
||||
|
||||
use super::*;
|
||||
use pretty_assertions::assert_eq;
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_params() {
|
||||
let params: FileTransferParams = FileTransferParams::new("test.rebex.net")
|
||||
.port(2222)
|
||||
.protocol(FileTransferProtocol::Scp)
|
||||
.username(Some("omar"))
|
||||
.password(Some("foobar"))
|
||||
.entry_directory(Some(&Path::new("/tmp")));
|
||||
assert_eq!(params.address.as_str(), "test.rebex.net");
|
||||
assert_eq!(params.port, 2222);
|
||||
assert_eq!(params.protocol, FileTransferProtocol::Scp);
|
||||
assert_eq!(params.username.as_ref().unwrap(), "omar");
|
||||
assert_eq!(params.password.as_ref().unwrap(), "foobar");
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_params_default() {
|
||||
let params: FileTransferParams = FileTransferParams::default();
|
||||
assert_eq!(params.address.as_str(), "localhost");
|
||||
assert_eq!(params.port, 22);
|
||||
assert_eq!(params.protocol, FileTransferProtocol::Sftp);
|
||||
assert!(params.username.is_none());
|
||||
assert!(params.password.is_none());
|
||||
}
|
||||
}
|
||||
@@ -25,13 +25,11 @@
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// Dependencies
|
||||
extern crate ssh2;
|
||||
|
||||
// Locals
|
||||
use super::{FileTransfer, FileTransferError, FileTransferErrorType};
|
||||
use crate::fs::{FsDirectory, FsEntry, FsFile};
|
||||
use crate::fs::{FsDirectory, FsEntry, FsFile, UnixPex};
|
||||
use crate::system::sshkey_storage::SshKeyStorage;
|
||||
use crate::utils::fmt::{fmt_time, shadow_password};
|
||||
|
||||
// Includes
|
||||
use ssh2::{Channel, FileStat, OpenFlags, OpenType, Session, Sftp};
|
||||
@@ -128,11 +126,11 @@ impl SftpFileTransfer {
|
||||
.map(|ext| String::from(ext.to_str().unwrap_or("")));
|
||||
let uid: Option<u32> = metadata.uid;
|
||||
let gid: Option<u32> = metadata.gid;
|
||||
let pex: Option<(u8, u8, u8)> = metadata.perm.map(|x| {
|
||||
let pex: Option<(UnixPex, UnixPex, UnixPex)> = metadata.perm.map(|x| {
|
||||
(
|
||||
((x >> 6) & 0x7) as u8,
|
||||
((x >> 3) & 0x7) as u8,
|
||||
(x & 0x7) as u8,
|
||||
UnixPex::from(((x >> 6) & 0x7) as u8),
|
||||
UnixPex::from(((x >> 3) & 0x7) as u8),
|
||||
UnixPex::from((x & 0x7) as u8),
|
||||
)
|
||||
});
|
||||
let size: u64 = metadata.size.unwrap_or(0);
|
||||
@@ -159,6 +157,19 @@ impl SftpFileTransfer {
|
||||
}
|
||||
false => None,
|
||||
};
|
||||
debug!("Follows {} attributes", path.display());
|
||||
debug!("Is directory? {}", metadata.is_dir());
|
||||
debug!("Is symlink? {}", is_symlink);
|
||||
debug!("name: {}", file_name);
|
||||
debug!("abs_path: {}", path.display());
|
||||
debug!("last_change_time: {}", fmt_time(mtime, "%Y-%m-%dT%H:%M:%S"));
|
||||
debug!("last_access_time: {}", fmt_time(mtime, "%Y-%m-%dT%H:%M:%S"));
|
||||
debug!("creation_time: {}", fmt_time(mtime, "%Y-%m-%dT%H:%M:%S"));
|
||||
debug!("symlink: {:?}", symlink);
|
||||
debug!("user: {:?}", uid);
|
||||
debug!("group: {:?}", gid);
|
||||
debug!("unix_pex: {:?}", pex);
|
||||
debug!("---------------------------------------");
|
||||
// Is a directory?
|
||||
match metadata.is_dir() {
|
||||
true => FsEntry::Directory(FsDirectory {
|
||||
@@ -167,7 +178,6 @@ impl SftpFileTransfer {
|
||||
last_change_time: mtime,
|
||||
last_access_time: atime,
|
||||
creation_time: SystemTime::UNIX_EPOCH,
|
||||
readonly: false,
|
||||
symlink,
|
||||
user: uid,
|
||||
group: gid,
|
||||
@@ -181,7 +191,6 @@ impl SftpFileTransfer {
|
||||
last_change_time: mtime,
|
||||
last_access_time: atime,
|
||||
creation_time: SystemTime::UNIX_EPOCH,
|
||||
readonly: false,
|
||||
symlink,
|
||||
user: uid,
|
||||
group: gid,
|
||||
@@ -205,6 +214,7 @@ impl SftpFileTransfer {
|
||||
match self.session.as_mut() {
|
||||
Some(session) => {
|
||||
// Create channel
|
||||
debug!("Running command: {}", cmd);
|
||||
let mut channel: Channel = match session.channel_session() {
|
||||
Ok(ch) => ch,
|
||||
Err(err) => {
|
||||
@@ -227,6 +237,7 @@ impl SftpFileTransfer {
|
||||
Ok(_) => {
|
||||
// Wait close
|
||||
let _ = channel.wait_close();
|
||||
debug!("Command output: {}", output);
|
||||
Ok(output)
|
||||
}
|
||||
Err(err) => Err(FileTransferError::new_ex(
|
||||
@@ -254,6 +265,7 @@ impl FileTransfer for SftpFileTransfer {
|
||||
password: Option<String>,
|
||||
) -> Result<Option<String>, FileTransferError> {
|
||||
// Setup tcp stream
|
||||
info!("Connecting to {}:{}", address, port);
|
||||
let socket_addresses: Vec<SocketAddr> =
|
||||
match format!("{}:{}", address, port).to_socket_addrs() {
|
||||
Ok(s) => s.collect(),
|
||||
@@ -267,7 +279,8 @@ impl FileTransfer for SftpFileTransfer {
|
||||
let mut tcp: Option<TcpStream> = None;
|
||||
// Try addresses
|
||||
for socket_addr in socket_addresses.iter() {
|
||||
match TcpStream::connect_timeout(&socket_addr, Duration::from_secs(30)) {
|
||||
debug!("Trying socket address {}", socket_addr);
|
||||
match TcpStream::connect_timeout(socket_addr, Duration::from_secs(30)) {
|
||||
Ok(stream) => {
|
||||
tcp = Some(stream);
|
||||
break;
|
||||
@@ -279,26 +292,30 @@ impl FileTransfer for SftpFileTransfer {
|
||||
let tcp: TcpStream = match tcp {
|
||||
Some(t) => t,
|
||||
None => {
|
||||
error!("No suitable socket address found; connection timeout");
|
||||
return Err(FileTransferError::new_ex(
|
||||
FileTransferErrorType::ConnectionError,
|
||||
String::from("Connection timeout"),
|
||||
))
|
||||
));
|
||||
}
|
||||
};
|
||||
// Create session
|
||||
let mut session: Session = match Session::new() {
|
||||
Ok(s) => s,
|
||||
Err(err) => {
|
||||
error!("Could not create session: {}", err);
|
||||
return Err(FileTransferError::new_ex(
|
||||
FileTransferErrorType::ConnectionError,
|
||||
err.to_string(),
|
||||
))
|
||||
));
|
||||
}
|
||||
};
|
||||
// Set TCP stream
|
||||
session.set_tcp_stream(tcp);
|
||||
// Open connection
|
||||
debug!("Initializing handshake");
|
||||
if let Err(err) = session.handshake() {
|
||||
error!("Handshake failed: {}", err);
|
||||
return Err(FileTransferError::new_ex(
|
||||
FileTransferErrorType::ConnectionError,
|
||||
err.to_string(),
|
||||
@@ -314,6 +331,11 @@ impl FileTransfer for SftpFileTransfer {
|
||||
.resolve(address.as_str(), username.as_str())
|
||||
{
|
||||
Some(rsa_key) => {
|
||||
debug!(
|
||||
"Authenticating with user {} and RSA key {}",
|
||||
username,
|
||||
rsa_key.display()
|
||||
);
|
||||
// Authenticate with RSA key
|
||||
if let Err(err) = session.userauth_pubkey_file(
|
||||
username.as_str(),
|
||||
@@ -321,6 +343,7 @@ impl FileTransfer for SftpFileTransfer {
|
||||
rsa_key.as_path(),
|
||||
password.as_deref(),
|
||||
) {
|
||||
error!("Authentication failed: {}", err);
|
||||
return Err(FileTransferError::new_ex(
|
||||
FileTransferErrorType::AuthenticationFailed,
|
||||
err.to_string(),
|
||||
@@ -329,10 +352,16 @@ impl FileTransfer for SftpFileTransfer {
|
||||
}
|
||||
None => {
|
||||
// Proceeed with username/password authentication
|
||||
debug!(
|
||||
"Authenticating with username {} and password {}",
|
||||
username,
|
||||
shadow_password(password.as_deref().unwrap_or(""))
|
||||
);
|
||||
if let Err(err) = session.userauth_password(
|
||||
username.as_str(),
|
||||
password.unwrap_or_else(|| String::from("")).as_str(),
|
||||
) {
|
||||
error!("Authentication failed: {}", err);
|
||||
return Err(FileTransferError::new_ex(
|
||||
FileTransferErrorType::AuthenticationFailed,
|
||||
err.to_string(),
|
||||
@@ -343,16 +372,19 @@ impl FileTransfer for SftpFileTransfer {
|
||||
// Set blocking to true
|
||||
session.set_blocking(true);
|
||||
// Get Sftp client
|
||||
debug!("Getting SFTP client...");
|
||||
let sftp: Sftp = match session.sftp() {
|
||||
Ok(s) => s,
|
||||
Err(err) => {
|
||||
error!("Could not get sftp client: {}", err);
|
||||
return Err(FileTransferError::new_ex(
|
||||
FileTransferErrorType::ProtocolError,
|
||||
err.to_string(),
|
||||
))
|
||||
));
|
||||
}
|
||||
};
|
||||
// Get working directory
|
||||
debug!("Getting working directory...");
|
||||
self.wrkdir = match sftp.realpath(PathBuf::from(".").as_path()) {
|
||||
Ok(p) => p,
|
||||
Err(err) => {
|
||||
@@ -367,6 +399,11 @@ impl FileTransfer for SftpFileTransfer {
|
||||
self.session = Some(session);
|
||||
// Set sftp
|
||||
self.sftp = Some(sftp);
|
||||
info!(
|
||||
"Connection established: {}; working directory {}",
|
||||
banner.as_deref().unwrap_or(""),
|
||||
self.wrkdir.display()
|
||||
);
|
||||
Ok(banner)
|
||||
}
|
||||
|
||||
@@ -374,6 +411,7 @@ impl FileTransfer for SftpFileTransfer {
|
||||
///
|
||||
/// Disconnect from the remote server
|
||||
fn disconnect(&mut self) -> Result<(), FileTransferError> {
|
||||
info!("Disconnecting from remote...");
|
||||
match self.session.as_ref() {
|
||||
Some(session) => {
|
||||
// Disconnect (greet server with 'Mandi' as they do in Friuli)
|
||||
@@ -407,6 +445,7 @@ impl FileTransfer for SftpFileTransfer {
|
||||
///
|
||||
/// Print working directory
|
||||
fn pwd(&mut self) -> Result<PathBuf, FileTransferError> {
|
||||
info!("PWD: {}", self.wrkdir.display());
|
||||
match self.sftp {
|
||||
Some(_) => Ok(self.wrkdir.clone()),
|
||||
None => Err(FileTransferError::new(
|
||||
@@ -422,10 +461,8 @@ impl FileTransfer for SftpFileTransfer {
|
||||
match self.sftp.as_ref() {
|
||||
Some(_) => {
|
||||
// Change working directory
|
||||
self.wrkdir = match self.get_remote_path(dir) {
|
||||
Ok(p) => p,
|
||||
Err(err) => return Err(err),
|
||||
};
|
||||
self.wrkdir = self.get_remote_path(dir)?;
|
||||
info!("Changed working directory to {}", self.wrkdir.display());
|
||||
Ok(self.wrkdir.clone())
|
||||
}
|
||||
None => Err(FileTransferError::new(
|
||||
@@ -437,11 +474,47 @@ impl FileTransfer for SftpFileTransfer {
|
||||
/// ### copy
|
||||
///
|
||||
/// Copy file to destination
|
||||
fn copy(&mut self, _src: &FsEntry, _dst: &Path) -> Result<(), FileTransferError> {
|
||||
// SFTP doesn't support file copy
|
||||
Err(FileTransferError::new(
|
||||
FileTransferErrorType::UnsupportedFeature,
|
||||
))
|
||||
fn copy(&mut self, src: &FsEntry, dst: &Path) -> Result<(), FileTransferError> {
|
||||
// NOTE: use SCP command to perform copy (UNSAFE)
|
||||
match self.is_connected() {
|
||||
true => {
|
||||
let dst: PathBuf = self.get_abs_path(dst);
|
||||
info!(
|
||||
"Copying {} to {}",
|
||||
src.get_abs_path().display(),
|
||||
dst.display()
|
||||
);
|
||||
// Run `cp -rf`
|
||||
match self.perform_shell_cmd_with_path(
|
||||
format!(
|
||||
"cp -rf \"{}\" \"{}\"; echo $?",
|
||||
src.get_abs_path().display(),
|
||||
dst.display()
|
||||
)
|
||||
.as_str(),
|
||||
) {
|
||||
Ok(output) =>
|
||||
// Check if output is 0
|
||||
{
|
||||
match output.as_str().trim() == "0" {
|
||||
true => Ok(()), // File copied
|
||||
false => Err(FileTransferError::new_ex(
|
||||
// Could not copy file
|
||||
FileTransferErrorType::FileCreateDenied,
|
||||
format!("\"{}\"", dst.display()),
|
||||
)),
|
||||
}
|
||||
}
|
||||
Err(err) => Err(FileTransferError::new_ex(
|
||||
FileTransferErrorType::ProtocolError,
|
||||
err.to_string(),
|
||||
)),
|
||||
}
|
||||
}
|
||||
false => Err(FileTransferError::new(
|
||||
FileTransferErrorType::UninitializedSession,
|
||||
)),
|
||||
}
|
||||
}
|
||||
|
||||
/// ### list_dir
|
||||
@@ -451,10 +524,8 @@ impl FileTransfer for SftpFileTransfer {
|
||||
match self.sftp.as_ref() {
|
||||
Some(sftp) => {
|
||||
// Get path
|
||||
let dir: PathBuf = match self.get_remote_path(path) {
|
||||
Ok(p) => p,
|
||||
Err(err) => return Err(err),
|
||||
};
|
||||
let dir: PathBuf = self.get_remote_path(path)?;
|
||||
info!("Getting file entries in {}", path.display());
|
||||
// Get files
|
||||
match sftp.readdir(dir.as_path()) {
|
||||
Err(err) => Err(FileTransferError::new_ex(
|
||||
@@ -481,11 +552,20 @@ impl FileTransfer for SftpFileTransfer {
|
||||
/// ### mkdir
|
||||
///
|
||||
/// Make directory
|
||||
/// In case the directory already exists, it must return an Error of kind `FileTransferErrorType::DirectoryAlreadyExists`
|
||||
fn mkdir(&mut self, dir: &Path) -> Result<(), FileTransferError> {
|
||||
match self.sftp.as_ref() {
|
||||
Some(sftp) => {
|
||||
// Make directory
|
||||
let path: PathBuf = self.get_abs_path(PathBuf::from(dir).as_path());
|
||||
// If directory already exists, return Err
|
||||
if sftp.stat(path.as_path()).is_ok() {
|
||||
error!("Directory {} already exists", path.display());
|
||||
return Err(FileTransferError::new(
|
||||
FileTransferErrorType::DirectoryAlreadyExists,
|
||||
));
|
||||
}
|
||||
info!("Making directory {}", path.display());
|
||||
match sftp.mkdir(path.as_path(), 0o775) {
|
||||
Ok(_) => Ok(()),
|
||||
Err(err) => Err(FileTransferError::new_ex(
|
||||
@@ -510,6 +590,7 @@ impl FileTransfer for SftpFileTransfer {
|
||||
));
|
||||
}
|
||||
// Match if file is a file or a directory
|
||||
info!("Removing file {}", file.get_abs_path().display());
|
||||
match file {
|
||||
FsEntry::File(f) => {
|
||||
// Remove file
|
||||
@@ -523,13 +604,11 @@ impl FileTransfer for SftpFileTransfer {
|
||||
}
|
||||
FsEntry::Directory(d) => {
|
||||
// Remove recursively
|
||||
debug!("{} is a directory; removing all directory entries", d.name);
|
||||
// Get directory files
|
||||
let directory_content: Vec<FsEntry> = match self.list_dir(d.abs_path.as_path()) {
|
||||
Ok(entries) => entries,
|
||||
Err(err) => return Err(err),
|
||||
};
|
||||
let directory_content: Vec<FsEntry> = self.list_dir(d.abs_path.as_path())?;
|
||||
for entry in directory_content.iter() {
|
||||
if let Err(err) = self.remove(&entry) {
|
||||
if let Err(err) = self.remove(entry) {
|
||||
return Err(err);
|
||||
}
|
||||
}
|
||||
@@ -554,6 +633,11 @@ impl FileTransfer for SftpFileTransfer {
|
||||
FileTransferErrorType::UninitializedSession,
|
||||
)),
|
||||
Some(sftp) => {
|
||||
info!(
|
||||
"Moving {} to {}",
|
||||
file.get_abs_path().display(),
|
||||
dst.display()
|
||||
);
|
||||
// Resolve destination path
|
||||
let abs_dst: PathBuf = self.get_abs_path(dst);
|
||||
// Get abs path of entry
|
||||
@@ -576,10 +660,8 @@ impl FileTransfer for SftpFileTransfer {
|
||||
match self.sftp.as_ref() {
|
||||
Some(sftp) => {
|
||||
// Get path
|
||||
let dir: PathBuf = match self.get_remote_path(path) {
|
||||
Ok(p) => p,
|
||||
Err(err) => return Err(err),
|
||||
};
|
||||
let dir: PathBuf = self.get_remote_path(path)?;
|
||||
info!("Stat file {}", dir.display());
|
||||
// Get file
|
||||
match sftp.stat(dir.as_path()) {
|
||||
Ok(metadata) => Ok(self.make_fsentry(dir.as_path(), &metadata)),
|
||||
@@ -599,6 +681,7 @@ impl FileTransfer for SftpFileTransfer {
|
||||
///
|
||||
/// Execute a command on remote host
|
||||
fn exec(&mut self, cmd: &str) -> Result<String, FileTransferError> {
|
||||
info!("Executing command {}", cmd);
|
||||
match self.is_connected() {
|
||||
true => match self.perform_shell_cmd_with_path(cmd) {
|
||||
Ok(output) => Ok(output),
|
||||
@@ -629,14 +712,24 @@ impl FileTransfer for SftpFileTransfer {
|
||||
)),
|
||||
Some(sftp) => {
|
||||
let remote_path: PathBuf = self.get_abs_path(file_name);
|
||||
info!(
|
||||
"Sending file {} to {}",
|
||||
local.abs_path.display(),
|
||||
remote_path.display()
|
||||
);
|
||||
// Calculate file mode
|
||||
let mode: i32 = match local.unix_pex {
|
||||
None => 0o644,
|
||||
Some((u, g, o)) => ((u as i32) << 6) + ((g as i32) << 3) + (o as i32),
|
||||
Some((u, g, o)) => {
|
||||
((u.as_byte() as i32) << 6)
|
||||
+ ((g.as_byte() as i32) << 3)
|
||||
+ (o.as_byte() as i32)
|
||||
}
|
||||
};
|
||||
debug!("File mode {:?}", mode);
|
||||
match sftp.open_mode(
|
||||
remote_path.as_path(),
|
||||
OpenFlags::WRITE | OpenFlags::CREATE | OpenFlags::APPEND | OpenFlags::TRUNCATE,
|
||||
OpenFlags::WRITE | OpenFlags::CREATE | OpenFlags::TRUNCATE,
|
||||
mode,
|
||||
OpenType::File,
|
||||
) {
|
||||
@@ -660,10 +753,8 @@ impl FileTransfer for SftpFileTransfer {
|
||||
)),
|
||||
Some(sftp) => {
|
||||
// Get remote file name
|
||||
let remote_path: PathBuf = match self.get_remote_path(file.abs_path.as_path()) {
|
||||
Ok(p) => p,
|
||||
Err(err) => return Err(err),
|
||||
};
|
||||
let remote_path: PathBuf = self.get_remote_path(file.abs_path.as_path())?;
|
||||
info!("Receiving file {}", remote_path.display());
|
||||
// Open remote file
|
||||
match sftp.open(remote_path.as_path()) {
|
||||
Ok(file) => Ok(Box::new(BufReader::with_capacity(65536, file))),
|
||||
@@ -701,6 +792,10 @@ impl FileTransfer for SftpFileTransfer {
|
||||
mod tests {
|
||||
|
||||
use super::*;
|
||||
use crate::utils::test_helpers::make_fsentry;
|
||||
#[cfg(feature = "with-containers")]
|
||||
use crate::utils::test_helpers::{create_sample_file_entry, write_file, write_ssh_key};
|
||||
use pretty_assertions::assert_eq;
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_new() {
|
||||
@@ -712,34 +807,196 @@ mod tests {
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_connect() {
|
||||
#[cfg(feature = "with-containers")]
|
||||
fn test_filetransfer_sftp_server() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert_eq!(client.is_connected(), false);
|
||||
// Sample file
|
||||
let (entry, file): (FsFile, tempfile::NamedTempFile) = create_sample_file_entry();
|
||||
// Connect
|
||||
assert!(client
|
||||
.connect(
|
||||
String::from("test.rebex.net"),
|
||||
22,
|
||||
Some(String::from("demo")),
|
||||
String::from("127.0.0.1"),
|
||||
10022,
|
||||
Some(String::from("sftp")),
|
||||
Some(String::from("password"))
|
||||
)
|
||||
.is_ok());
|
||||
// Check session and sftp
|
||||
assert!(client.session.is_some());
|
||||
assert!(client.sftp.is_some());
|
||||
assert_eq!(client.wrkdir, PathBuf::from("/"));
|
||||
assert_eq!(client.wrkdir, PathBuf::from("/config"));
|
||||
assert_eq!(client.is_connected(), true);
|
||||
// Pwd
|
||||
assert_eq!(client.wrkdir.clone(), client.pwd().ok().unwrap());
|
||||
// Stat
|
||||
let stat: FsFile = client
|
||||
.stat(PathBuf::from("/config/sshd.pid").as_path())
|
||||
.ok()
|
||||
.unwrap()
|
||||
.unwrap_file();
|
||||
assert_eq!(stat.name.as_str(), "sshd.pid");
|
||||
let stat: FsDirectory = client
|
||||
.stat(PathBuf::from("/config").as_path())
|
||||
.ok()
|
||||
.unwrap()
|
||||
.unwrap_dir();
|
||||
assert_eq!(stat.name.as_str(), "config");
|
||||
// Stat (err)
|
||||
assert!(client
|
||||
.stat(PathBuf::from("/config/5t0ca220.log").as_path())
|
||||
.is_err());
|
||||
// List dir (dir has 4 (one is hidden :D) entries)
|
||||
assert!(client.list_dir(&Path::new("/config")).unwrap().len() >= 4);
|
||||
// Make directory
|
||||
assert!(client.mkdir(PathBuf::from("/tmp/omar").as_path()).is_ok());
|
||||
// Remake directory (should report already exists)
|
||||
assert_eq!(
|
||||
client
|
||||
.mkdir(PathBuf::from("/tmp/omar").as_path())
|
||||
.err()
|
||||
.unwrap()
|
||||
.kind(),
|
||||
FileTransferErrorType::DirectoryAlreadyExists
|
||||
);
|
||||
// Make directory (err)
|
||||
assert!(client
|
||||
.mkdir(PathBuf::from("/root/aaaaa/pommlar").as_path())
|
||||
.is_err());
|
||||
// Change directory
|
||||
assert!(client
|
||||
.change_dir(PathBuf::from("/tmp/omar").as_path())
|
||||
.is_ok());
|
||||
// Change directory (err)
|
||||
assert!(client
|
||||
.change_dir(PathBuf::from("/tmp/oooo/aaaa/eee").as_path())
|
||||
.is_err());
|
||||
// Copy (not supported)
|
||||
assert!(client
|
||||
.copy(&FsEntry::File(entry.clone()), PathBuf::from("/").as_path())
|
||||
.is_err());
|
||||
// Exec
|
||||
assert_eq!(client.exec("echo 5").ok().unwrap().as_str(), "5\n");
|
||||
// Upload 2 files
|
||||
let mut writable = client
|
||||
.send_file(&entry, PathBuf::from("omar.txt").as_path())
|
||||
.ok()
|
||||
.unwrap();
|
||||
write_file(&file, &mut writable);
|
||||
assert!(client.on_sent(writable).is_ok());
|
||||
let mut writable = client
|
||||
.send_file(&entry, PathBuf::from("README.md").as_path())
|
||||
.ok()
|
||||
.unwrap();
|
||||
write_file(&file, &mut writable);
|
||||
assert!(client.on_sent(writable).is_ok());
|
||||
// Upload file (err)
|
||||
assert!(client
|
||||
.send_file(&entry, PathBuf::from("/ommlar/omarone").as_path())
|
||||
.is_err());
|
||||
// List dir
|
||||
let list: Vec<FsEntry> = client
|
||||
.list_dir(PathBuf::from("/tmp/omar").as_path())
|
||||
.ok()
|
||||
.unwrap();
|
||||
assert_eq!(list.len(), 2);
|
||||
// Find
|
||||
assert_eq!(client.find("*.txt").ok().unwrap().len(), 1);
|
||||
assert_eq!(client.find("*.md").ok().unwrap().len(), 1);
|
||||
assert_eq!(client.find("*.jpeg").ok().unwrap().len(), 0);
|
||||
// Rename
|
||||
assert!(client
|
||||
.mkdir(PathBuf::from("/tmp/uploads").as_path())
|
||||
.is_ok());
|
||||
assert!(client
|
||||
.rename(
|
||||
list.get(0).unwrap(),
|
||||
PathBuf::from("/tmp/uploads/README.txt").as_path()
|
||||
)
|
||||
.is_ok());
|
||||
// Rename (err)
|
||||
assert!(client
|
||||
.rename(list.get(0).unwrap(), PathBuf::from("OMARONE").as_path())
|
||||
.is_err());
|
||||
let dummy: FsEntry = FsEntry::File(FsFile {
|
||||
name: String::from("cucumber.txt"),
|
||||
abs_path: PathBuf::from("/cucumber.txt"),
|
||||
last_change_time: SystemTime::UNIX_EPOCH,
|
||||
last_access_time: SystemTime::UNIX_EPOCH,
|
||||
creation_time: SystemTime::UNIX_EPOCH,
|
||||
size: 0,
|
||||
ftype: Some(String::from("txt")), // File type
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
});
|
||||
assert!(client
|
||||
.rename(&dummy, PathBuf::from("/a/b/c").as_path())
|
||||
.is_err());
|
||||
// Remove
|
||||
assert!(client.remove(list.get(1).unwrap()).is_ok());
|
||||
assert!(client.remove(list.get(1).unwrap()).is_err());
|
||||
// Receive file
|
||||
let mut writable = client
|
||||
.send_file(&entry, PathBuf::from("/tmp/uploads/README.txt").as_path())
|
||||
.ok()
|
||||
.unwrap();
|
||||
write_file(&file, &mut writable);
|
||||
assert!(client.on_sent(writable).is_ok());
|
||||
let file: FsFile = client
|
||||
.list_dir(PathBuf::from("/tmp/uploads").as_path())
|
||||
.ok()
|
||||
.unwrap()
|
||||
.get(0)
|
||||
.unwrap()
|
||||
.clone()
|
||||
.unwrap_file();
|
||||
let mut readable = client.recv_file(&file).ok().unwrap();
|
||||
let mut data: Vec<u8> = vec![0; 1024];
|
||||
assert!(readable.read(&mut data).is_ok());
|
||||
assert!(client.on_recv(readable).is_ok());
|
||||
// Receive file (err)
|
||||
assert!(client.recv_file(&entry).is_err());
|
||||
// Cleanup
|
||||
assert!(client.change_dir(PathBuf::from("/").as_path()).is_ok());
|
||||
assert!(client
|
||||
.remove(&make_fsentry(PathBuf::from("/tmp/omar"), true))
|
||||
.is_ok());
|
||||
assert!(client
|
||||
.remove(&make_fsentry(PathBuf::from("/tmp/uploads"), true))
|
||||
.is_ok());
|
||||
// Disconnect
|
||||
assert!(client.disconnect().is_ok());
|
||||
assert_eq!(client.is_connected(), false);
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(feature = "with-containers")]
|
||||
fn test_filetransfer_sftp_ssh_storage() {
|
||||
let mut storage: SshKeyStorage = SshKeyStorage::empty();
|
||||
let key_file: tempfile::NamedTempFile = write_ssh_key();
|
||||
storage.add_key("127.0.0.1", "sftp", key_file.path().to_path_buf());
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(storage);
|
||||
// Connect
|
||||
assert!(client
|
||||
.connect(
|
||||
String::from("127.0.0.1"),
|
||||
10022,
|
||||
Some(String::from("sftp")),
|
||||
None,
|
||||
)
|
||||
.is_ok());
|
||||
assert_eq!(client.is_connected(), true);
|
||||
assert!(client.disconnect().is_ok());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_bad_auth() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert!(client
|
||||
.connect(
|
||||
String::from("test.rebex.net"),
|
||||
22,
|
||||
String::from("127.0.0.1"),
|
||||
10022,
|
||||
Some(String::from("demo")),
|
||||
Some(String::from("badpassword"))
|
||||
)
|
||||
@@ -747,13 +1004,52 @@ mod tests {
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(feature = "with-containers")]
|
||||
fn test_filetransfer_sftp_no_credentials() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert!(client
|
||||
.connect(String::from("test.rebex.net"), 22, None, None)
|
||||
.connect(String::from("127.0.0.1"), 10022, None, None)
|
||||
.is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(feature = "with-containers")]
|
||||
fn test_filetransfer_sftp_get_remote_path() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
// Connect
|
||||
assert!(client
|
||||
.connect(
|
||||
String::from("127.0.0.1"),
|
||||
10022,
|
||||
Some(String::from("sftp")),
|
||||
Some(String::from("password"))
|
||||
)
|
||||
.is_ok());
|
||||
// get realpath
|
||||
assert!(client
|
||||
.change_dir(PathBuf::from("/config").as_path())
|
||||
.is_ok());
|
||||
assert_eq!(
|
||||
client
|
||||
.get_remote_path(PathBuf::from("sshd.pid").as_path())
|
||||
.ok()
|
||||
.unwrap(),
|
||||
PathBuf::from("/config/sshd.pid")
|
||||
);
|
||||
// No such file
|
||||
assert!(client
|
||||
.get_remote_path(PathBuf::from("omarone.txt").as_path())
|
||||
.is_err());
|
||||
// Ok abs path
|
||||
assert_eq!(
|
||||
client
|
||||
.get_remote_path(PathBuf::from("/config/sshd.pid").as_path())
|
||||
.ok()
|
||||
.unwrap(),
|
||||
PathBuf::from("/config/sshd.pid")
|
||||
);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_bad_server() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
@@ -767,302 +1063,6 @@ mod tests {
|
||||
.is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_pwd() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert!(client
|
||||
.connect(
|
||||
String::from("test.rebex.net"),
|
||||
22,
|
||||
Some(String::from("demo")),
|
||||
Some(String::from("password"))
|
||||
)
|
||||
.is_ok());
|
||||
// Check session and sftp
|
||||
assert!(client.session.is_some());
|
||||
assert!(client.sftp.is_some());
|
||||
assert_eq!(client.wrkdir, PathBuf::from("/"));
|
||||
// Pwd
|
||||
assert_eq!(client.wrkdir.clone(), client.pwd().ok().unwrap());
|
||||
// Disconnect
|
||||
assert!(client.disconnect().is_ok());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_cwd() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert!(client
|
||||
.connect(
|
||||
String::from("test.rebex.net"),
|
||||
22,
|
||||
Some(String::from("demo")),
|
||||
Some(String::from("password"))
|
||||
)
|
||||
.is_ok());
|
||||
// Check session and sftp
|
||||
assert!(client.session.is_some());
|
||||
assert!(client.sftp.is_some());
|
||||
assert_eq!(client.wrkdir, PathBuf::from("/"));
|
||||
// Pwd
|
||||
assert_eq!(client.wrkdir.clone(), client.pwd().ok().unwrap());
|
||||
// Cwd (relative)
|
||||
assert!(client.change_dir(PathBuf::from("pub/").as_path()).is_ok());
|
||||
assert_eq!(client.wrkdir, PathBuf::from("/pub"));
|
||||
// Cwd (absolute)
|
||||
assert!(client.change_dir(PathBuf::from("/").as_path()).is_ok());
|
||||
assert_eq!(client.wrkdir, PathBuf::from("/"));
|
||||
// Disconnect
|
||||
assert!(client.disconnect().is_ok());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_copy() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert!(client
|
||||
.connect(
|
||||
String::from("test.rebex.net"),
|
||||
22,
|
||||
Some(String::from("demo")),
|
||||
Some(String::from("password"))
|
||||
)
|
||||
.is_ok());
|
||||
// Check session and sftp
|
||||
assert!(client.session.is_some());
|
||||
assert!(client.sftp.is_some());
|
||||
assert_eq!(client.wrkdir, PathBuf::from("/"));
|
||||
// Copy
|
||||
let file: FsFile = FsFile {
|
||||
name: String::from("readme.txt"),
|
||||
abs_path: PathBuf::from("/readme.txt"),
|
||||
last_change_time: SystemTime::UNIX_EPOCH,
|
||||
last_access_time: SystemTime::UNIX_EPOCH,
|
||||
creation_time: SystemTime::UNIX_EPOCH,
|
||||
size: 0,
|
||||
ftype: Some(String::from("txt")), // File type
|
||||
readonly: true,
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
};
|
||||
assert!(client
|
||||
.copy(&FsEntry::File(file), &Path::new("/tmp/dest.txt"))
|
||||
.is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_cwd_error() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert!(client
|
||||
.connect(
|
||||
String::from("test.rebex.net"),
|
||||
22,
|
||||
Some(String::from("demo")),
|
||||
Some(String::from("password"))
|
||||
)
|
||||
.is_ok());
|
||||
// Cwd (abs)
|
||||
assert!(client
|
||||
.change_dir(PathBuf::from("/omar/gabber").as_path())
|
||||
.is_err());
|
||||
// Cwd (rel)
|
||||
assert!(client
|
||||
.change_dir(PathBuf::from("gomar/pett").as_path())
|
||||
.is_err());
|
||||
// Disconnect
|
||||
assert!(client.disconnect().is_ok());
|
||||
assert!(client
|
||||
.change_dir(PathBuf::from("gomar/pett").as_path())
|
||||
.is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_ls() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert!(client
|
||||
.connect(
|
||||
String::from("test.rebex.net"),
|
||||
22,
|
||||
Some(String::from("demo")),
|
||||
Some(String::from("password"))
|
||||
)
|
||||
.is_ok());
|
||||
// Check session and sftp
|
||||
assert!(client.session.is_some());
|
||||
assert!(client.sftp.is_some());
|
||||
assert_eq!(client.wrkdir, PathBuf::from("/"));
|
||||
// List dir
|
||||
let pwd: PathBuf = client.pwd().ok().unwrap();
|
||||
let files: Vec<FsEntry> = client.list_dir(pwd.as_path()).ok().unwrap();
|
||||
assert_eq!(files.len(), 3); // There are 3 files
|
||||
// Disconnect
|
||||
assert!(client.disconnect().is_ok());
|
||||
// Verify err
|
||||
assert!(client.list_dir(pwd.as_path()).is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_stat() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert!(client
|
||||
.connect(
|
||||
String::from("test.rebex.net"),
|
||||
22,
|
||||
Some(String::from("demo")),
|
||||
Some(String::from("password"))
|
||||
)
|
||||
.is_ok());
|
||||
// Check session and sftp
|
||||
assert!(client.session.is_some());
|
||||
assert!(client.sftp.is_some());
|
||||
assert_eq!(client.wrkdir, PathBuf::from("/"));
|
||||
let file: FsEntry = client
|
||||
.stat(PathBuf::from("readme.txt").as_path())
|
||||
.ok()
|
||||
.unwrap();
|
||||
if let FsEntry::File(file) = file {
|
||||
assert_eq!(file.abs_path, PathBuf::from("/readme.txt"));
|
||||
} else {
|
||||
panic!("Expected readme.txt to be a file");
|
||||
}
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_exec() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert!(client
|
||||
.connect(
|
||||
String::from("test.rebex.net"),
|
||||
22,
|
||||
Some(String::from("demo")),
|
||||
Some(String::from("password"))
|
||||
)
|
||||
.is_ok());
|
||||
// Check session and scp
|
||||
assert!(client.session.is_some());
|
||||
// Exec
|
||||
assert_eq!(client.exec("echo 5").ok().unwrap().as_str(), "5\n");
|
||||
// Disconnect
|
||||
assert!(client.disconnect().is_ok());
|
||||
// Verify err
|
||||
assert!(client.exec("echo 1").is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_find() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert!(client
|
||||
.connect(
|
||||
String::from("test.rebex.net"),
|
||||
22,
|
||||
Some(String::from("demo")),
|
||||
Some(String::from("password"))
|
||||
)
|
||||
.is_ok());
|
||||
// Check session and scp
|
||||
assert!(client.session.is_some());
|
||||
// Search for file (let's search for pop3-*.png); there should be 2
|
||||
let search_res: Vec<FsEntry> = client.find("pop3-*.png").ok().unwrap();
|
||||
assert_eq!(search_res.len(), 2);
|
||||
// verify names
|
||||
assert_eq!(search_res[0].get_name(), "pop3-browser.png");
|
||||
assert_eq!(search_res[1].get_name(), "pop3-console-client.png");
|
||||
// Search directory
|
||||
let search_res: Vec<FsEntry> = client.find("pub").ok().unwrap();
|
||||
assert_eq!(search_res.len(), 1);
|
||||
// Disconnect
|
||||
assert!(client.disconnect().is_ok());
|
||||
// Verify err
|
||||
assert!(client.find("pippo").is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_recv() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert!(client
|
||||
.connect(
|
||||
String::from("test.rebex.net"),
|
||||
22,
|
||||
Some(String::from("demo")),
|
||||
Some(String::from("password"))
|
||||
)
|
||||
.is_ok());
|
||||
// Check session and sftp
|
||||
assert!(client.session.is_some());
|
||||
assert!(client.sftp.is_some());
|
||||
assert_eq!(client.wrkdir, PathBuf::from("/"));
|
||||
let file: FsFile = FsFile {
|
||||
name: String::from("readme.txt"),
|
||||
abs_path: PathBuf::from("/readme.txt"),
|
||||
last_change_time: SystemTime::UNIX_EPOCH,
|
||||
last_access_time: SystemTime::UNIX_EPOCH,
|
||||
creation_time: SystemTime::UNIX_EPOCH,
|
||||
size: 0,
|
||||
ftype: Some(String::from("txt")), // File type
|
||||
readonly: true,
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
};
|
||||
// Receive file
|
||||
assert!(client.recv_file(&file).is_ok());
|
||||
// Disconnect
|
||||
assert!(client.disconnect().is_ok());
|
||||
}
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_recv_failed_nosuchfile() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert!(client
|
||||
.connect(
|
||||
String::from("test.rebex.net"),
|
||||
22,
|
||||
Some(String::from("demo")),
|
||||
Some(String::from("password"))
|
||||
)
|
||||
.is_ok());
|
||||
// Check session and sftp
|
||||
assert!(client.session.is_some());
|
||||
assert!(client.sftp.is_some());
|
||||
assert_eq!(client.wrkdir, PathBuf::from("/"));
|
||||
// Receive file
|
||||
let file: FsFile = FsFile {
|
||||
name: String::from("omar.txt"),
|
||||
abs_path: PathBuf::from("/omar.txt"),
|
||||
last_change_time: SystemTime::UNIX_EPOCH,
|
||||
last_access_time: SystemTime::UNIX_EPOCH,
|
||||
creation_time: SystemTime::UNIX_EPOCH,
|
||||
size: 0,
|
||||
ftype: Some(String::from("txt")), // File type
|
||||
readonly: true,
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
};
|
||||
assert!(client.recv_file(&file).is_err());
|
||||
// Disconnect
|
||||
assert!(client.disconnect().is_ok());
|
||||
}
|
||||
|
||||
// NOTE: other functions doesn't work with this test SFTP server
|
||||
|
||||
/* NOTE: the server doesn't allow you to create directories
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_mkdir() {
|
||||
let mut client: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert!(client.connect(String::from("test.rebex.net"), 22, Some(String::from("demo")), Some(String::from("password"))).is_ok());
|
||||
let dir: String = String::from("foo");
|
||||
// Mkdir
|
||||
assert!(client.mkdir(dir).is_ok());
|
||||
// cwd
|
||||
assert!(client.change_dir(PathBuf::from("foo/").as_path()).is_ok());
|
||||
assert_eq!(client.wrkdir, PathBuf::from("/foo"));
|
||||
// Disconnect
|
||||
assert!(client.disconnect().is_ok());
|
||||
}
|
||||
*/
|
||||
|
||||
#[test]
|
||||
fn test_filetransfer_sftp_uninitialized() {
|
||||
let file: FsFile = FsFile {
|
||||
@@ -1073,18 +1073,33 @@ mod tests {
|
||||
creation_time: SystemTime::UNIX_EPOCH,
|
||||
size: 0,
|
||||
ftype: Some(String::from("txt")), // File type
|
||||
readonly: true,
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
};
|
||||
let mut sftp: SftpFileTransfer = SftpFileTransfer::new(SshKeyStorage::empty());
|
||||
assert!(sftp.change_dir(Path::new("/tmp")).is_err());
|
||||
assert!(sftp
|
||||
.copy(
|
||||
&make_fsentry(PathBuf::from("/nowhere"), false),
|
||||
PathBuf::from("/culonia").as_path()
|
||||
)
|
||||
.is_err());
|
||||
assert!(sftp.exec("echo 5").is_err());
|
||||
assert!(sftp.disconnect().is_err());
|
||||
assert!(sftp.list_dir(Path::new("/tmp")).is_err());
|
||||
assert!(sftp.mkdir(Path::new("/tmp")).is_err());
|
||||
assert!(sftp.pwd().is_err());
|
||||
assert!(sftp
|
||||
.remove(&make_fsentry(PathBuf::from("/nowhere"), false))
|
||||
.is_err());
|
||||
assert!(sftp
|
||||
.rename(
|
||||
&make_fsentry(PathBuf::from("/nowhere"), false),
|
||||
PathBuf::from("/culonia").as_path()
|
||||
)
|
||||
.is_err());
|
||||
assert!(sftp.stat(Path::new("/tmp")).is_err());
|
||||
assert!(sftp.recv_file(&file).is_err());
|
||||
assert!(sftp.send_file(&file, Path::new("/tmp/omar.txt")).is_err());
|
||||
|
||||
@@ -117,12 +117,14 @@ mod tests {
|
||||
|
||||
use super::*;
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
|
||||
#[test]
|
||||
fn test_fs_explorer_builder_new_default() {
|
||||
let explorer: FileExplorer = FileExplorerBuilder::new().build();
|
||||
// Verify
|
||||
assert!(!explorer.opts.intersects(ExplorerOpts::SHOW_HIDDEN_FILES));
|
||||
assert_eq!(explorer.file_sorting, FileSorting::ByName); // Default
|
||||
assert_eq!(explorer.file_sorting, FileSorting::Name); // Default
|
||||
assert_eq!(explorer.group_dirs, None);
|
||||
assert_eq!(explorer.stack_size, 16);
|
||||
}
|
||||
@@ -130,7 +132,7 @@ mod tests {
|
||||
#[test]
|
||||
fn test_fs_explorer_builder_new_all() {
|
||||
let explorer: FileExplorer = FileExplorerBuilder::new()
|
||||
.with_file_sorting(FileSorting::ByModifyTime)
|
||||
.with_file_sorting(FileSorting::ModifyTime)
|
||||
.with_group_dirs(Some(GroupDirs::First))
|
||||
.with_hidden_files(true)
|
||||
.with_stack_size(24)
|
||||
@@ -138,7 +140,7 @@ mod tests {
|
||||
.build();
|
||||
// Verify
|
||||
assert!(explorer.opts.intersects(ExplorerOpts::SHOW_HIDDEN_FILES));
|
||||
assert_eq!(explorer.file_sorting, FileSorting::ByModifyTime); // Default
|
||||
assert_eq!(explorer.file_sorting, FileSorting::ModifyTime); // Default
|
||||
assert_eq!(explorer.group_dirs, Some(GroupDirs::First));
|
||||
assert_eq!(explorer.stack_size, 24);
|
||||
}
|
||||
|
||||
@@ -25,18 +25,13 @@
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// Deps
|
||||
extern crate bytesize;
|
||||
extern crate regex;
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
extern crate users;
|
||||
// Locals
|
||||
use super::FsEntry;
|
||||
use crate::utils::fmt::{fmt_path_elide, fmt_pex, fmt_time};
|
||||
// Ext
|
||||
use bytesize::ByteSize;
|
||||
use regex::Regex;
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
use users::{get_group_by_gid, get_user_by_uid};
|
||||
// Types
|
||||
// FmtCallback: Formatter, fsentry: &FsEntry, cur_str, prefix, length, extra
|
||||
@@ -251,7 +246,7 @@ impl Formatter {
|
||||
_fmt_extra: Option<&String>,
|
||||
) -> String {
|
||||
// Get username
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
let group: String = match fsentry.get_group() {
|
||||
Some(gid) => match get_group_by_gid(gid) {
|
||||
Some(user) => user.name().to_string_lossy().to_string(),
|
||||
@@ -321,13 +316,13 @@ impl Formatter {
|
||||
};
|
||||
let name: &str = fsentry.get_name();
|
||||
let last_idx: usize = match fsentry.is_dir() {
|
||||
// NOTE: For directories is 19, since we push '/' to name
|
||||
true => file_len - 5,
|
||||
false => file_len - 4,
|
||||
// NOTE: For directories is l - 2, since we push '/' to name
|
||||
true => file_len - 2,
|
||||
false => file_len - 1,
|
||||
};
|
||||
let mut name: String = match name.len() >= file_len {
|
||||
false => name.to_string(),
|
||||
true => format!("{}...", &name[0..last_idx]),
|
||||
true => format!("{}…", &name[0..last_idx]),
|
||||
};
|
||||
if fsentry.is_dir() {
|
||||
name.push('/');
|
||||
@@ -359,7 +354,9 @@ impl Formatter {
|
||||
pex.push(file_type);
|
||||
match fsentry.get_unix_pex() {
|
||||
None => pex.push_str("?????????"),
|
||||
Some((owner, group, others)) => pex.push_str(fmt_pex(owner, group, others).as_str()),
|
||||
Some((owner, group, others)) => pex.push_str(
|
||||
format!("{}{}{}", fmt_pex(owner), fmt_pex(group), fmt_pex(others)).as_str(),
|
||||
),
|
||||
}
|
||||
// Add to cur str, prefix and the key value
|
||||
format!("{}{}{:10}", cur_str, prefix, pex)
|
||||
@@ -431,7 +428,7 @@ impl Formatter {
|
||||
_fmt_extra: Option<&String>,
|
||||
) -> String {
|
||||
// Get username
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
let username: String = match fsentry.get_user() {
|
||||
Some(uid) => match get_user_by_uid(uid) {
|
||||
Some(user) => user.name().to_string_lossy().to_string(),
|
||||
@@ -538,7 +535,9 @@ impl Formatter {
|
||||
mod tests {
|
||||
|
||||
use super::*;
|
||||
use crate::fs::{FsDirectory, FsFile};
|
||||
use crate::fs::{FsDirectory, FsFile, UnixPex};
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
use std::path::PathBuf;
|
||||
use std::time::SystemTime;
|
||||
|
||||
@@ -555,12 +554,11 @@ mod tests {
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
size: 8192,
|
||||
readonly: false,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
});
|
||||
let prefix: String = String::from("h");
|
||||
let mut callchain: CallChainBlock = CallChainBlock::new(dummy_fmt, prefix, None, None);
|
||||
@@ -596,14 +594,13 @@ mod tests {
|
||||
last_access_time: t,
|
||||
creation_time: t,
|
||||
size: 8192,
|
||||
readonly: false,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
});
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
assert_eq!(
|
||||
formatter.fmt(&entry),
|
||||
format!(
|
||||
@@ -627,18 +624,17 @@ mod tests {
|
||||
last_access_time: t,
|
||||
creation_time: t,
|
||||
size: 8192,
|
||||
readonly: false,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
});
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
assert_eq!(
|
||||
formatter.fmt(&entry),
|
||||
format!(
|
||||
"piroparoporoperoperu... -rw-r--r-- root 8.2 KB {}",
|
||||
"piroparoporoperoperupup… -rw-r--r-- root 8.2 KB {}",
|
||||
fmt_time(t, "%b %d %Y %H:%M")
|
||||
)
|
||||
);
|
||||
@@ -646,7 +642,7 @@ mod tests {
|
||||
assert_eq!(
|
||||
formatter.fmt(&entry),
|
||||
format!(
|
||||
"piroparoporoperoperu... -rw-r--r-- 0 8.2 KB {}",
|
||||
"piroparoporoperoperupup… -rw-r--r-- 0 8.2 KB {}",
|
||||
fmt_time(t, "%b %d %Y %H:%M")
|
||||
)
|
||||
);
|
||||
@@ -658,14 +654,13 @@ mod tests {
|
||||
last_access_time: t,
|
||||
creation_time: t,
|
||||
size: 8192,
|
||||
readonly: false,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: None, // UNIX only
|
||||
});
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
assert_eq!(
|
||||
formatter.fmt(&entry),
|
||||
format!(
|
||||
@@ -689,14 +684,13 @@ mod tests {
|
||||
last_access_time: t,
|
||||
creation_time: t,
|
||||
size: 8192,
|
||||
readonly: false,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: None, // UNIX only
|
||||
user: None, // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: None, // UNIX only
|
||||
});
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
assert_eq!(
|
||||
formatter.fmt(&entry),
|
||||
format!(
|
||||
@@ -726,13 +720,12 @@ mod tests {
|
||||
last_change_time: t_now,
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
readonly: false,
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((7, 5, 5)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(7), UnixPex::from(5), UnixPex::from(5))), // UNIX only
|
||||
});
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
assert_eq!(
|
||||
formatter.fmt(&entry),
|
||||
format!(
|
||||
@@ -755,13 +748,12 @@ mod tests {
|
||||
last_change_time: t_now,
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
readonly: false,
|
||||
symlink: None, // UNIX only
|
||||
user: None, // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: None, // UNIX only
|
||||
});
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
assert_eq!(
|
||||
formatter.fmt(&entry),
|
||||
format!(
|
||||
@@ -792,7 +784,6 @@ mod tests {
|
||||
last_access_time: t,
|
||||
creation_time: t,
|
||||
size: 8192,
|
||||
readonly: false,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: None, // UNIX only
|
||||
user: None, // UNIX only
|
||||
@@ -805,11 +796,10 @@ mod tests {
|
||||
last_change_time: t,
|
||||
last_access_time: t,
|
||||
creation_time: t,
|
||||
readonly: false,
|
||||
symlink: Some(Box::new(pointer)), // UNIX only
|
||||
user: None, // UNIX only
|
||||
group: None, // UNIX only
|
||||
unix_pex: Some((7, 5, 5)), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(7), UnixPex::from(5), UnixPex::from(5))), // UNIX only
|
||||
});
|
||||
assert_eq!(formatter.fmt(&entry), format!(
|
||||
"projects/ -> project.info 0 0 lrwxr-xr-x {} {} {}",
|
||||
@@ -824,11 +814,10 @@ mod tests {
|
||||
last_change_time: t,
|
||||
last_access_time: t,
|
||||
creation_time: t,
|
||||
readonly: false,
|
||||
symlink: None, // UNIX only
|
||||
user: None, // UNIX only
|
||||
group: None, // UNIX only
|
||||
unix_pex: Some((7, 5, 5)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: None, // UNIX only
|
||||
group: None, // UNIX only
|
||||
unix_pex: Some((UnixPex::from(7), UnixPex::from(5), UnixPex::from(5))), // UNIX only
|
||||
});
|
||||
assert_eq!(formatter.fmt(&entry), format!(
|
||||
"projects/ 0 0 drwxr-xr-x {} {} {}",
|
||||
@@ -844,7 +833,6 @@ mod tests {
|
||||
last_access_time: t,
|
||||
creation_time: t,
|
||||
size: 8192,
|
||||
readonly: false,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: None, // UNIX only
|
||||
user: None, // UNIX only
|
||||
@@ -858,12 +846,11 @@ mod tests {
|
||||
last_access_time: t,
|
||||
creation_time: t,
|
||||
size: 8192,
|
||||
readonly: false,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: Some(Box::new(pointer)), // UNIX only
|
||||
user: None, // UNIX only
|
||||
group: None, // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
});
|
||||
assert_eq!(formatter.fmt(&entry), format!(
|
||||
"bar.txt -> project.info 0 0 lrw-r--r-- 8.2 KB {} {} {}",
|
||||
@@ -879,12 +866,11 @@ mod tests {
|
||||
last_access_time: t,
|
||||
creation_time: t,
|
||||
size: 8192,
|
||||
readonly: false,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: None, // UNIX only
|
||||
user: None, // UNIX only
|
||||
group: None, // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: None, // UNIX only
|
||||
group: None, // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
});
|
||||
assert_eq!(formatter.fmt(&entry), format!(
|
||||
"bar.txt 0 0 -rw-r--r-- 8.2 KB {} {} {}",
|
||||
|
||||
@@ -28,8 +28,6 @@
|
||||
// Mods
|
||||
pub(crate) mod builder;
|
||||
mod formatter;
|
||||
// Deps
|
||||
extern crate bitflags;
|
||||
// Locals
|
||||
use super::FsEntry;
|
||||
use formatter::Formatter;
|
||||
@@ -54,10 +52,10 @@ bitflags! {
|
||||
/// FileSorting defines the criteria for sorting files
|
||||
#[derive(Copy, Clone, PartialEq, std::fmt::Debug)]
|
||||
pub enum FileSorting {
|
||||
ByName,
|
||||
ByModifyTime,
|
||||
ByCreationTime,
|
||||
BySize,
|
||||
Name,
|
||||
ModifyTime,
|
||||
CreationTime,
|
||||
Size,
|
||||
}
|
||||
|
||||
/// ## GroupDirs
|
||||
@@ -89,7 +87,7 @@ impl Default for FileExplorer {
|
||||
wrkdir: PathBuf::from("/"),
|
||||
dirstack: VecDeque::with_capacity(16),
|
||||
stack_size: 16,
|
||||
file_sorting: FileSorting::ByName,
|
||||
file_sorting: FileSorting::Name,
|
||||
group_dirs: None,
|
||||
opts: ExplorerOpts::empty(),
|
||||
fmt: Formatter::default(),
|
||||
@@ -239,10 +237,10 @@ impl FileExplorer {
|
||||
fn sort(&mut self) {
|
||||
// Choose sorting method
|
||||
match &self.file_sorting {
|
||||
FileSorting::ByName => self.sort_files_by_name(),
|
||||
FileSorting::ByCreationTime => self.sort_files_by_creation_time(),
|
||||
FileSorting::ByModifyTime => self.sort_files_by_mtime(),
|
||||
FileSorting::BySize => self.sort_files_by_size(),
|
||||
FileSorting::Name => self.sort_files_by_name(),
|
||||
FileSorting::CreationTime => self.sort_files_by_creation_time(),
|
||||
FileSorting::ModifyTime => self.sort_files_by_mtime(),
|
||||
FileSorting::Size => self.sort_files_by_size(),
|
||||
}
|
||||
// Directories first (NOTE: MUST COME AFTER OTHER SORTING)
|
||||
// Group directories if necessary
|
||||
@@ -306,6 +304,13 @@ impl FileExplorer {
|
||||
pub fn toggle_hidden_files(&mut self) {
|
||||
self.opts.toggle(ExplorerOpts::SHOW_HIDDEN_FILES);
|
||||
}
|
||||
|
||||
/// ### hidden_files_visible
|
||||
///
|
||||
/// Returns whether hidden files are visible
|
||||
pub fn hidden_files_visible(&self) -> bool {
|
||||
self.opts.intersects(ExplorerOpts::SHOW_HIDDEN_FILES)
|
||||
}
|
||||
}
|
||||
|
||||
// Traits
|
||||
@@ -313,10 +318,10 @@ impl FileExplorer {
|
||||
impl ToString for FileSorting {
|
||||
fn to_string(&self) -> String {
|
||||
String::from(match self {
|
||||
FileSorting::ByCreationTime => "by_creation_time",
|
||||
FileSorting::ByModifyTime => "by_mtime",
|
||||
FileSorting::ByName => "by_name",
|
||||
FileSorting::BySize => "by_size",
|
||||
FileSorting::CreationTime => "by_creation_time",
|
||||
FileSorting::ModifyTime => "by_mtime",
|
||||
FileSorting::Name => "by_name",
|
||||
FileSorting::Size => "by_size",
|
||||
})
|
||||
}
|
||||
}
|
||||
@@ -325,10 +330,10 @@ impl FromStr for FileSorting {
|
||||
type Err = ();
|
||||
fn from_str(s: &str) -> Result<Self, Self::Err> {
|
||||
match s.to_ascii_lowercase().as_str() {
|
||||
"by_creation_time" => Ok(FileSorting::ByCreationTime),
|
||||
"by_mtime" => Ok(FileSorting::ByModifyTime),
|
||||
"by_name" => Ok(FileSorting::ByName),
|
||||
"by_size" => Ok(FileSorting::BySize),
|
||||
"by_creation_time" => Ok(FileSorting::CreationTime),
|
||||
"by_mtime" => Ok(FileSorting::ModifyTime),
|
||||
"by_name" => Ok(FileSorting::Name),
|
||||
"by_size" => Ok(FileSorting::Size),
|
||||
_ => Err(()),
|
||||
}
|
||||
}
|
||||
@@ -358,9 +363,10 @@ impl FromStr for GroupDirs {
|
||||
mod tests {
|
||||
|
||||
use super::*;
|
||||
use crate::fs::{FsDirectory, FsFile};
|
||||
use crate::fs::{FsDirectory, FsFile, UnixPex};
|
||||
use crate::utils::fmt::fmt_time;
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
use std::thread::sleep;
|
||||
use std::time::{Duration, SystemTime};
|
||||
|
||||
@@ -374,8 +380,8 @@ mod tests {
|
||||
assert_eq!(explorer.wrkdir, PathBuf::from("/"));
|
||||
assert_eq!(explorer.stack_size, 16);
|
||||
assert_eq!(explorer.group_dirs, None);
|
||||
assert_eq!(explorer.file_sorting, FileSorting::ByName);
|
||||
assert_eq!(explorer.get_file_sorting(), FileSorting::ByName);
|
||||
assert_eq!(explorer.file_sorting, FileSorting::Name);
|
||||
assert_eq!(explorer.get_file_sorting(), FileSorting::Name);
|
||||
}
|
||||
|
||||
#[test]
|
||||
@@ -410,6 +416,7 @@ mod tests {
|
||||
let mut explorer: FileExplorer = FileExplorer::default();
|
||||
// Don't show hidden files
|
||||
explorer.opts.remove(ExplorerOpts::SHOW_HIDDEN_FILES);
|
||||
assert_eq!(explorer.hidden_files_visible(), false);
|
||||
// Create files
|
||||
explorer.set_files(vec![
|
||||
make_fs_entry("README.md", false),
|
||||
@@ -433,6 +440,7 @@ mod tests {
|
||||
assert_eq!(explorer.iter_files().count(), 4);
|
||||
// Toggle hidden
|
||||
explorer.toggle_hidden_files();
|
||||
assert_eq!(explorer.hidden_files_visible(), true);
|
||||
assert_eq!(explorer.iter_files().count(), 6); // All files are returned now
|
||||
}
|
||||
|
||||
@@ -451,7 +459,7 @@ mod tests {
|
||||
make_fs_entry("Cargo.lock", false),
|
||||
make_fs_entry("codecov.yml", false),
|
||||
]);
|
||||
explorer.sort_by(FileSorting::ByName);
|
||||
explorer.sort_by(FileSorting::Name);
|
||||
// First entry should be "Cargo.lock"
|
||||
assert_eq!(explorer.files.get(0).unwrap().get_name(), "Cargo.lock");
|
||||
// Last should be "src/"
|
||||
@@ -467,7 +475,7 @@ mod tests {
|
||||
let entry2: FsEntry = make_fs_entry("CODE_OF_CONDUCT.md", false);
|
||||
// Create files (files are then sorted by name)
|
||||
explorer.set_files(vec![entry1, entry2]);
|
||||
explorer.sort_by(FileSorting::ByModifyTime);
|
||||
explorer.sort_by(FileSorting::ModifyTime);
|
||||
// First entry should be "CODE_OF_CONDUCT.md"
|
||||
assert_eq!(
|
||||
explorer.files.get(0).unwrap().get_name(),
|
||||
@@ -486,7 +494,7 @@ mod tests {
|
||||
let entry2: FsEntry = make_fs_entry("CODE_OF_CONDUCT.md", false);
|
||||
// Create files (files are then sorted by name)
|
||||
explorer.set_files(vec![entry1, entry2]);
|
||||
explorer.sort_by(FileSorting::ByCreationTime);
|
||||
explorer.sort_by(FileSorting::CreationTime);
|
||||
// First entry should be "CODE_OF_CONDUCT.md"
|
||||
assert_eq!(
|
||||
explorer.files.get(0).unwrap().get_name(),
|
||||
@@ -505,7 +513,7 @@ mod tests {
|
||||
make_fs_entry("src/", true),
|
||||
make_fs_entry_with_size("CONTRIBUTING.md", false, 256),
|
||||
]);
|
||||
explorer.sort_by(FileSorting::BySize);
|
||||
explorer.sort_by(FileSorting::Size);
|
||||
// Directory has size 4096
|
||||
assert_eq!(explorer.files.get(0).unwrap().get_name(), "src/");
|
||||
assert_eq!(explorer.files.get(1).unwrap().get_name(), "README.md");
|
||||
@@ -528,7 +536,7 @@ mod tests {
|
||||
make_fs_entry("Cargo.lock", false),
|
||||
make_fs_entry("codecov.yml", false),
|
||||
]);
|
||||
explorer.sort_by(FileSorting::ByName);
|
||||
explorer.sort_by(FileSorting::Name);
|
||||
explorer.group_dirs_by(Some(GroupDirs::First));
|
||||
// First entry should be "docs"
|
||||
assert_eq!(explorer.files.get(0).unwrap().get_name(), "docs/");
|
||||
@@ -555,7 +563,7 @@ mod tests {
|
||||
make_fs_entry("Cargo.lock", false),
|
||||
make_fs_entry("codecov.yml", false),
|
||||
]);
|
||||
explorer.sort_by(FileSorting::ByName);
|
||||
explorer.sort_by(FileSorting::Name);
|
||||
explorer.group_dirs_by(Some(GroupDirs::Last));
|
||||
// Last entry should be "src"
|
||||
assert_eq!(explorer.files.get(8).unwrap().get_name(), "docs/");
|
||||
@@ -578,14 +586,13 @@ mod tests {
|
||||
last_access_time: t,
|
||||
creation_time: t,
|
||||
size: 8192,
|
||||
readonly: false,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
});
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
assert_eq!(
|
||||
explorer.fmt_file(&entry),
|
||||
format!(
|
||||
@@ -606,25 +613,25 @@ mod tests {
|
||||
#[test]
|
||||
fn test_fs_explorer_to_string_from_str_traits() {
|
||||
// File Sorting
|
||||
assert_eq!(FileSorting::ByCreationTime.to_string(), "by_creation_time");
|
||||
assert_eq!(FileSorting::ByModifyTime.to_string(), "by_mtime");
|
||||
assert_eq!(FileSorting::ByName.to_string(), "by_name");
|
||||
assert_eq!(FileSorting::BySize.to_string(), "by_size");
|
||||
assert_eq!(FileSorting::CreationTime.to_string(), "by_creation_time");
|
||||
assert_eq!(FileSorting::ModifyTime.to_string(), "by_mtime");
|
||||
assert_eq!(FileSorting::Name.to_string(), "by_name");
|
||||
assert_eq!(FileSorting::Size.to_string(), "by_size");
|
||||
assert_eq!(
|
||||
FileSorting::from_str("by_creation_time").ok().unwrap(),
|
||||
FileSorting::ByCreationTime
|
||||
FileSorting::CreationTime
|
||||
);
|
||||
assert_eq!(
|
||||
FileSorting::from_str("by_mtime").ok().unwrap(),
|
||||
FileSorting::ByModifyTime
|
||||
FileSorting::ModifyTime
|
||||
);
|
||||
assert_eq!(
|
||||
FileSorting::from_str("by_name").ok().unwrap(),
|
||||
FileSorting::ByName
|
||||
FileSorting::Name
|
||||
);
|
||||
assert_eq!(
|
||||
FileSorting::from_str("by_size").ok().unwrap(),
|
||||
FileSorting::BySize
|
||||
FileSorting::Size
|
||||
);
|
||||
assert!(FileSorting::from_str("omar").is_err());
|
||||
// Group dirs
|
||||
@@ -662,12 +669,11 @@ mod tests {
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
size: 64,
|
||||
ftype: None, // File type
|
||||
readonly: false,
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
ftype: None, // File type
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
}),
|
||||
true => FsEntry::Directory(FsDirectory {
|
||||
name: name.to_string(),
|
||||
@@ -675,11 +681,10 @@ mod tests {
|
||||
last_change_time: t_now,
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
readonly: false,
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((7, 5, 5)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(7), UnixPex::from(5), UnixPex::from(5))), // UNIX only
|
||||
}),
|
||||
}
|
||||
}
|
||||
@@ -694,12 +699,11 @@ mod tests {
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
size: size,
|
||||
ftype: None, // File type
|
||||
readonly: false,
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
ftype: None, // File type
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
}),
|
||||
true => FsEntry::Directory(FsDirectory {
|
||||
name: name.to_string(),
|
||||
@@ -707,11 +711,10 @@ mod tests {
|
||||
last_change_time: t_now,
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
readonly: false,
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((7, 5, 5)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(7), UnixPex::from(5), UnixPex::from(5))), // UNIX only
|
||||
}),
|
||||
}
|
||||
}
|
||||
|
||||
257
src/fs/mod.rs
@@ -52,11 +52,10 @@ pub struct FsDirectory {
|
||||
pub last_change_time: SystemTime,
|
||||
pub last_access_time: SystemTime,
|
||||
pub creation_time: SystemTime,
|
||||
pub readonly: bool,
|
||||
pub symlink: Option<Box<FsEntry>>, // UNIX only
|
||||
pub user: Option<u32>, // UNIX only
|
||||
pub group: Option<u32>, // UNIX only
|
||||
pub unix_pex: Option<(u8, u8, u8)>, // UNIX only
|
||||
pub symlink: Option<Box<FsEntry>>, // UNIX only
|
||||
pub user: Option<u32>, // UNIX only
|
||||
pub group: Option<u32>, // UNIX only
|
||||
pub unix_pex: Option<(UnixPex, UnixPex, UnixPex)>, // UNIX only
|
||||
}
|
||||
|
||||
/// ### FsFile
|
||||
@@ -71,12 +70,72 @@ pub struct FsFile {
|
||||
pub last_access_time: SystemTime,
|
||||
pub creation_time: SystemTime,
|
||||
pub size: usize,
|
||||
pub ftype: Option<String>, // File type
|
||||
pub readonly: bool,
|
||||
pub symlink: Option<Box<FsEntry>>, // UNIX only
|
||||
pub user: Option<u32>, // UNIX only
|
||||
pub group: Option<u32>, // UNIX only
|
||||
pub unix_pex: Option<(u8, u8, u8)>, // UNIX only
|
||||
pub ftype: Option<String>, // File type
|
||||
pub symlink: Option<Box<FsEntry>>, // UNIX only
|
||||
pub user: Option<u32>, // UNIX only
|
||||
pub group: Option<u32>, // UNIX only
|
||||
pub unix_pex: Option<(UnixPex, UnixPex, UnixPex)>, // UNIX only
|
||||
}
|
||||
|
||||
/// ## UnixPex
|
||||
///
|
||||
/// Describes the permissions on POSIX system.
|
||||
#[derive(Debug, Clone, Copy, Eq, PartialEq)]
|
||||
pub struct UnixPex {
|
||||
read: bool,
|
||||
write: bool,
|
||||
execute: bool,
|
||||
}
|
||||
|
||||
impl UnixPex {
|
||||
/// ### new
|
||||
///
|
||||
/// Instantiates a new `UnixPex`
|
||||
pub fn new(read: bool, write: bool, execute: bool) -> Self {
|
||||
Self {
|
||||
read,
|
||||
write,
|
||||
execute,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### can_read
|
||||
///
|
||||
/// Returns whether user can read
|
||||
pub fn can_read(&self) -> bool {
|
||||
self.read
|
||||
}
|
||||
|
||||
/// ### can_write
|
||||
///
|
||||
/// Returns whether user can write
|
||||
pub fn can_write(&self) -> bool {
|
||||
self.write
|
||||
}
|
||||
|
||||
/// ### can_execute
|
||||
///
|
||||
/// Returns whether user can execute
|
||||
pub fn can_execute(&self) -> bool {
|
||||
self.execute
|
||||
}
|
||||
|
||||
/// ### as_byte
|
||||
///
|
||||
/// Convert permission to byte as on POSIX systems
|
||||
pub fn as_byte(&self) -> u8 {
|
||||
((self.read as u8) << 2) + ((self.write as u8) << 1) + (self.execute as u8)
|
||||
}
|
||||
}
|
||||
|
||||
impl From<u8> for UnixPex {
|
||||
fn from(bits: u8) -> Self {
|
||||
Self {
|
||||
read: ((bits >> 2) & 0x01) != 0,
|
||||
write: ((bits >> 1) & 0x01) != 0,
|
||||
execute: (bits & 0x01) != 0,
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
impl FsEntry {
|
||||
@@ -173,7 +232,7 @@ impl FsEntry {
|
||||
/// ### get_unix_pex
|
||||
///
|
||||
/// Get unix pex from `FsEntry`
|
||||
pub fn get_unix_pex(&self) -> Option<(u8, u8, u8)> {
|
||||
pub fn get_unix_pex(&self) -> Option<(UnixPex, UnixPex, UnixPex)> {
|
||||
match self {
|
||||
FsEntry::Directory(dir) => dir.unix_pex,
|
||||
FsEntry::File(file) => file.unix_pex,
|
||||
@@ -226,12 +285,34 @@ impl FsEntry {
|
||||
},
|
||||
}
|
||||
}
|
||||
|
||||
/// ### unwrap_file
|
||||
///
|
||||
/// Unwrap FsEntry as FsFile
|
||||
pub fn unwrap_file(self) -> FsFile {
|
||||
match self {
|
||||
FsEntry::File(file) => file,
|
||||
_ => panic!("unwrap_file: not a file"),
|
||||
}
|
||||
}
|
||||
|
||||
#[cfg(test)]
|
||||
/// ### unwrap_dir
|
||||
///
|
||||
/// Unwrap FsEntry as FsDirectory
|
||||
pub fn unwrap_dir(self) -> FsDirectory {
|
||||
match self {
|
||||
FsEntry::Directory(dir) => dir,
|
||||
_ => panic!("unwrap_dir: not a directory"),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
#[cfg(test)]
|
||||
mod tests {
|
||||
|
||||
use super::*;
|
||||
use pretty_assertions::assert_eq;
|
||||
|
||||
#[test]
|
||||
fn test_fs_fsentry_dir() {
|
||||
@@ -242,11 +323,10 @@ mod tests {
|
||||
last_change_time: t_now,
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
readonly: false,
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((7, 5, 5)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(7), UnixPex::from(5), UnixPex::from(5))), // UNIX only
|
||||
});
|
||||
assert_eq!(entry.get_abs_path(), PathBuf::from("/foo"));
|
||||
assert_eq!(entry.get_name(), String::from("foo"));
|
||||
@@ -260,7 +340,11 @@ mod tests {
|
||||
assert_eq!(entry.is_symlink(), false);
|
||||
assert_eq!(entry.is_dir(), true);
|
||||
assert_eq!(entry.is_file(), false);
|
||||
assert_eq!(entry.get_unix_pex(), Some((7, 5, 5)));
|
||||
assert_eq!(
|
||||
entry.get_unix_pex(),
|
||||
Some((UnixPex::from(7), UnixPex::from(5), UnixPex::from(5)))
|
||||
);
|
||||
assert_eq!(entry.unwrap_dir().abs_path, PathBuf::from("/foo"));
|
||||
}
|
||||
|
||||
#[test]
|
||||
@@ -273,12 +357,11 @@ mod tests {
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
size: 8192,
|
||||
readonly: false,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
});
|
||||
assert_eq!(entry.get_abs_path(), PathBuf::from("/bar.txt"));
|
||||
assert_eq!(entry.get_name(), String::from("bar.txt"));
|
||||
@@ -289,10 +372,52 @@ mod tests {
|
||||
assert_eq!(entry.get_ftype(), Some(String::from("txt")));
|
||||
assert_eq!(entry.get_user(), Some(0));
|
||||
assert_eq!(entry.get_group(), Some(0));
|
||||
assert_eq!(entry.get_unix_pex(), Some((6, 4, 4)));
|
||||
assert_eq!(
|
||||
entry.get_unix_pex(),
|
||||
Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4)))
|
||||
);
|
||||
assert_eq!(entry.is_symlink(), false);
|
||||
assert_eq!(entry.is_dir(), false);
|
||||
assert_eq!(entry.is_file(), true);
|
||||
assert_eq!(entry.unwrap_file().abs_path, PathBuf::from("/bar.txt"));
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[should_panic]
|
||||
fn test_fs_fsentry_file_unwrap_bad() {
|
||||
let t_now: SystemTime = SystemTime::now();
|
||||
let entry: FsEntry = FsEntry::File(FsFile {
|
||||
name: String::from("bar.txt"),
|
||||
abs_path: PathBuf::from("/bar.txt"),
|
||||
last_change_time: t_now,
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
size: 8192,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
});
|
||||
entry.unwrap_dir();
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[should_panic]
|
||||
fn test_fs_fsentry_dir_unwrap_bad() {
|
||||
let t_now: SystemTime = SystemTime::now();
|
||||
let entry: FsEntry = FsEntry::Directory(FsDirectory {
|
||||
name: String::from("foo"),
|
||||
abs_path: PathBuf::from("/foo"),
|
||||
last_change_time: t_now,
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(7), UnixPex::from(5), UnixPex::from(5))), // UNIX only
|
||||
});
|
||||
entry.unwrap_file();
|
||||
}
|
||||
|
||||
#[test]
|
||||
@@ -305,12 +430,11 @@ mod tests {
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
size: 8192,
|
||||
readonly: false,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
});
|
||||
assert_eq!(entry.is_hidden(), false);
|
||||
let entry: FsEntry = FsEntry::File(FsFile {
|
||||
@@ -320,12 +444,11 @@ mod tests {
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
size: 8192,
|
||||
readonly: false,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
});
|
||||
assert_eq!(entry.is_hidden(), true);
|
||||
let entry: FsEntry = FsEntry::Directory(FsDirectory {
|
||||
@@ -334,11 +457,10 @@ mod tests {
|
||||
last_change_time: t_now,
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
readonly: false,
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((7, 5, 5)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(7), UnixPex::from(5), UnixPex::from(5))), // UNIX only
|
||||
});
|
||||
assert_eq!(entry.is_hidden(), true);
|
||||
}
|
||||
@@ -354,12 +476,11 @@ mod tests {
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
size: 8192,
|
||||
readonly: false,
|
||||
ftype: Some(String::from("txt")),
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((6, 4, 4)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(6), UnixPex::from(4), UnixPex::from(4))), // UNIX only
|
||||
});
|
||||
// Symlink is None...
|
||||
assert_eq!(
|
||||
@@ -373,11 +494,10 @@ mod tests {
|
||||
last_change_time: t_now,
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
readonly: false,
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((7, 5, 5)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(7), UnixPex::from(5), UnixPex::from(5))), // UNIX only
|
||||
});
|
||||
assert_eq!(entry.get_realfile().get_abs_path(), PathBuf::from("/foo"));
|
||||
}
|
||||
@@ -393,11 +513,10 @@ mod tests {
|
||||
last_change_time: t_now,
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
readonly: false,
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((7, 7, 7)), // UNIX only
|
||||
symlink: None, // UNIX only
|
||||
user: Some(0), // UNIX only
|
||||
group: Some(0), // UNIX only
|
||||
unix_pex: Some((UnixPex::from(7), UnixPex::from(7), UnixPex::from(7))), // UNIX only
|
||||
});
|
||||
let entry_child: FsEntry = FsEntry::Directory(FsDirectory {
|
||||
name: String::from("projects"),
|
||||
@@ -405,11 +524,10 @@ mod tests {
|
||||
last_change_time: t_now,
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
readonly: false,
|
||||
symlink: Some(Box::new(entry_target)),
|
||||
user: Some(0),
|
||||
group: Some(0),
|
||||
unix_pex: Some((7, 7, 7)),
|
||||
unix_pex: Some((UnixPex::from(7), UnixPex::from(7), UnixPex::from(7))),
|
||||
});
|
||||
let entry_root: FsEntry = FsEntry::File(FsFile {
|
||||
name: String::from("projects"),
|
||||
@@ -418,12 +536,11 @@ mod tests {
|
||||
last_access_time: t_now,
|
||||
creation_time: t_now,
|
||||
size: 8,
|
||||
readonly: false,
|
||||
ftype: None,
|
||||
symlink: Some(Box::new(entry_child)),
|
||||
user: Some(0),
|
||||
group: Some(0),
|
||||
unix_pex: Some((7, 7, 7)),
|
||||
unix_pex: Some((UnixPex::from(7), UnixPex::from(7), UnixPex::from(7))),
|
||||
});
|
||||
assert_eq!(entry_root.is_symlink(), true);
|
||||
// get real file
|
||||
@@ -434,4 +551,28 @@ mod tests {
|
||||
PathBuf::from("/home/cvisintin/projects")
|
||||
);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn unix_pex() {
|
||||
let pex: UnixPex = UnixPex::from(4);
|
||||
assert_eq!(pex.can_read(), true);
|
||||
assert_eq!(pex.can_write(), false);
|
||||
assert_eq!(pex.can_execute(), false);
|
||||
let pex: UnixPex = UnixPex::from(0);
|
||||
assert_eq!(pex.can_read(), false);
|
||||
assert_eq!(pex.can_write(), false);
|
||||
assert_eq!(pex.can_execute(), false);
|
||||
let pex: UnixPex = UnixPex::from(3);
|
||||
assert_eq!(pex.can_read(), false);
|
||||
assert_eq!(pex.can_write(), true);
|
||||
assert_eq!(pex.can_execute(), true);
|
||||
let pex: UnixPex = UnixPex::from(7);
|
||||
assert_eq!(pex.can_read(), true);
|
||||
assert_eq!(pex.can_write(), true);
|
||||
assert_eq!(pex.can_execute(), true);
|
||||
let pex: UnixPex = UnixPex::from(3);
|
||||
assert_eq!(pex.as_byte(), 3);
|
||||
let pex: UnixPex = UnixPex::from(7);
|
||||
assert_eq!(pex.as_byte(), 7);
|
||||
}
|
||||
}
|
||||
|
||||
394
src/host/mod.rs
@@ -25,8 +25,6 @@
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// dependencies
|
||||
extern crate wildmatch;
|
||||
// ext
|
||||
use std::fs::{self, File, Metadata, OpenOptions};
|
||||
use std::path::{Path, PathBuf};
|
||||
@@ -34,13 +32,14 @@ use std::time::SystemTime;
|
||||
use thiserror::Error;
|
||||
use wildmatch::WildMatch;
|
||||
// Metadata ext
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
use std::fs::set_permissions;
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
use std::os::unix::fs::{MetadataExt, PermissionsExt};
|
||||
|
||||
// Locals
|
||||
use crate::fs::{FsDirectory, FsEntry, FsFile};
|
||||
use crate::fs::{FsDirectory, FsEntry, FsFile, UnixPex};
|
||||
use crate::utils::path;
|
||||
|
||||
/// ## HostErrorType
|
||||
///
|
||||
@@ -68,7 +67,7 @@ pub enum HostErrorType {
|
||||
/// ### HostError
|
||||
///
|
||||
/// HostError is a wrapper for the error type and the exact io error
|
||||
|
||||
#[derive(Debug)]
|
||||
pub struct HostError {
|
||||
pub error: HostErrorType,
|
||||
ioerr: Option<std::io::Error>,
|
||||
@@ -125,12 +124,17 @@ impl Localhost {
|
||||
///
|
||||
/// Instantiates a new Localhost struct
|
||||
pub fn new(wrkdir: PathBuf) -> Result<Localhost, HostError> {
|
||||
debug!("Initializing localhost at {}", wrkdir.display());
|
||||
let mut host: Localhost = Localhost {
|
||||
wrkdir,
|
||||
files: Vec::new(),
|
||||
};
|
||||
// Check if dir exists
|
||||
if !host.file_exists(host.wrkdir.as_path()) {
|
||||
error!(
|
||||
"Failed to initialize localhost: {} doesn't exist",
|
||||
host.wrkdir.display()
|
||||
);
|
||||
return Err(HostError::new(
|
||||
HostErrorType::NoSuchFileOrDirectory,
|
||||
None,
|
||||
@@ -140,8 +144,15 @@ impl Localhost {
|
||||
// Retrieve files for provided path
|
||||
host.files = match host.scan_dir(host.wrkdir.as_path()) {
|
||||
Ok(files) => files,
|
||||
Err(err) => return Err(err),
|
||||
Err(err) => {
|
||||
error!(
|
||||
"Failed to initialize localhost: could not scan wrkdir: {}",
|
||||
err
|
||||
);
|
||||
return Err(err);
|
||||
}
|
||||
};
|
||||
info!("Localhost initialized with success");
|
||||
Ok(host)
|
||||
}
|
||||
|
||||
@@ -165,8 +176,10 @@ impl Localhost {
|
||||
/// Change working directory with the new provided directory
|
||||
pub fn change_wrkdir(&mut self, new_dir: &Path) -> Result<PathBuf, HostError> {
|
||||
let new_dir: PathBuf = self.to_abs_path(new_dir);
|
||||
info!("Changing localhost directory to {}...", new_dir.display());
|
||||
// Check whether directory exists
|
||||
if !self.file_exists(new_dir.as_path()) {
|
||||
error!("Could not change directory: No such file or directory");
|
||||
return Err(HostError::new(
|
||||
HostErrorType::NoSuchFileOrDirectory,
|
||||
None,
|
||||
@@ -174,10 +187,11 @@ impl Localhost {
|
||||
));
|
||||
}
|
||||
// Change directory
|
||||
if std::env::set_current_dir(new_dir.as_path()).is_err() {
|
||||
if let Err(err) = std::env::set_current_dir(new_dir.as_path()) {
|
||||
error!("Could not enter directory: {}", err);
|
||||
return Err(HostError::new(
|
||||
HostErrorType::NoSuchFileOrDirectory,
|
||||
None,
|
||||
Some(err),
|
||||
new_dir.as_path(),
|
||||
));
|
||||
}
|
||||
@@ -189,11 +203,13 @@ impl Localhost {
|
||||
self.files = match self.scan_dir(self.wrkdir.as_path()) {
|
||||
Ok(files) => files,
|
||||
Err(err) => {
|
||||
error!("Could not scan new directory: {}", err);
|
||||
// Restore directory
|
||||
self.wrkdir = prev_dir;
|
||||
return Err(err);
|
||||
}
|
||||
};
|
||||
debug!("Changed directory to {}", self.wrkdir.display());
|
||||
Ok(self.wrkdir.clone())
|
||||
}
|
||||
|
||||
@@ -210,6 +226,7 @@ impl Localhost {
|
||||
/// ignex: don't report error if directory already exists
|
||||
pub fn mkdir_ex(&mut self, dir_name: &Path, ignex: bool) -> Result<(), HostError> {
|
||||
let dir_path: PathBuf = self.to_abs_path(dir_name);
|
||||
info!("Making directory {}", dir_path.display());
|
||||
// If dir already exists, return Error
|
||||
if dir_path.exists() {
|
||||
match ignex {
|
||||
@@ -229,13 +246,17 @@ impl Localhost {
|
||||
if dir_name.is_relative() {
|
||||
self.files = self.scan_dir(self.wrkdir.as_path())?;
|
||||
}
|
||||
info!("Created directory {}", dir_path.display());
|
||||
Ok(())
|
||||
}
|
||||
Err(err) => Err(HostError::new(
|
||||
HostErrorType::CouldNotCreateFile,
|
||||
Some(err),
|
||||
dir_path.as_path(),
|
||||
)),
|
||||
Err(err) => {
|
||||
error!("Could not make directory: {}", err);
|
||||
Err(HostError::new(
|
||||
HostErrorType::CouldNotCreateFile,
|
||||
Some(err),
|
||||
dir_path.as_path(),
|
||||
))
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
@@ -246,7 +267,9 @@ impl Localhost {
|
||||
match entry {
|
||||
FsEntry::Directory(dir) => {
|
||||
// If file doesn't exist; return error
|
||||
debug!("Removing directory {}", dir.abs_path.display());
|
||||
if !dir.abs_path.as_path().exists() {
|
||||
error!("Directory doesn't exist");
|
||||
return Err(HostError::new(
|
||||
HostErrorType::NoSuchFileOrDirectory,
|
||||
None,
|
||||
@@ -258,18 +281,24 @@ impl Localhost {
|
||||
Ok(_) => {
|
||||
// Update dir
|
||||
self.files = self.scan_dir(self.wrkdir.as_path())?;
|
||||
info!("Removed directory {}", dir.abs_path.display());
|
||||
Ok(())
|
||||
}
|
||||
Err(err) => Err(HostError::new(
|
||||
HostErrorType::DeleteFailed,
|
||||
Some(err),
|
||||
dir.abs_path.as_path(),
|
||||
)),
|
||||
Err(err) => {
|
||||
error!("Could not remove directory: {}", err);
|
||||
Err(HostError::new(
|
||||
HostErrorType::DeleteFailed,
|
||||
Some(err),
|
||||
dir.abs_path.as_path(),
|
||||
))
|
||||
}
|
||||
}
|
||||
}
|
||||
FsEntry::File(file) => {
|
||||
// If file doesn't exist; return error
|
||||
debug!("Removing file {}", file.abs_path.display());
|
||||
if !file.abs_path.as_path().exists() {
|
||||
error!("File doesn't exist");
|
||||
return Err(HostError::new(
|
||||
HostErrorType::NoSuchFileOrDirectory,
|
||||
None,
|
||||
@@ -281,13 +310,17 @@ impl Localhost {
|
||||
Ok(_) => {
|
||||
// Update dir
|
||||
self.files = self.scan_dir(self.wrkdir.as_path())?;
|
||||
info!("Removed file {}", file.abs_path.display());
|
||||
Ok(())
|
||||
}
|
||||
Err(err) => Err(HostError::new(
|
||||
HostErrorType::DeleteFailed,
|
||||
Some(err),
|
||||
file.abs_path.as_path(),
|
||||
)),
|
||||
Err(err) => {
|
||||
error!("Could not remove file: {}", err);
|
||||
Err(HostError::new(
|
||||
HostErrorType::DeleteFailed,
|
||||
Some(err),
|
||||
file.abs_path.as_path(),
|
||||
))
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
@@ -302,13 +335,26 @@ impl Localhost {
|
||||
Ok(_) => {
|
||||
// Scan dir
|
||||
self.files = self.scan_dir(self.wrkdir.as_path())?;
|
||||
debug!(
|
||||
"Moved file {} to {}",
|
||||
entry.get_abs_path().display(),
|
||||
dst_path.display()
|
||||
);
|
||||
Ok(())
|
||||
}
|
||||
Err(err) => Err(HostError::new(
|
||||
HostErrorType::CouldNotCreateFile,
|
||||
Some(err),
|
||||
abs_path.as_path(),
|
||||
)),
|
||||
Err(err) => {
|
||||
error!(
|
||||
"Failed to move {} to {}: {}",
|
||||
entry.get_abs_path().display(),
|
||||
dst_path.display(),
|
||||
err
|
||||
);
|
||||
Err(HostError::new(
|
||||
HostErrorType::CouldNotCreateFile,
|
||||
Some(err),
|
||||
abs_path.as_path(),
|
||||
))
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
@@ -318,6 +364,11 @@ impl Localhost {
|
||||
pub fn copy(&mut self, entry: &FsEntry, dst: &Path) -> Result<(), HostError> {
|
||||
// Get absolute path of dest
|
||||
let dst: PathBuf = self.to_abs_path(dst);
|
||||
info!(
|
||||
"Copying file {} to {}",
|
||||
entry.get_abs_path().display(),
|
||||
dst.display()
|
||||
);
|
||||
// Match entry
|
||||
match entry {
|
||||
FsEntry::File(file) => {
|
||||
@@ -333,16 +384,19 @@ impl Localhost {
|
||||
};
|
||||
// Copy entry path to dst path
|
||||
if let Err(err) = std::fs::copy(file.abs_path.as_path(), dst.as_path()) {
|
||||
error!("Failed to copy file: {}", err);
|
||||
return Err(HostError::new(
|
||||
HostErrorType::CouldNotCreateFile,
|
||||
Some(err),
|
||||
file.abs_path.as_path(),
|
||||
));
|
||||
}
|
||||
info!("File copied");
|
||||
}
|
||||
FsEntry::Directory(dir) => {
|
||||
// If destination path doesn't exist, create destination
|
||||
if !dst.exists() {
|
||||
debug!("Directory {} doesn't exist; creating it", dst.display());
|
||||
self.mkdir(dst.as_path())?;
|
||||
}
|
||||
// Scan dir
|
||||
@@ -384,17 +438,19 @@ impl Localhost {
|
||||
/// ### stat
|
||||
///
|
||||
/// Stat file and create a FsEntry
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
pub fn stat(&self, path: &Path) -> Result<FsEntry, HostError> {
|
||||
info!("Stating file {}", path.display());
|
||||
let path: PathBuf = self.to_abs_path(path);
|
||||
let attr: Metadata = match fs::metadata(path.as_path()) {
|
||||
Ok(metadata) => metadata,
|
||||
Err(err) => {
|
||||
error!("Could not read file metadata: {}", err);
|
||||
return Err(HostError::new(
|
||||
HostErrorType::FileNotAccessible,
|
||||
Some(err),
|
||||
path.as_path(),
|
||||
))
|
||||
));
|
||||
}
|
||||
};
|
||||
let file_name: String = String::from(path.file_name().unwrap().to_str().unwrap_or(""));
|
||||
@@ -406,7 +462,6 @@ impl Localhost {
|
||||
last_change_time: attr.modified().unwrap_or(SystemTime::UNIX_EPOCH),
|
||||
last_access_time: attr.accessed().unwrap_or(SystemTime::UNIX_EPOCH),
|
||||
creation_time: attr.created().unwrap_or(SystemTime::UNIX_EPOCH),
|
||||
readonly: attr.permissions().readonly(),
|
||||
symlink: match fs::read_link(path.as_path()) {
|
||||
Ok(p) => match self.stat(p.as_path()) {
|
||||
Ok(entry) => Some(Box::new(entry)),
|
||||
@@ -429,7 +484,6 @@ impl Localhost {
|
||||
last_change_time: attr.modified().unwrap_or(SystemTime::UNIX_EPOCH),
|
||||
last_access_time: attr.accessed().unwrap_or(SystemTime::UNIX_EPOCH),
|
||||
creation_time: attr.created().unwrap_or(SystemTime::UNIX_EPOCH),
|
||||
readonly: attr.permissions().readonly(),
|
||||
size: attr.len() as usize,
|
||||
ftype: extension,
|
||||
symlink: match fs::read_link(path.as_path()) {
|
||||
@@ -451,17 +505,18 @@ impl Localhost {
|
||||
///
|
||||
/// Stat file and create a FsEntry
|
||||
#[cfg(target_os = "windows")]
|
||||
#[cfg(not(tarpaulin_include))]
|
||||
pub fn stat(&self, path: &Path) -> Result<FsEntry, HostError> {
|
||||
let path: PathBuf = self.to_abs_path(path);
|
||||
info!("Stating file {}", path.display());
|
||||
let attr: Metadata = match fs::metadata(path.as_path()) {
|
||||
Ok(metadata) => metadata,
|
||||
Err(err) => {
|
||||
error!("Could not read file metadata: {}", err);
|
||||
return Err(HostError::new(
|
||||
HostErrorType::FileNotAccessible,
|
||||
Some(err),
|
||||
path.as_path(),
|
||||
))
|
||||
));
|
||||
}
|
||||
};
|
||||
let file_name: String = String::from(path.file_name().unwrap().to_str().unwrap_or(""));
|
||||
@@ -473,7 +528,6 @@ impl Localhost {
|
||||
last_change_time: attr.modified().unwrap_or(SystemTime::UNIX_EPOCH),
|
||||
last_access_time: attr.accessed().unwrap_or(SystemTime::UNIX_EPOCH),
|
||||
creation_time: attr.created().unwrap_or(SystemTime::UNIX_EPOCH),
|
||||
readonly: attr.permissions().readonly(),
|
||||
symlink: match fs::read_link(path.as_path()) {
|
||||
Ok(p) => match self.stat(p.as_path()) {
|
||||
Ok(entry) => Some(Box::new(entry)),
|
||||
@@ -497,7 +551,6 @@ impl Localhost {
|
||||
last_change_time: attr.modified().unwrap_or(SystemTime::UNIX_EPOCH),
|
||||
last_access_time: attr.accessed().unwrap_or(SystemTime::UNIX_EPOCH),
|
||||
creation_time: attr.created().unwrap_or(SystemTime::UNIX_EPOCH),
|
||||
readonly: attr.permissions().readonly(),
|
||||
size: attr.len() as usize,
|
||||
ftype: extension,
|
||||
symlink: match fs::read_link(path.as_path()) {
|
||||
@@ -523,23 +576,30 @@ impl Localhost {
|
||||
let args: Vec<&str> = cmd.split(' ').collect();
|
||||
let cmd: &str = args.first().unwrap();
|
||||
let argv: &[&str] = &args[1..];
|
||||
info!("Executing command: {} {:?}", cmd, argv);
|
||||
match std::process::Command::new(cmd).args(argv).output() {
|
||||
Ok(output) => match std::str::from_utf8(&output.stdout) {
|
||||
Ok(s) => Ok(s.to_string()),
|
||||
Ok(s) => {
|
||||
info!("Command output: {}", s);
|
||||
Ok(s.to_string())
|
||||
}
|
||||
Err(_) => Ok(String::new()),
|
||||
},
|
||||
Err(err) => Err(HostError::new(
|
||||
HostErrorType::ExecutionFailed,
|
||||
Some(err),
|
||||
self.wrkdir.as_path(),
|
||||
)),
|
||||
Err(err) => {
|
||||
error!("Failed to run command: {}", err);
|
||||
Err(HostError::new(
|
||||
HostErrorType::ExecutionFailed,
|
||||
Some(err),
|
||||
self.wrkdir.as_path(),
|
||||
))
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### chmod
|
||||
///
|
||||
/// Change file mode to file, according to UNIX permissions
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
pub fn chmod(&self, path: &Path, pex: (u8, u8, u8)) -> Result<(), HostError> {
|
||||
let path: PathBuf = self.to_abs_path(path);
|
||||
// Get metadta
|
||||
@@ -548,19 +608,32 @@ impl Localhost {
|
||||
let mut mpex = metadata.permissions();
|
||||
mpex.set_mode(self.mode_to_u32(pex));
|
||||
match set_permissions(path.as_path(), mpex) {
|
||||
Ok(_) => Ok(()),
|
||||
Err(err) => Err(HostError::new(
|
||||
HostErrorType::FileNotAccessible,
|
||||
Some(err),
|
||||
path.as_path(),
|
||||
)),
|
||||
Ok(_) => {
|
||||
info!("Changed mode for {} to {:?}", path.display(), pex);
|
||||
Ok(())
|
||||
}
|
||||
Err(err) => {
|
||||
error!("Could not change mode for file {}: {}", path.display(), err);
|
||||
Err(HostError::new(
|
||||
HostErrorType::FileNotAccessible,
|
||||
Some(err),
|
||||
path.as_path(),
|
||||
))
|
||||
}
|
||||
}
|
||||
}
|
||||
Err(err) => Err(HostError::new(
|
||||
HostErrorType::FileNotAccessible,
|
||||
Some(err),
|
||||
path.as_path(),
|
||||
)),
|
||||
Err(err) => {
|
||||
error!(
|
||||
"Chmod failed; could not read metadata for file {}: {}",
|
||||
path.display(),
|
||||
err
|
||||
);
|
||||
Err(HostError::new(
|
||||
HostErrorType::FileNotAccessible,
|
||||
Some(err),
|
||||
path.as_path(),
|
||||
))
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
@@ -569,7 +642,9 @@ impl Localhost {
|
||||
/// Open file for read
|
||||
pub fn open_file_read(&self, file: &Path) -> Result<File, HostError> {
|
||||
let file: PathBuf = self.to_abs_path(file);
|
||||
info!("Opening file {} for read", file.display());
|
||||
if !self.file_exists(file.as_path()) {
|
||||
error!("File doesn't exist!");
|
||||
return Err(HostError::new(
|
||||
HostErrorType::NoSuchFileOrDirectory,
|
||||
None,
|
||||
@@ -583,11 +658,14 @@ impl Localhost {
|
||||
.open(file.as_path())
|
||||
{
|
||||
Ok(f) => Ok(f),
|
||||
Err(err) => Err(HostError::new(
|
||||
HostErrorType::FileNotAccessible,
|
||||
Some(err),
|
||||
file.as_path(),
|
||||
)),
|
||||
Err(err) => {
|
||||
error!("Could not open file for read: {}", err);
|
||||
Err(HostError::new(
|
||||
HostErrorType::FileNotAccessible,
|
||||
Some(err),
|
||||
file.as_path(),
|
||||
))
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
@@ -596,6 +674,7 @@ impl Localhost {
|
||||
/// Open file for write
|
||||
pub fn open_file_write(&self, file: &Path) -> Result<File, HostError> {
|
||||
let file: PathBuf = self.to_abs_path(file);
|
||||
info!("Opening file {} for write", file.display());
|
||||
match OpenOptions::new()
|
||||
.create(true)
|
||||
.write(true)
|
||||
@@ -603,18 +682,21 @@ impl Localhost {
|
||||
.open(file.as_path())
|
||||
{
|
||||
Ok(f) => Ok(f),
|
||||
Err(err) => match self.file_exists(file.as_path()) {
|
||||
true => Err(HostError::new(
|
||||
HostErrorType::ReadonlyFile,
|
||||
Some(err),
|
||||
file.as_path(),
|
||||
)),
|
||||
false => Err(HostError::new(
|
||||
HostErrorType::FileNotAccessible,
|
||||
Some(err),
|
||||
file.as_path(),
|
||||
)),
|
||||
},
|
||||
Err(err) => {
|
||||
error!("Failed to open file: {}", err);
|
||||
match self.file_exists(file.as_path()) {
|
||||
true => Err(HostError::new(
|
||||
HostErrorType::ReadonlyFile,
|
||||
Some(err),
|
||||
file.as_path(),
|
||||
)),
|
||||
false => Err(HostError::new(
|
||||
HostErrorType::FileNotAccessible,
|
||||
Some(err),
|
||||
file.as_path(),
|
||||
)),
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
@@ -629,13 +711,15 @@ impl Localhost {
|
||||
///
|
||||
/// Get content of the current directory as a list of fs entry
|
||||
pub fn scan_dir(&self, dir: &Path) -> Result<Vec<FsEntry>, HostError> {
|
||||
info!("Reading directory {}", dir.display());
|
||||
match std::fs::read_dir(dir) {
|
||||
Ok(e) => {
|
||||
let mut fs_entries: Vec<FsEntry> = Vec::new();
|
||||
for entry in e.flatten() {
|
||||
// NOTE: 0.4.1, don't fail if stat for one file fails
|
||||
if let Ok(entry) = self.stat(entry.path().as_path()) {
|
||||
fs_entries.push(entry);
|
||||
match self.stat(entry.path().as_path()) {
|
||||
Ok(entry) => fs_entries.push(entry),
|
||||
Err(e) => error!("Failed to stat {}: {}", entry.path().display(), e),
|
||||
}
|
||||
}
|
||||
Ok(fs_entries)
|
||||
@@ -683,10 +767,7 @@ impl Localhost {
|
||||
if filter.matches(dir.name.as_str()) {
|
||||
drained.push(FsEntry::Directory(dir.clone()));
|
||||
}
|
||||
match self.iter_search(dir.abs_path.as_path(), filter) {
|
||||
Ok(mut filtered) => drained.append(&mut filtered),
|
||||
Err(err) => return Err(err),
|
||||
}
|
||||
drained.append(&mut self.iter_search(dir.abs_path.as_path(), filter)?);
|
||||
}
|
||||
FsEntry::File(file) => {
|
||||
if filter.matches(file.name.as_str()) {
|
||||
@@ -703,18 +784,18 @@ impl Localhost {
|
||||
/// ### u32_to_mode
|
||||
///
|
||||
/// Return string with format xxxxxx to tuple of permissions (user, group, others)
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
fn u32_to_mode(&self, mode: u32) -> (u8, u8, u8) {
|
||||
let user: u8 = ((mode >> 6) & 0x7) as u8;
|
||||
let group: u8 = ((mode >> 3) & 0x7) as u8;
|
||||
let others: u8 = (mode & 0x7) as u8;
|
||||
#[cfg(target_family = "unix")]
|
||||
fn u32_to_mode(&self, mode: u32) -> (UnixPex, UnixPex, UnixPex) {
|
||||
let user: UnixPex = UnixPex::from(((mode >> 6) & 0x7) as u8);
|
||||
let group: UnixPex = UnixPex::from(((mode >> 3) & 0x7) as u8);
|
||||
let others: UnixPex = UnixPex::from((mode & 0x7) as u8);
|
||||
(user, group, others)
|
||||
}
|
||||
|
||||
/// mode_to_u32
|
||||
///
|
||||
/// Convert owner,group,others to u32
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
fn mode_to_u32(&self, mode: (u8, u8, u8)) -> u32 {
|
||||
((mode.0 as u32) << 6) + ((mode.1 as u32) << 3) + mode.2 as u32
|
||||
}
|
||||
@@ -723,15 +804,7 @@ impl Localhost {
|
||||
///
|
||||
/// Convert path to absolute path
|
||||
fn to_abs_path(&self, p: &Path) -> PathBuf {
|
||||
// Convert to abs path
|
||||
match p.is_relative() {
|
||||
true => {
|
||||
let mut path: PathBuf = self.wrkdir.clone();
|
||||
path.push(p);
|
||||
path
|
||||
}
|
||||
false => PathBuf::from(p),
|
||||
}
|
||||
path::absolutize(self.wrkdir.as_path(), p)
|
||||
}
|
||||
}
|
||||
|
||||
@@ -739,10 +812,17 @@ impl Localhost {
|
||||
mod tests {
|
||||
|
||||
use super::*;
|
||||
#[cfg(target_family = "unix")]
|
||||
use crate::utils::test_helpers::{create_sample_file, make_fsentry};
|
||||
use crate::utils::test_helpers::{make_dir_at, make_file_at};
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
#[cfg(target_family = "unix")]
|
||||
use std::fs::File;
|
||||
#[cfg(target_family = "unix")]
|
||||
use std::io::Write;
|
||||
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
use std::os::unix::fs::{symlink, PermissionsExt};
|
||||
|
||||
#[test]
|
||||
@@ -754,7 +834,7 @@ mod tests {
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
fn test_host_localhost_new() {
|
||||
let host: Localhost = Localhost::new(PathBuf::from("/dev")).ok().unwrap();
|
||||
assert_eq!(host.wrkdir, PathBuf::from("/dev"));
|
||||
@@ -790,14 +870,14 @@ mod tests {
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
fn test_host_localhost_pwd() {
|
||||
let host: Localhost = Localhost::new(PathBuf::from("/dev")).ok().unwrap();
|
||||
assert_eq!(host.pwd(), PathBuf::from("/dev"));
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
fn test_host_localhost_list_files() {
|
||||
let host: Localhost = Localhost::new(PathBuf::from("/dev")).ok().unwrap();
|
||||
// Scan dir
|
||||
@@ -810,7 +890,7 @@ mod tests {
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
fn test_host_localhost_change_dir() {
|
||||
let mut host: Localhost = Localhost::new(PathBuf::from("/dev")).ok().unwrap();
|
||||
let new_dir: PathBuf = PathBuf::from("/dev");
|
||||
@@ -826,7 +906,7 @@ mod tests {
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
#[should_panic]
|
||||
fn test_host_localhost_change_dir_failed() {
|
||||
let mut host: Localhost = Localhost::new(PathBuf::from("/dev")).ok().unwrap();
|
||||
@@ -835,7 +915,7 @@ mod tests {
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
fn test_host_localhost_open_read() {
|
||||
let host: Localhost = Localhost::new(PathBuf::from("/dev")).ok().unwrap();
|
||||
// Create temp file
|
||||
@@ -844,7 +924,7 @@ mod tests {
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
#[should_panic]
|
||||
fn test_host_localhost_open_read_err_no_such_file() {
|
||||
let host: Localhost = Localhost::new(PathBuf::from("/dev")).ok().unwrap();
|
||||
@@ -854,7 +934,7 @@ mod tests {
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(any(target_os = "macos", target_os = "linux"))]
|
||||
fn test_host_localhost_open_read_err_not_accessible() {
|
||||
let host: Localhost = Localhost::new(PathBuf::from("/dev")).ok().unwrap();
|
||||
let file: tempfile::NamedTempFile = create_sample_file();
|
||||
@@ -865,7 +945,7 @@ mod tests {
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
fn test_host_localhost_open_write() {
|
||||
let host: Localhost = Localhost::new(PathBuf::from("/dev")).ok().unwrap();
|
||||
// Create temp file
|
||||
@@ -874,7 +954,7 @@ mod tests {
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(any(target_os = "macos", target_os = "linux"))]
|
||||
fn test_host_localhost_open_write_err() {
|
||||
let host: Localhost = Localhost::new(PathBuf::from("/dev")).ok().unwrap();
|
||||
let file: tempfile::NamedTempFile = create_sample_file();
|
||||
@@ -883,7 +963,8 @@ mod tests {
|
||||
//fs::set_permissions(file.path(), perms)?;
|
||||
assert!(host.open_file_write(file.path()).is_err());
|
||||
}
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
|
||||
#[cfg(target_family = "unix")]
|
||||
#[test]
|
||||
fn test_host_localhost_symlinks() {
|
||||
let tmpdir: tempfile::TempDir = tempfile::TempDir::new().unwrap();
|
||||
@@ -931,7 +1012,7 @@ mod tests {
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
fn test_host_localhost_mkdir() {
|
||||
let tmpdir: tempfile::TempDir = tempfile::TempDir::new().unwrap();
|
||||
let mut host: Localhost = Localhost::new(PathBuf::from(tmpdir.path())).ok().unwrap();
|
||||
@@ -946,10 +1027,17 @@ mod tests {
|
||||
assert!(host
|
||||
.mkdir_ex(PathBuf::from("/tmp/test_dir_123456789").as_path(), true)
|
||||
.is_ok());
|
||||
// Fail
|
||||
assert!(host
|
||||
.mkdir_ex(
|
||||
PathBuf::from("/aaaa/oooooo/tmp/test_dir_123456789").as_path(),
|
||||
true
|
||||
)
|
||||
.is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
fn test_host_localhost_remove() {
|
||||
let tmpdir: tempfile::TempDir = tempfile::TempDir::new().unwrap();
|
||||
// Create sample file
|
||||
@@ -968,10 +1056,17 @@ mod tests {
|
||||
let files: Vec<FsEntry> = host.list_dir();
|
||||
assert_eq!(files.len(), 1); // There should be 1 file now
|
||||
assert!(host.remove(files.get(0).unwrap()).is_ok());
|
||||
// Remove unexisting directory
|
||||
assert!(host
|
||||
.remove(&make_fsentry(PathBuf::from("/a/b/c/d"), true))
|
||||
.is_err());
|
||||
assert!(host
|
||||
.remove(&make_fsentry(PathBuf::from("/aaaaaaa"), false))
|
||||
.is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
fn test_host_localhost_rename() {
|
||||
let tmpdir: tempfile::TempDir = tempfile::TempDir::new().unwrap();
|
||||
// Create sample file
|
||||
@@ -981,7 +1076,7 @@ mod tests {
|
||||
let mut host: Localhost = Localhost::new(PathBuf::from(tmpdir.path())).ok().unwrap();
|
||||
let files: Vec<FsEntry> = host.list_dir();
|
||||
assert_eq!(files.len(), 1); // There should be 1 file now
|
||||
assert_eq!(get_filename(files.get(0).unwrap()), String::from("foo.txt"));
|
||||
assert_eq!(files.get(0).unwrap().get_name(), "foo.txt");
|
||||
// Rename file
|
||||
let dst_path: PathBuf =
|
||||
PathBuf::from(format!("{}/bar.txt", tmpdir.path().display()).as_str());
|
||||
@@ -991,7 +1086,7 @@ mod tests {
|
||||
// There should be still 1 file now, but named bar.txt
|
||||
let files: Vec<FsEntry> = host.list_dir();
|
||||
assert_eq!(files.len(), 1); // There should be 0 files now
|
||||
assert_eq!(get_filename(files.get(0).unwrap()), String::from("bar.txt"));
|
||||
assert_eq!(files.get(0).unwrap().get_name(), "bar.txt");
|
||||
// Fail
|
||||
let bad_path: PathBuf = PathBuf::from("/asdailsjoidoewojdijow/ashdiuahu");
|
||||
assert!(host
|
||||
@@ -999,7 +1094,7 @@ mod tests {
|
||||
.is_err());
|
||||
}
|
||||
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
#[test]
|
||||
fn test_host_chmod() {
|
||||
let tmpdir: tempfile::TempDir = tempfile::TempDir::new().unwrap();
|
||||
@@ -1018,7 +1113,7 @@ mod tests {
|
||||
.is_err());
|
||||
}
|
||||
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
#[test]
|
||||
fn test_host_copy_file_absolute() {
|
||||
let tmpdir: tempfile::TempDir = tempfile::TempDir::new().unwrap();
|
||||
@@ -1039,9 +1134,16 @@ mod tests {
|
||||
assert!(host.copy(&file1_entry, file2_path.as_path()).is_ok());
|
||||
// Verify host has two files
|
||||
assert_eq!(host.files.len(), 2);
|
||||
// Fail copy
|
||||
assert!(host
|
||||
.copy(
|
||||
&make_fsentry(PathBuf::from("/a/a7/a/a7a"), false),
|
||||
PathBuf::from("571k422i").as_path()
|
||||
)
|
||||
.is_err());
|
||||
}
|
||||
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
#[test]
|
||||
fn test_host_copy_file_relative() {
|
||||
let tmpdir: tempfile::TempDir = tempfile::TempDir::new().unwrap();
|
||||
@@ -1063,7 +1165,7 @@ mod tests {
|
||||
assert_eq!(host.files.len(), 2);
|
||||
}
|
||||
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
#[test]
|
||||
fn test_host_copy_directory_absolute() {
|
||||
let tmpdir: tempfile::TempDir = tempfile::TempDir::new().unwrap();
|
||||
@@ -1094,7 +1196,7 @@ mod tests {
|
||||
assert!(host.stat(test_file_path.as_path()).is_ok());
|
||||
}
|
||||
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
#[test]
|
||||
fn test_host_copy_directory_relative() {
|
||||
let tmpdir: tempfile::TempDir = tempfile::TempDir::new().unwrap();
|
||||
@@ -1129,7 +1231,7 @@ mod tests {
|
||||
let tmpdir: tempfile::TempDir = tempfile::TempDir::new().unwrap();
|
||||
let host: Localhost = Localhost::new(PathBuf::from(tmpdir.path())).ok().unwrap();
|
||||
// Execute
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
#[cfg(target_family = "unix")]
|
||||
assert_eq!(host.exec("echo 5").ok().unwrap().as_str(), "5\n");
|
||||
#[cfg(target_os = "windows")]
|
||||
assert_eq!(host.exec("echo 5").ok().unwrap().as_str(), "5\r\n");
|
||||
@@ -1140,16 +1242,16 @@ mod tests {
|
||||
let tmpdir: tempfile::TempDir = tempfile::TempDir::new().unwrap();
|
||||
let dir_path: &Path = tmpdir.path();
|
||||
// Make files
|
||||
assert!(make_sample_file(dir_path, "pippo.txt").is_ok());
|
||||
assert!(make_sample_file(dir_path, "foo.jpg").is_ok());
|
||||
assert!(make_file_at(dir_path, "pippo.txt").is_ok());
|
||||
assert!(make_file_at(dir_path, "foo.jpg").is_ok());
|
||||
// Make nested struct
|
||||
assert!(make_dir(dir_path, "examples").is_ok());
|
||||
assert!(make_dir_at(dir_path, "examples").is_ok());
|
||||
let mut subdir: PathBuf = PathBuf::from(dir_path);
|
||||
subdir.push("examples/");
|
||||
assert!(make_sample_file(subdir.as_path(), "omar.txt").is_ok());
|
||||
assert!(make_sample_file(subdir.as_path(), "errors.txt").is_ok());
|
||||
assert!(make_sample_file(subdir.as_path(), "screenshot.png").is_ok());
|
||||
assert!(make_sample_file(subdir.as_path(), "examples.csv").is_ok());
|
||||
assert!(make_file_at(subdir.as_path(), "omar.txt").is_ok());
|
||||
assert!(make_file_at(subdir.as_path(), "errors.txt").is_ok());
|
||||
assert!(make_file_at(subdir.as_path(), "screenshot.png").is_ok());
|
||||
assert!(make_file_at(subdir.as_path(), "examples.csv").is_ok());
|
||||
let host: Localhost = Localhost::new(PathBuf::from(dir_path)).ok().unwrap();
|
||||
// Find txt files
|
||||
let mut result: Vec<FsEntry> = host.find("*.txt").ok().unwrap();
|
||||
@@ -1208,50 +1310,4 @@ mod tests {
|
||||
String::from("File already exists")
|
||||
);
|
||||
}
|
||||
|
||||
/// ### make_sample_file
|
||||
///
|
||||
/// Make a file with `name` in the current directory
|
||||
fn make_sample_file(dir: &Path, filename: &str) -> std::io::Result<()> {
|
||||
let mut p: PathBuf = PathBuf::from(dir);
|
||||
p.push(filename);
|
||||
let mut file: File = File::create(p.as_path())?;
|
||||
write!(
|
||||
file,
|
||||
"Lorem ipsum dolor sit amet, consectetur adipiscing elit.\nMauris ultricies consequat eros,\nnec scelerisque magna imperdiet metus.\n"
|
||||
)?;
|
||||
Ok(())
|
||||
}
|
||||
|
||||
/// ### make_dir
|
||||
///
|
||||
/// Make a directory in `dir`
|
||||
fn make_dir(dir: &Path, dirname: &str) -> std::io::Result<()> {
|
||||
let mut p: PathBuf = PathBuf::from(dir);
|
||||
p.push(dirname);
|
||||
std::fs::create_dir(p.as_path())
|
||||
}
|
||||
|
||||
/// ### create_sample_file
|
||||
///
|
||||
/// Create a sample file
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
fn create_sample_file() -> tempfile::NamedTempFile {
|
||||
// Write
|
||||
let mut tmpfile: tempfile::NamedTempFile = tempfile::NamedTempFile::new().unwrap();
|
||||
write!(
|
||||
tmpfile,
|
||||
"Lorem ipsum dolor sit amet, consectetur adipiscing elit.\nMauris ultricies consequat eros,\nnec scelerisque magna imperdiet metus.\n"
|
||||
)
|
||||
.unwrap();
|
||||
tmpfile
|
||||
}
|
||||
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
fn get_filename(entry: &FsEntry) -> String {
|
||||
match entry {
|
||||
FsEntry::Directory(d) => d.name.clone(),
|
||||
FsEntry::File(f) => f.name.clone(),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
37
src/lib.rs
@@ -1,3 +1,11 @@
|
||||
#![doc(html_playground_url = "https://play.rust-lang.org")]
|
||||
#![doc(
|
||||
html_favicon_url = "https://raw.githubusercontent.com/veeso/termscp/main/assets/images/termscp-128.png"
|
||||
)]
|
||||
#![doc(
|
||||
html_logo_url = "https://raw.githubusercontent.com/veeso/termscp/main/assets/images/termscp-512.png"
|
||||
)]
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
@@ -24,17 +32,44 @@
|
||||
|
||||
#[macro_use]
|
||||
extern crate bitflags;
|
||||
extern crate bytesize;
|
||||
extern crate chrono;
|
||||
extern crate content_inspector;
|
||||
extern crate crossterm;
|
||||
extern crate dirs;
|
||||
extern crate edit;
|
||||
extern crate hostname;
|
||||
#[cfg(feature = "with-keyring")]
|
||||
extern crate keyring;
|
||||
#[macro_use]
|
||||
extern crate lazy_static;
|
||||
#[macro_use]
|
||||
extern crate log;
|
||||
#[macro_use]
|
||||
extern crate magic_crypt;
|
||||
extern crate open;
|
||||
#[cfg(target_os = "windows")]
|
||||
extern crate path_slash;
|
||||
extern crate rand;
|
||||
extern crate regex;
|
||||
extern crate ssh2;
|
||||
extern crate suppaftp;
|
||||
extern crate tempfile;
|
||||
extern crate textwrap;
|
||||
extern crate tui_realm_stdlib;
|
||||
extern crate tuirealm;
|
||||
extern crate ureq;
|
||||
#[cfg(target_family = "unix")]
|
||||
extern crate users;
|
||||
extern crate whoami;
|
||||
extern crate wildmatch;
|
||||
|
||||
pub mod activity_manager;
|
||||
pub mod bookmarks;
|
||||
pub mod config;
|
||||
pub mod filetransfer;
|
||||
pub mod fs;
|
||||
pub mod host;
|
||||
pub mod support;
|
||||
pub mod system;
|
||||
pub mod ui;
|
||||
pub mod utils;
|
||||
|
||||
290
src/main.rs
@@ -26,175 +26,249 @@ const TERMSCP_VERSION: &str = env!("CARGO_PKG_VERSION");
|
||||
const TERMSCP_AUTHORS: &str = env!("CARGO_PKG_AUTHORS");
|
||||
|
||||
// Crates
|
||||
extern crate getopts;
|
||||
extern crate argh;
|
||||
#[macro_use]
|
||||
extern crate bitflags;
|
||||
#[macro_use]
|
||||
extern crate lazy_static;
|
||||
#[macro_use]
|
||||
extern crate log;
|
||||
#[macro_use]
|
||||
extern crate magic_crypt;
|
||||
extern crate rpassword;
|
||||
|
||||
// External libs
|
||||
use getopts::Options;
|
||||
use argh::FromArgs;
|
||||
use std::env;
|
||||
use std::path::PathBuf;
|
||||
use std::time::Duration;
|
||||
|
||||
// Include
|
||||
mod activity_manager;
|
||||
mod bookmarks;
|
||||
mod config;
|
||||
mod filetransfer;
|
||||
mod fs;
|
||||
mod host;
|
||||
mod support;
|
||||
mod system;
|
||||
mod ui;
|
||||
mod utils;
|
||||
|
||||
// namespaces
|
||||
use activity_manager::{ActivityManager, NextActivity};
|
||||
use filetransfer::FileTransferProtocol;
|
||||
use filetransfer::FileTransferParams;
|
||||
use system::logging;
|
||||
|
||||
/// ### print_usage
|
||||
///
|
||||
/// Print usage
|
||||
enum Task {
|
||||
Activity(NextActivity),
|
||||
ImportTheme(PathBuf),
|
||||
}
|
||||
|
||||
fn print_usage(opts: Options) {
|
||||
let brief = String::from(
|
||||
"Usage: termscp [options]... [protocol://user@address:port:wrkdir] [local-wrkdir]",
|
||||
);
|
||||
print!("{}", opts.usage(&brief));
|
||||
println!("\nPlease, report issues to <https://github.com/veeso/termscp>");
|
||||
#[derive(FromArgs)]
|
||||
#[argh(description = "
|
||||
where positional can be: [protocol://user@address:port:wrkdir] [local-wrkdir]
|
||||
|
||||
Please, report issues to <https://github.com/veeso/termscp>
|
||||
Please, consider supporting the author <https://www.buymeacoffee.com/veeso>")]
|
||||
struct Args {
|
||||
#[argh(switch, short = 'c', description = "open termscp configuration")]
|
||||
config: bool,
|
||||
#[argh(option, short = 'P', description = "provide password from CLI")]
|
||||
password: Option<String>,
|
||||
#[argh(switch, short = 'q', description = "disable logging")]
|
||||
quiet: bool,
|
||||
#[argh(option, short = 't', description = "import specified theme")]
|
||||
theme: Option<String>,
|
||||
#[argh(
|
||||
option,
|
||||
short = 'T',
|
||||
default = "10",
|
||||
description = "set UI ticks; default 10ms"
|
||||
)]
|
||||
ticks: u64,
|
||||
#[argh(switch, short = 'v', description = "print version")]
|
||||
version: bool,
|
||||
// -- positional
|
||||
#[argh(
|
||||
positional,
|
||||
description = "protocol://user@address:port:wrkdir local-wrkdir"
|
||||
)]
|
||||
positional: Vec<String>,
|
||||
}
|
||||
|
||||
struct RunOpts {
|
||||
remote: Option<FileTransferParams>,
|
||||
ticks: Duration,
|
||||
log_enabled: bool,
|
||||
task: Task,
|
||||
}
|
||||
|
||||
impl Default for RunOpts {
|
||||
fn default() -> Self {
|
||||
Self {
|
||||
remote: None,
|
||||
ticks: Duration::from_millis(10),
|
||||
log_enabled: true,
|
||||
task: Task::Activity(NextActivity::Authentication),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
fn main() {
|
||||
let args: Vec<String> = env::args().collect();
|
||||
//Program CLI options
|
||||
let mut address: Option<String> = None; // None
|
||||
let mut port: u16 = 22; // Default port
|
||||
let mut username: Option<String> = None; // Default username
|
||||
let mut password: Option<String> = None; // Default password
|
||||
let mut remote_wrkdir: Option<PathBuf> = None;
|
||||
let mut protocol: FileTransferProtocol = FileTransferProtocol::Sftp; // Default protocol
|
||||
let mut ticks: Duration = Duration::from_millis(10);
|
||||
//Process options
|
||||
let mut opts = Options::new();
|
||||
opts.optopt(
|
||||
"P",
|
||||
"password",
|
||||
"Provide password from CLI (use at your own risk)",
|
||||
"<password>",
|
||||
);
|
||||
opts.optopt("T", "ticks", "Set UI ticks; default 10ms", "<ms>");
|
||||
opts.optflag("v", "version", "");
|
||||
opts.optflag("h", "help", "Print this menu");
|
||||
let matches = match opts.parse(&args[1..]) {
|
||||
Ok(m) => m,
|
||||
Err(f) => {
|
||||
println!("{}", f.to_string());
|
||||
let args: Args = argh::from_env();
|
||||
// Parse args
|
||||
let mut run_opts: RunOpts = match parse_args(args) {
|
||||
Ok(opts) => opts,
|
||||
Err(err) => {
|
||||
eprintln!("{}", err);
|
||||
std::process::exit(255);
|
||||
}
|
||||
};
|
||||
// Help
|
||||
if matches.opt_present("h") {
|
||||
print_usage(opts);
|
||||
std::process::exit(255);
|
||||
}
|
||||
// Version
|
||||
if matches.opt_present("v") {
|
||||
eprintln!(
|
||||
"TermSCP - {} - Developed by {}",
|
||||
TERMSCP_VERSION, TERMSCP_AUTHORS,
|
||||
);
|
||||
std::process::exit(255);
|
||||
}
|
||||
// Match password
|
||||
if let Some(passwd) = matches.opt_str("P") {
|
||||
password = Some(passwd);
|
||||
}
|
||||
// Match ticks
|
||||
if let Some(val) = matches.opt_str("T") {
|
||||
match val.parse::<usize>() {
|
||||
Ok(val) => ticks = Duration::from_millis(val as u64),
|
||||
Err(_) => {
|
||||
eprintln!("Ticks is not a number '{}'", val);
|
||||
print_usage(opts);
|
||||
std::process::exit(255);
|
||||
}
|
||||
// Setup logging
|
||||
if run_opts.log_enabled {
|
||||
if let Err(err) = logging::init() {
|
||||
eprintln!("Failed to initialize logging: {}", err);
|
||||
}
|
||||
}
|
||||
// Check free args
|
||||
let extra_args: Vec<String> = matches.free;
|
||||
// Read password from remote
|
||||
if let Err(err) = read_password(&mut run_opts) {
|
||||
eprintln!("{}", err);
|
||||
std::process::exit(255);
|
||||
}
|
||||
info!("termscp {} started!", TERMSCP_VERSION);
|
||||
// Run
|
||||
info!("Starting activity manager...");
|
||||
let rc: i32 = run(run_opts);
|
||||
info!("termscp terminated");
|
||||
// Then return
|
||||
std::process::exit(rc);
|
||||
}
|
||||
|
||||
/// ### parse_args
|
||||
///
|
||||
/// Parse arguments
|
||||
/// In case of success returns `RunOpts`
|
||||
/// in case something is wrong returns the error message
|
||||
fn parse_args(args: Args) -> Result<RunOpts, String> {
|
||||
let mut run_opts: RunOpts = RunOpts::default();
|
||||
// Version
|
||||
if args.version {
|
||||
return Err(format!(
|
||||
"termscp - {} - Developed by {}",
|
||||
TERMSCP_VERSION, TERMSCP_AUTHORS,
|
||||
));
|
||||
}
|
||||
// Setup activity?
|
||||
if args.config {
|
||||
run_opts.task = Task::Activity(NextActivity::SetupActivity);
|
||||
}
|
||||
// Logging
|
||||
if args.quiet {
|
||||
run_opts.log_enabled = false;
|
||||
}
|
||||
// Match ticks
|
||||
run_opts.ticks = Duration::from_millis(args.ticks);
|
||||
// @! extra modes
|
||||
if let Some(theme) = args.theme {
|
||||
run_opts.task = Task::ImportTheme(PathBuf::from(theme));
|
||||
}
|
||||
// @! Ordinary mode
|
||||
// Remote argument
|
||||
if let Some(remote) = extra_args.get(0) {
|
||||
if let Some(remote) = args.positional.get(0) {
|
||||
// Parse address
|
||||
match utils::parser::parse_remote_opt(remote) {
|
||||
Ok(host_opts) => {
|
||||
match utils::parser::parse_remote_opt(remote.as_str()) {
|
||||
Ok(mut remote) => {
|
||||
// If password is provided, set password
|
||||
if let Some(passwd) = args.password {
|
||||
remote = remote.password(Some(passwd));
|
||||
}
|
||||
// Set params
|
||||
address = Some(host_opts.hostname);
|
||||
port = host_opts.port;
|
||||
protocol = host_opts.protocol;
|
||||
username = host_opts.username;
|
||||
remote_wrkdir = host_opts.wrkdir;
|
||||
run_opts.remote = Some(remote);
|
||||
// In this case the first activity will be FileTransfer
|
||||
run_opts.task = Task::Activity(NextActivity::FileTransfer);
|
||||
}
|
||||
Err(err) => {
|
||||
eprintln!("Bad address option: {}", err);
|
||||
print_usage(opts);
|
||||
std::process::exit(255);
|
||||
return Err(format!("Bad address option: {}", err));
|
||||
}
|
||||
}
|
||||
}
|
||||
// Local directory
|
||||
if let Some(localdir) = extra_args.get(1) {
|
||||
if let Some(localdir) = args.positional.get(1) {
|
||||
// Change working directory if local dir is set
|
||||
let localdir: PathBuf = PathBuf::from(localdir);
|
||||
if let Err(err) = env::set_current_dir(localdir.as_path()) {
|
||||
eprintln!("Bad working directory argument: {}", err);
|
||||
std::process::exit(255);
|
||||
return Err(format!("Bad working directory argument: {}", err));
|
||||
}
|
||||
}
|
||||
// Get working directory
|
||||
let wrkdir: PathBuf = match env::current_dir() {
|
||||
Ok(dir) => dir,
|
||||
Err(_) => PathBuf::from("/"),
|
||||
};
|
||||
Ok(run_opts)
|
||||
}
|
||||
|
||||
/// ### read_password
|
||||
///
|
||||
/// Read password from tty if address is specified
|
||||
fn read_password(run_opts: &mut RunOpts) -> Result<(), String> {
|
||||
// Initialize client if necessary
|
||||
let mut start_activity: NextActivity = NextActivity::Authentication;
|
||||
if address.is_some() {
|
||||
if password.is_none() {
|
||||
if let Some(remote) = run_opts.remote.as_mut() {
|
||||
debug!("User has specified remote options: address: {:?}, port: {:?}, protocol: {:?}, user: {:?}, password: {}", remote.address, remote.port, remote.protocol, remote.username, utils::fmt::shadow_password(remote.password.as_deref().unwrap_or("")));
|
||||
if remote.password.is_none() {
|
||||
// Ask password if unspecified
|
||||
password = match rpassword::read_password_from_tty(Some("Password: ")) {
|
||||
remote.password = match rpassword::read_password_from_tty(Some("Password: ")) {
|
||||
Ok(p) => {
|
||||
if p.is_empty() {
|
||||
None
|
||||
} else {
|
||||
debug!(
|
||||
"Read password from tty: {}",
|
||||
utils::fmt::shadow_password(p.as_str())
|
||||
);
|
||||
Some(p)
|
||||
}
|
||||
}
|
||||
Err(_) => {
|
||||
eprintln!("Could not read password from prompt");
|
||||
std::process::exit(255);
|
||||
return Err("Could not read password from prompt".to_string());
|
||||
}
|
||||
};
|
||||
}
|
||||
// In this case the first activity will be FileTransfer
|
||||
start_activity = NextActivity::FileTransfer;
|
||||
}
|
||||
// Create activity manager (and context too)
|
||||
let mut manager: ActivityManager = match ActivityManager::new(&wrkdir, ticks) {
|
||||
Ok(m) => m,
|
||||
Err(err) => {
|
||||
eprintln!("Could not start activity manager: {}", err);
|
||||
std::process::exit(255);
|
||||
}
|
||||
};
|
||||
// Set file transfer params if set
|
||||
if let Some(address) = address {
|
||||
manager.set_filetransfer_params(address, port, protocol, username, password, remote_wrkdir);
|
||||
}
|
||||
// Run
|
||||
manager.run(start_activity);
|
||||
// Then return
|
||||
std::process::exit(0);
|
||||
Ok(())
|
||||
}
|
||||
|
||||
/// ### run
|
||||
///
|
||||
/// Run task and return rc
|
||||
fn run(mut run_opts: RunOpts) -> i32 {
|
||||
match run_opts.task {
|
||||
Task::ImportTheme(theme) => match support::import_theme(theme.as_path()) {
|
||||
Ok(_) => {
|
||||
println!("Theme has been successfully imported!");
|
||||
0
|
||||
}
|
||||
Err(err) => {
|
||||
eprintln!("{}", err);
|
||||
1
|
||||
}
|
||||
},
|
||||
Task::Activity(activity) => {
|
||||
// Get working directory
|
||||
let wrkdir: PathBuf = match env::current_dir() {
|
||||
Ok(dir) => dir,
|
||||
Err(_) => PathBuf::from("/"),
|
||||
};
|
||||
// Create activity manager (and context too)
|
||||
let mut manager: ActivityManager =
|
||||
match ActivityManager::new(wrkdir.as_path(), run_opts.ticks) {
|
||||
Ok(m) => m,
|
||||
Err(err) => {
|
||||
eprintln!("Could not start activity manager: {}", err);
|
||||
return 1;
|
||||
}
|
||||
};
|
||||
// Set file transfer params if set
|
||||
if let Some(remote) = run_opts.remote.take() {
|
||||
manager.set_filetransfer_params(remote);
|
||||
}
|
||||
manager.run(activity);
|
||||
0
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
68
src/support.rs
Normal file
@@ -0,0 +1,68 @@
|
||||
//! ## Support
|
||||
//!
|
||||
//! this module exposes some extra run modes for termscp, meant to be used for "support", such as installing themes
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// mod
|
||||
use crate::system::{environment, theme_provider::ThemeProvider};
|
||||
use std::fs;
|
||||
use std::path::{Path, PathBuf};
|
||||
|
||||
/// ### import_theme
|
||||
///
|
||||
/// Import theme at provided path into termscp
|
||||
pub fn import_theme(p: &Path) -> Result<(), String> {
|
||||
if !p.exists() {
|
||||
return Err(String::from(
|
||||
"Could not import theme: No such file or directory",
|
||||
));
|
||||
}
|
||||
// Validate theme file
|
||||
ThemeProvider::new(p).map_err(|e| format!("Invalid theme error: {}", e))?;
|
||||
// get config dir
|
||||
let cfg_dir: PathBuf = get_config_dir()?;
|
||||
// Get theme directory
|
||||
let theme_file: PathBuf = environment::get_theme_path(cfg_dir.as_path());
|
||||
// Copy theme to theme_dir
|
||||
fs::copy(p, theme_file.as_path())
|
||||
.map(|_| ())
|
||||
.map_err(|e| format!("Could not import theme: {}", e))
|
||||
}
|
||||
|
||||
/// ### get_config_dir
|
||||
///
|
||||
/// Get configuration directory
|
||||
fn get_config_dir() -> Result<PathBuf, String> {
|
||||
match environment::init_config_dir() {
|
||||
Ok(Some(config_dir)) => Ok(config_dir),
|
||||
Ok(None) => Err(String::from(
|
||||
"Your system doesn't provide a configuration directory",
|
||||
)),
|
||||
Err(err) => Err(format!(
|
||||
"Could not initialize configuration directory: {}",
|
||||
err
|
||||
)),
|
||||
}
|
||||
}
|
||||
@@ -25,15 +25,15 @@
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// Deps
|
||||
extern crate whoami;
|
||||
// Crate
|
||||
#[cfg(any(target_os = "windows", target_os = "macos"))]
|
||||
#[cfg(feature = "with-keyring")]
|
||||
use super::keys::keyringstorage::KeyringStorage;
|
||||
use super::keys::{filestorage::FileStorage, KeyStorage, KeyStorageError};
|
||||
// Local
|
||||
use crate::bookmarks::serializer::BookmarkSerializer;
|
||||
use crate::bookmarks::{Bookmark, SerializerError, SerializerErrorKind, UserHosts};
|
||||
use crate::config::{
|
||||
bookmarks::{Bookmark, UserHosts},
|
||||
serialization::{deserialize, serialize, SerializerError, SerializerErrorKind},
|
||||
};
|
||||
use crate::filetransfer::FileTransferProtocol;
|
||||
use crate::utils::crypto;
|
||||
use crate::utils::fmt::fmt_time;
|
||||
@@ -67,10 +67,12 @@ impl BookmarksClient {
|
||||
recents_size: usize,
|
||||
) -> Result<BookmarksClient, SerializerError> {
|
||||
// Create default hosts
|
||||
let default_hosts: UserHosts = Default::default();
|
||||
// Make a key storage (windows / macos)
|
||||
#[cfg(any(target_os = "windows", target_os = "macos"))]
|
||||
let default_hosts: UserHosts = UserHosts::default();
|
||||
debug!("Setting up bookmarks client...");
|
||||
// Make a key storage (with-keyring)
|
||||
#[cfg(feature = "with-keyring")]
|
||||
let (key_storage, service_id): (Box<dyn KeyStorage>, &str) = {
|
||||
debug!("Setting up KeyStorage");
|
||||
let username: String = whoami::username();
|
||||
let storage: KeyringStorage = KeyringStorage::new(username.as_str());
|
||||
// Check if keyring storage is supported
|
||||
@@ -79,29 +81,41 @@ impl BookmarksClient {
|
||||
#[cfg(test)] // NOTE: when running test, add -test
|
||||
let app_name: &str = "termscp-test";
|
||||
match storage.is_supported() {
|
||||
true => (Box::new(storage), app_name),
|
||||
false => (Box::new(FileStorage::new(storage_path)), "bookmarks"),
|
||||
true => {
|
||||
debug!("Using KeyringStorage");
|
||||
(Box::new(storage), app_name)
|
||||
}
|
||||
false => {
|
||||
warn!("KeyringStorage is not supported; using FileStorage");
|
||||
(Box::new(FileStorage::new(storage_path)), "bookmarks")
|
||||
}
|
||||
}
|
||||
};
|
||||
// Make a key storage (linux / unix)
|
||||
#[cfg(any(target_os = "linux", target_os = "unix"))]
|
||||
// Make a key storage (wno-keyring)
|
||||
#[cfg(not(feature = "with-keyring"))]
|
||||
let (key_storage, service_id): (Box<dyn KeyStorage>, &str) = {
|
||||
#[cfg(not(test))]
|
||||
let app_name: &str = "bookmarks";
|
||||
#[cfg(test)] // NOTE: when running test, add -test
|
||||
let app_name: &str = "bookmarks-test";
|
||||
debug!("Using FileStorage");
|
||||
(Box::new(FileStorage::new(storage_path)), app_name)
|
||||
};
|
||||
// Load key
|
||||
let key: String = match key_storage.get_key(service_id) {
|
||||
Ok(k) => k,
|
||||
Ok(k) => {
|
||||
debug!("Key loaded with success");
|
||||
k
|
||||
}
|
||||
Err(e) => match e {
|
||||
KeyStorageError::NoSuchKey => {
|
||||
// If no such key, generate key and set it into the storage
|
||||
let key: String = Self::generate_key();
|
||||
debug!("Key doesn't exist yet or could not be loaded; generated a new key");
|
||||
if let Err(e) = key_storage.set_key(service_id, key.as_str()) {
|
||||
error!("Failed to set new key into storage: {}", e);
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::IoError,
|
||||
SerializerErrorKind::Io,
|
||||
format!("Could not write key to storage: {}", e),
|
||||
));
|
||||
}
|
||||
@@ -109,10 +123,11 @@ impl BookmarksClient {
|
||||
key
|
||||
}
|
||||
_ => {
|
||||
error!("Failed to get key from storage: {}", e);
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::IoError,
|
||||
SerializerErrorKind::Io,
|
||||
format!("Could not get key from storage: {}", e),
|
||||
))
|
||||
));
|
||||
}
|
||||
},
|
||||
};
|
||||
@@ -124,15 +139,19 @@ impl BookmarksClient {
|
||||
};
|
||||
// If bookmark file doesn't exist, initialize it
|
||||
if !bookmarks_file.exists() {
|
||||
info!("Bookmarks file doesn't exist yet; creating it...");
|
||||
if let Err(err) = client.write_bookmarks() {
|
||||
error!("Failed to create bookmarks file: {}", err);
|
||||
return Err(err);
|
||||
}
|
||||
} else {
|
||||
// Load bookmarks from file
|
||||
if let Err(err) = client.read_bookmarks() {
|
||||
error!("Failed to load bookmarks: {}", err);
|
||||
return Err(err);
|
||||
}
|
||||
}
|
||||
info!("Bookmarks client initialized");
|
||||
// Load key
|
||||
Ok(client)
|
||||
}
|
||||
@@ -152,19 +171,29 @@ impl BookmarksClient {
|
||||
key: &str,
|
||||
) -> Option<(String, u16, FileTransferProtocol, String, Option<String>)> {
|
||||
let entry: &Bookmark = self.hosts.bookmarks.get(key)?;
|
||||
debug!("Getting bookmark {}", key);
|
||||
Some((
|
||||
entry.address.clone(),
|
||||
entry.port,
|
||||
match FileTransferProtocol::from_str(entry.protocol.as_str()) {
|
||||
Ok(proto) => proto,
|
||||
Err(_) => FileTransferProtocol::Sftp, // Default
|
||||
Err(err) => {
|
||||
error!(
|
||||
"Found invalid protocol in bookmarks: {}; defaulting to SFTP",
|
||||
err
|
||||
);
|
||||
FileTransferProtocol::Sftp // Default
|
||||
}
|
||||
},
|
||||
entry.username.clone(),
|
||||
match &entry.password {
|
||||
// Decrypted password if Some; if decryption fails return None
|
||||
Some(pwd) => match self.decrypt_str(pwd.as_str()) {
|
||||
Ok(decrypted_pwd) => Some(decrypted_pwd),
|
||||
Err(_) => None,
|
||||
Err(err) => {
|
||||
error!("Failed to decrypt password for bookmark: {}", err);
|
||||
None
|
||||
}
|
||||
},
|
||||
None => None,
|
||||
},
|
||||
@@ -184,9 +213,11 @@ impl BookmarksClient {
|
||||
password: Option<String>,
|
||||
) {
|
||||
if name.is_empty() {
|
||||
error!("Fatal error; bookmark name is empty");
|
||||
panic!("Bookmark name can't be empty");
|
||||
}
|
||||
// Make bookmark
|
||||
info!("Added bookmark {} with address {}", name, addr);
|
||||
let host: Bookmark = self.make_bookmark(addr, port, protocol, username, password);
|
||||
self.hosts.bookmarks.insert(name, host);
|
||||
}
|
||||
@@ -196,6 +227,7 @@ impl BookmarksClient {
|
||||
/// Delete entry from bookmarks
|
||||
pub fn del_bookmark(&mut self, name: &str) {
|
||||
let _ = self.hosts.bookmarks.remove(name);
|
||||
info!("Removed bookmark {}", name);
|
||||
}
|
||||
/// ### iter_recents
|
||||
///
|
||||
@@ -209,13 +241,20 @@ impl BookmarksClient {
|
||||
/// Get recent associated to key
|
||||
pub fn get_recent(&self, key: &str) -> Option<(String, u16, FileTransferProtocol, String)> {
|
||||
// NOTE: password is not decrypted; recents will never have password
|
||||
info!("Getting bookmark {}", key);
|
||||
let entry: &Bookmark = self.hosts.recents.get(key)?;
|
||||
Some((
|
||||
entry.address.clone(),
|
||||
entry.port,
|
||||
match FileTransferProtocol::from_str(entry.protocol.as_str()) {
|
||||
Ok(proto) => proto,
|
||||
Err(_) => FileTransferProtocol::Sftp, // Default
|
||||
Err(err) => {
|
||||
error!(
|
||||
"Found invalid protocol in bookmarks: {}; defaulting to SFTP",
|
||||
err
|
||||
);
|
||||
FileTransferProtocol::Sftp // Default
|
||||
}
|
||||
},
|
||||
entry.username.clone(),
|
||||
))
|
||||
@@ -236,6 +275,7 @@ impl BookmarksClient {
|
||||
// Check if duplicated
|
||||
for recent_host in self.hosts.recents.values() {
|
||||
if *recent_host == host {
|
||||
debug!("Discarding recent since duplicated ({})", host.address);
|
||||
// Don't save duplicates
|
||||
return;
|
||||
}
|
||||
@@ -252,6 +292,7 @@ impl BookmarksClient {
|
||||
// Delete keys starting from the last one
|
||||
for key in keys.iter() {
|
||||
let _ = self.hosts.recents.remove(key);
|
||||
debug!("Removed recent bookmark {}", key);
|
||||
// If length is < self.recents_size; break
|
||||
if self.hosts.recents.len() < self.recents_size {
|
||||
break;
|
||||
@@ -259,6 +300,7 @@ impl BookmarksClient {
|
||||
}
|
||||
}
|
||||
let name: String = fmt_time(SystemTime::now(), "ISO%Y%m%dT%H%M%S");
|
||||
info!("Saved recent host {} ({})", name, host.address);
|
||||
self.hosts.recents.insert(name, host);
|
||||
}
|
||||
|
||||
@@ -267,6 +309,7 @@ impl BookmarksClient {
|
||||
/// Delete entry from recents
|
||||
pub fn del_recent(&mut self, name: &str) {
|
||||
let _ = self.hosts.recents.remove(name);
|
||||
info!("Removed recent host {}", name);
|
||||
}
|
||||
|
||||
/// ### write_bookmarks
|
||||
@@ -274,20 +317,21 @@ impl BookmarksClient {
|
||||
/// Write bookmarks to file
|
||||
pub fn write_bookmarks(&self) -> Result<(), SerializerError> {
|
||||
// Open file
|
||||
debug!("Writing bookmarks");
|
||||
match OpenOptions::new()
|
||||
.create(true)
|
||||
.write(true)
|
||||
.truncate(true)
|
||||
.open(self.bookmarks_file.as_path())
|
||||
{
|
||||
Ok(writer) => {
|
||||
let serializer: BookmarkSerializer = BookmarkSerializer {};
|
||||
serializer.serialize(Box::new(writer), &self.hosts)
|
||||
Ok(writer) => serialize(&self.hosts, Box::new(writer)),
|
||||
Err(err) => {
|
||||
error!("Failed to write bookmarks: {}", err);
|
||||
Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Io,
|
||||
err.to_string(),
|
||||
))
|
||||
}
|
||||
Err(err) => Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::IoError,
|
||||
err.to_string(),
|
||||
)),
|
||||
}
|
||||
}
|
||||
|
||||
@@ -296,14 +340,14 @@ impl BookmarksClient {
|
||||
/// Read bookmarks from file
|
||||
fn read_bookmarks(&mut self) -> Result<(), SerializerError> {
|
||||
// Open bookmarks file for read
|
||||
debug!("Reading bookmarks");
|
||||
match OpenOptions::new()
|
||||
.read(true)
|
||||
.open(self.bookmarks_file.as_path())
|
||||
{
|
||||
Ok(reader) => {
|
||||
// Deserialize
|
||||
let deserializer: BookmarkSerializer = BookmarkSerializer {};
|
||||
match deserializer.deserialize(Box::new(reader)) {
|
||||
match deserialize(Box::new(reader)) {
|
||||
Ok(hosts) => {
|
||||
self.hosts = hosts;
|
||||
Ok(())
|
||||
@@ -311,10 +355,13 @@ impl BookmarksClient {
|
||||
Err(err) => Err(err),
|
||||
}
|
||||
}
|
||||
Err(err) => Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::IoError,
|
||||
err.to_string(),
|
||||
)),
|
||||
Err(err) => {
|
||||
error!("Failed to read bookmarks: {}", err);
|
||||
Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Io,
|
||||
err.to_string(),
|
||||
))
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
@@ -360,7 +407,7 @@ impl BookmarksClient {
|
||||
match crypto::aes128_b64_decrypt(self.key.as_str(), secret) {
|
||||
Ok(txt) => Ok(txt),
|
||||
Err(err) => Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::SyntaxError,
|
||||
SerializerErrorKind::Syntax,
|
||||
err.to_string(),
|
||||
)),
|
||||
}
|
||||
@@ -372,13 +419,16 @@ impl BookmarksClient {
|
||||
mod tests {
|
||||
|
||||
use super::*;
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
use std::thread::sleep;
|
||||
use std::time::Duration;
|
||||
use tempfile::TempDir;
|
||||
|
||||
#[test]
|
||||
|
||||
fn test_system_bookmarks_new() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: tempfile::TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
// Initialize a new bookmarks client
|
||||
let client: BookmarksClient =
|
||||
@@ -392,7 +442,12 @@ mod tests {
|
||||
}
|
||||
|
||||
#[test]
|
||||
#[cfg(any(target_os = "unix", target_os = "linux"))]
|
||||
#[cfg(any(
|
||||
target_os = "linux",
|
||||
target_os = "freebsd",
|
||||
target_os = "netbsd",
|
||||
target_os = "openbsd"
|
||||
))]
|
||||
fn test_system_bookmarks_new_err() {
|
||||
assert!(BookmarksClient::new(
|
||||
Path::new("/tmp/oifoif/omar"),
|
||||
@@ -401,7 +456,7 @@ mod tests {
|
||||
)
|
||||
.is_err());
|
||||
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: tempfile::TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, _): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
assert!(
|
||||
BookmarksClient::new(cfg_path.as_path(), Path::new("/tmp/efnnu/omar"), 16).is_err()
|
||||
@@ -411,7 +466,7 @@ mod tests {
|
||||
#[test]
|
||||
|
||||
fn test_system_bookmarks_new_from_existing() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: tempfile::TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
// Initialize a new bookmarks client
|
||||
let mut client: BookmarksClient =
|
||||
@@ -457,7 +512,7 @@ mod tests {
|
||||
#[test]
|
||||
|
||||
fn test_system_bookmarks_manipulate_bookmarks() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: tempfile::TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
// Initialize a new bookmarks client
|
||||
let mut client: BookmarksClient =
|
||||
@@ -503,7 +558,7 @@ mod tests {
|
||||
#[should_panic]
|
||||
|
||||
fn test_system_bookmarks_bad_bookmark_name() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: tempfile::TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
// Initialize a new bookmarks client
|
||||
let mut client: BookmarksClient =
|
||||
@@ -522,7 +577,7 @@ mod tests {
|
||||
#[test]
|
||||
|
||||
fn test_system_bookmarks_manipulate_recents() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: tempfile::TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
// Initialize a new bookmarks client
|
||||
let mut client: BookmarksClient =
|
||||
@@ -557,7 +612,7 @@ mod tests {
|
||||
#[test]
|
||||
|
||||
fn test_system_bookmarks_dup_recent() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: tempfile::TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
// Initialize a new bookmarks client
|
||||
let mut client: BookmarksClient =
|
||||
@@ -582,7 +637,7 @@ mod tests {
|
||||
#[test]
|
||||
|
||||
fn test_system_bookmarks_recents_more_than_limit() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: tempfile::TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
// Initialize a new bookmarks client
|
||||
let mut client: BookmarksClient =
|
||||
@@ -628,9 +683,8 @@ mod tests {
|
||||
|
||||
#[test]
|
||||
#[should_panic]
|
||||
|
||||
fn test_system_bookmarks_add_bookmark_empty() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: tempfile::TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
// Initialize a new bookmarks client
|
||||
let mut client: BookmarksClient =
|
||||
@@ -646,22 +700,28 @@ mod tests {
|
||||
);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_system_bookmarks_decrypt_str() {
|
||||
let tmp_dir: tempfile::TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
// Initialize a new bookmarks client
|
||||
let mut client: BookmarksClient =
|
||||
BookmarksClient::new(cfg_path.as_path(), key_path.as_path(), 16).unwrap();
|
||||
client.key = "MYSUPERSECRETKEY".to_string();
|
||||
assert_eq!(
|
||||
client.decrypt_str("z4Z6LpcpYqBW4+bkIok+5A==").ok().unwrap(),
|
||||
"Hello world!"
|
||||
);
|
||||
assert!(client.decrypt_str("bidoof").is_err());
|
||||
}
|
||||
|
||||
/// ### get_paths
|
||||
///
|
||||
/// Get paths for configuration and key for bookmarks
|
||||
|
||||
fn get_paths(dir: &Path) -> (PathBuf, PathBuf) {
|
||||
let k: PathBuf = PathBuf::from(dir);
|
||||
let mut c: PathBuf = k.clone();
|
||||
c.push("bookmarks.toml");
|
||||
(c, k)
|
||||
}
|
||||
|
||||
/// ### create_tmp_dir
|
||||
///
|
||||
/// Create temporary directory
|
||||
|
||||
fn create_tmp_dir() -> tempfile::TempDir {
|
||||
tempfile::TempDir::new().ok().unwrap()
|
||||
}
|
||||
}
|
||||
|
||||
@@ -25,11 +25,11 @@
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// Deps
|
||||
extern crate rand;
|
||||
// Locals
|
||||
use crate::config::serializer::ConfigSerializer;
|
||||
use crate::config::{SerializerError, SerializerErrorKind, UserConfig};
|
||||
use crate::config::{
|
||||
params::UserConfig,
|
||||
serialization::{deserialize, serialize, SerializerError, SerializerErrorKind},
|
||||
};
|
||||
use crate::filetransfer::FileTransferProtocol;
|
||||
use crate::fs::explorer::GroupDirs;
|
||||
// Ext
|
||||
@@ -49,26 +49,34 @@ pub struct ConfigClient {
|
||||
config: UserConfig, // Configuration loaded
|
||||
config_path: PathBuf, // Configuration TOML Path
|
||||
ssh_key_dir: PathBuf, // SSH Key storage directory
|
||||
degraded: bool, // Indicates the `ConfigClient` is working in degraded mode
|
||||
}
|
||||
|
||||
impl ConfigClient {
|
||||
/// ### new
|
||||
///
|
||||
/// Instantiate a new `ConfigClient` with provided path
|
||||
pub fn new(config_path: &Path, ssh_key_dir: &Path) -> Result<ConfigClient, SerializerError> {
|
||||
pub fn new(config_path: &Path, ssh_key_dir: &Path) -> Result<Self, SerializerError> {
|
||||
// Initialize a default configuration
|
||||
let default_config: UserConfig = UserConfig::default();
|
||||
info!(
|
||||
"Setting up config client with config path {} and SSH key directory {}",
|
||||
config_path.display(),
|
||||
ssh_key_dir.display()
|
||||
);
|
||||
// Create client
|
||||
let mut client: ConfigClient = ConfigClient {
|
||||
config: default_config,
|
||||
config_path: PathBuf::from(config_path),
|
||||
ssh_key_dir: PathBuf::from(ssh_key_dir),
|
||||
degraded: false,
|
||||
};
|
||||
// If ssh key directory doesn't exist, create it
|
||||
if !ssh_key_dir.exists() {
|
||||
if let Err(err) = create_dir(ssh_key_dir) {
|
||||
error!("Failed to create SSH key dir: {}", err);
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::IoError,
|
||||
SerializerErrorKind::Io,
|
||||
format!(
|
||||
"Could not create SSH key directory \"{}\": {}",
|
||||
ssh_key_dir.display(),
|
||||
@@ -76,21 +84,40 @@ impl ConfigClient {
|
||||
),
|
||||
));
|
||||
}
|
||||
debug!("Created SSH key directory");
|
||||
}
|
||||
// If Config file doesn't exist, create it
|
||||
if !config_path.exists() {
|
||||
if let Err(err) = client.write_config() {
|
||||
error!("Couldn't create configuration file: {}", err);
|
||||
return Err(err);
|
||||
}
|
||||
debug!("Config file didn't exist; created file");
|
||||
} else {
|
||||
// otherwise Load configuration from file
|
||||
if let Err(err) = client.read_config() {
|
||||
error!("Couldn't read configuration file: {}", err);
|
||||
return Err(err);
|
||||
}
|
||||
debug!("Read configuration file");
|
||||
}
|
||||
Ok(client)
|
||||
}
|
||||
|
||||
/// ### degraded
|
||||
///
|
||||
/// Instantiate a ConfigClient in degraded mode.
|
||||
/// When in degraded mode, the configuration in use will be the default configuration
|
||||
/// and the IO operation on configuration won't be available
|
||||
pub fn degraded() -> Self {
|
||||
Self {
|
||||
config: UserConfig::default(),
|
||||
config_path: PathBuf::default(),
|
||||
ssh_key_dir: PathBuf::default(),
|
||||
degraded: true,
|
||||
}
|
||||
}
|
||||
|
||||
// Text editor
|
||||
|
||||
/// ### get_text_editor
|
||||
@@ -176,23 +203,40 @@ impl ConfigClient {
|
||||
self.config.user_interface.group_dirs = val.map(|val| val.to_string());
|
||||
}
|
||||
|
||||
/// ### get_file_fmt
|
||||
/// ### get_local_file_fmt
|
||||
///
|
||||
/// Get current file fmt
|
||||
pub fn get_file_fmt(&self) -> Option<String> {
|
||||
/// Get current file fmt for local host
|
||||
pub fn get_local_file_fmt(&self) -> Option<String> {
|
||||
self.config.user_interface.file_fmt.clone()
|
||||
}
|
||||
|
||||
/// ### set_file_fmt
|
||||
/// ### set_local_file_fmt
|
||||
///
|
||||
/// Set file fmt parameter
|
||||
pub fn set_file_fmt(&mut self, s: String) {
|
||||
/// Set file fmt parameter for local host
|
||||
pub fn set_local_file_fmt(&mut self, s: String) {
|
||||
self.config.user_interface.file_fmt = match s.is_empty() {
|
||||
true => None,
|
||||
false => Some(s),
|
||||
};
|
||||
}
|
||||
|
||||
/// ### get_remote_file_fmt
|
||||
///
|
||||
/// Get current file fmt for remote host
|
||||
pub fn get_remote_file_fmt(&self) -> Option<String> {
|
||||
self.config.user_interface.remote_file_fmt.clone()
|
||||
}
|
||||
|
||||
/// ### set_remote_file_fmt
|
||||
///
|
||||
/// Set file fmt parameter for remote host
|
||||
pub fn set_remote_file_fmt(&mut self, s: String) {
|
||||
self.config.user_interface.remote_file_fmt = match s.is_empty() {
|
||||
true => None,
|
||||
false => Some(s),
|
||||
};
|
||||
}
|
||||
|
||||
// SSH Keys
|
||||
|
||||
/// ### save_ssh_key
|
||||
@@ -206,6 +250,12 @@ impl ConfigClient {
|
||||
username: &str,
|
||||
ssh_key: &str,
|
||||
) -> Result<(), SerializerError> {
|
||||
if self.degraded {
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Generic,
|
||||
String::from("Configuration won't be saved, since in degraded mode"),
|
||||
));
|
||||
}
|
||||
let host_name: String = Self::make_ssh_host_key(host, username);
|
||||
// Get key path
|
||||
let ssh_key_path: PathBuf = {
|
||||
@@ -213,12 +263,18 @@ impl ConfigClient {
|
||||
p.push(format!("{}.key", host_name));
|
||||
p
|
||||
};
|
||||
info!(
|
||||
"Writing SSH file to {} for host {}",
|
||||
ssh_key_path.display(),
|
||||
host_name
|
||||
);
|
||||
// Write key to file
|
||||
let mut f: File = match File::create(ssh_key_path.as_path()) {
|
||||
Ok(f) => f,
|
||||
Err(err) => return Self::make_io_err(err),
|
||||
};
|
||||
if let Err(err) = f.write_all(ssh_key.as_bytes()) {
|
||||
error!("Failed to write SSH key to file: {}", err);
|
||||
return Self::make_io_err(err);
|
||||
}
|
||||
// Add host to keys
|
||||
@@ -233,7 +289,14 @@ impl ConfigClient {
|
||||
/// This operation also unlinks the key file in `ssh_key_dir`
|
||||
/// and also commits changes to configuration, to prevent incoerent data
|
||||
pub fn del_ssh_key(&mut self, host: &str, username: &str) -> Result<(), SerializerError> {
|
||||
if self.degraded {
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Generic,
|
||||
String::from("Configuration won't be saved, since in degraded mode"),
|
||||
));
|
||||
}
|
||||
// Remove key from configuration and get key path
|
||||
info!("Removing key for {}@{}", host, username);
|
||||
let key_path: PathBuf = match self
|
||||
.config
|
||||
.remote
|
||||
@@ -245,6 +308,7 @@ impl ConfigClient {
|
||||
};
|
||||
// Remove file
|
||||
if let Err(err) = remove_file(key_path.as_path()) {
|
||||
error!("Failed to remove key file {}: {}", key_path.display(), err);
|
||||
return Self::make_io_err(err);
|
||||
}
|
||||
// Commit changes to configuration
|
||||
@@ -257,6 +321,9 @@ impl ConfigClient {
|
||||
/// None is returned if key doesn't exist
|
||||
/// `std::io::Error` is returned in case it was not possible to read the key file
|
||||
pub fn get_ssh_key(&self, mkey: &str) -> std::io::Result<Option<SshHost>> {
|
||||
if self.degraded {
|
||||
return Ok(None);
|
||||
}
|
||||
// Check if Key exists
|
||||
match self.config.remote.ssh_keys.get(mkey) {
|
||||
None => Ok(None),
|
||||
@@ -282,6 +349,12 @@ impl ConfigClient {
|
||||
///
|
||||
/// Write configuration to file
|
||||
pub fn write_config(&self) -> Result<(), SerializerError> {
|
||||
if self.degraded {
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Generic,
|
||||
String::from("Configuration won't be saved, since in degraded mode"),
|
||||
));
|
||||
}
|
||||
// Open file
|
||||
match OpenOptions::new()
|
||||
.create(true)
|
||||
@@ -289,14 +362,14 @@ impl ConfigClient {
|
||||
.truncate(true)
|
||||
.open(self.config_path.as_path())
|
||||
{
|
||||
Ok(writer) => {
|
||||
let serializer: ConfigSerializer = ConfigSerializer {};
|
||||
serializer.serialize(Box::new(writer), &self.config)
|
||||
Ok(writer) => serialize(&self.config, Box::new(writer)),
|
||||
Err(err) => {
|
||||
error!("Failed to write configuration file: {}", err);
|
||||
Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Io,
|
||||
err.to_string(),
|
||||
))
|
||||
}
|
||||
Err(err) => Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::IoError,
|
||||
err.to_string(),
|
||||
)),
|
||||
}
|
||||
}
|
||||
|
||||
@@ -304,6 +377,12 @@ impl ConfigClient {
|
||||
///
|
||||
/// Read configuration from file (or reload it if already read)
|
||||
pub fn read_config(&mut self) -> Result<(), SerializerError> {
|
||||
if self.degraded {
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Generic,
|
||||
String::from("Configuration won't be loaded, since in degraded mode"),
|
||||
));
|
||||
}
|
||||
// Open bookmarks file for read
|
||||
match OpenOptions::new()
|
||||
.read(true)
|
||||
@@ -311,8 +390,7 @@ impl ConfigClient {
|
||||
{
|
||||
Ok(reader) => {
|
||||
// Deserialize
|
||||
let deserializer: ConfigSerializer = ConfigSerializer {};
|
||||
match deserializer.deserialize(Box::new(reader)) {
|
||||
match deserialize(Box::new(reader)) {
|
||||
Ok(config) => {
|
||||
self.config = config;
|
||||
Ok(())
|
||||
@@ -320,10 +398,13 @@ impl ConfigClient {
|
||||
Err(err) => Err(err),
|
||||
}
|
||||
}
|
||||
Err(err) => Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::IoError,
|
||||
err.to_string(),
|
||||
)),
|
||||
Err(err) => {
|
||||
error!("Failed to read configuration: {}", err);
|
||||
Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Io,
|
||||
err.to_string(),
|
||||
))
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
@@ -351,7 +432,7 @@ impl ConfigClient {
|
||||
/// Make serializer error from `std::io::Error`
|
||||
fn make_io_err(err: std::io::Error) -> Result<(), SerializerError> {
|
||||
Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::IoError,
|
||||
SerializerErrorKind::Io,
|
||||
err.to_string(),
|
||||
))
|
||||
}
|
||||
@@ -364,17 +445,20 @@ mod tests {
|
||||
use crate::config::UserConfig;
|
||||
use crate::utils::random::random_alphanumeric_with_len;
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
use std::io::Read;
|
||||
use tempfile::TempDir;
|
||||
|
||||
#[test]
|
||||
fn test_system_config_new() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, ssh_keys_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
let client: ConfigClient = ConfigClient::new(cfg_path.as_path(), ssh_keys_path.as_path())
|
||||
.ok()
|
||||
.unwrap();
|
||||
// Verify parameters
|
||||
let default_config: UserConfig = UserConfig::default();
|
||||
assert_eq!(client.degraded, false);
|
||||
assert_eq!(client.config.remote.ssh_keys.len(), 0);
|
||||
assert_eq!(
|
||||
client.config.user_interface.default_protocol,
|
||||
@@ -388,20 +472,34 @@ mod tests {
|
||||
assert_eq!(client.ssh_key_dir, ssh_keys_path);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_system_config_degraded() {
|
||||
let mut client: ConfigClient = ConfigClient::degraded();
|
||||
assert_eq!(client.degraded, true);
|
||||
assert_eq!(client.config_path, PathBuf::default());
|
||||
assert_eq!(client.ssh_key_dir, PathBuf::default());
|
||||
// I/O
|
||||
assert!(client.add_ssh_key("Omar", "omar", "omar").is_err());
|
||||
assert!(client.del_ssh_key("omar", "omar").is_err());
|
||||
assert!(client.get_ssh_key("omar").ok().unwrap().is_none());
|
||||
assert!(client.write_config().is_err());
|
||||
assert!(client.read_config().is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_system_config_new_err() {
|
||||
assert!(
|
||||
ConfigClient::new(Path::new("/tmp/oifoif/omar"), Path::new("/tmp/efnnu/omar"),)
|
||||
.is_err()
|
||||
);
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, _): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
assert!(ConfigClient::new(cfg_path.as_path(), Path::new("/tmp/efnnu/omar")).is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_system_config_from_existing() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
let mut client: ConfigClient = ConfigClient::new(cfg_path.as_path(), key_path.as_path())
|
||||
.ok()
|
||||
@@ -434,7 +532,7 @@ mod tests {
|
||||
|
||||
#[test]
|
||||
fn test_system_config_text_editor() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
let mut client: ConfigClient = ConfigClient::new(cfg_path.as_path(), key_path.as_path())
|
||||
.ok()
|
||||
@@ -445,7 +543,7 @@ mod tests {
|
||||
|
||||
#[test]
|
||||
fn test_system_config_default_protocol() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
let mut client: ConfigClient = ConfigClient::new(cfg_path.as_path(), key_path.as_path())
|
||||
.ok()
|
||||
@@ -459,7 +557,7 @@ mod tests {
|
||||
|
||||
#[test]
|
||||
fn test_system_config_show_hidden_files() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
let mut client: ConfigClient = ConfigClient::new(cfg_path.as_path(), key_path.as_path())
|
||||
.ok()
|
||||
@@ -470,7 +568,7 @@ mod tests {
|
||||
|
||||
#[test]
|
||||
fn test_system_config_check_for_updates() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
let mut client: ConfigClient = ConfigClient::new(cfg_path.as_path(), key_path.as_path())
|
||||
.ok()
|
||||
@@ -484,7 +582,7 @@ mod tests {
|
||||
|
||||
#[test]
|
||||
fn test_system_config_group_dirs() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
let mut client: ConfigClient = ConfigClient::new(cfg_path.as_path(), key_path.as_path())
|
||||
.ok()
|
||||
@@ -496,23 +594,41 @@ mod tests {
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_system_config_file_fmt() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
fn test_system_config_local_file_fmt() {
|
||||
let tmp_dir: TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
let mut client: ConfigClient = ConfigClient::new(cfg_path.as_path(), key_path.as_path())
|
||||
.ok()
|
||||
.unwrap();
|
||||
assert_eq!(client.get_file_fmt(), None);
|
||||
client.set_file_fmt(String::from("{NAME}"));
|
||||
assert_eq!(client.get_file_fmt().unwrap(), String::from("{NAME}"));
|
||||
assert_eq!(client.get_local_file_fmt(), None);
|
||||
client.set_local_file_fmt(String::from("{NAME}"));
|
||||
assert_eq!(client.get_local_file_fmt().unwrap(), String::from("{NAME}"));
|
||||
// Delete
|
||||
client.set_file_fmt(String::from(""));
|
||||
assert_eq!(client.get_file_fmt(), None);
|
||||
client.set_local_file_fmt(String::from(""));
|
||||
assert_eq!(client.get_local_file_fmt(), None);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_system_config_remote_file_fmt() {
|
||||
let tmp_dir: TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
let mut client: ConfigClient = ConfigClient::new(cfg_path.as_path(), key_path.as_path())
|
||||
.ok()
|
||||
.unwrap();
|
||||
assert_eq!(client.get_remote_file_fmt(), None);
|
||||
client.set_remote_file_fmt(String::from("{NAME}"));
|
||||
assert_eq!(
|
||||
client.get_remote_file_fmt().unwrap(),
|
||||
String::from("{NAME}")
|
||||
);
|
||||
// Delete
|
||||
client.set_remote_file_fmt(String::from(""));
|
||||
assert_eq!(client.get_remote_file_fmt(), None);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_system_config_ssh_keys() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: TempDir = TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
let mut client: ConfigClient = ConfigClient::new(cfg_path.as_path(), key_path.as_path())
|
||||
.ok()
|
||||
@@ -576,13 +692,6 @@ mod tests {
|
||||
(c, k)
|
||||
}
|
||||
|
||||
/// ### create_tmp_dir
|
||||
///
|
||||
/// Create temporary directory
|
||||
fn create_tmp_dir() -> tempfile::TempDir {
|
||||
tempfile::TempDir::new().ok().unwrap()
|
||||
}
|
||||
|
||||
fn get_sample_rsa_key() -> String {
|
||||
format!(
|
||||
"-----BEGIN OPENSSH PRIVATE KEY-----\n{}\n-----END OPENSSH PRIVATE KEY-----",
|
||||
|
||||
@@ -25,9 +25,6 @@
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// Deps
|
||||
extern crate dirs;
|
||||
|
||||
// Ext
|
||||
use std::path::{Path, PathBuf};
|
||||
|
||||
@@ -87,11 +84,32 @@ pub fn get_config_paths(config_dir: &Path) -> (PathBuf, PathBuf) {
|
||||
(bookmarks_file, keys_dir)
|
||||
}
|
||||
|
||||
/// ### get_log_paths
|
||||
///
|
||||
/// Returns the path for the supposed log file
|
||||
pub fn get_log_paths(config_dir: &Path) -> PathBuf {
|
||||
let mut log_file: PathBuf = PathBuf::from(config_dir);
|
||||
log_file.push("termscp.log");
|
||||
log_file
|
||||
}
|
||||
|
||||
/// ### get_theme_path
|
||||
///
|
||||
/// Get paths for theme provider
|
||||
/// Returns: path of theme.toml
|
||||
pub fn get_theme_path(config_dir: &Path) -> PathBuf {
|
||||
// Prepare paths
|
||||
let mut theme_file: PathBuf = PathBuf::from(config_dir);
|
||||
theme_file.push("theme.toml");
|
||||
theme_file
|
||||
}
|
||||
|
||||
#[cfg(test)]
|
||||
mod tests {
|
||||
|
||||
use super::*;
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
use std::fs::{File, OpenOptions};
|
||||
use std::io::Write;
|
||||
|
||||
@@ -142,4 +160,20 @@ mod tests {
|
||||
)
|
||||
);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_system_environment_get_log_paths() {
|
||||
assert_eq!(
|
||||
get_log_paths(&Path::new("/home/omar/.config/termscp/")),
|
||||
PathBuf::from("/home/omar/.config/termscp/termscp.log"),
|
||||
);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_system_environment_get_theme_path() {
|
||||
assert_eq!(
|
||||
get_theme_path(&Path::new("/home/omar/.config/termscp/")),
|
||||
PathBuf::from("/home/omar/.config/termscp/theme.toml"),
|
||||
);
|
||||
}
|
||||
}
|
||||
|
||||
@@ -125,6 +125,8 @@ mod tests {
|
||||
|
||||
use super::*;
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
|
||||
#[test]
|
||||
fn test_system_keys_filestorage_make_dir() {
|
||||
let storage: FileStorage = FileStorage::new(&Path::new("/tmp/"));
|
||||
|
||||
@@ -25,8 +25,6 @@
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// Deps
|
||||
extern crate keyring;
|
||||
// Local
|
||||
use super::{KeyStorage, KeyStorageError};
|
||||
// Ext
|
||||
@@ -39,7 +37,6 @@ pub struct KeyringStorage {
|
||||
username: String,
|
||||
}
|
||||
|
||||
#[cfg(not(tarpaulin_include))]
|
||||
impl KeyringStorage {
|
||||
/// ### new
|
||||
///
|
||||
@@ -51,7 +48,6 @@ impl KeyringStorage {
|
||||
}
|
||||
}
|
||||
|
||||
#[cfg(not(tarpaulin_include))]
|
||||
impl KeyStorage for KeyringStorage {
|
||||
/// ### get_key
|
||||
///
|
||||
@@ -68,7 +64,10 @@ impl KeyStorage for KeyringStorage {
|
||||
KeyringError::WindowsVaultError => Err(KeyStorageError::NoSuchKey),
|
||||
#[cfg(target_os = "macos")]
|
||||
KeyringError::MacOsKeychainError(_) => Err(KeyStorageError::NoSuchKey),
|
||||
_ => panic!("{}", e),
|
||||
#[cfg(target_os = "linux")]
|
||||
KeyringError::SecretServiceError(_) => Err(KeyStorageError::ProviderError),
|
||||
KeyringError::Parse(_) => Err(KeyStorageError::BadSytax),
|
||||
_ => Err(KeyStorageError::ProviderError),
|
||||
},
|
||||
}
|
||||
}
|
||||
@@ -93,17 +92,22 @@ impl KeyStorage for KeyringStorage {
|
||||
// Check what kind of error is returned
|
||||
match storage.get_password() {
|
||||
Ok(_) => true,
|
||||
#[cfg(not(target_os = "linux"))]
|
||||
Err(err) => !matches!(err, KeyringError::NoBackendFound),
|
||||
#[cfg(target_os = "linux")]
|
||||
Err(err) => !matches!(
|
||||
err,
|
||||
KeyringError::NoBackendFound | KeyringError::SecretServiceError(_)
|
||||
),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
#[cfg(test)]
|
||||
mod tests {
|
||||
|
||||
extern crate whoami;
|
||||
use super::*;
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
use whoami::username;
|
||||
|
||||
#[test]
|
||||
|
||||
@@ -27,30 +27,25 @@
|
||||
*/
|
||||
// Storages
|
||||
pub mod filestorage;
|
||||
#[cfg(any(target_os = "windows", target_os = "macos"))]
|
||||
#[cfg(feature = "with-keyring")]
|
||||
pub mod keyringstorage;
|
||||
// ext
|
||||
use thiserror::Error;
|
||||
|
||||
/// ## KeyStorageError
|
||||
///
|
||||
/// defines the error type for the `KeyStorage`
|
||||
#[derive(PartialEq, std::fmt::Debug)]
|
||||
#[derive(Debug, Error, PartialEq)]
|
||||
pub enum KeyStorageError {
|
||||
//BadKey,
|
||||
#[cfg(feature = "with-keyring")]
|
||||
#[error("Key has a bad syntax")]
|
||||
BadSytax,
|
||||
#[error("Provider service error")]
|
||||
ProviderError,
|
||||
#[error("No such key")]
|
||||
NoSuchKey,
|
||||
}
|
||||
|
||||
impl std::fmt::Display for KeyStorageError {
|
||||
fn fmt(&self, f: &mut std::fmt::Formatter) -> std::fmt::Result {
|
||||
let err: String = String::from(match &self {
|
||||
//KeyStorageError::BadKey => "Bad key syntax",
|
||||
KeyStorageError::ProviderError => "Provider service error",
|
||||
KeyStorageError::NoSuchKey => "No such key",
|
||||
});
|
||||
write!(f, "{}", err)
|
||||
}
|
||||
}
|
||||
|
||||
/// ## KeyStorage
|
||||
///
|
||||
/// this traits provides the methods to communicate and interact with the key storage.
|
||||
@@ -78,14 +73,21 @@ mod tests {
|
||||
|
||||
use super::*;
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
|
||||
#[test]
|
||||
fn test_system_keys_mod_errors() {
|
||||
#[cfg(feature = "with-keyring")]
|
||||
assert_eq!(
|
||||
format!("{}", KeyStorageError::ProviderError),
|
||||
KeyStorageError::BadSytax.to_string(),
|
||||
String::from("Key has a bad syntax")
|
||||
);
|
||||
assert_eq!(
|
||||
KeyStorageError::ProviderError.to_string(),
|
||||
String::from("Provider service error")
|
||||
);
|
||||
assert_eq!(
|
||||
format!("{}", KeyStorageError::NoSuchKey),
|
||||
KeyStorageError::NoSuchKey.to_string(),
|
||||
String::from("No such key")
|
||||
);
|
||||
}
|
||||
|
||||
72
src/system/logging.rs
Normal file
@@ -0,0 +1,72 @@
|
||||
//! ## Logging
|
||||
//!
|
||||
//! `logging` is the module which initializes the logging system for termscp
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use crate::system::environment::{get_log_paths, init_config_dir};
|
||||
use crate::utils::file::open_file;
|
||||
// ext
|
||||
use simplelog::{ConfigBuilder, LevelFilter, WriteLogger};
|
||||
use std::fs::File;
|
||||
use std::path::PathBuf;
|
||||
|
||||
/// ### init
|
||||
///
|
||||
/// Initialize logger
|
||||
pub fn init() -> Result<(), String> {
|
||||
// Init config dir
|
||||
let config_dir: PathBuf = match init_config_dir() {
|
||||
Ok(Some(p)) => p,
|
||||
Ok(None) => {
|
||||
return Err(String::from(
|
||||
"This system doesn't seem to support CONFIG_DIR",
|
||||
))
|
||||
}
|
||||
Err(err) => return Err(err),
|
||||
};
|
||||
let log_file_path: PathBuf = get_log_paths(config_dir.as_path());
|
||||
// Open log file
|
||||
let file: File = open_file(log_file_path.as_path(), true, true, false)
|
||||
.map_err(|e| format!("Failed to open file {}: {}", log_file_path.display(), e))?;
|
||||
// Prepare log config
|
||||
let config = ConfigBuilder::new()
|
||||
.set_time_format_str("%Y-%m-%dT%H:%M:%S%z")
|
||||
.build();
|
||||
// Make logger
|
||||
WriteLogger::init(LevelFilter::Trace, config, file)
|
||||
.map_err(|e| format!("Failed to initialize logger: {}", e))
|
||||
}
|
||||
|
||||
#[cfg(test)]
|
||||
mod test {
|
||||
|
||||
use super::*;
|
||||
|
||||
#[test]
|
||||
fn test_system_logging_setup() {
|
||||
assert!(init().is_ok());
|
||||
}
|
||||
}
|
||||
@@ -29,5 +29,7 @@
|
||||
pub mod bookmarks_client;
|
||||
pub mod config_client;
|
||||
pub mod environment;
|
||||
pub(crate) mod keys;
|
||||
pub(self) mod keys;
|
||||
pub mod logging;
|
||||
pub mod sshkey_storage;
|
||||
pub mod theme_provider;
|
||||
|
||||
@@ -42,6 +42,7 @@ impl SshKeyStorage {
|
||||
pub fn storage_from_config(cfg_client: &ConfigClient) -> Self {
|
||||
let mut hosts: HashMap<String, PathBuf> =
|
||||
HashMap::with_capacity(cfg_client.iter_ssh_keys().count());
|
||||
debug!("Setting up SSH key storage");
|
||||
// Iterate over keys
|
||||
for key in cfg_client.iter_ssh_keys() {
|
||||
match cfg_client.get_ssh_key(key) {
|
||||
@@ -52,8 +53,12 @@ impl SshKeyStorage {
|
||||
}
|
||||
None => continue,
|
||||
},
|
||||
Err(_) => continue,
|
||||
Err(err) => {
|
||||
error!("Failed to get SSH key for {}: {}", key, err);
|
||||
continue;
|
||||
}
|
||||
}
|
||||
info!("Got SSH key for {}", key);
|
||||
}
|
||||
// Return storage
|
||||
SshKeyStorage { hosts }
|
||||
@@ -62,6 +67,7 @@ impl SshKeyStorage {
|
||||
/// ### empty
|
||||
///
|
||||
/// Create an empty ssh key storage; used in case `ConfigClient` is not available
|
||||
#[cfg(test)]
|
||||
pub fn empty() -> Self {
|
||||
SshKeyStorage {
|
||||
hosts: HashMap::new(),
|
||||
@@ -82,19 +88,30 @@ impl SshKeyStorage {
|
||||
fn make_mapkey(host: &str, username: &str) -> String {
|
||||
format!("{}@{}", username, host)
|
||||
}
|
||||
|
||||
#[cfg(test)]
|
||||
/// ### add_key
|
||||
///
|
||||
/// Add a key to storage
|
||||
/// NOTE: available only for tests
|
||||
pub fn add_key(&mut self, host: &str, username: &str, p: PathBuf) {
|
||||
let key: String = Self::make_mapkey(host, username);
|
||||
self.hosts.insert(key, p);
|
||||
}
|
||||
}
|
||||
|
||||
#[cfg(test)]
|
||||
mod tests {
|
||||
|
||||
use super::*;
|
||||
|
||||
use crate::system::config_client::ConfigClient;
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
use std::path::Path;
|
||||
|
||||
#[test]
|
||||
fn test_system_sshkey_storage_new() {
|
||||
let tmp_dir: tempfile::TempDir = create_tmp_dir();
|
||||
let tmp_dir: tempfile::TempDir = tempfile::TempDir::new().ok().unwrap();
|
||||
let (cfg_path, key_path): (PathBuf, PathBuf) = get_paths(tmp_dir.path());
|
||||
let mut client: ConfigClient = ConfigClient::new(cfg_path.as_path(), key_path.as_path())
|
||||
.ok()
|
||||
@@ -122,6 +139,16 @@ mod tests {
|
||||
assert_eq!(storage.hosts.len(), 0);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_system_sshkey_storage_add() {
|
||||
let mut storage: SshKeyStorage = SshKeyStorage::empty();
|
||||
storage.add_key("deskichup", "veeso", PathBuf::from("/tmp/omar"));
|
||||
assert_eq!(
|
||||
*storage.resolve("deskichup", "veeso").unwrap(),
|
||||
PathBuf::from("/tmp/omar")
|
||||
);
|
||||
}
|
||||
|
||||
/// ### get_paths
|
||||
///
|
||||
/// Get paths for configuration and keys directory
|
||||
@@ -132,11 +159,4 @@ mod tests {
|
||||
c.push("config.toml");
|
||||
(c, k)
|
||||
}
|
||||
|
||||
/// ### create_tmp_dir
|
||||
///
|
||||
/// Create temporary directory
|
||||
fn create_tmp_dir() -> tempfile::TempDir {
|
||||
tempfile::TempDir::new().ok().unwrap()
|
||||
}
|
||||
}
|
||||
|
||||
246
src/system/theme_provider.rs
Normal file
@@ -0,0 +1,246 @@
|
||||
//! ## ThemeProvider
|
||||
//!
|
||||
//! `theme_provider` is the module which provides an API between the theme configuration and the system
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// Locals
|
||||
use crate::config::{
|
||||
serialization::{deserialize, serialize, SerializerError, SerializerErrorKind},
|
||||
themes::Theme,
|
||||
};
|
||||
// Ext
|
||||
use std::fs::OpenOptions;
|
||||
use std::path::{Path, PathBuf};
|
||||
use std::string::ToString;
|
||||
|
||||
/// ## ThemeProvider
|
||||
///
|
||||
/// ThemeProvider provides a high level API to communicate with the termscp theme
|
||||
pub struct ThemeProvider {
|
||||
theme: Theme, // Theme loaded
|
||||
theme_path: PathBuf, // Theme TOML Path
|
||||
degraded: bool, // Fallback mode; won't work with file system
|
||||
}
|
||||
|
||||
impl ThemeProvider {
|
||||
/// ### new
|
||||
///
|
||||
/// Instantiates a new `ThemeProvider`
|
||||
pub fn new(theme_path: &Path) -> Result<Self, SerializerError> {
|
||||
let default_theme: Theme = Theme::default();
|
||||
info!(
|
||||
"Setting up theme provider with thene path {} ",
|
||||
theme_path.display(),
|
||||
);
|
||||
// Create provider
|
||||
let mut provider: ThemeProvider = ThemeProvider {
|
||||
theme: default_theme,
|
||||
theme_path: theme_path.to_path_buf(),
|
||||
degraded: false,
|
||||
};
|
||||
// If Config file doesn't exist, create it
|
||||
if !theme_path.exists() {
|
||||
if let Err(err) = provider.save() {
|
||||
error!("Couldn't write theme file: {}", err);
|
||||
return Err(err);
|
||||
}
|
||||
debug!("Theme file didn't exist; created file");
|
||||
} else {
|
||||
// otherwise Load configuration from file
|
||||
if let Err(err) = provider.load() {
|
||||
error!("Couldn't read thene file: {}", err);
|
||||
return Err(err);
|
||||
}
|
||||
debug!("Read theme file");
|
||||
}
|
||||
Ok(provider)
|
||||
}
|
||||
|
||||
/// ### degraded
|
||||
///
|
||||
/// Create a new theme provider which won't work with file system.
|
||||
/// This is done in order to prevent a lot of `unwrap_or` on Ui
|
||||
pub fn degraded() -> Self {
|
||||
Self {
|
||||
theme: Theme::default(),
|
||||
theme_path: PathBuf::default(),
|
||||
degraded: true,
|
||||
}
|
||||
}
|
||||
|
||||
// -- getters
|
||||
|
||||
/// ### theme
|
||||
///
|
||||
/// Returns theme as reference
|
||||
pub fn theme(&self) -> &Theme {
|
||||
&self.theme
|
||||
}
|
||||
|
||||
/// ### theme_mut
|
||||
///
|
||||
/// Returns a mutable reference to the theme
|
||||
pub fn theme_mut(&mut self) -> &mut Theme {
|
||||
&mut self.theme
|
||||
}
|
||||
|
||||
// -- io
|
||||
|
||||
/// ### load
|
||||
///
|
||||
/// Load theme from file
|
||||
pub fn load(&mut self) -> Result<(), SerializerError> {
|
||||
if self.degraded {
|
||||
warn!("Configuration won't be loaded, since degraded; reloading default...");
|
||||
self.theme = Theme::default();
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Generic,
|
||||
String::from("Can't access theme file"),
|
||||
));
|
||||
}
|
||||
// Open theme file for read
|
||||
debug!("Loading theme from file...");
|
||||
match OpenOptions::new()
|
||||
.read(true)
|
||||
.open(self.theme_path.as_path())
|
||||
{
|
||||
Ok(reader) => {
|
||||
// Deserialize
|
||||
match deserialize(Box::new(reader)) {
|
||||
Ok(theme) => {
|
||||
self.theme = theme;
|
||||
Ok(())
|
||||
}
|
||||
Err(err) => Err(err),
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
error!("Failed to read theme: {}", err);
|
||||
Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Io,
|
||||
err.to_string(),
|
||||
))
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### save
|
||||
///
|
||||
/// Save theme to file
|
||||
pub fn save(&self) -> Result<(), SerializerError> {
|
||||
if self.degraded {
|
||||
warn!("Configuration won't be saved, since in degraded mode");
|
||||
return Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Generic,
|
||||
String::from("Can't access theme file"),
|
||||
));
|
||||
}
|
||||
// Open file
|
||||
debug!("Writing theme");
|
||||
match OpenOptions::new()
|
||||
.create(true)
|
||||
.write(true)
|
||||
.truncate(true)
|
||||
.open(self.theme_path.as_path())
|
||||
{
|
||||
Ok(writer) => serialize(self.theme(), Box::new(writer)),
|
||||
Err(err) => {
|
||||
error!("Failed to write theme: {}", err);
|
||||
Err(SerializerError::new_ex(
|
||||
SerializerErrorKind::Io,
|
||||
err.to_string(),
|
||||
))
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
#[cfg(test)]
|
||||
mod test {
|
||||
use super::*;
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
use tempfile::TempDir;
|
||||
use tuirealm::tui::style::Color;
|
||||
|
||||
#[test]
|
||||
fn test_system_theme_provider_new() {
|
||||
let tmp_dir: tempfile::TempDir = TempDir::new().ok().unwrap();
|
||||
let theme_path: PathBuf = get_theme_path(tmp_dir.path());
|
||||
// Initialize a new bookmarks client
|
||||
let mut provider: ThemeProvider = ThemeProvider::new(theme_path.as_path()).unwrap();
|
||||
// Verify client
|
||||
assert_eq!(provider.theme().auth_address, Color::Yellow);
|
||||
assert_eq!(provider.theme_path, theme_path);
|
||||
assert_eq!(provider.degraded, false);
|
||||
// Mutation
|
||||
provider.theme_mut().auth_address = Color::Green;
|
||||
assert_eq!(provider.theme().auth_address, Color::Green);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_system_theme_provider_load_and_save() {
|
||||
let tmp_dir: tempfile::TempDir = TempDir::new().ok().unwrap();
|
||||
let theme_path: PathBuf = get_theme_path(tmp_dir.path());
|
||||
// Initialize a new bookmarks client
|
||||
let mut provider: ThemeProvider = ThemeProvider::new(theme_path.as_path()).unwrap();
|
||||
// Write
|
||||
provider.theme_mut().auth_address = Color::Green;
|
||||
assert!(provider.save().is_ok());
|
||||
provider.theme_mut().auth_address = Color::Blue;
|
||||
// Reload
|
||||
assert!(provider.load().is_ok());
|
||||
// Unchanged
|
||||
assert_eq!(provider.theme().auth_address, Color::Green);
|
||||
// Instantiate a new provider
|
||||
let provider: ThemeProvider = ThemeProvider::new(theme_path.as_path()).unwrap();
|
||||
assert_eq!(provider.theme().auth_address, Color::Green); // Unchanged
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_system_theme_provider_degraded() {
|
||||
let mut provider: ThemeProvider = ThemeProvider::degraded();
|
||||
assert_eq!(provider.theme().auth_address, Color::Yellow);
|
||||
assert_eq!(provider.degraded, true);
|
||||
provider.theme_mut().auth_address = Color::Green;
|
||||
assert!(provider.load().is_err());
|
||||
assert_eq!(provider.theme().auth_address, Color::Yellow);
|
||||
assert!(provider.save().is_err());
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_system_theme_provider_err() {
|
||||
assert!(ThemeProvider::new(Path::new("/tmp/oifoif/omar")).is_err());
|
||||
}
|
||||
|
||||
/// ### get_theme_path
|
||||
///
|
||||
/// Get paths for theme file
|
||||
fn get_theme_path(dir: &Path) -> PathBuf {
|
||||
let mut p: PathBuf = PathBuf::from(dir);
|
||||
p.push("theme.toml");
|
||||
p
|
||||
}
|
||||
}
|
||||
@@ -25,18 +25,15 @@
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// Dependencies
|
||||
extern crate dirs;
|
||||
|
||||
// Locals
|
||||
use super::{AuthActivity, FileTransferProtocol};
|
||||
use crate::system::bookmarks_client::BookmarksClient;
|
||||
use crate::system::environment;
|
||||
use crate::ui::layout::props::PropValue;
|
||||
use crate::ui::layout::Payload;
|
||||
|
||||
// Ext
|
||||
use std::path::PathBuf;
|
||||
use tui_realm_stdlib::{input::InputPropsBuilder, radio::RadioPropsBuilder};
|
||||
use tuirealm::{Payload, PropsBuilder, Value};
|
||||
|
||||
impl AuthActivity {
|
||||
/// ### del_bookmark
|
||||
@@ -47,7 +44,7 @@ impl AuthActivity {
|
||||
// Iterate over kyes
|
||||
let name: Option<&String> = self.bookmarks_list.get(idx);
|
||||
if let Some(name) = name {
|
||||
bookmarks_cli.del_bookmark(&name);
|
||||
bookmarks_cli.del_bookmark(name);
|
||||
// Write bookmarks
|
||||
self.write_bookmarks();
|
||||
}
|
||||
@@ -63,7 +60,7 @@ impl AuthActivity {
|
||||
if let Some(bookmarks_cli) = self.bookmarks_client.as_ref() {
|
||||
// Iterate over bookmarks
|
||||
if let Some(key) = self.bookmarks_list.get(idx) {
|
||||
if let Some(bookmark) = bookmarks_cli.get_bookmark(&key) {
|
||||
if let Some(bookmark) = bookmarks_cli.get_bookmark(key) {
|
||||
// Load parameters into components
|
||||
self.load_bookmark_into_gui(
|
||||
bookmark.0, bookmark.1, bookmark.2, bookmark.3, bookmark.4,
|
||||
@@ -83,10 +80,10 @@ impl AuthActivity {
|
||||
let password: Option<String> = match save_password {
|
||||
true => match self
|
||||
.view
|
||||
.get_value(super::COMPONENT_RADIO_BOOKMARK_SAVE_PWD)
|
||||
.get_state(super::COMPONENT_RADIO_BOOKMARK_SAVE_PWD)
|
||||
{
|
||||
Some(Payload::Unsigned(0)) => Some(password), // Yes
|
||||
_ => None, // No such component / No
|
||||
Some(Payload::One(Value::Usize(0))) => Some(password), // Yes
|
||||
_ => None, // No such component / No
|
||||
},
|
||||
false => None,
|
||||
};
|
||||
@@ -107,7 +104,7 @@ impl AuthActivity {
|
||||
if let Some(client) = self.bookmarks_client.as_mut() {
|
||||
let name: Option<&String> = self.recents_list.get(idx);
|
||||
if let Some(name) = name {
|
||||
client.del_recent(&name);
|
||||
client.del_recent(name);
|
||||
// Write bookmarks
|
||||
self.write_bookmarks();
|
||||
}
|
||||
@@ -246,32 +243,29 @@ impl AuthActivity {
|
||||
password: Option<String>,
|
||||
) {
|
||||
// Load parameters into components
|
||||
if let Some(mut props) = self.view.get_props(super::COMPONENT_INPUT_ADDR) {
|
||||
let props = props.with_value(PropValue::Str(addr)).build();
|
||||
if let Some(props) = self.view.get_props(super::COMPONENT_INPUT_ADDR) {
|
||||
let props = InputPropsBuilder::from(props).with_value(addr).build();
|
||||
self.view.update(super::COMPONENT_INPUT_ADDR, props);
|
||||
}
|
||||
if let Some(mut props) = self.view.get_props(super::COMPONENT_INPUT_PORT) {
|
||||
let props = props.with_value(PropValue::Str(port.to_string())).build();
|
||||
if let Some(props) = self.view.get_props(super::COMPONENT_INPUT_PORT) {
|
||||
let props = InputPropsBuilder::from(props)
|
||||
.with_value(port.to_string())
|
||||
.build();
|
||||
self.view.update(super::COMPONENT_INPUT_PORT, props);
|
||||
}
|
||||
if let Some(mut props) = self.view.get_props(super::COMPONENT_RADIO_PROTOCOL) {
|
||||
let props = props
|
||||
.with_value(PropValue::Unsigned(match protocol {
|
||||
FileTransferProtocol::Sftp => 0,
|
||||
FileTransferProtocol::Scp => 1,
|
||||
FileTransferProtocol::Ftp(false) => 2,
|
||||
FileTransferProtocol::Ftp(true) => 3,
|
||||
}))
|
||||
if let Some(props) = self.view.get_props(super::COMPONENT_RADIO_PROTOCOL) {
|
||||
let props = RadioPropsBuilder::from(props)
|
||||
.with_value(Self::protocol_enum_to_opt(protocol))
|
||||
.build();
|
||||
self.view.update(super::COMPONENT_RADIO_PROTOCOL, props);
|
||||
}
|
||||
if let Some(mut props) = self.view.get_props(super::COMPONENT_INPUT_USERNAME) {
|
||||
let props = props.with_value(PropValue::Str(username)).build();
|
||||
if let Some(props) = self.view.get_props(super::COMPONENT_INPUT_USERNAME) {
|
||||
let props = InputPropsBuilder::from(props).with_value(username).build();
|
||||
self.view.update(super::COMPONENT_INPUT_USERNAME, props);
|
||||
}
|
||||
if let Some(password) = password {
|
||||
if let Some(mut props) = self.view.get_props(super::COMPONENT_INPUT_PASSWORD) {
|
||||
let props = props.with_value(PropValue::Str(password)).build();
|
||||
if let Some(props) = self.view.get_props(super::COMPONENT_INPUT_PASSWORD) {
|
||||
let props = InputPropsBuilder::from(props).with_value(password).build();
|
||||
self.view.update(super::COMPONENT_INPUT_PASSWORD, props);
|
||||
}
|
||||
}
|
||||
116
src/ui/activities/auth/misc.rs
Normal file
@@ -0,0 +1,116 @@
|
||||
//! ## AuthActivity
|
||||
//!
|
||||
//! `auth_activity` is the module which implements the authentication activity
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
use super::{AuthActivity, FileTransferParams, FileTransferProtocol};
|
||||
|
||||
impl AuthActivity {
|
||||
/// ### protocol_opt_to_enum
|
||||
///
|
||||
/// Convert radio index for protocol into a `FileTransferProtocol`
|
||||
pub(super) fn protocol_opt_to_enum(protocol: usize) -> FileTransferProtocol {
|
||||
match protocol {
|
||||
1 => FileTransferProtocol::Scp,
|
||||
2 => FileTransferProtocol::Ftp(false),
|
||||
3 => FileTransferProtocol::Ftp(true),
|
||||
_ => FileTransferProtocol::Sftp,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### protocol_enum_to_opt
|
||||
///
|
||||
/// Convert `FileTransferProtocol` enum into radio group index
|
||||
pub(super) fn protocol_enum_to_opt(protocol: FileTransferProtocol) -> usize {
|
||||
match protocol {
|
||||
FileTransferProtocol::Sftp => 0,
|
||||
FileTransferProtocol::Scp => 1,
|
||||
FileTransferProtocol::Ftp(false) => 2,
|
||||
FileTransferProtocol::Ftp(true) => 3,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### get_default_port_for_protocol
|
||||
///
|
||||
/// Get the default port for protocol
|
||||
pub(super) fn get_default_port_for_protocol(protocol: FileTransferProtocol) -> u16 {
|
||||
match protocol {
|
||||
FileTransferProtocol::Sftp | FileTransferProtocol::Scp => 22,
|
||||
FileTransferProtocol::Ftp(_) => 21,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### is_port_standard
|
||||
///
|
||||
/// Returns whether the port is standard or not
|
||||
pub(super) fn is_port_standard(port: u16) -> bool {
|
||||
port < 1024
|
||||
}
|
||||
|
||||
/// ### check_minimum_window_size
|
||||
///
|
||||
/// Check minimum window size window
|
||||
pub(super) fn check_minimum_window_size(&mut self, height: u16) {
|
||||
if height < 25 {
|
||||
// Mount window error
|
||||
self.mount_size_err();
|
||||
} else {
|
||||
self.umount_size_err();
|
||||
}
|
||||
}
|
||||
|
||||
/// ### collect_host_params
|
||||
///
|
||||
/// Get input values from fields or return an error if fields are invalid
|
||||
pub(super) fn collect_host_params(&self) -> Result<FileTransferParams, &'static str> {
|
||||
let (address, port, protocol, username, password): (
|
||||
String,
|
||||
u16,
|
||||
FileTransferProtocol,
|
||||
String,
|
||||
String,
|
||||
) = self.get_input();
|
||||
if address.is_empty() {
|
||||
return Err("Invalid host");
|
||||
}
|
||||
if port == 0 {
|
||||
return Err("Invalid port");
|
||||
}
|
||||
Ok(FileTransferParams {
|
||||
address,
|
||||
port,
|
||||
protocol,
|
||||
username: match username.is_empty() {
|
||||
true => None,
|
||||
false => Some(username),
|
||||
},
|
||||
password: match password.is_empty() {
|
||||
true => None,
|
||||
false => Some(password),
|
||||
},
|
||||
entry_directory: None,
|
||||
})
|
||||
}
|
||||
}
|
||||
@@ -27,30 +27,31 @@
|
||||
*/
|
||||
// Sub modules
|
||||
mod bookmarks;
|
||||
mod misc;
|
||||
mod update;
|
||||
mod view;
|
||||
|
||||
// Dependencies
|
||||
extern crate crossterm;
|
||||
extern crate tui;
|
||||
|
||||
// locals
|
||||
use super::{Activity, Context, ExitReason};
|
||||
use crate::filetransfer::FileTransferProtocol;
|
||||
use crate::config::themes::Theme;
|
||||
use crate::filetransfer::{FileTransferParams, FileTransferProtocol};
|
||||
use crate::system::bookmarks_client::BookmarksClient;
|
||||
use crate::ui::context::FileTransferParams;
|
||||
use crate::ui::layout::view::View;
|
||||
use crate::utils::git;
|
||||
|
||||
// Includes
|
||||
use crossterm::event::Event;
|
||||
use crossterm::terminal::{disable_raw_mode, enable_raw_mode};
|
||||
use tuirealm::{Update, View};
|
||||
|
||||
// -- components
|
||||
const COMPONENT_TEXT_HEADER: &str = "TEXT_HEADER";
|
||||
const COMPONENT_TEXT_H1: &str = "TEXT_H1";
|
||||
const COMPONENT_TEXT_H2: &str = "TEXT_H2";
|
||||
const COMPONENT_TEXT_NEW_VERSION: &str = "TEXT_NEW_VERSION";
|
||||
const COMPONENT_TEXT_NEW_VERSION_NOTES: &str = "TEXTAREA_NEW_VERSION";
|
||||
const COMPONENT_TEXT_FOOTER: &str = "TEXT_FOOTER";
|
||||
const COMPONENT_TEXT_HELP: &str = "TEXT_HELP";
|
||||
const COMPONENT_TEXT_ERROR: &str = "TEXT_ERROR";
|
||||
const COMPONENT_TEXT_SIZE_ERR: &str = "TEXT_SIZE_ERR";
|
||||
const COMPONENT_INPUT_ADDR: &str = "INPUT_ADDRESS";
|
||||
const COMPONENT_INPUT_PORT: &str = "INPUT_PORT";
|
||||
const COMPONENT_INPUT_USERNAME: &str = "INPUT_USERNAME";
|
||||
@@ -66,6 +67,7 @@ const COMPONENT_RECENTS_LIST: &str = "RECENTS_LIST";
|
||||
|
||||
// Store keys
|
||||
const STORE_KEY_LATEST_VERSION: &str = "AUTH_LATEST_VERSION";
|
||||
const STORE_KEY_RELEASE_NOTES: &str = "AUTH_RELEASE_NOTES";
|
||||
|
||||
/// ### AuthActivity
|
||||
///
|
||||
@@ -106,38 +108,61 @@ impl AuthActivity {
|
||||
///
|
||||
/// If enabled in configuration, check for updates from Github
|
||||
fn check_for_updates(&mut self) {
|
||||
debug!("Check for updates...");
|
||||
// Check version only if unset in the store
|
||||
let ctx: &Context = self.context.as_ref().unwrap();
|
||||
if !ctx.store.isset(STORE_KEY_LATEST_VERSION) {
|
||||
let mut new_version: Option<String> = match ctx.config_client.as_ref() {
|
||||
Some(client) => {
|
||||
if client.get_check_for_updates() {
|
||||
// Send request
|
||||
match git::check_for_updates(env!("CARGO_PKG_VERSION")) {
|
||||
Ok(version) => version,
|
||||
Err(err) => {
|
||||
// Report error
|
||||
self.mount_error(
|
||||
format!("Could not check for new updates: {}", err).as_str(),
|
||||
);
|
||||
// None
|
||||
None
|
||||
}
|
||||
}
|
||||
} else {
|
||||
None
|
||||
let ctx: &mut Context = self.context_mut();
|
||||
if !ctx.store().isset(STORE_KEY_LATEST_VERSION) {
|
||||
debug!("Version is not set in storage");
|
||||
if ctx.config().get_check_for_updates() {
|
||||
debug!("Check for updates is enabled");
|
||||
// Send request
|
||||
match git::check_for_updates(env!("CARGO_PKG_VERSION")) {
|
||||
Ok(Some(git::GithubTag { tag_name, body })) => {
|
||||
// If some, store version and release notes
|
||||
info!("Latest version is: {}", tag_name);
|
||||
ctx.store_mut()
|
||||
.set_string(STORE_KEY_LATEST_VERSION, tag_name);
|
||||
ctx.store_mut().set_string(STORE_KEY_RELEASE_NOTES, body);
|
||||
}
|
||||
Ok(None) => {
|
||||
info!("Latest version is: {} (current)", env!("CARGO_PKG_VERSION"));
|
||||
// Just set flag as check
|
||||
ctx.store_mut().set(STORE_KEY_LATEST_VERSION);
|
||||
}
|
||||
Err(err) => {
|
||||
// Report error
|
||||
error!("Failed to get latest version: {}", err);
|
||||
self.mount_error(
|
||||
format!("Could not check for new updates: {}", err).as_str(),
|
||||
);
|
||||
}
|
||||
}
|
||||
None => None,
|
||||
};
|
||||
let ctx: &mut Context = self.context.as_mut().unwrap();
|
||||
// Set version into the store (or just a flag)
|
||||
match new_version.take() {
|
||||
Some(new_version) => ctx.store.set_string(STORE_KEY_LATEST_VERSION, new_version), // If Some, set String
|
||||
None => ctx.store.set(STORE_KEY_LATEST_VERSION), // If None, just set flag
|
||||
} else {
|
||||
info!("Check for updates is disabled");
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### context
|
||||
///
|
||||
/// Returns a reference to context
|
||||
fn context(&self) -> &Context {
|
||||
self.context.as_ref().unwrap()
|
||||
}
|
||||
|
||||
/// ### context_mut
|
||||
///
|
||||
/// Returns a mutable reference to context
|
||||
fn context_mut(&mut self) -> &mut Context {
|
||||
self.context.as_mut().unwrap()
|
||||
}
|
||||
|
||||
/// ### theme
|
||||
///
|
||||
/// Returns a reference to theme
|
||||
fn theme(&self) -> &Theme {
|
||||
self.context().theme_provider().theme()
|
||||
}
|
||||
}
|
||||
|
||||
impl Activity for AuthActivity {
|
||||
@@ -147,26 +172,33 @@ impl Activity for AuthActivity {
|
||||
/// `on_create` must initialize all the data structures used by the activity
|
||||
/// Context is taken from activity manager and will be released only when activity is destroyed
|
||||
fn on_create(&mut self, mut context: Context) {
|
||||
debug!("Initializing activity");
|
||||
// Initialize file transfer params
|
||||
context.ft_params = Some(FileTransferParams::default());
|
||||
context.set_ftparams(FileTransferParams::default());
|
||||
// Set context
|
||||
self.context = Some(context);
|
||||
// Clear terminal
|
||||
self.context.as_mut().unwrap().clear_screen();
|
||||
self.context_mut().clear_screen();
|
||||
// Put raw mode on enabled
|
||||
let _ = enable_raw_mode();
|
||||
// Init bookmarks client
|
||||
if self.bookmarks_client.is_none() {
|
||||
self.init_bookmarks_client();
|
||||
}
|
||||
// Verify error state from context
|
||||
if let Some(err) = self.context.as_mut().unwrap().get_error() {
|
||||
self.mount_error(err.as_str());
|
||||
if let Err(err) = enable_raw_mode() {
|
||||
error!("Failed to enter raw mode: {}", err);
|
||||
}
|
||||
// If check for updates is enabled, check for updates
|
||||
self.check_for_updates();
|
||||
// Initialize view
|
||||
self.init();
|
||||
// Init bookmarks client
|
||||
if self.bookmarks_client.is_none() {
|
||||
self.init_bookmarks_client();
|
||||
// View bookarmsk
|
||||
self.view_bookmarks();
|
||||
self.view_recent_connections();
|
||||
}
|
||||
// Verify error state from context
|
||||
if let Some(err) = self.context_mut().error() {
|
||||
self.mount_error(err.as_str());
|
||||
}
|
||||
info!("Activity initialized");
|
||||
}
|
||||
|
||||
/// ### on_draw
|
||||
@@ -179,9 +211,13 @@ impl Activity for AuthActivity {
|
||||
return;
|
||||
}
|
||||
// Read one event
|
||||
if let Ok(Some(event)) = self.context.as_ref().unwrap().input_hnd.read_event() {
|
||||
if let Ok(Some(event)) = self.context().input_hnd().read_event() {
|
||||
// Set redraw to true
|
||||
self.redraw = true;
|
||||
// Handle on resize
|
||||
if let Event::Resize(_, h) = event {
|
||||
self.check_minimum_window_size(h);
|
||||
}
|
||||
// Handle event on view and update
|
||||
let msg = self.view.on(event);
|
||||
self.update(msg);
|
||||
@@ -211,7 +247,9 @@ impl Activity for AuthActivity {
|
||||
/// This function finally releases the context
|
||||
fn on_destroy(&mut self) -> Option<Context> {
|
||||
// Disable raw mode
|
||||
let _ = disable_raw_mode();
|
||||
if let Err(err) = disable_raw_mode() {
|
||||
error!("Failed to disable raw mode: {}", err);
|
||||
}
|
||||
self.context.as_ref()?;
|
||||
// Clear terminal and return
|
||||
match self.context.take() {
|
||||
@@ -27,126 +27,128 @@
|
||||
*/
|
||||
// locals
|
||||
use super::{
|
||||
AuthActivity, FileTransferParams, COMPONENT_BOOKMARKS_LIST, COMPONENT_INPUT_ADDR,
|
||||
AuthActivity, FileTransferProtocol, COMPONENT_BOOKMARKS_LIST, COMPONENT_INPUT_ADDR,
|
||||
COMPONENT_INPUT_BOOKMARK_NAME, COMPONENT_INPUT_PASSWORD, COMPONENT_INPUT_PORT,
|
||||
COMPONENT_INPUT_USERNAME, COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK,
|
||||
COMPONENT_RADIO_BOOKMARK_DEL_RECENT, COMPONENT_RADIO_BOOKMARK_SAVE_PWD,
|
||||
COMPONENT_RADIO_PROTOCOL, COMPONENT_RADIO_QUIT, COMPONENT_RECENTS_LIST, COMPONENT_TEXT_ERROR,
|
||||
COMPONENT_TEXT_HELP,
|
||||
COMPONENT_TEXT_HELP, COMPONENT_TEXT_NEW_VERSION_NOTES, COMPONENT_TEXT_SIZE_ERR,
|
||||
};
|
||||
use crate::ui::activities::keymap::*;
|
||||
use crate::ui::layout::{Msg, Payload};
|
||||
use crate::ui::keymap::*;
|
||||
use tui_realm_stdlib::InputPropsBuilder;
|
||||
use tuirealm::{Msg, Payload, PropsBuilder, Update, Value};
|
||||
|
||||
// -- update
|
||||
|
||||
impl AuthActivity {
|
||||
impl Update for AuthActivity {
|
||||
/// ### update
|
||||
///
|
||||
/// Update auth activity model based on msg
|
||||
/// The function exits when returns None
|
||||
pub(super) fn update(&mut self, msg: Option<(String, Msg)>) -> Option<(String, Msg)> {
|
||||
fn update(&mut self, msg: Option<(String, Msg)>) -> Option<(String, Msg)> {
|
||||
let ref_msg: Option<(&str, &Msg)> = msg.as_ref().map(|(s, msg)| (s.as_str(), msg));
|
||||
// Match msg
|
||||
match ref_msg {
|
||||
None => None, // Exit after None
|
||||
Some(msg) => match msg {
|
||||
// Focus ( DOWN )
|
||||
(COMPONENT_INPUT_ADDR, &MSG_KEY_DOWN) => {
|
||||
(COMPONENT_RADIO_PROTOCOL, key) if key == &MSG_KEY_DOWN => {
|
||||
// Give focus to port
|
||||
self.view.active(COMPONENT_INPUT_ADDR);
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_ADDR, key) if key == &MSG_KEY_DOWN => {
|
||||
// Give focus to port
|
||||
self.view.active(COMPONENT_INPUT_PORT);
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_PORT, &MSG_KEY_DOWN) => {
|
||||
// Give focus to port
|
||||
self.view.active(COMPONENT_RADIO_PROTOCOL);
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_PROTOCOL, &MSG_KEY_DOWN) => {
|
||||
(COMPONENT_INPUT_PORT, key) if key == &MSG_KEY_DOWN => {
|
||||
// Give focus to port
|
||||
self.view.active(COMPONENT_INPUT_USERNAME);
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_USERNAME, &MSG_KEY_DOWN) => {
|
||||
(COMPONENT_INPUT_USERNAME, key) if key == &MSG_KEY_DOWN => {
|
||||
// Give focus to port
|
||||
self.view.active(COMPONENT_INPUT_PASSWORD);
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_PASSWORD, &MSG_KEY_DOWN) => {
|
||||
(COMPONENT_INPUT_PASSWORD, key) if key == &MSG_KEY_DOWN => {
|
||||
// Give focus to port
|
||||
self.view.active(COMPONENT_INPUT_ADDR);
|
||||
self.view.active(COMPONENT_RADIO_PROTOCOL);
|
||||
None
|
||||
}
|
||||
// Focus ( UP )
|
||||
(COMPONENT_INPUT_PASSWORD, &MSG_KEY_UP) => {
|
||||
(COMPONENT_INPUT_PASSWORD, key) if key == &MSG_KEY_UP => {
|
||||
// Give focus to port
|
||||
self.view.active(COMPONENT_INPUT_USERNAME);
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_USERNAME, &MSG_KEY_UP) => {
|
||||
// Give focus to port
|
||||
self.view.active(COMPONENT_RADIO_PROTOCOL);
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_PROTOCOL, &MSG_KEY_UP) => {
|
||||
(COMPONENT_INPUT_USERNAME, key) if key == &MSG_KEY_UP => {
|
||||
// Give focus to port
|
||||
self.view.active(COMPONENT_INPUT_PORT);
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_PORT, &MSG_KEY_UP) => {
|
||||
(COMPONENT_INPUT_PORT, key) if key == &MSG_KEY_UP => {
|
||||
// Give focus to port
|
||||
self.view.active(COMPONENT_INPUT_ADDR);
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_ADDR, &MSG_KEY_UP) => {
|
||||
(COMPONENT_INPUT_ADDR, key) if key == &MSG_KEY_UP => {
|
||||
// Give focus to port
|
||||
self.view.active(COMPONENT_RADIO_PROTOCOL);
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_PROTOCOL, key) if key == &MSG_KEY_UP => {
|
||||
// Give focus to port
|
||||
self.view.active(COMPONENT_INPUT_PASSWORD);
|
||||
None
|
||||
}
|
||||
// <TAB> bookmarks
|
||||
(COMPONENT_BOOKMARKS_LIST, &MSG_KEY_TAB)
|
||||
| (COMPONENT_RECENTS_LIST, &MSG_KEY_TAB) => {
|
||||
// Give focus to address
|
||||
self.view.active(COMPONENT_INPUT_ADDR);
|
||||
None
|
||||
}
|
||||
// Any <TAB>, go to bookmarks
|
||||
(_, &MSG_KEY_TAB) => {
|
||||
self.view.active(COMPONENT_BOOKMARKS_LIST);
|
||||
None
|
||||
// Protocol - On Change
|
||||
(COMPONENT_RADIO_PROTOCOL, Msg::OnChange(Payload::One(Value::Usize(protocol)))) => {
|
||||
// If port is standard, update the current port with default for selected protocol
|
||||
let protocol: FileTransferProtocol = Self::protocol_opt_to_enum(*protocol);
|
||||
// Get port
|
||||
let port: u16 = self.get_input_port();
|
||||
match Self::is_port_standard(port) {
|
||||
false => None, // Return None
|
||||
true => {
|
||||
self.update_input_port(Self::get_default_port_for_protocol(protocol))
|
||||
}
|
||||
}
|
||||
}
|
||||
// Bookmarks commands
|
||||
// <RIGHT> / <LEFT>
|
||||
(COMPONENT_BOOKMARKS_LIST, &MSG_KEY_RIGHT) => {
|
||||
(COMPONENT_BOOKMARKS_LIST, key) if key == &MSG_KEY_RIGHT => {
|
||||
// Give focus to recents
|
||||
self.view.active(COMPONENT_RECENTS_LIST);
|
||||
None
|
||||
}
|
||||
(COMPONENT_RECENTS_LIST, &MSG_KEY_LEFT) => {
|
||||
(COMPONENT_RECENTS_LIST, key) if key == &MSG_KEY_LEFT => {
|
||||
// Give focus to bookmarks
|
||||
self.view.active(COMPONENT_BOOKMARKS_LIST);
|
||||
None
|
||||
}
|
||||
// <DEL | 'E'>
|
||||
(COMPONENT_BOOKMARKS_LIST, &MSG_KEY_DEL)
|
||||
| (COMPONENT_BOOKMARKS_LIST, &MSG_KEY_CHAR_E) => {
|
||||
(COMPONENT_BOOKMARKS_LIST, key)
|
||||
if key == &MSG_KEY_DEL || key == &MSG_KEY_CHAR_E =>
|
||||
{
|
||||
// Show delete popup
|
||||
self.mount_bookmark_del_dialog();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RECENTS_LIST, &MSG_KEY_DEL)
|
||||
| (COMPONENT_RECENTS_LIST, &MSG_KEY_CHAR_E) => {
|
||||
(COMPONENT_RECENTS_LIST, key) if key == &MSG_KEY_DEL || key == &MSG_KEY_CHAR_E => {
|
||||
// Show delete popup
|
||||
self.mount_recent_del_dialog();
|
||||
None
|
||||
}
|
||||
// Enter
|
||||
(COMPONENT_BOOKMARKS_LIST, Msg::OnSubmit(Payload::Unsigned(idx))) => {
|
||||
(COMPONENT_BOOKMARKS_LIST, Msg::OnSubmit(Payload::One(Value::Usize(idx)))) => {
|
||||
self.load_bookmark(*idx);
|
||||
// Give focus to input password
|
||||
self.view.active(COMPONENT_INPUT_PASSWORD);
|
||||
None
|
||||
}
|
||||
(COMPONENT_RECENTS_LIST, Msg::OnSubmit(Payload::Unsigned(idx))) => {
|
||||
(COMPONENT_RECENTS_LIST, Msg::OnSubmit(Payload::One(Value::Usize(idx)))) => {
|
||||
self.load_recent(*idx);
|
||||
// Give focus to input password
|
||||
self.view.active(COMPONENT_INPUT_PASSWORD);
|
||||
@@ -156,7 +158,7 @@ impl AuthActivity {
|
||||
// Del bookmarks
|
||||
(
|
||||
COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK,
|
||||
Msg::OnSubmit(Payload::Unsigned(index)),
|
||||
Msg::OnSubmit(Payload::One(Value::Usize(index))),
|
||||
) => {
|
||||
// hide bookmark delete
|
||||
self.umount_bookmark_del_dialog();
|
||||
@@ -164,8 +166,8 @@ impl AuthActivity {
|
||||
match *index {
|
||||
0 => {
|
||||
// Get selected bookmark
|
||||
match self.view.get_value(COMPONENT_BOOKMARKS_LIST) {
|
||||
Some(Payload::Unsigned(index)) => {
|
||||
match self.view.get_state(COMPONENT_BOOKMARKS_LIST) {
|
||||
Some(Payload::One(Value::Usize(index))) => {
|
||||
// Delete bookmark
|
||||
self.del_bookmark(index);
|
||||
// Update bookmarks
|
||||
@@ -177,15 +179,18 @@ impl AuthActivity {
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
(COMPONENT_RADIO_BOOKMARK_DEL_RECENT, Msg::OnSubmit(Payload::Unsigned(index))) => {
|
||||
(
|
||||
COMPONENT_RADIO_BOOKMARK_DEL_RECENT,
|
||||
Msg::OnSubmit(Payload::One(Value::Usize(index))),
|
||||
) => {
|
||||
// hide bookmark delete
|
||||
self.umount_recent_del_dialog();
|
||||
// Index must be 0 => YES
|
||||
match *index {
|
||||
0 => {
|
||||
// Get selected bookmark
|
||||
match self.view.get_value(COMPONENT_RECENTS_LIST) {
|
||||
Some(Payload::Unsigned(index)) => {
|
||||
match self.view.get_state(COMPONENT_RECENTS_LIST) {
|
||||
Some(Payload::One(Value::Usize(index))) => {
|
||||
// Delete recent
|
||||
self.del_recent(index);
|
||||
// Update bookmarks
|
||||
@@ -198,68 +203,68 @@ impl AuthActivity {
|
||||
}
|
||||
}
|
||||
// <ESC> hide tab
|
||||
(COMPONENT_RADIO_BOOKMARK_DEL_RECENT, &MSG_KEY_ESC) => {
|
||||
match self
|
||||
.view
|
||||
.get_props(COMPONENT_RADIO_BOOKMARK_DEL_RECENT)
|
||||
.as_mut()
|
||||
{
|
||||
Some(props) => {
|
||||
let msg = self.view.update(
|
||||
COMPONENT_RADIO_BOOKMARK_DEL_RECENT,
|
||||
props.hidden().build(),
|
||||
);
|
||||
self.update(msg)
|
||||
}
|
||||
None => None,
|
||||
}
|
||||
(COMPONENT_RADIO_BOOKMARK_DEL_RECENT, key) if key == &MSG_KEY_ESC => {
|
||||
self.umount_recent_del_dialog();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK, &MSG_KEY_ESC) => {
|
||||
match self
|
||||
.view
|
||||
.get_props(COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK)
|
||||
.as_mut()
|
||||
{
|
||||
Some(props) => {
|
||||
let msg = self.view.update(
|
||||
COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK,
|
||||
props.hidden().build(),
|
||||
);
|
||||
self.update(msg)
|
||||
}
|
||||
None => None,
|
||||
}
|
||||
(COMPONENT_RADIO_BOOKMARK_DEL_RECENT, _) => None,
|
||||
(COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK, key) if key == &MSG_KEY_ESC => {
|
||||
self.umount_bookmark_del_dialog();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK, _) => None,
|
||||
// Error message
|
||||
(COMPONENT_TEXT_ERROR, key) if key == &MSG_KEY_ESC || key == &MSG_KEY_ENTER => {
|
||||
// Umount text error
|
||||
self.umount_error();
|
||||
None
|
||||
}
|
||||
(COMPONENT_TEXT_ERROR, _) => None,
|
||||
(COMPONENT_TEXT_NEW_VERSION_NOTES, key)
|
||||
if key == &MSG_KEY_ESC || key == &MSG_KEY_ENTER =>
|
||||
{
|
||||
// Umount release notes
|
||||
self.umount_release_notes();
|
||||
None
|
||||
}
|
||||
(COMPONENT_TEXT_NEW_VERSION_NOTES, _) => None,
|
||||
// Help
|
||||
(_, &MSG_KEY_CTRL_H) => {
|
||||
(_, key) if key == &MSG_KEY_CTRL_H => {
|
||||
// Show help
|
||||
self.mount_help();
|
||||
None
|
||||
}
|
||||
(COMPONENT_TEXT_HELP, &MSG_KEY_ENTER) | (COMPONENT_TEXT_HELP, &MSG_KEY_ESC) => {
|
||||
// Release notes
|
||||
(_, key) if key == &MSG_KEY_CTRL_R => {
|
||||
// Show release notes
|
||||
self.mount_release_notes();
|
||||
None
|
||||
}
|
||||
(COMPONENT_TEXT_HELP, key) if key == &MSG_KEY_ESC || key == &MSG_KEY_ENTER => {
|
||||
// Hide text help
|
||||
self.umount_help();
|
||||
None
|
||||
}
|
||||
(COMPONENT_TEXT_HELP, _) => None,
|
||||
// Enter setup
|
||||
(_, &MSG_KEY_CTRL_C) => {
|
||||
(_, key) if key == &MSG_KEY_CTRL_C => {
|
||||
self.exit_reason = Some(super::ExitReason::EnterSetup);
|
||||
None
|
||||
}
|
||||
// Save bookmark; show popup
|
||||
(_, &MSG_KEY_CTRL_S) => {
|
||||
(_, key) if key == &MSG_KEY_CTRL_S => {
|
||||
// Show popup
|
||||
self.mount_bookmark_save_dialog();
|
||||
// Give focus to bookmark name
|
||||
self.view.active(COMPONENT_INPUT_BOOKMARK_NAME);
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_BOOKMARK_NAME, &MSG_KEY_DOWN) => {
|
||||
(COMPONENT_INPUT_BOOKMARK_NAME, key) if key == &MSG_KEY_DOWN => {
|
||||
// Give focus to pwd
|
||||
self.view.active(COMPONENT_RADIO_BOOKMARK_SAVE_PWD);
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_BOOKMARK_SAVE_PWD, &MSG_KEY_UP) => {
|
||||
(COMPONENT_RADIO_BOOKMARK_SAVE_PWD, key) if key == &MSG_KEY_UP => {
|
||||
// Give focus to pwd
|
||||
self.view.active(COMPONENT_INPUT_BOOKMARK_NAME);
|
||||
None
|
||||
@@ -269,36 +274,34 @@ impl AuthActivity {
|
||||
| (COMPONENT_RADIO_BOOKMARK_SAVE_PWD, Msg::OnSubmit(_)) => {
|
||||
// Get values
|
||||
let bookmark_name: String =
|
||||
match self.view.get_value(COMPONENT_INPUT_BOOKMARK_NAME) {
|
||||
Some(Payload::Text(s)) => s,
|
||||
match self.view.get_state(COMPONENT_INPUT_BOOKMARK_NAME) {
|
||||
Some(Payload::One(Value::Str(s))) => s,
|
||||
_ => String::new(),
|
||||
};
|
||||
let save_pwd: bool = matches!(
|
||||
self.view.get_value(COMPONENT_RADIO_BOOKMARK_SAVE_PWD),
|
||||
Some(Payload::Unsigned(0))
|
||||
self.view.get_state(COMPONENT_RADIO_BOOKMARK_SAVE_PWD),
|
||||
Some(Payload::One(Value::Usize(0)))
|
||||
);
|
||||
// Save bookmark
|
||||
self.save_bookmark(bookmark_name, save_pwd);
|
||||
if !bookmark_name.is_empty() {
|
||||
self.save_bookmark(bookmark_name, save_pwd);
|
||||
}
|
||||
// Umount popup
|
||||
self.umount_bookmark_save_dialog();
|
||||
// Reload bookmarks
|
||||
self.view_bookmarks()
|
||||
}
|
||||
// Hide save bookmark
|
||||
(COMPONENT_INPUT_BOOKMARK_NAME, &MSG_KEY_ESC)
|
||||
| (COMPONENT_RADIO_BOOKMARK_SAVE_PWD, &MSG_KEY_ESC) => {
|
||||
(COMPONENT_INPUT_BOOKMARK_NAME, key) | (COMPONENT_RADIO_BOOKMARK_SAVE_PWD, key)
|
||||
if key == &MSG_KEY_ESC =>
|
||||
{
|
||||
// Umount popup
|
||||
self.umount_bookmark_save_dialog();
|
||||
None
|
||||
}
|
||||
// Error message
|
||||
(COMPONENT_TEXT_ERROR, &MSG_KEY_ENTER) => {
|
||||
// Umount text error
|
||||
self.umount_error();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_BOOKMARK_NAME, _) | (COMPONENT_RADIO_BOOKMARK_SAVE_PWD, _) => None,
|
||||
// Quit dialog
|
||||
(COMPONENT_RADIO_QUIT, Msg::OnSubmit(Payload::Unsigned(choice))) => {
|
||||
(COMPONENT_RADIO_QUIT, Msg::OnSubmit(Payload::One(Value::Usize(choice)))) => {
|
||||
// If choice is 0, quit termscp
|
||||
if *choice == 0 {
|
||||
self.exit_reason = Some(super::ExitReason::Quit);
|
||||
@@ -306,36 +309,30 @@ impl AuthActivity {
|
||||
self.umount_quit();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_QUIT, &MSG_KEY_ESC) => {
|
||||
(COMPONENT_RADIO_QUIT, key) if key == &MSG_KEY_ESC => {
|
||||
self.umount_quit();
|
||||
None
|
||||
}
|
||||
// On submit on any unhandled (connect)
|
||||
(_, Msg::OnSubmit(_)) | (_, &MSG_KEY_ENTER) => {
|
||||
// Match <ENTER> key for all other components
|
||||
self.save_recent();
|
||||
let (address, port, protocol, username, password) = self.get_input();
|
||||
// Set file transfer params to context
|
||||
let mut ft_params: &mut FileTransferParams =
|
||||
&mut self.context.as_mut().unwrap().ft_params.as_mut().unwrap();
|
||||
ft_params.address = address;
|
||||
ft_params.port = port;
|
||||
ft_params.protocol = protocol;
|
||||
ft_params.username = match username.is_empty() {
|
||||
true => None,
|
||||
false => Some(username),
|
||||
};
|
||||
ft_params.password = match password.is_empty() {
|
||||
true => None,
|
||||
false => Some(password),
|
||||
};
|
||||
// Set exit reason
|
||||
self.exit_reason = Some(super::ExitReason::Connect);
|
||||
// Return None
|
||||
// -- text size error; block everything
|
||||
(COMPONENT_TEXT_SIZE_ERR, _) => None,
|
||||
// <TAB> bookmarks
|
||||
(COMPONENT_BOOKMARKS_LIST, key) | (COMPONENT_RECENTS_LIST, key)
|
||||
if key == &MSG_KEY_TAB =>
|
||||
{
|
||||
// Give focus to address
|
||||
self.view.active(COMPONENT_INPUT_ADDR);
|
||||
None
|
||||
}
|
||||
// Any <TAB>, go to bookmarks
|
||||
(_, key) if key == &MSG_KEY_TAB => {
|
||||
self.view.active(COMPONENT_BOOKMARKS_LIST);
|
||||
None
|
||||
}
|
||||
// On submit on any unhandled (connect)
|
||||
(_, Msg::OnSubmit(_)) => self.on_unhandled_submit(),
|
||||
(_, key) if key == &MSG_KEY_ENTER => self.on_unhandled_submit(),
|
||||
// <ESC> => Quit
|
||||
(_, &MSG_KEY_ESC) => {
|
||||
(_, key) if key == &MSG_KEY_ESC => {
|
||||
self.mount_quit();
|
||||
None
|
||||
}
|
||||
@@ -344,3 +341,36 @@ impl AuthActivity {
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
impl AuthActivity {
|
||||
fn update_input_port(&mut self, port: u16) -> Option<(String, Msg)> {
|
||||
match self.view.get_props(COMPONENT_INPUT_PORT) {
|
||||
None => None,
|
||||
Some(props) => {
|
||||
let props = InputPropsBuilder::from(props)
|
||||
.with_value(port.to_string())
|
||||
.build();
|
||||
self.view.update(COMPONENT_INPUT_PORT, props)
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
fn on_unhandled_submit(&mut self) -> Option<(String, Msg)> {
|
||||
// Validate fields
|
||||
match self.collect_host_params() {
|
||||
Err(err) => {
|
||||
// mount error
|
||||
self.mount_error(err);
|
||||
}
|
||||
Ok(params) => {
|
||||
self.save_recent();
|
||||
// Set file transfer params to context
|
||||
self.context_mut().set_ftparams(params);
|
||||
// Set exit reason
|
||||
self.exit_reason = Some(super::ExitReason::Connect);
|
||||
}
|
||||
}
|
||||
// Return None
|
||||
None
|
||||
}
|
||||
}
|
||||
795
src/ui/activities/auth/view.rs
Normal file
@@ -0,0 +1,795 @@
|
||||
//! ## AuthActivity
|
||||
//!
|
||||
//! `auth_activity` is the module which implements the authentication activity
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// Locals
|
||||
use super::{AuthActivity, Context, FileTransferProtocol};
|
||||
use crate::ui::components::bookmark_list::{BookmarkList, BookmarkListPropsBuilder};
|
||||
use crate::utils::ui::draw_area_in;
|
||||
// Ext
|
||||
use tui_realm_stdlib::{
|
||||
input::{Input, InputPropsBuilder},
|
||||
label::{Label, LabelPropsBuilder},
|
||||
list::{List, ListPropsBuilder},
|
||||
paragraph::{Paragraph, ParagraphPropsBuilder},
|
||||
radio::{Radio, RadioPropsBuilder},
|
||||
span::{Span, SpanPropsBuilder},
|
||||
textarea::{Textarea, TextareaPropsBuilder},
|
||||
};
|
||||
use tuirealm::tui::{
|
||||
layout::{Constraint, Direction, Layout},
|
||||
style::Color,
|
||||
widgets::{BorderType, Borders, Clear},
|
||||
};
|
||||
use tuirealm::{
|
||||
props::{Alignment, InputType, PropsBuilder, TableBuilder, TextSpan},
|
||||
Msg, Payload, Value,
|
||||
};
|
||||
|
||||
impl AuthActivity {
|
||||
/// ### init
|
||||
///
|
||||
/// Initialize view, mounting all startup components inside the view
|
||||
pub(super) fn init(&mut self) {
|
||||
let key_color = self.theme().misc_keys;
|
||||
let addr_color = self.theme().auth_address;
|
||||
let protocol_color = self.theme().auth_protocol;
|
||||
let port_color = self.theme().auth_port;
|
||||
let username_color = self.theme().auth_username;
|
||||
let password_color = self.theme().auth_password;
|
||||
let bookmarks_color = self.theme().auth_bookmarks;
|
||||
let recents_color = self.theme().auth_recents;
|
||||
// Headers
|
||||
self.view.mount(
|
||||
super::COMPONENT_TEXT_H1,
|
||||
Box::new(Label::new(
|
||||
LabelPropsBuilder::default()
|
||||
.bold()
|
||||
.italic()
|
||||
.with_text(String::from("$ termscp"))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
self.view.mount(
|
||||
super::COMPONENT_TEXT_H2,
|
||||
Box::new(Label::new(
|
||||
LabelPropsBuilder::default()
|
||||
.bold()
|
||||
.italic()
|
||||
.with_text(format!("$ version {}", env!("CARGO_PKG_VERSION")))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Footer
|
||||
self.view.mount(
|
||||
super::COMPONENT_TEXT_FOOTER,
|
||||
Box::new(Span::new(
|
||||
SpanPropsBuilder::default()
|
||||
.with_spans(vec![
|
||||
TextSpan::new("Press ").bold(),
|
||||
TextSpan::new("<CTRL+H>").bold().fg(key_color),
|
||||
TextSpan::new(" to show keybindings; ").bold(),
|
||||
TextSpan::new("<CTRL+C>").bold().fg(key_color),
|
||||
TextSpan::new(" to enter setup").bold(),
|
||||
])
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Get default protocol
|
||||
let default_protocol: FileTransferProtocol = self.context().config().get_default_protocol();
|
||||
// Protocol
|
||||
self.view.mount(
|
||||
super::COMPONENT_RADIO_PROTOCOL,
|
||||
Box::new(Radio::new(
|
||||
RadioPropsBuilder::default()
|
||||
.with_color(protocol_color)
|
||||
.with_inverted_color(Color::Black)
|
||||
.with_borders(Borders::ALL, BorderType::Rounded, protocol_color)
|
||||
.with_title("Protocol", Alignment::Left)
|
||||
.with_options(&["SFTP", "SCP", "FTP", "FTPS"])
|
||||
.with_value(Self::protocol_enum_to_opt(default_protocol))
|
||||
.rewind(true)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Address
|
||||
self.view.mount(
|
||||
super::COMPONENT_INPUT_ADDR,
|
||||
Box::new(Input::new(
|
||||
InputPropsBuilder::default()
|
||||
.with_foreground(addr_color)
|
||||
.with_borders(Borders::ALL, BorderType::Rounded, addr_color)
|
||||
.with_label("Remote host", Alignment::Left)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Port
|
||||
self.view.mount(
|
||||
super::COMPONENT_INPUT_PORT,
|
||||
Box::new(Input::new(
|
||||
InputPropsBuilder::default()
|
||||
.with_foreground(port_color)
|
||||
.with_borders(Borders::ALL, BorderType::Rounded, port_color)
|
||||
.with_label("Port number", Alignment::Left)
|
||||
.with_input(InputType::Number)
|
||||
.with_input_len(5)
|
||||
.with_value(Self::get_default_port_for_protocol(default_protocol).to_string())
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Username
|
||||
self.view.mount(
|
||||
super::COMPONENT_INPUT_USERNAME,
|
||||
Box::new(Input::new(
|
||||
InputPropsBuilder::default()
|
||||
.with_foreground(username_color)
|
||||
.with_borders(Borders::ALL, BorderType::Rounded, username_color)
|
||||
.with_label("Username", Alignment::Left)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Password
|
||||
self.view.mount(
|
||||
super::COMPONENT_INPUT_PASSWORD,
|
||||
Box::new(Input::new(
|
||||
InputPropsBuilder::default()
|
||||
.with_foreground(password_color)
|
||||
.with_borders(Borders::ALL, BorderType::Rounded, password_color)
|
||||
.with_label("Password", Alignment::Left)
|
||||
.with_input(InputType::Password)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Version notice
|
||||
if let Some(version) = self
|
||||
.context()
|
||||
.store()
|
||||
.get_string(super::STORE_KEY_LATEST_VERSION)
|
||||
{
|
||||
let version: String = version.to_string();
|
||||
self.view.mount(
|
||||
super::COMPONENT_TEXT_NEW_VERSION,
|
||||
Box::new(Span::new(
|
||||
SpanPropsBuilder::default()
|
||||
.with_foreground(Color::Yellow)
|
||||
.with_spans(vec![
|
||||
TextSpan::from("termscp "),
|
||||
TextSpan::new(version.as_str()).underlined().bold(),
|
||||
TextSpan::from(" is NOW available! Get it from <https://veeso.github.io/termscp/>; view release notes with <CTRL+R>"),
|
||||
])
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
}
|
||||
// Bookmarks
|
||||
self.view.mount(
|
||||
super::COMPONENT_BOOKMARKS_LIST,
|
||||
Box::new(BookmarkList::new(
|
||||
BookmarkListPropsBuilder::default()
|
||||
.with_background(bookmarks_color)
|
||||
.with_foreground(Color::Black)
|
||||
.with_borders(Borders::ALL, BorderType::Plain, bookmarks_color)
|
||||
.with_title("Bookmarks", Alignment::Left)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Recents
|
||||
self.view.mount(
|
||||
super::COMPONENT_RECENTS_LIST,
|
||||
Box::new(BookmarkList::new(
|
||||
BookmarkListPropsBuilder::default()
|
||||
.with_background(recents_color)
|
||||
.with_foreground(Color::Black)
|
||||
.with_borders(Borders::ALL, BorderType::Plain, recents_color)
|
||||
.with_title("Recent connections", Alignment::Left)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Load bookmarks
|
||||
let _ = self.view_bookmarks();
|
||||
let _ = self.view_recent_connections();
|
||||
// Active protocol
|
||||
self.view.active(super::COMPONENT_RADIO_PROTOCOL);
|
||||
}
|
||||
|
||||
/// ### view
|
||||
///
|
||||
/// Display view on canvas
|
||||
pub(super) fn view(&mut self) {
|
||||
let mut ctx: Context = self.context.take().unwrap();
|
||||
let _ = ctx.terminal().draw(|f| {
|
||||
// Check window size
|
||||
let height: u16 = f.size().height;
|
||||
self.check_minimum_window_size(height);
|
||||
// Prepare chunks
|
||||
let chunks = Layout::default()
|
||||
.direction(Direction::Vertical)
|
||||
.margin(1)
|
||||
.constraints(
|
||||
[
|
||||
Constraint::Length(21), // Auth Form
|
||||
Constraint::Min(3), // Bookmarks
|
||||
]
|
||||
.as_ref(),
|
||||
)
|
||||
.split(f.size());
|
||||
// Create explorer chunks
|
||||
let auth_chunks = Layout::default()
|
||||
.constraints(
|
||||
[
|
||||
Constraint::Length(1), // h1
|
||||
Constraint::Length(1), // h2
|
||||
Constraint::Length(1), // Version
|
||||
Constraint::Length(3), // protocol
|
||||
Constraint::Length(3), // host
|
||||
Constraint::Length(3), // port
|
||||
Constraint::Length(3), // username
|
||||
Constraint::Length(3), // password
|
||||
Constraint::Length(3), // footer
|
||||
]
|
||||
.as_ref(),
|
||||
)
|
||||
.direction(Direction::Vertical)
|
||||
.split(chunks[0]);
|
||||
// Create bookmark chunks
|
||||
let bookmark_chunks = Layout::default()
|
||||
.constraints([Constraint::Percentage(50), Constraint::Percentage(50)].as_ref())
|
||||
.direction(Direction::Horizontal)
|
||||
.split(chunks[1]);
|
||||
// Render
|
||||
// Auth chunks
|
||||
self.view
|
||||
.render(super::COMPONENT_TEXT_H1, f, auth_chunks[0]);
|
||||
self.view
|
||||
.render(super::COMPONENT_TEXT_H2, f, auth_chunks[1]);
|
||||
self.view
|
||||
.render(super::COMPONENT_TEXT_NEW_VERSION, f, auth_chunks[2]);
|
||||
self.view
|
||||
.render(super::COMPONENT_RADIO_PROTOCOL, f, auth_chunks[3]);
|
||||
self.view
|
||||
.render(super::COMPONENT_INPUT_ADDR, f, auth_chunks[4]);
|
||||
self.view
|
||||
.render(super::COMPONENT_INPUT_PORT, f, auth_chunks[5]);
|
||||
self.view
|
||||
.render(super::COMPONENT_INPUT_USERNAME, f, auth_chunks[6]);
|
||||
self.view
|
||||
.render(super::COMPONENT_INPUT_PASSWORD, f, auth_chunks[7]);
|
||||
self.view
|
||||
.render(super::COMPONENT_TEXT_FOOTER, f, auth_chunks[8]);
|
||||
// Bookmark chunks
|
||||
self.view
|
||||
.render(super::COMPONENT_BOOKMARKS_LIST, f, bookmark_chunks[0]);
|
||||
self.view
|
||||
.render(super::COMPONENT_RECENTS_LIST, f, bookmark_chunks[1]);
|
||||
// Popups
|
||||
if let Some(props) = self.view.get_props(super::COMPONENT_TEXT_ERROR) {
|
||||
if props.visible {
|
||||
let popup = draw_area_in(f.size(), 50, 10);
|
||||
f.render_widget(Clear, popup);
|
||||
// make popup
|
||||
self.view.render(super::COMPONENT_TEXT_ERROR, f, popup);
|
||||
}
|
||||
}
|
||||
if let Some(props) = self.view.get_props(super::COMPONENT_TEXT_SIZE_ERR) {
|
||||
if props.visible {
|
||||
let popup = draw_area_in(f.size(), 80, 20);
|
||||
f.render_widget(Clear, popup);
|
||||
// make popup
|
||||
self.view.render(super::COMPONENT_TEXT_SIZE_ERR, f, popup);
|
||||
}
|
||||
}
|
||||
if let Some(props) = self.view.get_props(super::COMPONENT_RADIO_QUIT) {
|
||||
if props.visible {
|
||||
// make popup
|
||||
let popup = draw_area_in(f.size(), 30, 10);
|
||||
f.render_widget(Clear, popup);
|
||||
self.view.render(super::COMPONENT_RADIO_QUIT, f, popup);
|
||||
}
|
||||
}
|
||||
if let Some(props) = self
|
||||
.view
|
||||
.get_props(super::COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK)
|
||||
{
|
||||
if props.visible {
|
||||
// make popup
|
||||
let popup = draw_area_in(f.size(), 30, 10);
|
||||
f.render_widget(Clear, popup);
|
||||
self.view
|
||||
.render(super::COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK, f, popup);
|
||||
}
|
||||
}
|
||||
if let Some(props) = self
|
||||
.view
|
||||
.get_props(super::COMPONENT_RADIO_BOOKMARK_DEL_RECENT)
|
||||
{
|
||||
if props.visible {
|
||||
// make popup
|
||||
let popup = draw_area_in(f.size(), 30, 10);
|
||||
f.render_widget(Clear, popup);
|
||||
self.view
|
||||
.render(super::COMPONENT_RADIO_BOOKMARK_DEL_RECENT, f, popup);
|
||||
}
|
||||
}
|
||||
if let Some(props) = self.view.get_props(super::COMPONENT_TEXT_NEW_VERSION_NOTES) {
|
||||
if props.visible {
|
||||
// make popup
|
||||
let popup = draw_area_in(f.size(), 90, 90);
|
||||
f.render_widget(Clear, popup);
|
||||
self.view
|
||||
.render(super::COMPONENT_TEXT_NEW_VERSION_NOTES, f, popup);
|
||||
}
|
||||
}
|
||||
if let Some(props) = self.view.get_props(super::COMPONENT_TEXT_HELP) {
|
||||
if props.visible {
|
||||
// make popup
|
||||
let popup = draw_area_in(f.size(), 50, 70);
|
||||
f.render_widget(Clear, popup);
|
||||
self.view.render(super::COMPONENT_TEXT_HELP, f, popup);
|
||||
}
|
||||
}
|
||||
if let Some(props) = self
|
||||
.view
|
||||
.get_props(super::COMPONENT_RADIO_BOOKMARK_SAVE_PWD)
|
||||
{
|
||||
if props.visible {
|
||||
// make popup
|
||||
let popup = draw_area_in(f.size(), 20, 20);
|
||||
f.render_widget(Clear, popup);
|
||||
let popup_chunks = Layout::default()
|
||||
.direction(Direction::Vertical)
|
||||
.constraints(
|
||||
[
|
||||
Constraint::Length(3), // Input form
|
||||
Constraint::Length(2), // Yes/No
|
||||
]
|
||||
.as_ref(),
|
||||
)
|
||||
.split(popup);
|
||||
self.view
|
||||
.render(super::COMPONENT_INPUT_BOOKMARK_NAME, f, popup_chunks[0]);
|
||||
self.view
|
||||
.render(super::COMPONENT_RADIO_BOOKMARK_SAVE_PWD, f, popup_chunks[1]);
|
||||
}
|
||||
}
|
||||
});
|
||||
self.context = Some(ctx);
|
||||
}
|
||||
|
||||
// -- partials
|
||||
|
||||
/// ### view_bookmarks
|
||||
///
|
||||
/// Make text span from bookmarks
|
||||
pub(super) fn view_bookmarks(&mut self) -> Option<(String, Msg)> {
|
||||
let bookmarks: Vec<String> = self
|
||||
.bookmarks_list
|
||||
.iter()
|
||||
.map(|x| {
|
||||
let entry: (String, u16, FileTransferProtocol, String, _) = self
|
||||
.bookmarks_client
|
||||
.as_ref()
|
||||
.unwrap()
|
||||
.get_bookmark(x)
|
||||
.unwrap();
|
||||
format!(
|
||||
"{} ({}://{}@{}:{})",
|
||||
x,
|
||||
entry.2.to_string().to_lowercase(),
|
||||
entry.3,
|
||||
entry.0,
|
||||
entry.1
|
||||
)
|
||||
})
|
||||
.collect();
|
||||
match self.view.get_props(super::COMPONENT_BOOKMARKS_LIST) {
|
||||
None => None,
|
||||
Some(props) => {
|
||||
let msg = self.view.update(
|
||||
super::COMPONENT_BOOKMARKS_LIST,
|
||||
BookmarkListPropsBuilder::from(props)
|
||||
.with_bookmarks(bookmarks)
|
||||
.build(),
|
||||
);
|
||||
msg
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### view_recent_connections
|
||||
///
|
||||
/// View recent connections
|
||||
pub(super) fn view_recent_connections(&mut self) -> Option<(String, Msg)> {
|
||||
let bookmarks: Vec<String> = self
|
||||
.recents_list
|
||||
.iter()
|
||||
.map(|x| {
|
||||
let entry: (String, u16, FileTransferProtocol, String) = self
|
||||
.bookmarks_client
|
||||
.as_ref()
|
||||
.unwrap()
|
||||
.get_recent(x)
|
||||
.unwrap();
|
||||
|
||||
format!(
|
||||
"{}://{}@{}:{}",
|
||||
entry.2.to_string().to_lowercase(),
|
||||
entry.3,
|
||||
entry.0,
|
||||
entry.1
|
||||
)
|
||||
})
|
||||
.collect();
|
||||
match self.view.get_props(super::COMPONENT_RECENTS_LIST) {
|
||||
None => None,
|
||||
Some(props) => {
|
||||
let msg = self.view.update(
|
||||
super::COMPONENT_RECENTS_LIST,
|
||||
BookmarkListPropsBuilder::from(props)
|
||||
.with_bookmarks(bookmarks)
|
||||
.build(),
|
||||
);
|
||||
msg
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// -- mount
|
||||
|
||||
/// ### mount_error
|
||||
///
|
||||
/// Mount error box
|
||||
pub(super) fn mount_error(&mut self, text: &str) {
|
||||
// Mount
|
||||
let err_color = self.theme().misc_error_dialog;
|
||||
self.view.mount(
|
||||
super::COMPONENT_TEXT_ERROR,
|
||||
Box::new(Paragraph::new(
|
||||
ParagraphPropsBuilder::default()
|
||||
.with_foreground(err_color)
|
||||
.with_borders(Borders::ALL, BorderType::Thick, err_color)
|
||||
.bold()
|
||||
.with_text_alignment(Alignment::Center)
|
||||
.with_texts(vec![TextSpan::from(text)])
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Give focus to error
|
||||
self.view.active(super::COMPONENT_TEXT_ERROR);
|
||||
}
|
||||
|
||||
/// ### umount_error
|
||||
///
|
||||
/// Umount error message
|
||||
pub(super) fn umount_error(&mut self) {
|
||||
self.view.umount(super::COMPONENT_TEXT_ERROR);
|
||||
}
|
||||
|
||||
/// ### mount_size_err
|
||||
///
|
||||
/// Mount size error
|
||||
pub(super) fn mount_size_err(&mut self) {
|
||||
// Mount
|
||||
let err_color = self.theme().misc_error_dialog;
|
||||
self.view.mount(
|
||||
super::COMPONENT_TEXT_SIZE_ERR,
|
||||
Box::new(Paragraph::new(
|
||||
ParagraphPropsBuilder::default()
|
||||
.with_foreground(err_color)
|
||||
.with_borders(Borders::ALL, BorderType::Thick, err_color)
|
||||
.bold()
|
||||
.with_texts(vec![TextSpan::from(
|
||||
"termscp requires at least 24 lines of height to run",
|
||||
)])
|
||||
.with_text_alignment(Alignment::Center)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Give focus to error
|
||||
self.view.active(super::COMPONENT_TEXT_SIZE_ERR);
|
||||
}
|
||||
|
||||
/// ### umount_size_err
|
||||
///
|
||||
/// Umount error size error
|
||||
pub(super) fn umount_size_err(&mut self) {
|
||||
self.view.umount(super::COMPONENT_TEXT_SIZE_ERR);
|
||||
}
|
||||
|
||||
/// ### mount_quit
|
||||
///
|
||||
/// Mount quit popup
|
||||
pub(super) fn mount_quit(&mut self) {
|
||||
// Protocol
|
||||
let quit_color = self.theme().misc_quit_dialog;
|
||||
self.view.mount(
|
||||
super::COMPONENT_RADIO_QUIT,
|
||||
Box::new(Radio::new(
|
||||
RadioPropsBuilder::default()
|
||||
.with_color(quit_color)
|
||||
.with_borders(Borders::ALL, BorderType::Rounded, quit_color)
|
||||
.with_inverted_color(Color::Black)
|
||||
.with_title("Quit termscp?", Alignment::Center)
|
||||
.with_options(&[String::from("Yes"), String::from("No")])
|
||||
.rewind(true)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
self.view.active(super::COMPONENT_RADIO_QUIT);
|
||||
}
|
||||
|
||||
/// ### umount_quit
|
||||
///
|
||||
/// Umount quit popup
|
||||
pub(super) fn umount_quit(&mut self) {
|
||||
self.view.umount(super::COMPONENT_RADIO_QUIT);
|
||||
}
|
||||
|
||||
/// ### mount_bookmark_del_dialog
|
||||
///
|
||||
/// Mount bookmark delete dialog
|
||||
pub(super) fn mount_bookmark_del_dialog(&mut self) {
|
||||
let warn_color = self.theme().misc_warn_dialog;
|
||||
self.view.mount(
|
||||
super::COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK,
|
||||
Box::new(Radio::new(
|
||||
RadioPropsBuilder::default()
|
||||
.with_color(warn_color)
|
||||
.with_inverted_color(Color::Black)
|
||||
.with_borders(Borders::ALL, BorderType::Rounded, warn_color)
|
||||
.with_title("Delete bookmark?", Alignment::Center)
|
||||
.with_options(&[String::from("Yes"), String::from("No")])
|
||||
.with_value(1)
|
||||
.rewind(true)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Active
|
||||
self.view
|
||||
.active(super::COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK);
|
||||
}
|
||||
|
||||
/// ### umount_bookmark_del_dialog
|
||||
///
|
||||
/// umount delete bookmark dialog
|
||||
pub(super) fn umount_bookmark_del_dialog(&mut self) {
|
||||
self.view
|
||||
.umount(super::COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK);
|
||||
}
|
||||
|
||||
/// ### mount_bookmark_del_dialog
|
||||
///
|
||||
/// Mount recent delete dialog
|
||||
pub(super) fn mount_recent_del_dialog(&mut self) {
|
||||
let warn_color = self.theme().misc_warn_dialog;
|
||||
self.view.mount(
|
||||
super::COMPONENT_RADIO_BOOKMARK_DEL_RECENT,
|
||||
Box::new(Radio::new(
|
||||
RadioPropsBuilder::default()
|
||||
.with_color(warn_color)
|
||||
.with_inverted_color(Color::Black)
|
||||
.with_borders(Borders::ALL, BorderType::Rounded, warn_color)
|
||||
.with_title("Delete bookmark?", Alignment::Center)
|
||||
.with_options(&[String::from("Yes"), String::from("No")])
|
||||
.with_value(1)
|
||||
.rewind(true)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Active
|
||||
self.view.active(super::COMPONENT_RADIO_BOOKMARK_DEL_RECENT);
|
||||
}
|
||||
|
||||
/// ### umount_recent_del_dialog
|
||||
///
|
||||
/// umount delete recent dialog
|
||||
pub(super) fn umount_recent_del_dialog(&mut self) {
|
||||
self.view.umount(super::COMPONENT_RADIO_BOOKMARK_DEL_RECENT);
|
||||
}
|
||||
|
||||
/// ### mount_bookmark_save_dialog
|
||||
///
|
||||
/// Mount bookmark save dialog
|
||||
pub(super) fn mount_bookmark_save_dialog(&mut self) {
|
||||
let save_color = self.theme().misc_save_dialog;
|
||||
let warn_color = self.theme().misc_warn_dialog;
|
||||
self.view.mount(
|
||||
super::COMPONENT_INPUT_BOOKMARK_NAME,
|
||||
Box::new(Input::new(
|
||||
InputPropsBuilder::default()
|
||||
.with_foreground(save_color)
|
||||
.with_label("Save bookmark as…", Alignment::Center)
|
||||
.with_borders(
|
||||
Borders::TOP | Borders::RIGHT | Borders::LEFT,
|
||||
BorderType::Rounded,
|
||||
Color::Reset,
|
||||
)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
self.view.mount(
|
||||
super::COMPONENT_RADIO_BOOKMARK_SAVE_PWD,
|
||||
Box::new(Radio::new(
|
||||
RadioPropsBuilder::default()
|
||||
.with_color(warn_color)
|
||||
.with_borders(
|
||||
Borders::BOTTOM | Borders::RIGHT | Borders::LEFT,
|
||||
BorderType::Rounded,
|
||||
Color::Reset,
|
||||
)
|
||||
.with_title("Save password?", Alignment::Center)
|
||||
.with_options(&[String::from("Yes"), String::from("No")])
|
||||
.rewind(true)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Give focus to input bookmark name
|
||||
self.view.active(super::COMPONENT_INPUT_BOOKMARK_NAME);
|
||||
}
|
||||
|
||||
/// ### umount_bookmark_save_dialog
|
||||
///
|
||||
/// Umount bookmark save dialog
|
||||
pub(super) fn umount_bookmark_save_dialog(&mut self) {
|
||||
self.view.umount(super::COMPONENT_RADIO_BOOKMARK_SAVE_PWD);
|
||||
self.view.umount(super::COMPONENT_INPUT_BOOKMARK_NAME);
|
||||
}
|
||||
|
||||
/// ### mount_help
|
||||
///
|
||||
/// Mount help
|
||||
pub(super) fn mount_help(&mut self) {
|
||||
let key_color = self.theme().misc_keys;
|
||||
self.view.mount(
|
||||
super::COMPONENT_TEXT_HELP,
|
||||
Box::new(List::new(
|
||||
ListPropsBuilder::default()
|
||||
.with_borders(Borders::ALL, BorderType::Rounded, Color::White)
|
||||
.with_highlighted_str(Some("?"))
|
||||
.with_max_scroll_step(8)
|
||||
.scrollable(true)
|
||||
.bold()
|
||||
.with_title("Help", Alignment::Center)
|
||||
.with_rows(
|
||||
TableBuilder::default()
|
||||
.add_col(TextSpan::new("<ESC>").bold().fg(key_color))
|
||||
.add_col(TextSpan::from(" Quit termscp"))
|
||||
.add_row()
|
||||
.add_col(TextSpan::new("<TAB>").bold().fg(key_color))
|
||||
.add_col(TextSpan::from(" Switch from form and bookmarks"))
|
||||
.add_row()
|
||||
.add_col(TextSpan::new("<RIGHT/LEFT>").bold().fg(key_color))
|
||||
.add_col(TextSpan::from(" Switch bookmark tab"))
|
||||
.add_row()
|
||||
.add_col(TextSpan::new("<UP/DOWN>").bold().fg(key_color))
|
||||
.add_col(TextSpan::from(" Move up/down in current tab"))
|
||||
.add_row()
|
||||
.add_col(TextSpan::new("<ENTER>").bold().fg(key_color))
|
||||
.add_col(TextSpan::from(" Connect/Load bookmark"))
|
||||
.add_row()
|
||||
.add_col(TextSpan::new("<DEL|E>").bold().fg(key_color))
|
||||
.add_col(TextSpan::from(" Delete selected bookmark"))
|
||||
.add_row()
|
||||
.add_col(TextSpan::new("<CTRL+C>").bold().fg(key_color))
|
||||
.add_col(TextSpan::from(" Enter setup"))
|
||||
.add_row()
|
||||
.add_col(TextSpan::new("<CTRL+S>").bold().fg(key_color))
|
||||
.add_col(TextSpan::from(" Save bookmark"))
|
||||
.build(),
|
||||
)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Active help
|
||||
self.view.active(super::COMPONENT_TEXT_HELP);
|
||||
}
|
||||
|
||||
/// ### umount_help
|
||||
///
|
||||
/// Umount help
|
||||
pub(super) fn umount_help(&mut self) {
|
||||
self.view.umount(super::COMPONENT_TEXT_HELP);
|
||||
}
|
||||
|
||||
/// ### mount_release_notes
|
||||
///
|
||||
/// mount release notes text area
|
||||
pub(super) fn mount_release_notes(&mut self) {
|
||||
if let Some(ctx) = self.context.as_ref() {
|
||||
if let Some(release_notes) = ctx.store().get_string(super::STORE_KEY_RELEASE_NOTES) {
|
||||
// make spans
|
||||
let spans: Vec<TextSpan> = release_notes.lines().map(TextSpan::from).collect();
|
||||
self.view.mount(
|
||||
super::COMPONENT_TEXT_NEW_VERSION_NOTES,
|
||||
Box::new(Textarea::new(
|
||||
TextareaPropsBuilder::default()
|
||||
.with_borders(Borders::ALL, BorderType::Rounded, Color::LightYellow)
|
||||
.with_title("Release notes", Alignment::Center)
|
||||
.with_texts(spans)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
self.view.active(super::COMPONENT_TEXT_NEW_VERSION_NOTES);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### umount_release_notes
|
||||
///
|
||||
/// Umount release notes text area
|
||||
pub(super) fn umount_release_notes(&mut self) {
|
||||
self.view.umount(super::COMPONENT_TEXT_NEW_VERSION_NOTES);
|
||||
}
|
||||
|
||||
/// ### get_input
|
||||
///
|
||||
/// Collect input values from view
|
||||
pub(super) fn get_input(&self) -> (String, u16, FileTransferProtocol, String, String) {
|
||||
let addr: String = self.get_input_addr();
|
||||
let port: u16 = self.get_input_port();
|
||||
let protocol: FileTransferProtocol = self.get_input_protocol();
|
||||
let username: String = self.get_input_username();
|
||||
let password: String = self.get_input_password();
|
||||
(addr, port, protocol, username, password)
|
||||
}
|
||||
|
||||
pub(super) fn get_input_addr(&self) -> String {
|
||||
match self.view.get_state(super::COMPONENT_INPUT_ADDR) {
|
||||
Some(Payload::One(Value::Str(x))) => x,
|
||||
_ => String::new(),
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn get_input_port(&self) -> u16 {
|
||||
match self.view.get_state(super::COMPONENT_INPUT_PORT) {
|
||||
Some(Payload::One(Value::Usize(x))) => match x > 65535 {
|
||||
true => 0,
|
||||
false => x as u16,
|
||||
},
|
||||
_ => 0,
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn get_input_protocol(&self) -> FileTransferProtocol {
|
||||
match self.view.get_state(super::COMPONENT_RADIO_PROTOCOL) {
|
||||
Some(Payload::One(Value::Usize(x))) => Self::protocol_opt_to_enum(x),
|
||||
_ => FileTransferProtocol::Sftp,
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn get_input_username(&self) -> String {
|
||||
match self.view.get_state(super::COMPONENT_INPUT_USERNAME) {
|
||||
Some(Payload::One(Value::Str(x))) => x,
|
||||
_ => String::new(),
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn get_input_password(&self) -> String {
|
||||
match self.view.get_state(super::COMPONENT_INPUT_PASSWORD) {
|
||||
Some(Payload::One(Value::Str(x))) => x,
|
||||
_ => String::new(),
|
||||
}
|
||||
}
|
||||
}
|
||||
@@ -1,711 +0,0 @@
|
||||
//! ## AuthActivity
|
||||
//!
|
||||
//! `auth_activity` is the module which implements the authentication activity
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// Locals
|
||||
use super::{AuthActivity, Context, FileTransferProtocol};
|
||||
use crate::ui::layout::components::{
|
||||
bookmark_list::BookmarkList, input::Input, msgbox::MsgBox, radio_group::RadioGroup,
|
||||
table::Table, text::Text, title::Title,
|
||||
};
|
||||
use crate::ui::layout::props::{
|
||||
InputType, PropValue, PropsBuilder, TableBuilder, TextParts, TextSpan, TextSpanBuilder,
|
||||
};
|
||||
use crate::ui::layout::utils::draw_area_in;
|
||||
use crate::ui::layout::{Msg, Payload};
|
||||
// Ext
|
||||
use tui::{
|
||||
layout::{Constraint, Direction, Layout},
|
||||
style::Color,
|
||||
widgets::Clear,
|
||||
};
|
||||
|
||||
impl AuthActivity {
|
||||
/// ### init
|
||||
///
|
||||
/// Initialize view, mounting all startup components inside the view
|
||||
pub(super) fn init(&mut self) {
|
||||
// Header
|
||||
self.view.mount(super::COMPONENT_TEXT_HEADER, Box::new(
|
||||
Title::new(
|
||||
PropsBuilder::default().with_foreground(Color::White).with_texts(
|
||||
TextParts::new(Some(String::from(" _____ ____ ____ ____ \n|_ _|__ _ __ _ __ ___ / ___| / ___| _ \\ \n | |/ _ \\ '__| '_ ` _ \\\\___ \\| | | |_) |\n | | __/ | | | | | | |___) | |___| __/ \n |_|\\___|_| |_| |_| |_|____/ \\____|_| \n")), None)
|
||||
).bold().build()
|
||||
)
|
||||
));
|
||||
// Footer
|
||||
self.view.mount(
|
||||
super::COMPONENT_TEXT_FOOTER,
|
||||
Box::new(Text::new(
|
||||
PropsBuilder::default()
|
||||
.with_texts(TextParts::new(
|
||||
None,
|
||||
Some(vec![
|
||||
TextSpanBuilder::new("Press ").bold().build(),
|
||||
TextSpanBuilder::new("<CTRL+H>")
|
||||
.bold()
|
||||
.with_foreground(Color::Cyan)
|
||||
.build(),
|
||||
TextSpanBuilder::new(" to show keybindings; ")
|
||||
.bold()
|
||||
.build(),
|
||||
TextSpanBuilder::new("<CTRL+C>")
|
||||
.bold()
|
||||
.with_foreground(Color::Cyan)
|
||||
.build(),
|
||||
TextSpanBuilder::new(" to enter setup").bold().build(),
|
||||
]),
|
||||
))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Address
|
||||
self.view.mount(
|
||||
super::COMPONENT_INPUT_ADDR,
|
||||
Box::new(Input::new(
|
||||
PropsBuilder::default()
|
||||
.with_foreground(Color::Yellow)
|
||||
.with_texts(TextParts::new(Some(String::from("Remote address")), None))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Port
|
||||
self.view.mount(
|
||||
super::COMPONENT_INPUT_PORT,
|
||||
Box::new(Input::new(
|
||||
PropsBuilder::default()
|
||||
.with_foreground(Color::LightCyan)
|
||||
.with_texts(TextParts::new(Some(String::from("Port number")), None))
|
||||
.with_input(InputType::Number)
|
||||
.with_input_len(5)
|
||||
.with_value(PropValue::Str(String::from("22")))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Protocol
|
||||
self.view.mount(
|
||||
super::COMPONENT_RADIO_PROTOCOL,
|
||||
Box::new(RadioGroup::new(
|
||||
PropsBuilder::default()
|
||||
.with_foreground(Color::LightGreen)
|
||||
.with_background(Color::Black)
|
||||
.with_texts(TextParts::new(
|
||||
Some(String::from("Protocol")),
|
||||
Some(vec![
|
||||
TextSpan::from("SFTP"),
|
||||
TextSpan::from("SCP"),
|
||||
TextSpan::from("FTP"),
|
||||
TextSpan::from("FTPS"),
|
||||
]),
|
||||
))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Username
|
||||
self.view.mount(
|
||||
super::COMPONENT_INPUT_USERNAME,
|
||||
Box::new(Input::new(
|
||||
PropsBuilder::default()
|
||||
.with_foreground(Color::LightMagenta)
|
||||
.with_texts(TextParts::new(Some(String::from("Username")), None))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Password
|
||||
self.view.mount(
|
||||
super::COMPONENT_INPUT_PASSWORD,
|
||||
Box::new(Input::new(
|
||||
PropsBuilder::default()
|
||||
.with_foreground(Color::LightBlue)
|
||||
.with_texts(TextParts::new(Some(String::from("Password")), None))
|
||||
.with_input(InputType::Password)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Version notice
|
||||
if let Some(version) = self
|
||||
.context
|
||||
.as_ref()
|
||||
.unwrap()
|
||||
.store
|
||||
.get_string(super::STORE_KEY_LATEST_VERSION)
|
||||
{
|
||||
self.view.mount(
|
||||
super::COMPONENT_TEXT_NEW_VERSION,
|
||||
Box::new(Text::new(
|
||||
PropsBuilder::default()
|
||||
.with_foreground(Color::Yellow)
|
||||
.with_texts(TextParts::new(None, Some(vec![TextSpan::from(format!("TermSCP {} is now available! Download it from <https://github.com/veeso/termscp/releases/latest>", version))])))
|
||||
.build()
|
||||
))
|
||||
);
|
||||
}
|
||||
// Bookmarks
|
||||
self.view.mount(
|
||||
super::COMPONENT_BOOKMARKS_LIST,
|
||||
Box::new(BookmarkList::new(
|
||||
PropsBuilder::default()
|
||||
.with_background(Color::LightGreen)
|
||||
.with_foreground(Color::Black)
|
||||
.with_texts(TextParts::new(Some(String::from("Bookmarks")), None))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
let _ = self.view_bookmarks();
|
||||
// Recents
|
||||
self.view.mount(
|
||||
super::COMPONENT_RECENTS_LIST,
|
||||
Box::new(BookmarkList::new(
|
||||
PropsBuilder::default()
|
||||
.with_background(Color::LightBlue)
|
||||
.with_foreground(Color::Black)
|
||||
.with_texts(TextParts::new(
|
||||
Some(String::from("Recent connections")),
|
||||
None,
|
||||
))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
let _ = self.view_recent_connections();
|
||||
// Active address
|
||||
self.view.active(super::COMPONENT_INPUT_ADDR);
|
||||
}
|
||||
|
||||
/// ### view
|
||||
///
|
||||
/// Display view on canvas
|
||||
pub(super) fn view(&mut self) {
|
||||
let mut ctx: Context = self.context.take().unwrap();
|
||||
let _ = ctx.terminal.draw(|f| {
|
||||
// Prepare chunks
|
||||
let chunks = Layout::default()
|
||||
.direction(Direction::Vertical)
|
||||
.margin(1)
|
||||
.constraints(
|
||||
[
|
||||
Constraint::Percentage(70), // Auth Form
|
||||
Constraint::Percentage(30), // Bookmarks
|
||||
]
|
||||
.as_ref(),
|
||||
)
|
||||
.split(f.size());
|
||||
// Create explorer chunks
|
||||
let auth_chunks = Layout::default()
|
||||
.constraints(
|
||||
[
|
||||
Constraint::Length(6), // header
|
||||
Constraint::Length(1), // Version
|
||||
Constraint::Length(3), // host
|
||||
Constraint::Length(3), // port
|
||||
Constraint::Length(3), // protocol
|
||||
Constraint::Length(3), // username
|
||||
Constraint::Length(3), // password
|
||||
Constraint::Length(3), // footer
|
||||
]
|
||||
.as_ref(),
|
||||
)
|
||||
.direction(Direction::Vertical)
|
||||
.split(chunks[0]);
|
||||
// Create bookmark chunks
|
||||
let bookmark_chunks = Layout::default()
|
||||
.constraints([Constraint::Percentage(50), Constraint::Percentage(50)].as_ref())
|
||||
.direction(Direction::Horizontal)
|
||||
.split(chunks[1]);
|
||||
// Render
|
||||
// Auth chunks
|
||||
self.view
|
||||
.render(super::COMPONENT_TEXT_HEADER, f, auth_chunks[0]);
|
||||
self.view
|
||||
.render(super::COMPONENT_TEXT_NEW_VERSION, f, auth_chunks[1]);
|
||||
self.view
|
||||
.render(super::COMPONENT_INPUT_ADDR, f, auth_chunks[2]);
|
||||
self.view
|
||||
.render(super::COMPONENT_INPUT_PORT, f, auth_chunks[3]);
|
||||
self.view
|
||||
.render(super::COMPONENT_RADIO_PROTOCOL, f, auth_chunks[4]);
|
||||
self.view
|
||||
.render(super::COMPONENT_INPUT_USERNAME, f, auth_chunks[5]);
|
||||
self.view
|
||||
.render(super::COMPONENT_INPUT_PASSWORD, f, auth_chunks[6]);
|
||||
self.view
|
||||
.render(super::COMPONENT_TEXT_FOOTER, f, auth_chunks[7]);
|
||||
// Bookmark chunks
|
||||
self.view
|
||||
.render(super::COMPONENT_BOOKMARKS_LIST, f, bookmark_chunks[0]);
|
||||
self.view
|
||||
.render(super::COMPONENT_RECENTS_LIST, f, bookmark_chunks[1]);
|
||||
// Popups
|
||||
if let Some(mut props) = self.view.get_props(super::COMPONENT_TEXT_ERROR) {
|
||||
if props.build().visible {
|
||||
let popup = draw_area_in(f.size(), 50, 10);
|
||||
f.render_widget(Clear, popup);
|
||||
// make popup
|
||||
self.view.render(super::COMPONENT_TEXT_ERROR, f, popup);
|
||||
}
|
||||
}
|
||||
if let Some(mut props) = self.view.get_props(super::COMPONENT_RADIO_QUIT) {
|
||||
if props.build().visible {
|
||||
// make popup
|
||||
let popup = draw_area_in(f.size(), 30, 10);
|
||||
f.render_widget(Clear, popup);
|
||||
self.view.render(super::COMPONENT_RADIO_QUIT, f, popup);
|
||||
}
|
||||
}
|
||||
if let Some(mut props) = self
|
||||
.view
|
||||
.get_props(super::COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK)
|
||||
{
|
||||
if props.build().visible {
|
||||
// make popup
|
||||
let popup = draw_area_in(f.size(), 30, 10);
|
||||
f.render_widget(Clear, popup);
|
||||
self.view
|
||||
.render(super::COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK, f, popup);
|
||||
}
|
||||
}
|
||||
if let Some(mut props) = self
|
||||
.view
|
||||
.get_props(super::COMPONENT_RADIO_BOOKMARK_DEL_RECENT)
|
||||
{
|
||||
if props.build().visible {
|
||||
// make popup
|
||||
let popup = draw_area_in(f.size(), 30, 10);
|
||||
f.render_widget(Clear, popup);
|
||||
self.view
|
||||
.render(super::COMPONENT_RADIO_BOOKMARK_DEL_RECENT, f, popup);
|
||||
}
|
||||
}
|
||||
if let Some(mut props) = self.view.get_props(super::COMPONENT_TEXT_HELP) {
|
||||
if props.build().visible {
|
||||
// make popup
|
||||
let popup = draw_area_in(f.size(), 50, 70);
|
||||
f.render_widget(Clear, popup);
|
||||
self.view.render(super::COMPONENT_TEXT_HELP, f, popup);
|
||||
}
|
||||
}
|
||||
if let Some(mut props) = self
|
||||
.view
|
||||
.get_props(super::COMPONENT_RADIO_BOOKMARK_SAVE_PWD)
|
||||
{
|
||||
if props.build().visible {
|
||||
// make popup
|
||||
let popup = draw_area_in(f.size(), 20, 20);
|
||||
f.render_widget(Clear, popup);
|
||||
let popup_chunks = Layout::default()
|
||||
.direction(Direction::Vertical)
|
||||
.constraints(
|
||||
[
|
||||
Constraint::Length(3), // Input form
|
||||
Constraint::Length(2), // Yes/No
|
||||
]
|
||||
.as_ref(),
|
||||
)
|
||||
.split(popup);
|
||||
self.view
|
||||
.render(super::COMPONENT_INPUT_BOOKMARK_NAME, f, popup_chunks[0]);
|
||||
self.view
|
||||
.render(super::COMPONENT_RADIO_BOOKMARK_SAVE_PWD, f, popup_chunks[1]);
|
||||
}
|
||||
}
|
||||
});
|
||||
self.context = Some(ctx);
|
||||
}
|
||||
|
||||
// -- partials
|
||||
|
||||
/// ### view_bookmarks
|
||||
///
|
||||
/// Make text span from bookmarks
|
||||
pub(super) fn view_bookmarks(&mut self) -> Option<(String, Msg)> {
|
||||
let bookmarks: Vec<TextSpan> = self
|
||||
.bookmarks_list
|
||||
.iter()
|
||||
.map(|x| {
|
||||
let entry: (String, u16, FileTransferProtocol, String, _) = self
|
||||
.bookmarks_client
|
||||
.as_ref()
|
||||
.unwrap()
|
||||
.get_bookmark(x)
|
||||
.unwrap();
|
||||
TextSpan::from(
|
||||
format!(
|
||||
"{} ({}://{}@{}:{})",
|
||||
x,
|
||||
entry.2.to_string().to_lowercase(),
|
||||
entry.3,
|
||||
entry.0,
|
||||
entry.1
|
||||
)
|
||||
.as_str(),
|
||||
)
|
||||
})
|
||||
.collect();
|
||||
match self
|
||||
.view
|
||||
.get_props(super::COMPONENT_BOOKMARKS_LIST)
|
||||
.as_mut()
|
||||
{
|
||||
None => None,
|
||||
Some(props) => {
|
||||
let msg = self.view.update(
|
||||
super::COMPONENT_BOOKMARKS_LIST,
|
||||
props
|
||||
.with_texts(TextParts::new(
|
||||
Some(String::from("Bookmarks")),
|
||||
Some(bookmarks),
|
||||
))
|
||||
.build(),
|
||||
);
|
||||
msg
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### view_recent_connections
|
||||
///
|
||||
/// View recent connections
|
||||
pub(super) fn view_recent_connections(&mut self) -> Option<(String, Msg)> {
|
||||
let bookmarks: Vec<TextSpan> = self
|
||||
.recents_list
|
||||
.iter()
|
||||
.map(|x| {
|
||||
let entry: (String, u16, FileTransferProtocol, String) = self
|
||||
.bookmarks_client
|
||||
.as_ref()
|
||||
.unwrap()
|
||||
.get_recent(x)
|
||||
.unwrap();
|
||||
TextSpan::from(
|
||||
format!(
|
||||
"{}://{}@{}:{}",
|
||||
entry.2.to_string().to_lowercase(),
|
||||
entry.3,
|
||||
entry.0,
|
||||
entry.1
|
||||
)
|
||||
.as_str(),
|
||||
)
|
||||
})
|
||||
.collect();
|
||||
match self.view.get_props(super::COMPONENT_RECENTS_LIST).as_mut() {
|
||||
None => None,
|
||||
Some(props) => {
|
||||
let msg = self.view.update(
|
||||
super::COMPONENT_RECENTS_LIST,
|
||||
props
|
||||
.with_texts(TextParts::new(
|
||||
Some(String::from("Recent connections")),
|
||||
Some(bookmarks),
|
||||
))
|
||||
.build(),
|
||||
);
|
||||
msg
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// -- mount
|
||||
|
||||
/// ### mount_error
|
||||
///
|
||||
/// Mount error box
|
||||
pub(super) fn mount_error(&mut self, text: &str) {
|
||||
// Mount
|
||||
self.view.mount(
|
||||
super::COMPONENT_TEXT_ERROR,
|
||||
Box::new(MsgBox::new(
|
||||
PropsBuilder::default()
|
||||
.with_foreground(Color::Red)
|
||||
.bold()
|
||||
.with_texts(TextParts::new(None, Some(vec![TextSpan::from(text)])))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Give focus to error
|
||||
self.view.active(super::COMPONENT_TEXT_ERROR);
|
||||
}
|
||||
|
||||
/// ### umount_error
|
||||
///
|
||||
/// Umount error message
|
||||
pub(super) fn umount_error(&mut self) {
|
||||
self.view.umount(super::COMPONENT_TEXT_ERROR);
|
||||
}
|
||||
|
||||
/// ### mount_quit
|
||||
///
|
||||
/// Mount quit popup
|
||||
pub(super) fn mount_quit(&mut self) {
|
||||
// Protocol
|
||||
self.view.mount(
|
||||
super::COMPONENT_RADIO_QUIT,
|
||||
Box::new(RadioGroup::new(
|
||||
PropsBuilder::default()
|
||||
.with_foreground(Color::Yellow)
|
||||
.with_background(Color::Black)
|
||||
.with_texts(TextParts::new(
|
||||
Some(String::from("Quit TermSCP?")),
|
||||
Some(vec![TextSpan::from("Yes"), TextSpan::from("No")]),
|
||||
))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
self.view.active(super::COMPONENT_RADIO_QUIT);
|
||||
}
|
||||
|
||||
/// ### umount_quit
|
||||
///
|
||||
/// Umount quit popup
|
||||
pub(super) fn umount_quit(&mut self) {
|
||||
self.view.umount(super::COMPONENT_RADIO_QUIT);
|
||||
}
|
||||
|
||||
/// ### mount_bookmark_del_dialog
|
||||
///
|
||||
/// Mount bookmark delete dialog
|
||||
pub(super) fn mount_bookmark_del_dialog(&mut self) {
|
||||
self.view.mount(
|
||||
super::COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK,
|
||||
Box::new(RadioGroup::new(
|
||||
PropsBuilder::default()
|
||||
.with_foreground(Color::Yellow)
|
||||
.with_background(Color::Black)
|
||||
.with_texts(TextParts::new(
|
||||
Some(String::from("Delete bookmark?")),
|
||||
Some(vec![TextSpan::from("Yes"), TextSpan::from("No")]),
|
||||
))
|
||||
.with_value(PropValue::Unsigned(1))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Active
|
||||
self.view
|
||||
.active(super::COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK);
|
||||
}
|
||||
|
||||
/// ### umount_bookmark_del_dialog
|
||||
///
|
||||
/// umount delete bookmark dialog
|
||||
pub(super) fn umount_bookmark_del_dialog(&mut self) {
|
||||
self.view
|
||||
.umount(super::COMPONENT_RADIO_BOOKMARK_DEL_BOOKMARK);
|
||||
}
|
||||
|
||||
/// ### mount_bookmark_del_dialog
|
||||
///
|
||||
/// Mount recent delete dialog
|
||||
pub(super) fn mount_recent_del_dialog(&mut self) {
|
||||
self.view.mount(
|
||||
super::COMPONENT_RADIO_BOOKMARK_DEL_RECENT,
|
||||
Box::new(RadioGroup::new(
|
||||
PropsBuilder::default()
|
||||
.with_foreground(Color::Yellow)
|
||||
.with_background(Color::Black)
|
||||
.with_texts(TextParts::new(
|
||||
Some(String::from("Delete bookmark?")),
|
||||
Some(vec![TextSpan::from("Yes"), TextSpan::from("No")]),
|
||||
))
|
||||
.with_value(PropValue::Unsigned(1))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Active
|
||||
self.view.active(super::COMPONENT_RADIO_BOOKMARK_DEL_RECENT);
|
||||
}
|
||||
|
||||
/// ### umount_recent_del_dialog
|
||||
///
|
||||
/// umount delete recent dialog
|
||||
pub(super) fn umount_recent_del_dialog(&mut self) {
|
||||
self.view.umount(super::COMPONENT_RADIO_BOOKMARK_DEL_RECENT);
|
||||
}
|
||||
|
||||
/// ### mount_bookmark_save_dialog
|
||||
///
|
||||
/// Mount bookmark save dialog
|
||||
pub(super) fn mount_bookmark_save_dialog(&mut self) {
|
||||
self.view.mount(
|
||||
super::COMPONENT_INPUT_BOOKMARK_NAME,
|
||||
Box::new(Input::new(
|
||||
PropsBuilder::default()
|
||||
.with_foreground(Color::LightCyan)
|
||||
.with_texts(TextParts::new(
|
||||
Some(String::from("Save bookmark as...")),
|
||||
None,
|
||||
))
|
||||
//.with_borders(Borders::TOP | Borders::RIGHT | Borders::LEFT)
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
self.view.mount(
|
||||
super::COMPONENT_RADIO_BOOKMARK_SAVE_PWD,
|
||||
Box::new(RadioGroup::new(
|
||||
PropsBuilder::default()
|
||||
.with_foreground(Color::Red)
|
||||
//.with_borders(Borders::BOTTOM | Borders::RIGHT | Borders::LEFT)
|
||||
.with_texts(TextParts::new(
|
||||
Some(String::from("Save password?")),
|
||||
Some(vec![TextSpan::from("Yes"), TextSpan::from("No")]),
|
||||
))
|
||||
//.with_value(PropValue::Unsigned(1))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Give focus to input bookmark name
|
||||
self.view.active(super::COMPONENT_INPUT_BOOKMARK_NAME);
|
||||
}
|
||||
|
||||
/// ### umount_bookmark_save_dialog
|
||||
///
|
||||
/// Umount bookmark save dialog
|
||||
pub(super) fn umount_bookmark_save_dialog(&mut self) {
|
||||
self.view.umount(super::COMPONENT_RADIO_BOOKMARK_SAVE_PWD);
|
||||
self.view.umount(super::COMPONENT_INPUT_BOOKMARK_NAME);
|
||||
}
|
||||
|
||||
/// ### mount_help
|
||||
///
|
||||
/// Mount help
|
||||
pub(super) fn mount_help(&mut self) {
|
||||
self.view.mount(
|
||||
super::COMPONENT_TEXT_HELP,
|
||||
Box::new(Table::new(
|
||||
PropsBuilder::default()
|
||||
.with_texts(TextParts::table(
|
||||
Some(String::from("Help")),
|
||||
TableBuilder::default()
|
||||
.add_col(
|
||||
TextSpanBuilder::new("<ESC>")
|
||||
.bold()
|
||||
.with_foreground(Color::Cyan)
|
||||
.build(),
|
||||
)
|
||||
.add_col(TextSpan::from(" Quit TermSCP"))
|
||||
.add_row()
|
||||
.add_col(
|
||||
TextSpanBuilder::new("<TAB>")
|
||||
.bold()
|
||||
.with_foreground(Color::Cyan)
|
||||
.build(),
|
||||
)
|
||||
.add_col(TextSpan::from(" Switch from form and bookmarks"))
|
||||
.add_row()
|
||||
.add_col(
|
||||
TextSpanBuilder::new("<RIGHT/LEFT>")
|
||||
.bold()
|
||||
.with_foreground(Color::Cyan)
|
||||
.build(),
|
||||
)
|
||||
.add_col(TextSpan::from(" Switch bookmark tab"))
|
||||
.add_row()
|
||||
.add_col(
|
||||
TextSpanBuilder::new("<UP/DOWN>")
|
||||
.bold()
|
||||
.with_foreground(Color::Cyan)
|
||||
.build(),
|
||||
)
|
||||
.add_col(TextSpan::from(" Move up/down in current tab"))
|
||||
.add_row()
|
||||
.add_col(
|
||||
TextSpanBuilder::new("<ENTER>")
|
||||
.bold()
|
||||
.with_foreground(Color::Cyan)
|
||||
.build(),
|
||||
)
|
||||
.add_col(TextSpan::from(" Connect/Load bookmark"))
|
||||
.add_row()
|
||||
.add_col(
|
||||
TextSpanBuilder::new("<DEL|E>")
|
||||
.bold()
|
||||
.with_foreground(Color::Cyan)
|
||||
.build(),
|
||||
)
|
||||
.add_col(TextSpan::from(" Delete selected bookmark"))
|
||||
.add_row()
|
||||
.add_col(
|
||||
TextSpanBuilder::new("<CTRL+C>")
|
||||
.bold()
|
||||
.with_foreground(Color::Cyan)
|
||||
.build(),
|
||||
)
|
||||
.add_col(TextSpan::from(" Enter setup"))
|
||||
.add_row()
|
||||
.add_col(
|
||||
TextSpanBuilder::new("<CTRL+S>")
|
||||
.bold()
|
||||
.with_foreground(Color::Cyan)
|
||||
.build(),
|
||||
)
|
||||
.add_col(TextSpan::from(" Save bookmark"))
|
||||
.build(),
|
||||
))
|
||||
.build(),
|
||||
)),
|
||||
);
|
||||
// Active help
|
||||
self.view.active(super::COMPONENT_TEXT_HELP);
|
||||
}
|
||||
|
||||
/// ### umount_help
|
||||
///
|
||||
/// Umount help
|
||||
pub(super) fn umount_help(&mut self) {
|
||||
self.view.umount(super::COMPONENT_TEXT_HELP);
|
||||
}
|
||||
|
||||
/// ### get_input
|
||||
///
|
||||
/// Collect input values from view
|
||||
pub(super) fn get_input(&self) -> (String, u16, FileTransferProtocol, String, String) {
|
||||
let addr: String = match self.view.get_value(super::COMPONENT_INPUT_ADDR) {
|
||||
Some(Payload::Text(a)) => a,
|
||||
_ => String::new(),
|
||||
};
|
||||
let port: u16 = match self.view.get_value(super::COMPONENT_INPUT_PORT) {
|
||||
Some(Payload::Unsigned(p)) => p as u16,
|
||||
_ => 0,
|
||||
};
|
||||
let protocol: FileTransferProtocol =
|
||||
match self.view.get_value(super::COMPONENT_RADIO_PROTOCOL) {
|
||||
Some(Payload::Unsigned(p)) => match p {
|
||||
1 => FileTransferProtocol::Scp,
|
||||
2 => FileTransferProtocol::Ftp(false),
|
||||
3 => FileTransferProtocol::Ftp(true),
|
||||
_ => FileTransferProtocol::Sftp,
|
||||
},
|
||||
_ => FileTransferProtocol::Sftp,
|
||||
};
|
||||
let username: String = match self.view.get_value(super::COMPONENT_INPUT_USERNAME) {
|
||||
Some(Payload::Text(a)) => a,
|
||||
_ => String::new(),
|
||||
};
|
||||
let password: String = match self.view.get_value(super::COMPONENT_INPUT_PASSWORD) {
|
||||
Some(Payload::Text(a)) => a,
|
||||
_ => String::new(),
|
||||
};
|
||||
(addr, port, protocol, username, password)
|
||||
}
|
||||
}
|
||||
184
src/ui/activities/filetransfer/actions/change_dir.rs
Normal file
@@ -0,0 +1,184 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use super::{FileTransferActivity, FsEntry};
|
||||
use std::path::PathBuf;
|
||||
|
||||
impl FileTransferActivity {
|
||||
/// ### action_enter_local_dir
|
||||
///
|
||||
/// Enter a directory on local host from entry
|
||||
/// Return true whether the directory changed
|
||||
pub(crate) fn action_enter_local_dir(&mut self, entry: FsEntry, block_sync: bool) -> bool {
|
||||
match entry {
|
||||
FsEntry::Directory(dir) => {
|
||||
self.local_changedir(dir.abs_path.as_path(), true);
|
||||
if self.browser.sync_browsing && !block_sync {
|
||||
self.action_change_remote_dir(dir.name, true);
|
||||
}
|
||||
true
|
||||
}
|
||||
FsEntry::File(file) => {
|
||||
match &file.symlink {
|
||||
Some(symlink_entry) => {
|
||||
// If symlink and is directory, point to symlink
|
||||
match &**symlink_entry {
|
||||
FsEntry::Directory(dir) => {
|
||||
self.local_changedir(dir.abs_path.as_path(), true);
|
||||
// Check whether to sync
|
||||
if self.browser.sync_browsing && !block_sync {
|
||||
self.action_change_remote_dir(dir.name.clone(), true);
|
||||
}
|
||||
true
|
||||
}
|
||||
_ => false,
|
||||
}
|
||||
}
|
||||
None => false,
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### action_enter_remote_dir
|
||||
///
|
||||
/// Enter a directory on local host from entry
|
||||
/// Return true whether the directory changed
|
||||
pub(crate) fn action_enter_remote_dir(&mut self, entry: FsEntry, block_sync: bool) -> bool {
|
||||
match entry {
|
||||
FsEntry::Directory(dir) => {
|
||||
self.remote_changedir(dir.abs_path.as_path(), true);
|
||||
if self.browser.sync_browsing && !block_sync {
|
||||
self.action_change_local_dir(dir.name, true);
|
||||
}
|
||||
true
|
||||
}
|
||||
FsEntry::File(file) => {
|
||||
match &file.symlink {
|
||||
Some(symlink_entry) => {
|
||||
// If symlink and is directory, point to symlink
|
||||
match &**symlink_entry {
|
||||
FsEntry::Directory(dir) => {
|
||||
self.remote_changedir(dir.abs_path.as_path(), true);
|
||||
// Check whether to sync
|
||||
if self.browser.sync_browsing && !block_sync {
|
||||
self.action_change_local_dir(dir.name.clone(), true);
|
||||
}
|
||||
true
|
||||
}
|
||||
_ => false,
|
||||
}
|
||||
}
|
||||
None => false,
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### action_change_local_dir
|
||||
///
|
||||
/// Change local directory reading value from input
|
||||
pub(crate) fn action_change_local_dir(&mut self, input: String, block_sync: bool) {
|
||||
let dir_path: PathBuf = self.local_to_abs_path(PathBuf::from(input.as_str()).as_path());
|
||||
self.local_changedir(dir_path.as_path(), true);
|
||||
// Check whether to sync
|
||||
if self.browser.sync_browsing && !block_sync {
|
||||
self.action_change_remote_dir(input, true);
|
||||
}
|
||||
}
|
||||
|
||||
/// ### action_change_remote_dir
|
||||
///
|
||||
/// Change remote directory reading value from input
|
||||
pub(crate) fn action_change_remote_dir(&mut self, input: String, block_sync: bool) {
|
||||
let dir_path: PathBuf = self.remote_to_abs_path(PathBuf::from(input.as_str()).as_path());
|
||||
self.remote_changedir(dir_path.as_path(), true);
|
||||
// Check whether to sync
|
||||
if self.browser.sync_browsing && !block_sync {
|
||||
self.action_change_local_dir(input, true);
|
||||
}
|
||||
}
|
||||
|
||||
/// ### action_go_to_previous_local_dir
|
||||
///
|
||||
/// Go to previous directory from localhost
|
||||
pub(crate) fn action_go_to_previous_local_dir(&mut self, block_sync: bool) {
|
||||
if let Some(d) = self.local_mut().popd() {
|
||||
self.local_changedir(d.as_path(), false);
|
||||
// Check whether to sync
|
||||
if self.browser.sync_browsing && !block_sync {
|
||||
self.action_go_to_previous_remote_dir(true);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### action_go_to_previous_remote_dir
|
||||
///
|
||||
/// Go to previous directory from remote host
|
||||
pub(crate) fn action_go_to_previous_remote_dir(&mut self, block_sync: bool) {
|
||||
if let Some(d) = self.remote_mut().popd() {
|
||||
self.remote_changedir(d.as_path(), false);
|
||||
// Check whether to sync
|
||||
if self.browser.sync_browsing && !block_sync {
|
||||
self.action_go_to_previous_local_dir(true);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### action_go_to_local_upper_dir
|
||||
///
|
||||
/// Go to upper directory on local host
|
||||
pub(crate) fn action_go_to_local_upper_dir(&mut self, block_sync: bool) {
|
||||
// Get pwd
|
||||
let path: PathBuf = self.local().wrkdir.clone();
|
||||
// Go to parent directory
|
||||
if let Some(parent) = path.as_path().parent() {
|
||||
self.local_changedir(parent, true);
|
||||
// If sync is enabled update remote too
|
||||
if self.browser.sync_browsing && !block_sync {
|
||||
self.action_go_to_remote_upper_dir(true);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// #### action_go_to_remote_upper_dir
|
||||
///
|
||||
/// Go to upper directory on remote host
|
||||
pub(crate) fn action_go_to_remote_upper_dir(&mut self, block_sync: bool) {
|
||||
// Get pwd
|
||||
let path: PathBuf = self.remote().wrkdir.clone();
|
||||
// Go to parent directory
|
||||
if let Some(parent) = path.as_path().parent() {
|
||||
self.remote_changedir(parent, true);
|
||||
// If sync is enabled update local too
|
||||
if self.browser.sync_browsing && !block_sync {
|
||||
self.action_go_to_local_upper_dir(true);
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
263
src/ui/activities/filetransfer/actions/copy.rs
Normal file
@@ -0,0 +1,263 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use super::{FileTransferActivity, FsEntry, LogLevel, SelectedEntry, TransferPayload};
|
||||
use crate::filetransfer::FileTransferErrorType;
|
||||
use crate::fs::FsFile;
|
||||
use std::path::{Path, PathBuf};
|
||||
|
||||
impl FileTransferActivity {
|
||||
/// ### action_local_copy
|
||||
///
|
||||
/// Copy file on local
|
||||
pub(crate) fn action_local_copy(&mut self, input: String) {
|
||||
match self.get_local_selected_entries() {
|
||||
SelectedEntry::One(entry) => {
|
||||
let dest_path: PathBuf = PathBuf::from(input);
|
||||
self.local_copy_file(&entry, dest_path.as_path());
|
||||
// Reload entries
|
||||
self.reload_local_dir();
|
||||
}
|
||||
SelectedEntry::Many(entries) => {
|
||||
// Try to copy each file to Input/{FILE_NAME}
|
||||
let base_path: PathBuf = PathBuf::from(input);
|
||||
// Iter files
|
||||
for entry in entries.iter() {
|
||||
let mut dest_path: PathBuf = base_path.clone();
|
||||
dest_path.push(entry.get_name());
|
||||
self.local_copy_file(entry, dest_path.as_path());
|
||||
}
|
||||
// Reload entries
|
||||
self.reload_local_dir();
|
||||
}
|
||||
SelectedEntry::None => {}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### action_remote_copy
|
||||
///
|
||||
/// Copy file on remote
|
||||
pub(crate) fn action_remote_copy(&mut self, input: String) {
|
||||
match self.get_remote_selected_entries() {
|
||||
SelectedEntry::One(entry) => {
|
||||
let dest_path: PathBuf = PathBuf::from(input);
|
||||
self.remote_copy_file(entry, dest_path.as_path());
|
||||
// Reload entries
|
||||
self.reload_remote_dir();
|
||||
}
|
||||
SelectedEntry::Many(entries) => {
|
||||
// Try to copy each file to Input/{FILE_NAME}
|
||||
let base_path: PathBuf = PathBuf::from(input);
|
||||
// Iter files
|
||||
for entry in entries.into_iter() {
|
||||
let mut dest_path: PathBuf = base_path.clone();
|
||||
dest_path.push(entry.get_name());
|
||||
self.remote_copy_file(entry, dest_path.as_path());
|
||||
}
|
||||
// Reload entries
|
||||
self.reload_remote_dir();
|
||||
}
|
||||
SelectedEntry::None => {}
|
||||
}
|
||||
}
|
||||
|
||||
fn local_copy_file(&mut self, entry: &FsEntry, dest: &Path) {
|
||||
match self.host.copy(entry, dest) {
|
||||
Ok(_) => {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!(
|
||||
"Copied \"{}\" to \"{}\"",
|
||||
entry.get_abs_path().display(),
|
||||
dest.display()
|
||||
),
|
||||
);
|
||||
}
|
||||
Err(err) => self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not copy \"{}\" to \"{}\": {}",
|
||||
entry.get_abs_path().display(),
|
||||
dest.display(),
|
||||
err
|
||||
),
|
||||
),
|
||||
}
|
||||
}
|
||||
|
||||
fn remote_copy_file(&mut self, entry: FsEntry, dest: &Path) {
|
||||
match self.client.as_mut().copy(&entry, dest) {
|
||||
Ok(_) => {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!(
|
||||
"Copied \"{}\" to \"{}\"",
|
||||
entry.get_abs_path().display(),
|
||||
dest.display()
|
||||
),
|
||||
);
|
||||
}
|
||||
Err(err) => match err.kind() {
|
||||
FileTransferErrorType::UnsupportedFeature => {
|
||||
// If copy is not supported, perform the tricky copy
|
||||
self.tricky_copy(entry, dest);
|
||||
}
|
||||
_ => self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not copy \"{}\" to \"{}\": {}",
|
||||
entry.get_abs_path().display(),
|
||||
dest.display(),
|
||||
err
|
||||
),
|
||||
),
|
||||
},
|
||||
}
|
||||
}
|
||||
|
||||
/// ### tricky_copy
|
||||
///
|
||||
/// Tricky copy will be used whenever copy command is not available on remote host
|
||||
fn tricky_copy(&mut self, entry: FsEntry, dest: &Path) {
|
||||
// NOTE: VERY IMPORTANT; wait block must be umounted or something really bad will happen
|
||||
self.umount_wait();
|
||||
// match entry
|
||||
match entry {
|
||||
FsEntry::File(entry) => {
|
||||
// Create tempfile
|
||||
let tmpfile: tempfile::NamedTempFile = match tempfile::NamedTempFile::new() {
|
||||
Ok(f) => f,
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Copy failed: could not create temporary file: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
};
|
||||
// Download file
|
||||
let name = entry.name.clone();
|
||||
let entry_path = entry.abs_path.clone();
|
||||
if let Err(err) =
|
||||
self.filetransfer_recv(TransferPayload::File(entry), tmpfile.path(), Some(name))
|
||||
{
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Copy failed: could not download to temporary file: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
// Get local fs entry
|
||||
let tmpfile_entry: FsFile = match self.host.stat(tmpfile.path()) {
|
||||
Ok(e) => e.unwrap_file(),
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Copy failed: could not stat \"{}\": {}",
|
||||
tmpfile.path().display(),
|
||||
err
|
||||
),
|
||||
);
|
||||
return;
|
||||
}
|
||||
};
|
||||
// Upload file to destination
|
||||
let wrkdir = self.remote().wrkdir.clone();
|
||||
if let Err(err) = self.filetransfer_send(
|
||||
TransferPayload::File(tmpfile_entry),
|
||||
wrkdir.as_path(),
|
||||
Some(String::from(dest.to_string_lossy())),
|
||||
) {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Copy failed: could not write file {}: {}",
|
||||
entry_path.display(),
|
||||
err
|
||||
),
|
||||
);
|
||||
return;
|
||||
}
|
||||
}
|
||||
FsEntry::Directory(_) => {
|
||||
let tempdir: tempfile::TempDir = match tempfile::TempDir::new() {
|
||||
Ok(d) => d,
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Copy failed: could not create temporary directory: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
};
|
||||
// Get path of dest
|
||||
let mut tempdir_path: PathBuf = tempdir.path().to_path_buf();
|
||||
tempdir_path.push(entry.get_name());
|
||||
// Download file
|
||||
if let Err(err) =
|
||||
self.filetransfer_recv(TransferPayload::Any(entry), tempdir.path(), None)
|
||||
{
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Copy failed: failed to download file: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
// Stat dir
|
||||
let tempdir_entry: FsEntry = match self.host.stat(tempdir_path.as_path()) {
|
||||
Ok(e) => e,
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Copy failed: could not stat \"{}\": {}",
|
||||
tempdir.path().display(),
|
||||
err
|
||||
),
|
||||
);
|
||||
return;
|
||||
}
|
||||
};
|
||||
// Upload to destination
|
||||
let wrkdir: PathBuf = self.remote().wrkdir.clone();
|
||||
if let Err(err) = self.filetransfer_send(
|
||||
TransferPayload::Any(tempdir_entry),
|
||||
wrkdir.as_path(),
|
||||
Some(String::from(dest.to_string_lossy())),
|
||||
) {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Copy failed: failed to send file: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
116
src/ui/activities/filetransfer/actions/delete.rs
Normal file
@@ -0,0 +1,116 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use super::{FileTransferActivity, FsEntry, LogLevel, SelectedEntry};
|
||||
|
||||
impl FileTransferActivity {
|
||||
pub(crate) fn action_local_delete(&mut self) {
|
||||
match self.get_local_selected_entries() {
|
||||
SelectedEntry::One(entry) => {
|
||||
// Delete file
|
||||
self.local_remove_file(&entry);
|
||||
// Reload
|
||||
self.reload_local_dir();
|
||||
}
|
||||
SelectedEntry::Many(entries) => {
|
||||
// Iter files
|
||||
for entry in entries.iter() {
|
||||
// Delete file
|
||||
self.local_remove_file(entry);
|
||||
}
|
||||
// Reload entries
|
||||
self.reload_local_dir();
|
||||
}
|
||||
SelectedEntry::None => {}
|
||||
}
|
||||
}
|
||||
|
||||
pub(crate) fn action_remote_delete(&mut self) {
|
||||
match self.get_remote_selected_entries() {
|
||||
SelectedEntry::One(entry) => {
|
||||
// Delete file
|
||||
self.remote_remove_file(&entry);
|
||||
// Reload
|
||||
self.reload_remote_dir();
|
||||
}
|
||||
SelectedEntry::Many(entries) => {
|
||||
// Iter files
|
||||
for entry in entries.iter() {
|
||||
// Delete file
|
||||
self.remote_remove_file(entry);
|
||||
}
|
||||
// Reload entries
|
||||
self.reload_remote_dir();
|
||||
}
|
||||
SelectedEntry::None => {}
|
||||
}
|
||||
}
|
||||
|
||||
pub(crate) fn local_remove_file(&mut self, entry: &FsEntry) {
|
||||
match self.host.remove(entry) {
|
||||
Ok(_) => {
|
||||
// Log
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Removed file \"{}\"", entry.get_abs_path().display()),
|
||||
);
|
||||
}
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not delete file \"{}\": {}",
|
||||
entry.get_abs_path().display(),
|
||||
err
|
||||
),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(crate) fn remote_remove_file(&mut self, entry: &FsEntry) {
|
||||
match self.client.remove(entry) {
|
||||
Ok(_) => {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Removed file \"{}\"", entry.get_abs_path().display()),
|
||||
);
|
||||
}
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not delete file \"{}\": {}",
|
||||
entry.get_abs_path().display(),
|
||||
err
|
||||
),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
232
src/ui/activities/filetransfer/actions/edit.rs
Normal file
@@ -0,0 +1,232 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use super::{FileTransferActivity, FsEntry, LogLevel, SelectedEntry, TransferPayload};
|
||||
use crate::fs::FsFile;
|
||||
// ext
|
||||
use crossterm::terminal::{disable_raw_mode, enable_raw_mode};
|
||||
use std::fs::OpenOptions;
|
||||
use std::io::Read;
|
||||
use std::path::{Path, PathBuf};
|
||||
use std::time::SystemTime;
|
||||
|
||||
impl FileTransferActivity {
|
||||
pub(crate) fn action_edit_local_file(&mut self) {
|
||||
let entries: Vec<FsEntry> = match self.get_local_selected_entries() {
|
||||
SelectedEntry::One(entry) => vec![entry],
|
||||
SelectedEntry::Many(entries) => entries,
|
||||
SelectedEntry::None => vec![],
|
||||
};
|
||||
// Edit all entries
|
||||
for entry in entries.iter() {
|
||||
// Check if file
|
||||
if entry.is_file() {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Opening file \"{}\"…", entry.get_abs_path().display()),
|
||||
);
|
||||
// Edit file
|
||||
if let Err(err) = self.edit_local_file(entry.get_abs_path().as_path()) {
|
||||
self.log_and_alert(LogLevel::Error, err);
|
||||
}
|
||||
}
|
||||
}
|
||||
// Reload entries
|
||||
self.reload_local_dir();
|
||||
}
|
||||
|
||||
pub(crate) fn action_edit_remote_file(&mut self) {
|
||||
let entries: Vec<FsEntry> = match self.get_remote_selected_entries() {
|
||||
SelectedEntry::One(entry) => vec![entry],
|
||||
SelectedEntry::Many(entries) => entries,
|
||||
SelectedEntry::None => vec![],
|
||||
};
|
||||
// Edit all entries
|
||||
for entry in entries.into_iter() {
|
||||
// Check if file
|
||||
if let FsEntry::File(file) = entry {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Opening file \"{}\"…", file.abs_path.display()),
|
||||
);
|
||||
// Edit file
|
||||
if let Err(err) = self.edit_remote_file(file) {
|
||||
self.log_and_alert(LogLevel::Error, err);
|
||||
}
|
||||
}
|
||||
}
|
||||
// Reload entries
|
||||
self.reload_remote_dir();
|
||||
}
|
||||
|
||||
/// ### edit_local_file
|
||||
///
|
||||
/// Edit a file on localhost
|
||||
fn edit_local_file(&mut self, path: &Path) -> Result<(), String> {
|
||||
// Read first 2048 bytes or less from file to check if it is textual
|
||||
match OpenOptions::new().read(true).open(path) {
|
||||
Ok(mut f) => {
|
||||
// Read
|
||||
let mut buff: [u8; 2048] = [0; 2048];
|
||||
match f.read(&mut buff) {
|
||||
Ok(size) => {
|
||||
if content_inspector::inspect(&buff[0..size]).is_binary() {
|
||||
return Err("Could not open file in editor: file is binary".to_string());
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
return Err(format!("Could not read file: {}", err));
|
||||
}
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
return Err(format!("Could not read file: {}", err));
|
||||
}
|
||||
}
|
||||
// Put input mode back to normal
|
||||
if let Err(err) = disable_raw_mode() {
|
||||
error!("Failed to disable raw mode: {}", err);
|
||||
}
|
||||
// Leave alternate mode
|
||||
#[cfg(not(target_os = "windows"))]
|
||||
if let Some(ctx) = self.context.as_mut() {
|
||||
ctx.leave_alternate_screen();
|
||||
}
|
||||
// Open editor
|
||||
match edit::edit_file(path) {
|
||||
Ok(_) => self.log(
|
||||
LogLevel::Info,
|
||||
format!(
|
||||
"Changes performed through editor saved to \"{}\"!",
|
||||
path.display()
|
||||
),
|
||||
),
|
||||
Err(err) => return Err(format!("Could not open editor: {}", err)),
|
||||
}
|
||||
#[cfg(not(target_os = "windows"))]
|
||||
if let Some(ctx) = self.context.as_mut() {
|
||||
// Clear screen
|
||||
ctx.clear_screen();
|
||||
// Enter alternate mode
|
||||
ctx.enter_alternate_screen();
|
||||
}
|
||||
// Re-enable raw mode
|
||||
let _ = enable_raw_mode();
|
||||
Ok(())
|
||||
}
|
||||
|
||||
/// ### edit_remote_file
|
||||
///
|
||||
/// Edit file on remote host
|
||||
fn edit_remote_file(&mut self, file: FsFile) -> Result<(), String> {
|
||||
// Create temp file
|
||||
let tmpfile: PathBuf = match self.download_file_as_temp(&file) {
|
||||
Ok(p) => p,
|
||||
Err(err) => return Err(err),
|
||||
};
|
||||
// Download file
|
||||
let file_name = file.name.clone();
|
||||
let file_path = file.abs_path.clone();
|
||||
if let Err(err) = self.filetransfer_recv(
|
||||
TransferPayload::File(file),
|
||||
tmpfile.as_path(),
|
||||
Some(file_name.clone()),
|
||||
) {
|
||||
return Err(format!("Could not open file {}: {}", file_name, err));
|
||||
}
|
||||
// Get current file modification time
|
||||
let prev_mtime: SystemTime = match self.host.stat(tmpfile.as_path()) {
|
||||
Ok(e) => e.get_last_change_time(),
|
||||
Err(err) => {
|
||||
return Err(format!(
|
||||
"Could not stat \"{}\": {}",
|
||||
tmpfile.as_path().display(),
|
||||
err
|
||||
))
|
||||
}
|
||||
};
|
||||
// Edit file
|
||||
if let Err(err) = self.edit_local_file(tmpfile.as_path()) {
|
||||
return Err(err);
|
||||
}
|
||||
// Get local fs entry
|
||||
let tmpfile_entry: FsEntry = match self.host.stat(tmpfile.as_path()) {
|
||||
Ok(e) => e,
|
||||
Err(err) => {
|
||||
return Err(format!(
|
||||
"Could not stat \"{}\": {}",
|
||||
tmpfile.as_path().display(),
|
||||
err
|
||||
))
|
||||
}
|
||||
};
|
||||
// Check if file has changed
|
||||
match prev_mtime != tmpfile_entry.get_last_change_time() {
|
||||
true => {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!(
|
||||
"File \"{}\" has changed; writing changes to remote",
|
||||
file_path.display()
|
||||
),
|
||||
);
|
||||
// Get local fs entry
|
||||
let tmpfile_entry: FsFile = match self.host.stat(tmpfile.as_path()) {
|
||||
Ok(e) => e.unwrap_file(),
|
||||
Err(err) => {
|
||||
return Err(format!(
|
||||
"Could not stat \"{}\": {}",
|
||||
tmpfile.as_path().display(),
|
||||
err
|
||||
))
|
||||
}
|
||||
};
|
||||
// Send file
|
||||
let wrkdir = self.remote().wrkdir.clone();
|
||||
if let Err(err) = self.filetransfer_send(
|
||||
TransferPayload::File(tmpfile_entry),
|
||||
wrkdir.as_path(),
|
||||
Some(file_name),
|
||||
) {
|
||||
return Err(format!(
|
||||
"Could not write file {}: {}",
|
||||
file_path.display(),
|
||||
err
|
||||
));
|
||||
}
|
||||
}
|
||||
false => {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("File \"{}\" hasn't changed", file_path.display()),
|
||||
);
|
||||
}
|
||||
}
|
||||
Ok(())
|
||||
}
|
||||
}
|
||||
66
src/ui/activities/filetransfer/actions/exec.rs
Normal file
@@ -0,0 +1,66 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use super::{FileTransferActivity, LogLevel};
|
||||
|
||||
impl FileTransferActivity {
|
||||
pub(crate) fn action_local_exec(&mut self, input: String) {
|
||||
match self.host.exec(input.as_str()) {
|
||||
Ok(output) => {
|
||||
// Reload files
|
||||
self.log(LogLevel::Info, format!("\"{}\": {}", input, output));
|
||||
// Reload entries
|
||||
self.reload_local_dir();
|
||||
}
|
||||
Err(err) => {
|
||||
// Report err
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not execute command \"{}\": {}", input, err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(crate) fn action_remote_exec(&mut self, input: String) {
|
||||
match self.client.as_mut().exec(input.as_str()) {
|
||||
Ok(output) => {
|
||||
// Reload files
|
||||
self.log(LogLevel::Info, format!("\"{}\": {}", input, output));
|
||||
self.reload_remote_dir();
|
||||
}
|
||||
Err(err) => {
|
||||
// Report err
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not execute command \"{}\": {}", input, err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
221
src/ui/activities/filetransfer/actions/find.rs
Normal file
@@ -0,0 +1,221 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use super::super::browser::FileExplorerTab;
|
||||
use super::{FileTransferActivity, FsEntry, LogLevel, SelectedEntry, TransferPayload};
|
||||
|
||||
use std::path::PathBuf;
|
||||
|
||||
impl FileTransferActivity {
|
||||
pub(crate) fn action_local_find(&mut self, input: String) -> Result<Vec<FsEntry>, String> {
|
||||
match self.host.find(input.as_str()) {
|
||||
Ok(entries) => Ok(entries),
|
||||
Err(err) => Err(format!("Could not search for files: {}", err)),
|
||||
}
|
||||
}
|
||||
|
||||
pub(crate) fn action_remote_find(&mut self, input: String) -> Result<Vec<FsEntry>, String> {
|
||||
match self.client.as_mut().find(input.as_str()) {
|
||||
Ok(entries) => Ok(entries),
|
||||
Err(err) => Err(format!("Could not search for files: {}", err)),
|
||||
}
|
||||
}
|
||||
|
||||
pub(crate) fn action_find_changedir(&mut self) {
|
||||
// Match entry
|
||||
if let SelectedEntry::One(entry) = self.get_found_selected_entries() {
|
||||
// Get path: if a directory, use directory path; if it is a File, get parent path
|
||||
let path: PathBuf = match entry {
|
||||
FsEntry::Directory(dir) => dir.abs_path,
|
||||
FsEntry::File(file) => match file.abs_path.parent() {
|
||||
None => PathBuf::from("."),
|
||||
Some(p) => p.to_path_buf(),
|
||||
},
|
||||
};
|
||||
// Change directory
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::Local => {
|
||||
self.local_changedir(path.as_path(), true)
|
||||
}
|
||||
FileExplorerTab::FindRemote | FileExplorerTab::Remote => {
|
||||
self.remote_changedir(path.as_path(), true)
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(crate) fn action_find_transfer(&mut self, save_as: Option<String>) {
|
||||
let wrkdir: PathBuf = match self.browser.tab() {
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::Local => self.remote().wrkdir.clone(),
|
||||
FileExplorerTab::FindRemote | FileExplorerTab::Remote => self.local().wrkdir.clone(),
|
||||
};
|
||||
match self.get_found_selected_entries() {
|
||||
SelectedEntry::One(entry) => match self.browser.tab() {
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::Local => {
|
||||
if let Err(err) = self.filetransfer_send(
|
||||
TransferPayload::Any(entry.get_realfile()),
|
||||
wrkdir.as_path(),
|
||||
save_as,
|
||||
) {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not upload file: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
}
|
||||
FileExplorerTab::FindRemote | FileExplorerTab::Remote => {
|
||||
if let Err(err) = self.filetransfer_recv(
|
||||
TransferPayload::Any(entry.get_realfile()),
|
||||
wrkdir.as_path(),
|
||||
save_as,
|
||||
) {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not download file: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
}
|
||||
},
|
||||
SelectedEntry::Many(entries) => {
|
||||
// In case of selection: save multiple files in wrkdir/input
|
||||
let mut dest_path: PathBuf = wrkdir;
|
||||
if let Some(save_as) = save_as {
|
||||
dest_path.push(save_as);
|
||||
}
|
||||
// Iter files
|
||||
let entries = entries.iter().map(|x| x.get_realfile()).collect();
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::Local => {
|
||||
if let Err(err) = self.filetransfer_send(
|
||||
TransferPayload::Many(entries),
|
||||
dest_path.as_path(),
|
||||
None,
|
||||
) {
|
||||
{
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not upload file: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
}
|
||||
}
|
||||
FileExplorerTab::FindRemote | FileExplorerTab::Remote => {
|
||||
if let Err(err) = self.filetransfer_recv(
|
||||
TransferPayload::Many(entries),
|
||||
dest_path.as_path(),
|
||||
None,
|
||||
) {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not download file: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
SelectedEntry::None => {}
|
||||
}
|
||||
}
|
||||
|
||||
pub(crate) fn action_find_delete(&mut self) {
|
||||
match self.get_found_selected_entries() {
|
||||
SelectedEntry::One(entry) => {
|
||||
// Delete file
|
||||
self.remove_found_file(&entry);
|
||||
}
|
||||
SelectedEntry::Many(entries) => {
|
||||
// Iter files
|
||||
for entry in entries.iter() {
|
||||
// Delete file
|
||||
self.remove_found_file(entry);
|
||||
}
|
||||
}
|
||||
SelectedEntry::None => {}
|
||||
}
|
||||
}
|
||||
|
||||
fn remove_found_file(&mut self, entry: &FsEntry) {
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::Local => {
|
||||
self.local_remove_file(entry);
|
||||
}
|
||||
FileExplorerTab::FindRemote | FileExplorerTab::Remote => {
|
||||
self.remote_remove_file(entry);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(crate) fn action_find_open(&mut self) {
|
||||
match self.get_found_selected_entries() {
|
||||
SelectedEntry::One(entry) => {
|
||||
// Open file
|
||||
self.open_found_file(&entry, None);
|
||||
}
|
||||
SelectedEntry::Many(entries) => {
|
||||
// Iter files
|
||||
for entry in entries.iter() {
|
||||
// Open file
|
||||
self.open_found_file(entry, None);
|
||||
}
|
||||
}
|
||||
SelectedEntry::None => {}
|
||||
}
|
||||
}
|
||||
|
||||
pub(crate) fn action_find_open_with(&mut self, with: &str) {
|
||||
match self.get_found_selected_entries() {
|
||||
SelectedEntry::One(entry) => {
|
||||
// Open file
|
||||
self.open_found_file(&entry, Some(with));
|
||||
}
|
||||
SelectedEntry::Many(entries) => {
|
||||
// Iter files
|
||||
for entry in entries.iter() {
|
||||
// Open file
|
||||
self.open_found_file(entry, Some(with));
|
||||
}
|
||||
}
|
||||
SelectedEntry::None => {}
|
||||
}
|
||||
}
|
||||
|
||||
fn open_found_file(&mut self, entry: &FsEntry, with: Option<&str>) {
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::Local => {
|
||||
self.action_open_local_file(entry, with);
|
||||
}
|
||||
FileExplorerTab::FindRemote | FileExplorerTab::Remote => {
|
||||
self.action_open_remote_file(entry, with);
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
70
src/ui/activities/filetransfer/actions/mkdir.rs
Normal file
@@ -0,0 +1,70 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use super::{FileTransferActivity, LogLevel};
|
||||
use std::path::PathBuf;
|
||||
|
||||
impl FileTransferActivity {
|
||||
pub(crate) fn action_local_mkdir(&mut self, input: String) {
|
||||
match self.host.mkdir(PathBuf::from(input.as_str()).as_path()) {
|
||||
Ok(_) => {
|
||||
// Reload files
|
||||
self.log(LogLevel::Info, format!("Created directory \"{}\"", input));
|
||||
// Reload entries
|
||||
self.reload_local_dir();
|
||||
}
|
||||
Err(err) => {
|
||||
// Report err
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not create directory \"{}\": {}", input, err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
pub(crate) fn action_remote_mkdir(&mut self, input: String) {
|
||||
match self
|
||||
.client
|
||||
.as_mut()
|
||||
.mkdir(PathBuf::from(input.as_str()).as_path())
|
||||
{
|
||||
Ok(_) => {
|
||||
// Reload files
|
||||
self.log(LogLevel::Info, format!("Created directory \"{}\"", input));
|
||||
self.reload_remote_dir();
|
||||
}
|
||||
Err(err) => {
|
||||
// Report err
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not create directory \"{}\": {}", input, err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
149
src/ui/activities/filetransfer/actions/mod.rs
Normal file
@@ -0,0 +1,149 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
pub(self) use super::{FileTransferActivity, FsEntry, LogLevel, TransferPayload};
|
||||
use tuirealm::{Payload, Value};
|
||||
|
||||
// actions
|
||||
pub(crate) mod change_dir;
|
||||
pub(crate) mod copy;
|
||||
pub(crate) mod delete;
|
||||
pub(crate) mod edit;
|
||||
pub(crate) mod exec;
|
||||
pub(crate) mod find;
|
||||
pub(crate) mod mkdir;
|
||||
pub(crate) mod newfile;
|
||||
pub(crate) mod open;
|
||||
pub(crate) mod rename;
|
||||
pub(crate) mod save;
|
||||
pub(crate) mod submit;
|
||||
|
||||
#[derive(Debug)]
|
||||
pub(crate) enum SelectedEntry {
|
||||
One(FsEntry),
|
||||
Many(Vec<FsEntry>),
|
||||
None,
|
||||
}
|
||||
|
||||
#[derive(Debug)]
|
||||
enum SelectedEntryIndex {
|
||||
One(usize),
|
||||
Many(Vec<usize>),
|
||||
None,
|
||||
}
|
||||
|
||||
impl From<Option<&FsEntry>> for SelectedEntry {
|
||||
fn from(opt: Option<&FsEntry>) -> Self {
|
||||
match opt {
|
||||
Some(e) => SelectedEntry::One(e.clone()),
|
||||
None => SelectedEntry::None,
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
impl From<Vec<&FsEntry>> for SelectedEntry {
|
||||
fn from(files: Vec<&FsEntry>) -> Self {
|
||||
SelectedEntry::Many(files.into_iter().cloned().collect())
|
||||
}
|
||||
}
|
||||
|
||||
impl FileTransferActivity {
|
||||
/// ### get_local_selected_entries
|
||||
///
|
||||
/// Get local file entry
|
||||
pub(crate) fn get_local_selected_entries(&self) -> SelectedEntry {
|
||||
match self.get_selected_index(super::COMPONENT_EXPLORER_LOCAL) {
|
||||
SelectedEntryIndex::One(idx) => SelectedEntry::from(self.local().get(idx)),
|
||||
SelectedEntryIndex::Many(files) => {
|
||||
let files: Vec<&FsEntry> = files
|
||||
.iter()
|
||||
.map(|x| self.local().get(*x)) // Usize to Option<FsEntry>
|
||||
.flatten()
|
||||
.collect();
|
||||
SelectedEntry::from(files)
|
||||
}
|
||||
SelectedEntryIndex::None => SelectedEntry::None,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### get_remote_selected_entries
|
||||
///
|
||||
/// Get remote file entry
|
||||
pub(crate) fn get_remote_selected_entries(&self) -> SelectedEntry {
|
||||
match self.get_selected_index(super::COMPONENT_EXPLORER_REMOTE) {
|
||||
SelectedEntryIndex::One(idx) => SelectedEntry::from(self.remote().get(idx)),
|
||||
SelectedEntryIndex::Many(files) => {
|
||||
let files: Vec<&FsEntry> = files
|
||||
.iter()
|
||||
.map(|x| self.remote().get(*x)) // Usize to Option<FsEntry>
|
||||
.flatten()
|
||||
.collect();
|
||||
SelectedEntry::from(files)
|
||||
}
|
||||
SelectedEntryIndex::None => SelectedEntry::None,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### get_remote_selected_entries
|
||||
///
|
||||
/// Get remote file entry
|
||||
pub(crate) fn get_found_selected_entries(&self) -> SelectedEntry {
|
||||
match self.get_selected_index(super::COMPONENT_EXPLORER_FIND) {
|
||||
SelectedEntryIndex::One(idx) => {
|
||||
SelectedEntry::from(self.found().as_ref().unwrap().get(idx))
|
||||
}
|
||||
SelectedEntryIndex::Many(files) => {
|
||||
let files: Vec<&FsEntry> = files
|
||||
.iter()
|
||||
.map(|x| self.found().as_ref().unwrap().get(*x)) // Usize to Option<FsEntry>
|
||||
.flatten()
|
||||
.collect();
|
||||
SelectedEntry::from(files)
|
||||
}
|
||||
SelectedEntryIndex::None => SelectedEntry::None,
|
||||
}
|
||||
}
|
||||
|
||||
// -- private
|
||||
|
||||
fn get_selected_index(&self, component: &str) -> SelectedEntryIndex {
|
||||
match self.view.get_state(component) {
|
||||
Some(Payload::One(Value::Usize(idx))) => SelectedEntryIndex::One(idx),
|
||||
Some(Payload::Vec(files)) => {
|
||||
let list: Vec<usize> = files
|
||||
.iter()
|
||||
.map(|x| match x {
|
||||
Value::Usize(v) => *v,
|
||||
_ => 0,
|
||||
})
|
||||
.collect();
|
||||
SelectedEntryIndex::Many(list)
|
||||
}
|
||||
_ => SelectedEntryIndex::None,
|
||||
}
|
||||
}
|
||||
}
|
||||
128
src/ui/activities/filetransfer/actions/newfile.rs
Normal file
@@ -0,0 +1,128 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use super::{FileTransferActivity, FsEntry, LogLevel};
|
||||
use std::path::PathBuf;
|
||||
|
||||
impl FileTransferActivity {
|
||||
pub(crate) fn action_local_newfile(&mut self, input: String) {
|
||||
// Check if file exists
|
||||
let mut file_exists: bool = false;
|
||||
for file in self.local().iter_files_all() {
|
||||
if input == file.get_name() {
|
||||
file_exists = true;
|
||||
}
|
||||
}
|
||||
if file_exists {
|
||||
self.log_and_alert(
|
||||
LogLevel::Warn,
|
||||
format!("File \"{}\" already exists", input,),
|
||||
);
|
||||
return;
|
||||
}
|
||||
// Create file
|
||||
let file_path: PathBuf = PathBuf::from(input.as_str());
|
||||
if let Err(err) = self.host.open_file_write(file_path.as_path()) {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not create file \"{}\": {}", file_path.display(), err),
|
||||
);
|
||||
} else {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Created file \"{}\"", file_path.display()),
|
||||
);
|
||||
}
|
||||
// Reload files
|
||||
self.reload_local_dir();
|
||||
}
|
||||
|
||||
pub(crate) fn action_remote_newfile(&mut self, input: String) {
|
||||
// Check if file exists
|
||||
let mut file_exists: bool = false;
|
||||
for file in self.remote().iter_files_all() {
|
||||
if input == file.get_name() {
|
||||
file_exists = true;
|
||||
}
|
||||
}
|
||||
if file_exists {
|
||||
self.log_and_alert(
|
||||
LogLevel::Warn,
|
||||
format!("File \"{}\" already exists", input,),
|
||||
);
|
||||
return;
|
||||
}
|
||||
// Get path on remote
|
||||
let file_path: PathBuf = PathBuf::from(input.as_str());
|
||||
// Create file (on local)
|
||||
match tempfile::NamedTempFile::new() {
|
||||
Err(err) => self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not create tempfile: {}", err),
|
||||
),
|
||||
Ok(tfile) => {
|
||||
// Stat tempfile
|
||||
let local_file: FsEntry = match self.host.stat(tfile.path()) {
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not stat tempfile: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
Ok(f) => f,
|
||||
};
|
||||
if let FsEntry::File(local_file) = local_file {
|
||||
// Create file
|
||||
match self.client.send_file(&local_file, file_path.as_path()) {
|
||||
Err(err) => self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not create file \"{}\": {}", file_path.display(), err),
|
||||
),
|
||||
Ok(writer) => {
|
||||
// Finalize write
|
||||
if let Err(err) = self.client.on_sent(writer) {
|
||||
self.log_and_alert(
|
||||
LogLevel::Warn,
|
||||
format!("Could not finalize file: {}", err),
|
||||
);
|
||||
} else {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Created file \"{}\"", file_path.display()),
|
||||
);
|
||||
}
|
||||
// Reload files
|
||||
self.reload_remote_dir();
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
166
src/ui/activities/filetransfer/actions/open.rs
Normal file
@@ -0,0 +1,166 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use super::{FileTransferActivity, FsEntry, LogLevel, SelectedEntry, TransferPayload};
|
||||
// ext
|
||||
use std::path::{Path, PathBuf};
|
||||
|
||||
impl FileTransferActivity {
|
||||
/// ### action_open_local
|
||||
///
|
||||
/// Open local file
|
||||
pub(crate) fn action_open_local(&mut self) {
|
||||
let entries: Vec<FsEntry> = match self.get_local_selected_entries() {
|
||||
SelectedEntry::One(entry) => vec![entry],
|
||||
SelectedEntry::Many(entries) => entries,
|
||||
SelectedEntry::None => vec![],
|
||||
};
|
||||
entries
|
||||
.iter()
|
||||
.for_each(|x| self.action_open_local_file(x, None));
|
||||
}
|
||||
|
||||
/// ### action_open_remote
|
||||
///
|
||||
/// Open local file
|
||||
pub(crate) fn action_open_remote(&mut self) {
|
||||
let entries: Vec<FsEntry> = match self.get_remote_selected_entries() {
|
||||
SelectedEntry::One(entry) => vec![entry],
|
||||
SelectedEntry::Many(entries) => entries,
|
||||
SelectedEntry::None => vec![],
|
||||
};
|
||||
entries
|
||||
.iter()
|
||||
.for_each(|x| self.action_open_remote_file(x, None));
|
||||
}
|
||||
|
||||
/// ### action_open_local_file
|
||||
///
|
||||
/// Perform open lopcal file
|
||||
pub(crate) fn action_open_local_file(&mut self, entry: &FsEntry, open_with: Option<&str>) {
|
||||
let entry: FsEntry = entry.get_realfile();
|
||||
self.open_path_with(entry.get_abs_path().as_path(), open_with);
|
||||
}
|
||||
|
||||
/// ### action_open_local
|
||||
///
|
||||
/// Open remote file. The file is first downloaded to a temporary directory on localhost
|
||||
pub(crate) fn action_open_remote_file(&mut self, entry: &FsEntry, open_with: Option<&str>) {
|
||||
let entry: FsEntry = entry.get_realfile();
|
||||
// Download file
|
||||
let tmpfile: String =
|
||||
match self.get_cache_tmp_name(entry.get_name(), entry.get_ftype().as_deref()) {
|
||||
None => {
|
||||
self.log(LogLevel::Error, String::from("Could not create tempdir"));
|
||||
return;
|
||||
}
|
||||
Some(p) => p,
|
||||
};
|
||||
let cache: PathBuf = match self.cache.as_ref() {
|
||||
None => {
|
||||
self.log(LogLevel::Error, String::from("Could not create tempdir"));
|
||||
return;
|
||||
}
|
||||
Some(p) => p.path().to_path_buf(),
|
||||
};
|
||||
match self.filetransfer_recv(
|
||||
TransferPayload::Any(entry),
|
||||
cache.as_path(),
|
||||
Some(tmpfile.clone()),
|
||||
) {
|
||||
Ok(_) => {
|
||||
// Make file and open if file exists
|
||||
let mut tmp: PathBuf = cache;
|
||||
tmp.push(tmpfile.as_str());
|
||||
if tmp.exists() {
|
||||
self.open_path_with(tmp.as_path(), open_with);
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
self.log(
|
||||
LogLevel::Error,
|
||||
format!("Failed to download remote entry: {}", err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### action_local_open_with
|
||||
///
|
||||
/// Open selected file with provided application
|
||||
pub(crate) fn action_local_open_with(&mut self, with: &str) {
|
||||
let entries: Vec<FsEntry> = match self.get_local_selected_entries() {
|
||||
SelectedEntry::One(entry) => vec![entry],
|
||||
SelectedEntry::Many(entries) => entries,
|
||||
SelectedEntry::None => vec![],
|
||||
};
|
||||
// Open all entries
|
||||
entries
|
||||
.iter()
|
||||
.for_each(|x| self.action_open_local_file(x, Some(with)));
|
||||
}
|
||||
|
||||
/// ### action_remote_open_with
|
||||
///
|
||||
/// Open selected file with provided application
|
||||
pub(crate) fn action_remote_open_with(&mut self, with: &str) {
|
||||
let entries: Vec<FsEntry> = match self.get_remote_selected_entries() {
|
||||
SelectedEntry::One(entry) => vec![entry],
|
||||
SelectedEntry::Many(entries) => entries,
|
||||
SelectedEntry::None => vec![],
|
||||
};
|
||||
// Open all entries
|
||||
entries
|
||||
.iter()
|
||||
.for_each(|x| self.action_open_remote_file(x, Some(with)));
|
||||
}
|
||||
|
||||
/// ### open_path_with
|
||||
///
|
||||
/// Common function which opens a path with default or specified program.
|
||||
fn open_path_with(&mut self, p: &Path, with: Option<&str>) {
|
||||
// Open file
|
||||
let result = match with {
|
||||
None => open::that(p),
|
||||
Some(with) => open::with(p, with),
|
||||
};
|
||||
// Log result
|
||||
match result {
|
||||
Ok(_) => self.log(LogLevel::Info, format!("Opened file `{}`", p.display())),
|
||||
Err(err) => self.log(
|
||||
LogLevel::Error,
|
||||
format!("Failed to open filoe `{}`: {}", p.display(), err),
|
||||
),
|
||||
}
|
||||
// NOTE: clear screen in order to prevent crap on stderr
|
||||
if let Some(ctx) = self.context.as_mut() {
|
||||
// Clear screen
|
||||
ctx.clear_screen();
|
||||
}
|
||||
}
|
||||
}
|
||||
128
src/ui/activities/filetransfer/actions/rename.rs
Normal file
@@ -0,0 +1,128 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use super::{FileTransferActivity, FsEntry, LogLevel, SelectedEntry};
|
||||
use std::path::{Path, PathBuf};
|
||||
|
||||
impl FileTransferActivity {
|
||||
pub(crate) fn action_local_rename(&mut self, input: String) {
|
||||
match self.get_local_selected_entries() {
|
||||
SelectedEntry::One(entry) => {
|
||||
let dest_path: PathBuf = PathBuf::from(input);
|
||||
self.local_rename_file(&entry, dest_path.as_path());
|
||||
// Reload entries
|
||||
self.reload_local_dir();
|
||||
}
|
||||
SelectedEntry::Many(entries) => {
|
||||
// Try to copy each file to Input/{FILE_NAME}
|
||||
let base_path: PathBuf = PathBuf::from(input);
|
||||
// Iter files
|
||||
for entry in entries.iter() {
|
||||
let mut dest_path: PathBuf = base_path.clone();
|
||||
dest_path.push(entry.get_name());
|
||||
self.local_rename_file(entry, dest_path.as_path());
|
||||
}
|
||||
// Reload entries
|
||||
self.reload_local_dir();
|
||||
}
|
||||
SelectedEntry::None => {}
|
||||
}
|
||||
}
|
||||
|
||||
pub(crate) fn action_remote_rename(&mut self, input: String) {
|
||||
match self.get_remote_selected_entries() {
|
||||
SelectedEntry::One(entry) => {
|
||||
let dest_path: PathBuf = PathBuf::from(input);
|
||||
self.remote_rename_file(&entry, dest_path.as_path());
|
||||
// Reload entries
|
||||
self.reload_remote_dir();
|
||||
}
|
||||
SelectedEntry::Many(entries) => {
|
||||
// Try to copy each file to Input/{FILE_NAME}
|
||||
let base_path: PathBuf = PathBuf::from(input);
|
||||
// Iter files
|
||||
for entry in entries.iter() {
|
||||
let mut dest_path: PathBuf = base_path.clone();
|
||||
dest_path.push(entry.get_name());
|
||||
self.remote_rename_file(entry, dest_path.as_path());
|
||||
}
|
||||
// Reload entries
|
||||
self.reload_remote_dir();
|
||||
}
|
||||
SelectedEntry::None => {}
|
||||
}
|
||||
}
|
||||
|
||||
fn local_rename_file(&mut self, entry: &FsEntry, dest: &Path) {
|
||||
match self.host.rename(entry, dest) {
|
||||
Ok(_) => {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!(
|
||||
"Moved \"{}\" to \"{}\"",
|
||||
entry.get_abs_path().display(),
|
||||
dest.display()
|
||||
),
|
||||
);
|
||||
}
|
||||
Err(err) => self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not move \"{}\" to \"{}\": {}",
|
||||
entry.get_abs_path().display(),
|
||||
dest.display(),
|
||||
err
|
||||
),
|
||||
),
|
||||
}
|
||||
}
|
||||
|
||||
fn remote_rename_file(&mut self, entry: &FsEntry, dest: &Path) {
|
||||
match self.client.as_mut().rename(entry, dest) {
|
||||
Ok(_) => {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!(
|
||||
"Moved \"{}\" to \"{}\"",
|
||||
entry.get_abs_path().display(),
|
||||
dest.display()
|
||||
),
|
||||
);
|
||||
}
|
||||
Err(err) => self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not move \"{}\" to \"{}\": {}",
|
||||
entry.get_abs_path().display(),
|
||||
dest.display(),
|
||||
err
|
||||
),
|
||||
),
|
||||
}
|
||||
}
|
||||
}
|
||||
136
src/ui/activities/filetransfer/actions/save.rs
Normal file
@@ -0,0 +1,136 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use super::{FileTransferActivity, LogLevel, SelectedEntry, TransferPayload};
|
||||
use std::path::PathBuf;
|
||||
|
||||
impl FileTransferActivity {
|
||||
pub(crate) fn action_local_saveas(&mut self, input: String) {
|
||||
self.action_local_send_file(Some(input));
|
||||
}
|
||||
|
||||
pub(crate) fn action_remote_saveas(&mut self, input: String) {
|
||||
self.action_remote_recv_file(Some(input));
|
||||
}
|
||||
|
||||
pub(crate) fn action_local_send(&mut self) {
|
||||
self.action_local_send_file(None);
|
||||
}
|
||||
|
||||
pub(crate) fn action_remote_recv(&mut self) {
|
||||
self.action_remote_recv_file(None);
|
||||
}
|
||||
|
||||
fn action_local_send_file(&mut self, save_as: Option<String>) {
|
||||
let wrkdir: PathBuf = self.remote().wrkdir.clone();
|
||||
match self.get_local_selected_entries() {
|
||||
SelectedEntry::One(entry) => {
|
||||
if let Err(err) = self.filetransfer_send(
|
||||
TransferPayload::Any(entry.get_realfile()),
|
||||
wrkdir.as_path(),
|
||||
save_as,
|
||||
) {
|
||||
{
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not upload file: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
}
|
||||
}
|
||||
SelectedEntry::Many(entries) => {
|
||||
// In case of selection: save multiple files in wrkdir/input
|
||||
let mut dest_path: PathBuf = wrkdir;
|
||||
if let Some(save_as) = save_as {
|
||||
dest_path.push(save_as);
|
||||
}
|
||||
// Iter files
|
||||
let entries = entries.iter().map(|x| x.get_realfile()).collect();
|
||||
if let Err(err) = self.filetransfer_send(
|
||||
TransferPayload::Many(entries),
|
||||
dest_path.as_path(),
|
||||
None,
|
||||
) {
|
||||
{
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not upload file: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
}
|
||||
}
|
||||
SelectedEntry::None => {}
|
||||
}
|
||||
}
|
||||
|
||||
fn action_remote_recv_file(&mut self, save_as: Option<String>) {
|
||||
let wrkdir: PathBuf = self.local().wrkdir.clone();
|
||||
match self.get_remote_selected_entries() {
|
||||
SelectedEntry::One(entry) => {
|
||||
if let Err(err) = self.filetransfer_recv(
|
||||
TransferPayload::Any(entry.get_realfile()),
|
||||
wrkdir.as_path(),
|
||||
save_as,
|
||||
) {
|
||||
{
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not download file: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
}
|
||||
}
|
||||
SelectedEntry::Many(entries) => {
|
||||
// In case of selection: save multiple files in wrkdir/input
|
||||
let mut dest_path: PathBuf = wrkdir;
|
||||
if let Some(save_as) = save_as {
|
||||
dest_path.push(save_as);
|
||||
}
|
||||
// Iter files
|
||||
let entries = entries.iter().map(|x| x.get_realfile()).collect();
|
||||
if let Err(err) = self.filetransfer_recv(
|
||||
TransferPayload::Many(entries),
|
||||
dest_path.as_path(),
|
||||
None,
|
||||
) {
|
||||
{
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not download file: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
}
|
||||
}
|
||||
SelectedEntry::None => {}
|
||||
}
|
||||
}
|
||||
}
|
||||
88
src/ui/activities/filetransfer/actions/submit.rs
Normal file
@@ -0,0 +1,88 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use super::{FileTransferActivity, FsEntry};
|
||||
|
||||
enum SubmitAction {
|
||||
ChangeDir,
|
||||
None,
|
||||
}
|
||||
|
||||
impl FileTransferActivity {
|
||||
/// ### action_submit_local
|
||||
///
|
||||
/// Decides which action to perform on submit for local explorer
|
||||
/// Return true whether the directory changed
|
||||
pub(crate) fn action_submit_local(&mut self, entry: FsEntry) -> bool {
|
||||
let action: SubmitAction = match &entry {
|
||||
FsEntry::Directory(_) => SubmitAction::ChangeDir,
|
||||
FsEntry::File(file) => {
|
||||
match &file.symlink {
|
||||
Some(symlink_entry) => {
|
||||
// If symlink and is directory, point to symlink
|
||||
match &**symlink_entry {
|
||||
FsEntry::Directory(_) => SubmitAction::ChangeDir,
|
||||
_ => SubmitAction::None,
|
||||
}
|
||||
}
|
||||
None => SubmitAction::None,
|
||||
}
|
||||
}
|
||||
};
|
||||
match action {
|
||||
SubmitAction::ChangeDir => self.action_enter_local_dir(entry, false),
|
||||
SubmitAction::None => false,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### action_submit_remote
|
||||
///
|
||||
/// Decides which action to perform on submit for remote explorer
|
||||
/// Return true whether the directory changed
|
||||
pub(crate) fn action_submit_remote(&mut self, entry: FsEntry) -> bool {
|
||||
let action: SubmitAction = match &entry {
|
||||
FsEntry::Directory(_) => SubmitAction::ChangeDir,
|
||||
FsEntry::File(file) => {
|
||||
match &file.symlink {
|
||||
Some(symlink_entry) => {
|
||||
// If symlink and is directory, point to symlink
|
||||
match &**symlink_entry {
|
||||
FsEntry::Directory(_) => SubmitAction::ChangeDir,
|
||||
_ => SubmitAction::None,
|
||||
}
|
||||
}
|
||||
None => SubmitAction::None,
|
||||
}
|
||||
}
|
||||
};
|
||||
match action {
|
||||
SubmitAction::ChangeDir => self.action_enter_remote_dir(entry, false),
|
||||
SubmitAction::None => false,
|
||||
}
|
||||
}
|
||||
}
|
||||
164
src/ui/activities/filetransfer/lib/browser.rs
Normal file
@@ -0,0 +1,164 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
use crate::fs::explorer::{builder::FileExplorerBuilder, FileExplorer, FileSorting, GroupDirs};
|
||||
use crate::fs::FsEntry;
|
||||
use crate::system::config_client::ConfigClient;
|
||||
|
||||
/// ## FileExplorerTab
|
||||
///
|
||||
/// File explorer tab
|
||||
#[derive(Clone, Copy)]
|
||||
pub enum FileExplorerTab {
|
||||
Local,
|
||||
Remote,
|
||||
FindLocal, // Find result tab
|
||||
FindRemote, // Find result tab
|
||||
}
|
||||
|
||||
/// ## Browser
|
||||
///
|
||||
/// Browser contains the browser options
|
||||
pub struct Browser {
|
||||
local: FileExplorer, // Local File explorer state
|
||||
remote: FileExplorer, // Remote File explorer state
|
||||
found: Option<FileExplorer>, // File explorer for find result
|
||||
tab: FileExplorerTab, // Current selected tab
|
||||
pub sync_browsing: bool,
|
||||
}
|
||||
|
||||
impl Browser {
|
||||
/// ### new
|
||||
///
|
||||
/// Build a new `Browser` struct
|
||||
pub fn new(cli: &ConfigClient) -> Self {
|
||||
Self {
|
||||
local: Self::build_local_explorer(cli),
|
||||
remote: Self::build_remote_explorer(cli),
|
||||
found: None,
|
||||
tab: FileExplorerTab::Local,
|
||||
sync_browsing: false,
|
||||
}
|
||||
}
|
||||
|
||||
pub fn local(&self) -> &FileExplorer {
|
||||
&self.local
|
||||
}
|
||||
|
||||
pub fn local_mut(&mut self) -> &mut FileExplorer {
|
||||
&mut self.local
|
||||
}
|
||||
|
||||
pub fn remote(&self) -> &FileExplorer {
|
||||
&self.remote
|
||||
}
|
||||
|
||||
pub fn remote_mut(&mut self) -> &mut FileExplorer {
|
||||
&mut self.remote
|
||||
}
|
||||
|
||||
pub fn found(&self) -> Option<&FileExplorer> {
|
||||
self.found.as_ref()
|
||||
}
|
||||
|
||||
pub fn found_mut(&mut self) -> Option<&mut FileExplorer> {
|
||||
self.found.as_mut()
|
||||
}
|
||||
|
||||
pub fn set_found(&mut self, files: Vec<FsEntry>) {
|
||||
let mut explorer = Self::build_found_explorer();
|
||||
explorer.set_files(files);
|
||||
self.found = Some(explorer);
|
||||
}
|
||||
|
||||
pub fn del_found(&mut self) {
|
||||
self.found = None;
|
||||
}
|
||||
|
||||
pub fn tab(&self) -> FileExplorerTab {
|
||||
self.tab
|
||||
}
|
||||
|
||||
/// ### change_tab
|
||||
///
|
||||
/// Update tab value
|
||||
pub fn change_tab(&mut self, tab: FileExplorerTab) {
|
||||
self.tab = tab;
|
||||
}
|
||||
|
||||
/// ### toggle_sync_browsing
|
||||
///
|
||||
/// Invert the current state for the sync browsing
|
||||
pub fn toggle_sync_browsing(&mut self) {
|
||||
self.sync_browsing = !self.sync_browsing;
|
||||
}
|
||||
|
||||
/// ### build_local_explorer
|
||||
///
|
||||
/// Build a file explorer with local host setup
|
||||
pub fn build_local_explorer(cli: &ConfigClient) -> FileExplorer {
|
||||
let mut builder = Self::build_explorer(cli);
|
||||
builder.with_formatter(cli.get_local_file_fmt().as_deref());
|
||||
builder.build()
|
||||
}
|
||||
|
||||
/// ### build_remote_explorer
|
||||
///
|
||||
/// Build a file explorer with remote host setup
|
||||
pub fn build_remote_explorer(cli: &ConfigClient) -> FileExplorer {
|
||||
let mut builder = Self::build_explorer(cli);
|
||||
builder.with_formatter(cli.get_remote_file_fmt().as_deref());
|
||||
builder.build()
|
||||
}
|
||||
|
||||
/// ### build_explorer
|
||||
///
|
||||
/// Build explorer reading configuration from `ConfigClient`
|
||||
fn build_explorer(cli: &ConfigClient) -> FileExplorerBuilder {
|
||||
let mut builder: FileExplorerBuilder = FileExplorerBuilder::new();
|
||||
// Set common keys
|
||||
builder
|
||||
.with_file_sorting(FileSorting::Name)
|
||||
.with_stack_size(16)
|
||||
.with_group_dirs(cli.get_group_dirs())
|
||||
.with_hidden_files(cli.get_show_hidden_files());
|
||||
builder
|
||||
}
|
||||
|
||||
/// ### build_found_explorer
|
||||
///
|
||||
/// Build explorer reading from `ConfigClient`, for found result (has some differences)
|
||||
fn build_found_explorer() -> FileExplorer {
|
||||
FileExplorerBuilder::new()
|
||||
.with_file_sorting(FileSorting::Name)
|
||||
.with_group_dirs(Some(GroupDirs::First))
|
||||
.with_hidden_files(true)
|
||||
.with_stack_size(0)
|
||||
.with_formatter(Some("{NAME:32} {SYMLINK}"))
|
||||
.build()
|
||||
}
|
||||
}
|
||||
29
src/ui/activities/filetransfer/lib/mod.rs
Normal file
@@ -0,0 +1,29 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
pub(crate) mod browser;
|
||||
pub(crate) mod transfer;
|
||||
259
src/ui/activities/filetransfer/lib/transfer.rs
Normal file
@@ -0,0 +1,259 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
use bytesize::ByteSize;
|
||||
use std::fmt;
|
||||
use std::time::Instant;
|
||||
|
||||
/// ### TransferStates
|
||||
///
|
||||
/// TransferStates contains the states related to the transfer process
|
||||
pub struct TransferStates {
|
||||
aborted: bool, // Describes whether the transfer process has been aborted
|
||||
pub full: ProgressStates, // full transfer states
|
||||
pub partial: ProgressStates, // Partial transfer states
|
||||
}
|
||||
|
||||
/// ### ProgressStates
|
||||
///
|
||||
/// Progress states describes the states for the progress of a single transfer part
|
||||
pub struct ProgressStates {
|
||||
started: Instant,
|
||||
total: usize,
|
||||
written: usize,
|
||||
}
|
||||
|
||||
impl Default for TransferStates {
|
||||
fn default() -> Self {
|
||||
Self::new()
|
||||
}
|
||||
}
|
||||
|
||||
impl TransferStates {
|
||||
/// ### new
|
||||
///
|
||||
/// Instantiates a new transfer states
|
||||
pub fn new() -> TransferStates {
|
||||
TransferStates {
|
||||
aborted: false,
|
||||
full: ProgressStates::default(),
|
||||
partial: ProgressStates::default(),
|
||||
}
|
||||
}
|
||||
|
||||
/// ### reset
|
||||
///
|
||||
/// Re-intiialize transfer states
|
||||
pub fn reset(&mut self) {
|
||||
self.aborted = false;
|
||||
}
|
||||
|
||||
/// ### abort
|
||||
///
|
||||
/// Set aborted to true
|
||||
pub fn abort(&mut self) {
|
||||
self.aborted = true;
|
||||
}
|
||||
|
||||
/// ### aborted
|
||||
///
|
||||
/// Returns whether transfer has been aborted
|
||||
pub fn aborted(&self) -> bool {
|
||||
self.aborted
|
||||
}
|
||||
}
|
||||
|
||||
impl Default for ProgressStates {
|
||||
fn default() -> Self {
|
||||
ProgressStates {
|
||||
started: Instant::now(),
|
||||
written: 0,
|
||||
total: 0,
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
impl fmt::Display for ProgressStates {
|
||||
fn fmt(&self, f: &mut fmt::Formatter<'_>) -> fmt::Result {
|
||||
let eta: String = match self.calc_eta() {
|
||||
0 => String::from("--:--"),
|
||||
seconds => format!(
|
||||
"{:0width$}:{:0width$}",
|
||||
(seconds / 60),
|
||||
(seconds % 60),
|
||||
width = 2
|
||||
),
|
||||
};
|
||||
write!(
|
||||
f,
|
||||
"{:.2}% - ETA {} ({}/s)",
|
||||
self.calc_progress_percentage(),
|
||||
eta,
|
||||
ByteSize(self.calc_bytes_per_second())
|
||||
)
|
||||
}
|
||||
}
|
||||
|
||||
impl ProgressStates {
|
||||
/// ### init
|
||||
///
|
||||
/// Initialize a new Progress State
|
||||
pub fn init(&mut self, sz: usize) {
|
||||
self.started = Instant::now();
|
||||
self.total = sz;
|
||||
self.written = 0;
|
||||
}
|
||||
|
||||
/// ### update_progress
|
||||
///
|
||||
/// Update progress state
|
||||
pub fn update_progress(&mut self, delta: usize) -> f64 {
|
||||
self.written += delta;
|
||||
self.calc_progress_percentage()
|
||||
}
|
||||
|
||||
/// ### calc_progress
|
||||
///
|
||||
/// Calculate progress in a range between 0.0 to 1.0
|
||||
pub fn calc_progress(&self) -> f64 {
|
||||
let prog: f64 = (self.written as f64) / (self.total as f64);
|
||||
match prog > 1.0 {
|
||||
true => 1.0,
|
||||
false => prog,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### started
|
||||
///
|
||||
/// Get started
|
||||
pub fn started(&self) -> Instant {
|
||||
self.started
|
||||
}
|
||||
|
||||
/// ### calc_progress_percentage
|
||||
///
|
||||
/// Calculate the current transfer progress as percentage
|
||||
fn calc_progress_percentage(&self) -> f64 {
|
||||
self.calc_progress() * 100.0
|
||||
}
|
||||
|
||||
/// ### calc_bytes_per_second
|
||||
///
|
||||
/// Generic function to calculate bytes per second using elapsed time since transfer started and the bytes written
|
||||
/// and the total amount of bytes to write
|
||||
pub fn calc_bytes_per_second(&self) -> u64 {
|
||||
// bytes_written : elapsed_secs = x : 1
|
||||
let elapsed_secs: u64 = self.started.elapsed().as_secs();
|
||||
match elapsed_secs {
|
||||
0 => match self.written == self.total {
|
||||
// NOTE: would divide by 0 :D
|
||||
true => self.total as u64, // Download completed in less than 1 second
|
||||
false => 0, // 0 B/S
|
||||
},
|
||||
_ => self.written as u64 / elapsed_secs,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### calc_eta
|
||||
///
|
||||
/// Calculate ETA for current transfer as seconds
|
||||
fn calc_eta(&self) -> u64 {
|
||||
let elapsed_secs: u64 = self.started.elapsed().as_secs();
|
||||
let prog: f64 = self.calc_progress_percentage();
|
||||
match prog as u64 {
|
||||
0 => 0,
|
||||
_ => ((elapsed_secs * 100) / (prog as u64)) - elapsed_secs,
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
#[cfg(test)]
|
||||
mod test {
|
||||
|
||||
use super::*;
|
||||
|
||||
use pretty_assertions::assert_eq;
|
||||
use std::time::Duration;
|
||||
|
||||
#[test]
|
||||
fn test_ui_activities_filetransfer_lib_transfer_progress_states() {
|
||||
let mut states: ProgressStates = ProgressStates::default();
|
||||
assert_eq!(states.total, 0);
|
||||
assert_eq!(states.written, 0);
|
||||
assert!(states.started().elapsed().as_secs() < 5);
|
||||
// Init new transfer
|
||||
states.init(1024);
|
||||
assert_eq!(states.total, 1024);
|
||||
assert_eq!(states.written, 0);
|
||||
assert_eq!(states.calc_bytes_per_second(), 0);
|
||||
assert_eq!(states.calc_eta(), 0);
|
||||
assert_eq!(states.calc_progress_percentage(), 0.0);
|
||||
assert_eq!(states.calc_progress(), 0.0);
|
||||
assert_eq!(states.to_string().as_str(), "0.00% - ETA --:-- (0 B/s)");
|
||||
// Wait 4 second (virtually)
|
||||
states.started = states.started.checked_sub(Duration::from_secs(4)).unwrap();
|
||||
// Update state
|
||||
states.update_progress(256);
|
||||
assert_eq!(states.total, 1024);
|
||||
assert_eq!(states.written, 256);
|
||||
assert_eq!(states.calc_bytes_per_second(), 64); // 256 bytes in 4 seconds
|
||||
assert_eq!(states.calc_eta(), 12); // 16 total sub 4
|
||||
assert_eq!(states.calc_progress_percentage(), 25.0);
|
||||
assert_eq!(states.calc_progress(), 0.25);
|
||||
assert_eq!(states.to_string().as_str(), "25.00% - ETA 00:12 (64 B/s)");
|
||||
// 100%
|
||||
states.started = states.started.checked_sub(Duration::from_secs(12)).unwrap();
|
||||
states.update_progress(768);
|
||||
assert_eq!(states.total, 1024);
|
||||
assert_eq!(states.written, 1024);
|
||||
assert_eq!(states.calc_bytes_per_second(), 64); // 256 bytes in 4 seconds
|
||||
assert_eq!(states.calc_eta(), 0); // 16 total sub 4
|
||||
assert_eq!(states.calc_progress_percentage(), 100.0);
|
||||
assert_eq!(states.calc_progress(), 1.0);
|
||||
assert_eq!(states.to_string().as_str(), "100.00% - ETA --:-- (64 B/s)");
|
||||
// Check if terminated at started
|
||||
states.started = Instant::now();
|
||||
assert_eq!(states.calc_bytes_per_second(), 1024);
|
||||
}
|
||||
|
||||
#[test]
|
||||
fn test_ui_activities_filetransfer_lib_transfer_states() {
|
||||
let mut states: TransferStates = TransferStates::default();
|
||||
assert_eq!(states.aborted, false);
|
||||
assert_eq!(states.full.total, 0);
|
||||
assert_eq!(states.full.written, 0);
|
||||
assert!(states.full.started.elapsed().as_secs() < 5);
|
||||
assert_eq!(states.partial.total, 0);
|
||||
assert_eq!(states.partial.written, 0);
|
||||
assert!(states.partial.started.elapsed().as_secs() < 5);
|
||||
// Aborted
|
||||
states.abort();
|
||||
assert_eq!(states.aborted(), true);
|
||||
states.reset();
|
||||
assert_eq!(states.aborted(), false);
|
||||
}
|
||||
}
|
||||
@@ -23,22 +23,31 @@
|
||||
*/
|
||||
// Locals
|
||||
use super::{ConfigClient, FileTransferActivity, LogLevel, LogRecord};
|
||||
use crate::fs::explorer::{builder::FileExplorerBuilder, FileExplorer, FileSorting, GroupDirs};
|
||||
use crate::system::environment;
|
||||
use crate::system::sshkey_storage::SshKeyStorage;
|
||||
use crate::utils::path;
|
||||
// Ext
|
||||
use std::env;
|
||||
use std::path::PathBuf;
|
||||
use std::path::{Path, PathBuf};
|
||||
use tuirealm::Update;
|
||||
|
||||
const LOG_CAPACITY: usize = 256;
|
||||
|
||||
impl FileTransferActivity {
|
||||
/// ### log
|
||||
///
|
||||
/// Add message to log events
|
||||
pub(super) fn log(&mut self, level: LogLevel, msg: &str) {
|
||||
pub(super) fn log(&mut self, level: LogLevel, msg: String) {
|
||||
// Log to file
|
||||
match level {
|
||||
LogLevel::Error => error!("{}", msg),
|
||||
LogLevel::Info => info!("{}", msg),
|
||||
LogLevel::Warn => warn!("{}", msg),
|
||||
}
|
||||
// Create log record
|
||||
let record: LogRecord = LogRecord::new(level, msg);
|
||||
//Check if history overflows the size
|
||||
if self.log_records.len() + 1 > self.log_size {
|
||||
if self.log_records.len() + 1 > LOG_CAPACITY {
|
||||
self.log_records.pop_back(); // Start cleaning events from back
|
||||
}
|
||||
// Eventually push front the new record
|
||||
@@ -52,8 +61,8 @@ impl FileTransferActivity {
|
||||
///
|
||||
/// Add message to log events and also display it as an alert
|
||||
pub(super) fn log_and_alert(&mut self, level: LogLevel, msg: String) {
|
||||
self.log(level, msg.as_str());
|
||||
self.mount_error(msg.as_str());
|
||||
self.log(level, msg);
|
||||
// Update log
|
||||
let msg = self.update_logbox();
|
||||
self.update(msg);
|
||||
@@ -63,7 +72,7 @@ impl FileTransferActivity {
|
||||
///
|
||||
/// Initialize configuration client if possible.
|
||||
/// This function doesn't return errors.
|
||||
pub(super) fn init_config_client() -> Option<ConfigClient> {
|
||||
pub(super) fn init_config_client() -> ConfigClient {
|
||||
match environment::init_config_dir() {
|
||||
Ok(termscp_dir) => match termscp_dir {
|
||||
Some(termscp_dir) => {
|
||||
@@ -71,67 +80,28 @@ impl FileTransferActivity {
|
||||
let (config_path, ssh_keys_path): (PathBuf, PathBuf) =
|
||||
environment::get_config_paths(termscp_dir.as_path());
|
||||
match ConfigClient::new(config_path.as_path(), ssh_keys_path.as_path()) {
|
||||
Ok(config_client) => Some(config_client),
|
||||
Err(_) => None,
|
||||
Ok(config_client) => config_client,
|
||||
Err(_) => ConfigClient::degraded(),
|
||||
}
|
||||
}
|
||||
None => None,
|
||||
None => ConfigClient::degraded(),
|
||||
},
|
||||
Err(_) => None,
|
||||
Err(_) => ConfigClient::degraded(),
|
||||
}
|
||||
}
|
||||
|
||||
/// ### make_ssh_storage
|
||||
///
|
||||
/// Make ssh storage from `ConfigClient` if possible, empty otherwise
|
||||
pub(super) fn make_ssh_storage(cli: Option<&ConfigClient>) -> SshKeyStorage {
|
||||
match cli {
|
||||
Some(cli) => SshKeyStorage::storage_from_config(cli),
|
||||
None => SshKeyStorage::empty(),
|
||||
}
|
||||
}
|
||||
|
||||
/// ### build_explorer
|
||||
///
|
||||
/// Build explorer reading configuration from `ConfigClient`
|
||||
pub(super) fn build_explorer(cli: Option<&ConfigClient>) -> FileExplorer {
|
||||
match &cli {
|
||||
Some(cli) => FileExplorerBuilder::new() // Build according to current configuration
|
||||
.with_file_sorting(FileSorting::ByName)
|
||||
.with_group_dirs(cli.get_group_dirs())
|
||||
.with_hidden_files(cli.get_show_hidden_files())
|
||||
.with_stack_size(16)
|
||||
.with_formatter(cli.get_file_fmt().as_deref())
|
||||
.build(),
|
||||
None => FileExplorerBuilder::new() // Build default
|
||||
.with_file_sorting(FileSorting::ByName)
|
||||
.with_group_dirs(Some(GroupDirs::First))
|
||||
.with_stack_size(16)
|
||||
.build(),
|
||||
}
|
||||
}
|
||||
|
||||
/// ### build_found_explorer
|
||||
///
|
||||
/// Build explorer reading from `ConfigClient`, for found result (has some differences)
|
||||
pub(super) fn build_found_explorer() -> FileExplorer {
|
||||
FileExplorerBuilder::new()
|
||||
.with_file_sorting(FileSorting::ByName)
|
||||
.with_group_dirs(Some(GroupDirs::First))
|
||||
.with_hidden_files(true)
|
||||
.with_stack_size(0)
|
||||
.with_formatter(Some("{NAME} {SYMLINK}"))
|
||||
.build()
|
||||
/// Make ssh storage from `ConfigClient` if possible, empty otherwise (empty is implicit if degraded)
|
||||
pub(super) fn make_ssh_storage(cli: &ConfigClient) -> SshKeyStorage {
|
||||
SshKeyStorage::storage_from_config(cli)
|
||||
}
|
||||
|
||||
/// ### setup_text_editor
|
||||
///
|
||||
/// Set text editor to use
|
||||
pub(super) fn setup_text_editor(&self) {
|
||||
if let Some(config_cli) = self.context.as_ref().unwrap().config_client.as_ref() {
|
||||
// Set text editor
|
||||
env::set_var("EDITOR", config_cli.get_text_editor());
|
||||
}
|
||||
env::set_var("EDITOR", self.config().get_text_editor());
|
||||
}
|
||||
|
||||
/// ### read_input_event
|
||||
@@ -139,7 +109,7 @@ impl FileTransferActivity {
|
||||
/// Read one event.
|
||||
/// Returns whether at least one event has been handled
|
||||
pub(super) fn read_input_event(&mut self) -> bool {
|
||||
if let Ok(Some(event)) = self.context.as_ref().unwrap().input_hnd.read_event() {
|
||||
if let Ok(Some(event)) = self.context().input_hnd().read_event() {
|
||||
// Handle event
|
||||
let msg = self.view.on(event);
|
||||
self.update(msg);
|
||||
@@ -150,4 +120,18 @@ impl FileTransferActivity {
|
||||
false
|
||||
}
|
||||
}
|
||||
|
||||
/// ### local_to_abs_path
|
||||
///
|
||||
/// Convert a path to absolute according to local explorer
|
||||
pub(super) fn local_to_abs_path(&self, path: &Path) -> PathBuf {
|
||||
path::absolutize(self.local().wrkdir.as_path(), path)
|
||||
}
|
||||
|
||||
/// ### remote_to_abs_path
|
||||
///
|
||||
/// Convert a path to absolute according to remote explorer
|
||||
pub(super) fn remote_to_abs_path(&self, path: &Path) -> PathBuf {
|
||||
path::absolutize(self.remote().wrkdir.as_path(), path)
|
||||
}
|
||||
}
|
||||
@@ -26,40 +26,39 @@
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// This module is split into files, cause it's just too big
|
||||
mod actions;
|
||||
mod misc;
|
||||
mod session;
|
||||
mod update;
|
||||
mod view;
|
||||
|
||||
// Dependencies
|
||||
extern crate chrono;
|
||||
extern crate crossterm;
|
||||
extern crate textwrap;
|
||||
extern crate tui;
|
||||
pub(self) mod actions;
|
||||
pub(self) mod lib;
|
||||
pub(self) mod misc;
|
||||
pub(self) mod session;
|
||||
pub(self) mod update;
|
||||
pub(self) mod view;
|
||||
|
||||
// locals
|
||||
use super::{Activity, Context, ExitReason};
|
||||
use crate::config::themes::Theme;
|
||||
use crate::filetransfer::ftp_transfer::FtpFileTransfer;
|
||||
use crate::filetransfer::scp_transfer::ScpFileTransfer;
|
||||
use crate::filetransfer::sftp_transfer::SftpFileTransfer;
|
||||
use crate::filetransfer::{FileTransfer, FileTransferProtocol};
|
||||
use crate::fs::explorer::FileExplorer;
|
||||
use crate::fs::FsEntry;
|
||||
use crate::host::Localhost;
|
||||
use crate::system::config_client::ConfigClient;
|
||||
use crate::ui::layout::view::View;
|
||||
pub(self) use lib::browser;
|
||||
use lib::browser::Browser;
|
||||
use lib::transfer::TransferStates;
|
||||
pub(self) use session::TransferPayload;
|
||||
|
||||
// Includes
|
||||
use chrono::{DateTime, Local};
|
||||
use crossterm::terminal::{disable_raw_mode, enable_raw_mode};
|
||||
use std::collections::VecDeque;
|
||||
use std::path::PathBuf;
|
||||
use std::time::Instant;
|
||||
use tempfile::TempDir;
|
||||
use tuirealm::View;
|
||||
|
||||
// -- Storage keys
|
||||
|
||||
const STORAGE_EXPLORER_WIDTH: &str = "FILETRANSFER_EXPLORER_WIDTH";
|
||||
const STORAGE_LOGBOX_WIDTH: &str = "LOGBOX_WIDTH";
|
||||
|
||||
// -- components
|
||||
|
||||
@@ -67,7 +66,8 @@ const COMPONENT_EXPLORER_LOCAL: &str = "EXPLORER_LOCAL";
|
||||
const COMPONENT_EXPLORER_REMOTE: &str = "EXPLORER_REMOTE";
|
||||
const COMPONENT_EXPLORER_FIND: &str = "EXPLORER_FIND";
|
||||
const COMPONENT_LOG_BOX: &str = "LOG_BOX";
|
||||
const COMPONENT_PROGRESS_BAR: &str = "PROGRESS_BAR";
|
||||
const COMPONENT_PROGRESS_BAR_FULL: &str = "PROGRESS_BAR_FULL";
|
||||
const COMPONENT_PROGRESS_BAR_PARTIAL: &str = "PROGRESS_BAR_PARTIAL";
|
||||
const COMPONENT_TEXT_ERROR: &str = "TEXT_ERROR";
|
||||
const COMPONENT_TEXT_FATAL: &str = "TEXT_FATAL";
|
||||
const COMPONENT_TEXT_HELP: &str = "TEXT_HELP";
|
||||
@@ -78,24 +78,17 @@ const COMPONENT_INPUT_FIND: &str = "INPUT_FIND";
|
||||
const COMPONENT_INPUT_GOTO: &str = "INPUT_GOTO";
|
||||
const COMPONENT_INPUT_MKDIR: &str = "INPUT_MKDIR";
|
||||
const COMPONENT_INPUT_NEWFILE: &str = "INPUT_NEWFILE";
|
||||
const COMPONENT_INPUT_OPEN_WITH: &str = "INPUT_OPEN_WITH";
|
||||
const COMPONENT_INPUT_RENAME: &str = "INPUT_RENAME";
|
||||
const COMPONENT_INPUT_SAVEAS: &str = "INPUT_SAVEAS";
|
||||
const COMPONENT_RADIO_DELETE: &str = "RADIO_DELETE";
|
||||
const COMPONENT_RADIO_DISCONNECT: &str = "RADIO_DISCONNECT";
|
||||
const COMPONENT_RADIO_QUIT: &str = "RADIO_QUIT";
|
||||
const COMPONENT_RADIO_SORTING: &str = "RADIO_SORTING";
|
||||
const COMPONENT_SPAN_STATUS_BAR_LOCAL: &str = "STATUS_BAR_LOCAL";
|
||||
const COMPONENT_SPAN_STATUS_BAR_REMOTE: &str = "STATUS_BAR_REMOTE";
|
||||
const COMPONENT_LIST_FILEINFO: &str = "LIST_FILEINFO";
|
||||
|
||||
/// ## FileExplorerTab
|
||||
///
|
||||
/// File explorer tab
|
||||
enum FileExplorerTab {
|
||||
Local,
|
||||
Remote,
|
||||
FindLocal, // Find result tab
|
||||
FindRemote, // Find result tab
|
||||
}
|
||||
|
||||
/// ## LogLevel
|
||||
///
|
||||
/// Log level type
|
||||
@@ -118,90 +111,15 @@ impl LogRecord {
|
||||
/// ### new
|
||||
///
|
||||
/// Instantiates a new LogRecord
|
||||
pub fn new(level: LogLevel, msg: &str) -> LogRecord {
|
||||
pub fn new(level: LogLevel, msg: String) -> LogRecord {
|
||||
LogRecord {
|
||||
time: Local::now(),
|
||||
level,
|
||||
msg: String::from(msg),
|
||||
msg,
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### TransferStates
|
||||
///
|
||||
/// TransferStates contains the states related to the transfer process
|
||||
struct TransferStates {
|
||||
pub progress: f64, // Current read/write progress (percentage)
|
||||
pub started: Instant, // Instant the transfer process started
|
||||
pub aborted: bool, // Describes whether the transfer process has been aborted
|
||||
pub bytes_written: usize, // Bytes written during transfer
|
||||
pub bytes_total: usize, // Total bytes to write
|
||||
}
|
||||
|
||||
impl TransferStates {
|
||||
/// ### new
|
||||
///
|
||||
/// Instantiates a new transfer states
|
||||
pub fn new() -> TransferStates {
|
||||
TransferStates {
|
||||
progress: 0.0,
|
||||
started: Instant::now(),
|
||||
aborted: false,
|
||||
bytes_written: 0,
|
||||
bytes_total: 0,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### reset
|
||||
///
|
||||
/// Re-intiialize transfer states
|
||||
pub fn reset(&mut self) {
|
||||
self.progress = 0.0;
|
||||
self.started = Instant::now();
|
||||
self.aborted = false;
|
||||
self.bytes_written = 0;
|
||||
self.bytes_total = 0;
|
||||
}
|
||||
|
||||
/// ### set_progress
|
||||
///
|
||||
/// Calculate progress percentage based on current progress
|
||||
pub fn set_progress(&mut self, w: usize, sz: usize) {
|
||||
self.bytes_written = w;
|
||||
self.bytes_total = sz;
|
||||
let mut prog: f64 = ((self.bytes_written as f64) * 100.0) / (self.bytes_total as f64);
|
||||
// Check value
|
||||
if prog > 100.0 {
|
||||
prog = 100.0;
|
||||
} else if prog < 0.0 {
|
||||
prog = 0.0;
|
||||
}
|
||||
self.progress = prog;
|
||||
}
|
||||
|
||||
/// ### byte_per_second
|
||||
///
|
||||
/// Calculate bytes per second
|
||||
pub fn bytes_per_second(&self) -> u64 {
|
||||
// bytes_written : elapsed_secs = x : 1
|
||||
let elapsed_secs: u64 = self.started.elapsed().as_secs();
|
||||
match elapsed_secs {
|
||||
0 => match self.bytes_written == self.bytes_total {
|
||||
// NOTE: would divide by 0 :D
|
||||
true => self.bytes_total as u64, // Download completed in less than 1 second
|
||||
false => 0, // 0 B/S
|
||||
},
|
||||
_ => self.bytes_written as u64 / elapsed_secs,
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
impl Default for TransferStates {
|
||||
fn default() -> Self {
|
||||
Self::new()
|
||||
}
|
||||
}
|
||||
|
||||
/// ## FileTransferActivity
|
||||
///
|
||||
/// FileTransferActivity is the data holder for the file transfer activity
|
||||
@@ -209,45 +127,116 @@ pub struct FileTransferActivity {
|
||||
exit_reason: Option<ExitReason>, // Exit reason
|
||||
context: Option<Context>, // Context holder
|
||||
view: View, // View
|
||||
host: Localhost, // Localhost
|
||||
client: Box<dyn FileTransfer>, // File transfer client
|
||||
local: FileExplorer, // Local File explorer state
|
||||
remote: FileExplorer, // Remote File explorer state
|
||||
found: Option<FileExplorer>, // File explorer for find result
|
||||
tab: FileExplorerTab, // Current selected tab
|
||||
browser: Browser, // Browser
|
||||
log_records: VecDeque<LogRecord>, // Log records
|
||||
log_size: usize, // Log records size (max)
|
||||
transfer: TransferStates, // Transfer states
|
||||
cache: Option<TempDir>, // Temporary directory where to store stuff
|
||||
}
|
||||
|
||||
impl FileTransferActivity {
|
||||
/// ### new
|
||||
///
|
||||
/// Instantiates a new FileTransferActivity
|
||||
pub fn new(protocol: FileTransferProtocol) -> FileTransferActivity {
|
||||
pub fn new(host: Localhost, protocol: FileTransferProtocol) -> FileTransferActivity {
|
||||
// Get config client
|
||||
let config_client: Option<ConfigClient> = Self::init_config_client();
|
||||
let config_client: ConfigClient = Self::init_config_client();
|
||||
FileTransferActivity {
|
||||
exit_reason: None,
|
||||
context: None,
|
||||
view: View::init(),
|
||||
host,
|
||||
client: match protocol {
|
||||
FileTransferProtocol::Sftp => Box::new(SftpFileTransfer::new(
|
||||
Self::make_ssh_storage(config_client.as_ref()),
|
||||
Self::make_ssh_storage(&config_client),
|
||||
)),
|
||||
FileTransferProtocol::Ftp(ftps) => Box::new(FtpFileTransfer::new(ftps)),
|
||||
FileTransferProtocol::Scp => Box::new(ScpFileTransfer::new(
|
||||
Self::make_ssh_storage(config_client.as_ref()),
|
||||
)),
|
||||
FileTransferProtocol::Scp => {
|
||||
Box::new(ScpFileTransfer::new(Self::make_ssh_storage(&config_client)))
|
||||
}
|
||||
},
|
||||
local: Self::build_explorer(config_client.as_ref()),
|
||||
remote: Self::build_explorer(config_client.as_ref()),
|
||||
found: None,
|
||||
tab: FileExplorerTab::Local,
|
||||
browser: Browser::new(&config_client),
|
||||
log_records: VecDeque::with_capacity(256), // 256 events is enough I guess
|
||||
log_size: 256, // Must match with capacity
|
||||
transfer: TransferStates::default(),
|
||||
cache: match TempDir::new() {
|
||||
Ok(d) => Some(d),
|
||||
Err(_) => None,
|
||||
},
|
||||
}
|
||||
}
|
||||
|
||||
fn local(&self) -> &FileExplorer {
|
||||
self.browser.local()
|
||||
}
|
||||
|
||||
fn local_mut(&mut self) -> &mut FileExplorer {
|
||||
self.browser.local_mut()
|
||||
}
|
||||
|
||||
fn remote(&self) -> &FileExplorer {
|
||||
self.browser.remote()
|
||||
}
|
||||
|
||||
fn remote_mut(&mut self) -> &mut FileExplorer {
|
||||
self.browser.remote_mut()
|
||||
}
|
||||
|
||||
fn found(&self) -> Option<&FileExplorer> {
|
||||
self.browser.found()
|
||||
}
|
||||
|
||||
fn found_mut(&mut self) -> Option<&mut FileExplorer> {
|
||||
self.browser.found_mut()
|
||||
}
|
||||
|
||||
/// ### get_cache_tmp_name
|
||||
///
|
||||
/// Get file name for a file in cache
|
||||
fn get_cache_tmp_name(&self, name: &str, file_type: Option<&str>) -> Option<String> {
|
||||
self.cache.as_ref().map(|_| {
|
||||
let base: String = format!(
|
||||
"{}-{}",
|
||||
name,
|
||||
std::time::SystemTime::now()
|
||||
.duration_since(std::time::UNIX_EPOCH)
|
||||
.unwrap()
|
||||
.as_millis()
|
||||
);
|
||||
match file_type {
|
||||
None => base,
|
||||
Some(file_type) => format!("{}.{}", base, file_type),
|
||||
}
|
||||
})
|
||||
}
|
||||
|
||||
/// ### context
|
||||
///
|
||||
/// Returns a reference to context
|
||||
fn context(&self) -> &Context {
|
||||
self.context.as_ref().unwrap()
|
||||
}
|
||||
|
||||
/// ### context_mut
|
||||
///
|
||||
/// Returns a mutable reference to context
|
||||
fn context_mut(&mut self) -> &mut Context {
|
||||
self.context.as_mut().unwrap()
|
||||
}
|
||||
|
||||
/// ### config
|
||||
///
|
||||
/// Returns config client reference
|
||||
fn config(&self) -> &ConfigClient {
|
||||
self.context().config()
|
||||
}
|
||||
|
||||
/// ### theme
|
||||
///
|
||||
/// Get a reference to `Theme`
|
||||
fn theme(&self) -> &Theme {
|
||||
self.context().theme_provider().theme()
|
||||
}
|
||||
}
|
||||
|
||||
/**
|
||||
@@ -262,25 +251,30 @@ impl Activity for FileTransferActivity {
|
||||
/// `on_create` is the function which must be called to initialize the activity.
|
||||
/// `on_create` must initialize all the data structures used by the activity
|
||||
fn on_create(&mut self, context: Context) {
|
||||
debug!("Initializing activity...");
|
||||
// Set context
|
||||
self.context = Some(context);
|
||||
// Clear terminal
|
||||
self.context.as_mut().unwrap().clear_screen();
|
||||
self.context_mut().clear_screen();
|
||||
// Put raw mode on enabled
|
||||
let _ = enable_raw_mode();
|
||||
// Set working directory
|
||||
let pwd: PathBuf = self.context.as_ref().unwrap().local.pwd();
|
||||
// Get files at current wd
|
||||
self.local_scan(pwd.as_path());
|
||||
self.local.wrkdir = pwd;
|
||||
if let Err(err) = enable_raw_mode() {
|
||||
error!("Failed to enter raw mode: {}", err);
|
||||
}
|
||||
// Get files at current pwd
|
||||
self.reload_local_dir();
|
||||
debug!("Read working directory");
|
||||
// Configure text editor
|
||||
self.setup_text_editor();
|
||||
debug!("Setup text editor");
|
||||
// init view
|
||||
self.init();
|
||||
debug!("Initialized view");
|
||||
// Verify error state from context
|
||||
if let Some(err) = self.context.as_mut().unwrap().get_error() {
|
||||
if let Some(err) = self.context.as_mut().unwrap().error() {
|
||||
error!("Fatal error on create: {}", err);
|
||||
self.mount_fatal(&err);
|
||||
}
|
||||
info!("Created FileTransferActivity");
|
||||
}
|
||||
|
||||
/// ### on_draw
|
||||
@@ -296,8 +290,12 @@ impl Activity for FileTransferActivity {
|
||||
}
|
||||
// Check if connected (popup must be None, otherwise would try reconnecting in loop in case of error)
|
||||
if !self.client.is_connected() && self.view.get_props(COMPONENT_TEXT_FATAL).is_none() {
|
||||
let params = self.context.as_ref().unwrap().ft_params.as_ref().unwrap();
|
||||
let msg: String = format!("Connecting to {}:{}...", params.address, params.port);
|
||||
let params = self.context().ft_params().unwrap();
|
||||
info!(
|
||||
"Client is not connected to remote; connecting to {}:{}",
|
||||
params.address, params.port
|
||||
);
|
||||
let msg: String = format!("Connecting to {}:{}…", params.address, params.port);
|
||||
// Set init state to connecting popup
|
||||
self.mount_wait(msg.as_str());
|
||||
// Force ui draw
|
||||
@@ -329,8 +327,16 @@ impl Activity for FileTransferActivity {
|
||||
/// `on_destroy` is the function which cleans up runtime variables and data before terminating the activity.
|
||||
/// This function must be called once before terminating the activity.
|
||||
fn on_destroy(&mut self) -> Option<Context> {
|
||||
// Destroy cache
|
||||
if let Some(cache) = self.cache.take() {
|
||||
if let Err(err) = cache.close() {
|
||||
error!("Failed to delete cache: {}", err);
|
||||
}
|
||||
}
|
||||
// Disable raw mode
|
||||
let _ = disable_raw_mode();
|
||||
if let Err(err) = disable_raw_mode() {
|
||||
error!("Failed to disable raw mode: {}", err);
|
||||
}
|
||||
// Disconnect client
|
||||
if self.client.is_connected() {
|
||||
let _ = self.client.disconnect();
|
||||
1063
src/ui/activities/filetransfer/session.rs
Normal file
939
src/ui/activities/filetransfer/update.rs
Normal file
@@ -0,0 +1,939 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use super::{
|
||||
actions::SelectedEntry, browser::FileExplorerTab, FileTransferActivity, LogLevel,
|
||||
COMPONENT_EXPLORER_FIND, COMPONENT_EXPLORER_LOCAL, COMPONENT_EXPLORER_REMOTE,
|
||||
COMPONENT_INPUT_COPY, COMPONENT_INPUT_EXEC, COMPONENT_INPUT_FIND, COMPONENT_INPUT_GOTO,
|
||||
COMPONENT_INPUT_MKDIR, COMPONENT_INPUT_NEWFILE, COMPONENT_INPUT_OPEN_WITH,
|
||||
COMPONENT_INPUT_RENAME, COMPONENT_INPUT_SAVEAS, COMPONENT_LIST_FILEINFO, COMPONENT_LOG_BOX,
|
||||
COMPONENT_PROGRESS_BAR_FULL, COMPONENT_PROGRESS_BAR_PARTIAL, COMPONENT_RADIO_DELETE,
|
||||
COMPONENT_RADIO_DISCONNECT, COMPONENT_RADIO_QUIT, COMPONENT_RADIO_SORTING,
|
||||
COMPONENT_TEXT_ERROR, COMPONENT_TEXT_FATAL, COMPONENT_TEXT_HELP,
|
||||
};
|
||||
use crate::fs::explorer::FileSorting;
|
||||
use crate::fs::FsEntry;
|
||||
use crate::ui::components::{file_list::FileListPropsBuilder, logbox::LogboxPropsBuilder};
|
||||
use crate::ui::keymap::*;
|
||||
use crate::utils::fmt::fmt_path_elide_ex;
|
||||
// externals
|
||||
use tui_realm_stdlib::progress_bar::ProgressBarPropsBuilder;
|
||||
use tuirealm::{
|
||||
props::{Alignment, PropsBuilder, TableBuilder, TextSpan},
|
||||
tui::style::Color,
|
||||
Msg, Payload, Update, Value,
|
||||
};
|
||||
|
||||
impl Update for FileTransferActivity {
|
||||
// -- update
|
||||
|
||||
/// ### update
|
||||
///
|
||||
/// Update auth activity model based on msg
|
||||
/// The function exits when returns None
|
||||
fn update(&mut self, msg: Option<(String, Msg)>) -> Option<(String, Msg)> {
|
||||
let ref_msg: Option<(&str, &Msg)> = msg.as_ref().map(|(s, msg)| (s.as_str(), msg));
|
||||
// Match msg
|
||||
match ref_msg {
|
||||
None => None, // Exit after None
|
||||
Some(msg) => match msg {
|
||||
// -- local tab
|
||||
(COMPONENT_EXPLORER_LOCAL, key) if key == &MSG_KEY_RIGHT => {
|
||||
// Change tab
|
||||
self.view.active(COMPONENT_EXPLORER_REMOTE);
|
||||
self.browser.change_tab(FileExplorerTab::Remote);
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) if key == &MSG_KEY_BACKSPACE => {
|
||||
// Go to previous directory
|
||||
self.action_go_to_previous_local_dir(false);
|
||||
if self.browser.sync_browsing {
|
||||
let _ = self.update_remote_filelist();
|
||||
}
|
||||
// Reload file list component
|
||||
self.update_local_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, Msg::OnSubmit(Payload::One(Value::Usize(idx)))) => {
|
||||
// Match selected file
|
||||
let mut entry: Option<FsEntry> = None;
|
||||
if let Some(e) = self.local().get(*idx) {
|
||||
entry = Some(e.clone());
|
||||
}
|
||||
if let Some(entry) = entry {
|
||||
if self.action_submit_local(entry) {
|
||||
// Update file list if sync
|
||||
if self.browser.sync_browsing {
|
||||
let _ = self.update_remote_filelist();
|
||||
}
|
||||
self.update_local_filelist()
|
||||
} else {
|
||||
None
|
||||
}
|
||||
} else {
|
||||
None
|
||||
}
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) if key == &MSG_KEY_SPACE => {
|
||||
self.action_local_send();
|
||||
self.update_remote_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) if key == &MSG_KEY_CHAR_A => {
|
||||
// Toggle hidden files
|
||||
self.local_mut().toggle_hidden_files();
|
||||
// Update status bar
|
||||
self.refresh_local_status_bar();
|
||||
// Reload file list component
|
||||
self.update_local_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) if key == &MSG_KEY_CHAR_I => {
|
||||
if let SelectedEntry::One(file) = self.get_local_selected_entries() {
|
||||
self.mount_file_info(&file);
|
||||
}
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) if key == &MSG_KEY_CHAR_L => {
|
||||
// Reload directory
|
||||
self.reload_local_dir();
|
||||
// Reload file list component
|
||||
self.update_local_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) if key == &MSG_KEY_CHAR_O => {
|
||||
self.action_edit_local_file();
|
||||
// Reload file list component
|
||||
self.update_local_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) if key == &MSG_KEY_CHAR_U => {
|
||||
self.action_go_to_local_upper_dir(false);
|
||||
if self.browser.sync_browsing {
|
||||
let _ = self.update_remote_filelist();
|
||||
}
|
||||
// Reload file list component
|
||||
self.update_local_filelist()
|
||||
}
|
||||
// -- remote tab
|
||||
(COMPONENT_EXPLORER_REMOTE, key) if key == &MSG_KEY_LEFT => {
|
||||
// Change tab
|
||||
self.view.active(COMPONENT_EXPLORER_LOCAL);
|
||||
self.browser.change_tab(FileExplorerTab::Local);
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, Msg::OnSubmit(Payload::One(Value::Usize(idx)))) => {
|
||||
// Match selected file
|
||||
let mut entry: Option<FsEntry> = None;
|
||||
if let Some(e) = self.remote().get(*idx) {
|
||||
entry = Some(e.clone());
|
||||
}
|
||||
if let Some(entry) = entry {
|
||||
if self.action_submit_remote(entry) {
|
||||
// Update file list if sync
|
||||
if self.browser.sync_browsing {
|
||||
let _ = self.update_local_filelist();
|
||||
}
|
||||
self.update_remote_filelist()
|
||||
} else {
|
||||
None
|
||||
}
|
||||
} else {
|
||||
None
|
||||
}
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, key) if key == &MSG_KEY_SPACE => {
|
||||
self.action_remote_recv();
|
||||
self.update_local_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, key) if key == &MSG_KEY_BACKSPACE => {
|
||||
// Go to previous directory
|
||||
self.action_go_to_previous_remote_dir(false);
|
||||
// If sync is enabled update local too
|
||||
if self.browser.sync_browsing {
|
||||
let _ = self.update_local_filelist();
|
||||
}
|
||||
// Reload file list component
|
||||
self.update_remote_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, key) if key == &MSG_KEY_CHAR_A => {
|
||||
// Toggle hidden files
|
||||
self.remote_mut().toggle_hidden_files();
|
||||
// Update status bar
|
||||
self.refresh_remote_status_bar();
|
||||
// Reload file list component
|
||||
self.update_remote_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, key) if key == &MSG_KEY_CHAR_I => {
|
||||
if let SelectedEntry::One(file) = self.get_remote_selected_entries() {
|
||||
self.mount_file_info(&file);
|
||||
}
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, key) if key == &MSG_KEY_CHAR_L => {
|
||||
// Reload directory
|
||||
self.reload_remote_dir();
|
||||
// Reload file list component
|
||||
self.update_remote_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, key) if key == &MSG_KEY_CHAR_O => {
|
||||
// Edit file
|
||||
self.action_edit_remote_file();
|
||||
// Reload file list component
|
||||
self.update_remote_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, key) if key == &MSG_KEY_CHAR_U => {
|
||||
self.action_go_to_remote_upper_dir(false);
|
||||
if self.browser.sync_browsing {
|
||||
let _ = self.update_local_filelist();
|
||||
}
|
||||
// Reload file list component
|
||||
self.update_remote_filelist()
|
||||
}
|
||||
// -- common explorer keys
|
||||
(COMPONENT_EXPLORER_LOCAL, key) | (COMPONENT_EXPLORER_REMOTE, key)
|
||||
if key == &MSG_KEY_CHAR_B =>
|
||||
{
|
||||
// Show sorting file
|
||||
self.mount_file_sorting();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) | (COMPONENT_EXPLORER_REMOTE, key)
|
||||
if key == &MSG_KEY_CHAR_C =>
|
||||
{
|
||||
self.mount_copy();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) | (COMPONENT_EXPLORER_REMOTE, key)
|
||||
if key == &MSG_KEY_CHAR_D =>
|
||||
{
|
||||
self.mount_mkdir();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) | (COMPONENT_EXPLORER_REMOTE, key)
|
||||
if key == &MSG_KEY_CHAR_F =>
|
||||
{
|
||||
self.mount_find_input();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) | (COMPONENT_EXPLORER_REMOTE, key)
|
||||
if key == &MSG_KEY_CHAR_G =>
|
||||
{
|
||||
self.mount_goto();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) | (COMPONENT_EXPLORER_REMOTE, key)
|
||||
if key == &MSG_KEY_CHAR_H =>
|
||||
{
|
||||
self.mount_help();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) | (COMPONENT_EXPLORER_REMOTE, key)
|
||||
if key == &MSG_KEY_CHAR_N =>
|
||||
{
|
||||
self.mount_newfile();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key)
|
||||
| (COMPONENT_EXPLORER_REMOTE, key)
|
||||
| (COMPONENT_LOG_BOX, key)
|
||||
if key == &MSG_KEY_CHAR_Q =>
|
||||
{
|
||||
self.mount_quit();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) | (COMPONENT_EXPLORER_REMOTE, key)
|
||||
if key == &MSG_KEY_CHAR_R =>
|
||||
{
|
||||
// Mount rename
|
||||
self.mount_rename();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key)
|
||||
| (COMPONENT_EXPLORER_REMOTE, key)
|
||||
| (COMPONENT_EXPLORER_FIND, key)
|
||||
if key == &MSG_KEY_CHAR_S =>
|
||||
{
|
||||
// Mount save as
|
||||
self.mount_saveas();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key)
|
||||
| (COMPONENT_EXPLORER_REMOTE, key)
|
||||
| (COMPONENT_EXPLORER_FIND, key)
|
||||
if key == &MSG_KEY_CHAR_V =>
|
||||
{
|
||||
// View
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.action_open_local(),
|
||||
FileExplorerTab::Remote => self.action_open_remote(),
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::FindRemote => {
|
||||
self.action_find_open()
|
||||
}
|
||||
}
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key)
|
||||
| (COMPONENT_EXPLORER_REMOTE, key)
|
||||
| (COMPONENT_EXPLORER_FIND, key)
|
||||
if key == &MSG_KEY_CHAR_W =>
|
||||
{
|
||||
// Open with
|
||||
self.mount_openwith();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) | (COMPONENT_EXPLORER_REMOTE, key)
|
||||
if key == &MSG_KEY_CHAR_X =>
|
||||
{
|
||||
// Mount exec
|
||||
self.mount_exec();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key) | (COMPONENT_EXPLORER_REMOTE, key)
|
||||
if key == &MSG_KEY_CHAR_Y =>
|
||||
{
|
||||
// Toggle browser sync
|
||||
self.browser.toggle_sync_browsing();
|
||||
// Update status bar
|
||||
self.refresh_remote_status_bar();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key)
|
||||
| (COMPONENT_EXPLORER_REMOTE, key)
|
||||
| (COMPONENT_LOG_BOX, key)
|
||||
if key == &MSG_KEY_ESC =>
|
||||
{
|
||||
self.mount_disconnect();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, key)
|
||||
| (COMPONENT_EXPLORER_REMOTE, key)
|
||||
| (COMPONENT_EXPLORER_FIND, key)
|
||||
if key == &MSG_KEY_CHAR_E || key == &MSG_KEY_DEL =>
|
||||
{
|
||||
self.mount_radio_delete();
|
||||
None
|
||||
}
|
||||
// -- find result explorer
|
||||
(COMPONENT_EXPLORER_FIND, key) if key == &MSG_KEY_ESC => {
|
||||
// Umount find
|
||||
self.umount_find();
|
||||
// Finalize find
|
||||
self.finalize_find();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_FIND, Msg::OnSubmit(_)) => {
|
||||
// Find changedir
|
||||
self.action_find_changedir();
|
||||
// Umount find
|
||||
self.umount_find();
|
||||
// Finalize find
|
||||
self.finalize_find();
|
||||
// Reload files
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
(COMPONENT_EXPLORER_FIND, key) if key == &MSG_KEY_SPACE => {
|
||||
// Get entry
|
||||
self.action_find_transfer(None);
|
||||
// Reload files
|
||||
match self.browser.tab() {
|
||||
// NOTE: swapped by purpose
|
||||
FileExplorerTab::FindLocal => self.update_remote_filelist(),
|
||||
FileExplorerTab::FindRemote => self.update_local_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
// -- switch to log
|
||||
(COMPONENT_EXPLORER_LOCAL, key) | (COMPONENT_EXPLORER_REMOTE, key)
|
||||
if key == &MSG_KEY_TAB =>
|
||||
{
|
||||
self.view.active(COMPONENT_LOG_BOX); // Active log box
|
||||
None
|
||||
}
|
||||
// -- Log box
|
||||
(COMPONENT_LOG_BOX, key) if key == &MSG_KEY_TAB => {
|
||||
self.view.blur(); // Blur log box
|
||||
None
|
||||
}
|
||||
// -- copy popup
|
||||
(COMPONENT_INPUT_COPY, key) if key == &MSG_KEY_ESC => {
|
||||
self.umount_copy();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_COPY, Msg::OnSubmit(Payload::One(Value::Str(input)))) => {
|
||||
// Copy file
|
||||
self.umount_copy();
|
||||
self.mount_blocking_wait("Copying file(s)…");
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.action_local_copy(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_remote_copy(input.to_string()),
|
||||
_ => panic!("Found tab doesn't support COPY"),
|
||||
}
|
||||
self.umount_wait();
|
||||
// Reload files
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
(COMPONENT_INPUT_COPY, _) => None,
|
||||
// -- exec popup
|
||||
(COMPONENT_INPUT_EXEC, key) if key == &MSG_KEY_ESC => {
|
||||
self.umount_exec();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_EXEC, Msg::OnSubmit(Payload::One(Value::Str(input)))) => {
|
||||
// Exex command
|
||||
self.umount_exec();
|
||||
self.mount_blocking_wait(format!("Executing '{}'…", input).as_str());
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.action_local_exec(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_remote_exec(input.to_string()),
|
||||
_ => panic!("Found tab doesn't support EXEC"),
|
||||
}
|
||||
self.umount_wait();
|
||||
// Reload files
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
(COMPONENT_INPUT_EXEC, _) => None,
|
||||
// -- find popup
|
||||
(COMPONENT_INPUT_FIND, key) if key == &MSG_KEY_ESC => {
|
||||
self.umount_find_input();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_FIND, Msg::OnSubmit(Payload::One(Value::Str(input)))) => {
|
||||
self.umount_find_input();
|
||||
// Find
|
||||
let res: Result<Vec<FsEntry>, String> = match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.action_local_find(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_remote_find(input.to_string()),
|
||||
_ => panic!("Trying to search for files, while already in a find result"),
|
||||
};
|
||||
// Match result
|
||||
match res {
|
||||
Err(err) => {
|
||||
// Mount error
|
||||
self.mount_error(err.as_str());
|
||||
}
|
||||
Ok(files) => {
|
||||
// Create explorer and load files
|
||||
self.browser.set_found(files);
|
||||
// Mount result widget
|
||||
self.mount_find(input);
|
||||
self.update_find_list();
|
||||
// Initialize tab
|
||||
self.browser.change_tab(match self.browser.tab() {
|
||||
FileExplorerTab::Local => FileExplorerTab::FindLocal,
|
||||
FileExplorerTab::Remote => FileExplorerTab::FindRemote,
|
||||
_ => FileExplorerTab::FindLocal,
|
||||
});
|
||||
}
|
||||
}
|
||||
None
|
||||
}
|
||||
// -- goto popup
|
||||
(COMPONENT_INPUT_GOTO, key) if key == &MSG_KEY_ESC => {
|
||||
self.umount_goto();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_GOTO, Msg::OnSubmit(Payload::One(Value::Str(input)))) => {
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => {
|
||||
self.action_change_local_dir(input.to_string(), false)
|
||||
}
|
||||
FileExplorerTab::Remote => {
|
||||
self.action_change_remote_dir(input.to_string(), false)
|
||||
}
|
||||
_ => panic!("Found tab doesn't support GOTO"),
|
||||
}
|
||||
// Umount
|
||||
self.umount_goto();
|
||||
// Reload files if sync
|
||||
if self.browser.sync_browsing {
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Remote => self.update_local_filelist(),
|
||||
FileExplorerTab::Local => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
};
|
||||
}
|
||||
// Reload files
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
(COMPONENT_INPUT_GOTO, _) => None,
|
||||
// -- make directory
|
||||
(COMPONENT_INPUT_MKDIR, key) if key == &MSG_KEY_ESC => {
|
||||
self.umount_mkdir();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_MKDIR, Msg::OnSubmit(Payload::One(Value::Str(input)))) => {
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.action_local_mkdir(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_remote_mkdir(input.to_string()),
|
||||
_ => panic!("Found tab doesn't support MKDIR"),
|
||||
}
|
||||
self.umount_mkdir();
|
||||
// Reload files
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
(COMPONENT_INPUT_MKDIR, _) => None,
|
||||
// -- new file
|
||||
(COMPONENT_INPUT_NEWFILE, key) if key == &MSG_KEY_ESC => {
|
||||
self.umount_newfile();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_NEWFILE, Msg::OnSubmit(Payload::One(Value::Str(input)))) => {
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.action_local_newfile(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_remote_newfile(input.to_string()),
|
||||
_ => panic!("Found tab doesn't support NEWFILE"),
|
||||
}
|
||||
self.umount_newfile();
|
||||
// Reload files
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
(COMPONENT_INPUT_NEWFILE, _) => None,
|
||||
// -- open with
|
||||
(COMPONENT_INPUT_OPEN_WITH, key) if key == &MSG_KEY_ESC => {
|
||||
self.umount_openwith();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_OPEN_WITH, Msg::OnSubmit(Payload::One(Value::Str(input)))) => {
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.action_local_open_with(input),
|
||||
FileExplorerTab::Remote => self.action_remote_open_with(input),
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::FindRemote => {
|
||||
self.action_find_open_with(input)
|
||||
}
|
||||
}
|
||||
self.umount_openwith();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_OPEN_WITH, _) => None,
|
||||
// -- rename
|
||||
(COMPONENT_INPUT_RENAME, key) if key == &MSG_KEY_ESC => {
|
||||
self.umount_rename();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_RENAME, Msg::OnSubmit(Payload::One(Value::Str(input)))) => {
|
||||
self.umount_rename();
|
||||
self.mount_blocking_wait("Moving file(s)…");
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.action_local_rename(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_remote_rename(input.to_string()),
|
||||
_ => panic!("Found tab doesn't support RENAME"),
|
||||
}
|
||||
self.umount_wait();
|
||||
// Reload files
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
(COMPONENT_INPUT_RENAME, _) => None,
|
||||
// -- save as
|
||||
(COMPONENT_INPUT_SAVEAS, key) if key == &MSG_KEY_ESC => {
|
||||
self.umount_saveas();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_SAVEAS, Msg::OnSubmit(Payload::One(Value::Str(input)))) => {
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.action_local_saveas(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_remote_saveas(input.to_string()),
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::FindRemote => {
|
||||
// Get entry
|
||||
self.action_find_transfer(Some(input.to_string()));
|
||||
}
|
||||
}
|
||||
self.umount_saveas();
|
||||
// Reload files
|
||||
match self.browser.tab() {
|
||||
// NOTE: Swapped is intentional
|
||||
FileExplorerTab::Local => self.update_remote_filelist(),
|
||||
FileExplorerTab::Remote => self.update_local_filelist(),
|
||||
FileExplorerTab::FindLocal => self.update_remote_filelist(),
|
||||
FileExplorerTab::FindRemote => self.update_local_filelist(),
|
||||
}
|
||||
}
|
||||
(COMPONENT_INPUT_SAVEAS, _) => None,
|
||||
// -- fileinfo
|
||||
(COMPONENT_LIST_FILEINFO, key) | (COMPONENT_LIST_FILEINFO, key)
|
||||
if key == &MSG_KEY_ENTER || key == &MSG_KEY_ESC =>
|
||||
{
|
||||
self.umount_file_info();
|
||||
None
|
||||
}
|
||||
(COMPONENT_LIST_FILEINFO, _) => None,
|
||||
// -- delete
|
||||
(COMPONENT_RADIO_DELETE, key)
|
||||
if key == &MSG_KEY_ESC
|
||||
|| key == &Msg::OnSubmit(Payload::One(Value::Usize(1))) =>
|
||||
{
|
||||
self.umount_radio_delete();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_DELETE, Msg::OnSubmit(Payload::One(Value::Usize(0)))) => {
|
||||
// Choice is 'YES'
|
||||
self.umount_radio_delete();
|
||||
self.mount_blocking_wait("Removing file(s)…");
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.action_local_delete(),
|
||||
FileExplorerTab::Remote => self.action_remote_delete(),
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::FindRemote => {
|
||||
// Get entry
|
||||
self.action_find_delete();
|
||||
// Delete entries
|
||||
match self.view.get_state(COMPONENT_EXPLORER_FIND) {
|
||||
Some(Payload::One(Value::Usize(idx))) => {
|
||||
// Reload entries
|
||||
self.found_mut().unwrap().del_entry(idx);
|
||||
}
|
||||
Some(Payload::Vec(values)) => {
|
||||
values
|
||||
.iter()
|
||||
.map(|x| match x {
|
||||
Value::Usize(v) => *v,
|
||||
_ => 0,
|
||||
})
|
||||
.for_each(|x| self.found_mut().unwrap().del_entry(x));
|
||||
}
|
||||
_ => {}
|
||||
}
|
||||
self.update_find_list();
|
||||
}
|
||||
}
|
||||
self.umount_wait();
|
||||
// Reload files
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
FileExplorerTab::FindLocal => self.update_local_filelist(),
|
||||
FileExplorerTab::FindRemote => self.update_remote_filelist(),
|
||||
}
|
||||
}
|
||||
(COMPONENT_RADIO_DELETE, _) => None,
|
||||
// -- disconnect
|
||||
(COMPONENT_RADIO_DISCONNECT, key)
|
||||
if key == &MSG_KEY_ESC
|
||||
|| key == &Msg::OnSubmit(Payload::One(Value::Usize(1))) =>
|
||||
{
|
||||
self.umount_disconnect();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_DISCONNECT, Msg::OnSubmit(Payload::One(Value::Usize(0)))) => {
|
||||
self.disconnect();
|
||||
self.umount_disconnect();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_DISCONNECT, _) => None,
|
||||
// -- quit
|
||||
(COMPONENT_RADIO_QUIT, key)
|
||||
if key == &MSG_KEY_ESC
|
||||
|| key == &Msg::OnSubmit(Payload::One(Value::Usize(1))) =>
|
||||
{
|
||||
self.umount_quit();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_QUIT, Msg::OnSubmit(Payload::One(Value::Usize(0)))) => {
|
||||
self.disconnect_and_quit();
|
||||
self.umount_quit();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_QUIT, _) => None,
|
||||
// -- sorting
|
||||
(COMPONENT_RADIO_SORTING, key) if key == &MSG_KEY_ESC => {
|
||||
self.umount_file_sorting();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_SORTING, Msg::OnSubmit(_)) => {
|
||||
self.umount_file_sorting();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_SORTING, Msg::OnChange(Payload::One(Value::Usize(mode)))) => {
|
||||
// Get sorting mode
|
||||
let sorting: FileSorting = match mode {
|
||||
1 => FileSorting::ModifyTime,
|
||||
2 => FileSorting::CreationTime,
|
||||
3 => FileSorting::Size,
|
||||
_ => FileSorting::Name,
|
||||
};
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.local_mut().sort_by(sorting),
|
||||
FileExplorerTab::Remote => self.remote_mut().sort_by(sorting),
|
||||
_ => panic!("Found result doesn't support SORTING"),
|
||||
}
|
||||
// Update status bar
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.refresh_local_status_bar(),
|
||||
FileExplorerTab::Remote => self.refresh_remote_status_bar(),
|
||||
_ => panic!("Found result doesn't support SORTING"),
|
||||
};
|
||||
// Reload files
|
||||
match self.browser.tab() {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
(COMPONENT_RADIO_SORTING, _) => None,
|
||||
// -- error
|
||||
(COMPONENT_TEXT_ERROR, key) | (COMPONENT_TEXT_ERROR, key)
|
||||
if key == &MSG_KEY_ESC || key == &MSG_KEY_ENTER =>
|
||||
{
|
||||
self.umount_error();
|
||||
None
|
||||
}
|
||||
(COMPONENT_TEXT_ERROR, _) => None,
|
||||
// -- fatal
|
||||
(COMPONENT_TEXT_FATAL, key) | (COMPONENT_TEXT_FATAL, key)
|
||||
if key == &MSG_KEY_ESC || key == &MSG_KEY_ENTER =>
|
||||
{
|
||||
self.exit_reason = Some(super::ExitReason::Disconnect);
|
||||
None
|
||||
}
|
||||
(COMPONENT_TEXT_FATAL, _) => None,
|
||||
// -- help
|
||||
(COMPONENT_TEXT_HELP, key) | (COMPONENT_TEXT_HELP, key)
|
||||
if key == &MSG_KEY_ESC || key == &MSG_KEY_ENTER =>
|
||||
{
|
||||
self.umount_help();
|
||||
None
|
||||
}
|
||||
(COMPONENT_TEXT_HELP, _) => None,
|
||||
// -- progress bar
|
||||
(COMPONENT_PROGRESS_BAR_PARTIAL, key) if key == &MSG_KEY_CTRL_C => {
|
||||
// Set transfer aborted to True
|
||||
self.transfer.abort();
|
||||
None
|
||||
}
|
||||
(COMPONENT_PROGRESS_BAR_PARTIAL, _) => None,
|
||||
// -- fallback
|
||||
(_, _) => None, // Nothing to do
|
||||
},
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
impl FileTransferActivity {
|
||||
/// ### update_local_filelist
|
||||
///
|
||||
/// Update local file list
|
||||
pub(super) fn update_local_filelist(&mut self) -> Option<(String, Msg)> {
|
||||
match self.view.get_props(super::COMPONENT_EXPLORER_LOCAL) {
|
||||
Some(props) => {
|
||||
// Get width
|
||||
let width: usize = self
|
||||
.context()
|
||||
.store()
|
||||
.get_unsigned(super::STORAGE_EXPLORER_WIDTH)
|
||||
.unwrap_or(256);
|
||||
let hostname: String = match hostname::get() {
|
||||
Ok(h) => {
|
||||
let hostname: String = h.as_os_str().to_string_lossy().to_string();
|
||||
let tokens: Vec<&str> = hostname.split('.').collect();
|
||||
String::from(*tokens.get(0).unwrap_or(&"localhost"))
|
||||
}
|
||||
Err(_) => String::from("localhost"),
|
||||
};
|
||||
let hostname: String = format!(
|
||||
"{}:{} ",
|
||||
hostname,
|
||||
fmt_path_elide_ex(self.local().wrkdir.as_path(), width, hostname.len() + 3) // 3 because of '/…/'
|
||||
);
|
||||
let files: Vec<String> = self
|
||||
.local()
|
||||
.iter_files()
|
||||
.map(|x: &FsEntry| self.local().fmt_file(x))
|
||||
.collect();
|
||||
// Update
|
||||
let props = FileListPropsBuilder::from(props)
|
||||
.with_files(files)
|
||||
.with_title(hostname, Alignment::Left)
|
||||
.build();
|
||||
// Update
|
||||
self.view.update(super::COMPONENT_EXPLORER_LOCAL, props)
|
||||
}
|
||||
None => None,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### update_remote_filelist
|
||||
///
|
||||
/// Update remote file list
|
||||
pub(super) fn update_remote_filelist(&mut self) -> Option<(String, Msg)> {
|
||||
match self.view.get_props(super::COMPONENT_EXPLORER_REMOTE) {
|
||||
Some(props) => {
|
||||
// Get width
|
||||
let width: usize = self
|
||||
.context()
|
||||
.store()
|
||||
.get_unsigned(super::STORAGE_EXPLORER_WIDTH)
|
||||
.unwrap_or(256);
|
||||
let params = self.context().ft_params().unwrap();
|
||||
let hostname: String = format!(
|
||||
"{}:{} ",
|
||||
params.address,
|
||||
fmt_path_elide_ex(
|
||||
self.remote().wrkdir.as_path(),
|
||||
width,
|
||||
params.address.len() + 3 // 3 because of '/…/'
|
||||
)
|
||||
);
|
||||
let files: Vec<String> = self
|
||||
.remote()
|
||||
.iter_files()
|
||||
.map(|x: &FsEntry| self.remote().fmt_file(x))
|
||||
.collect();
|
||||
// Update
|
||||
let props = FileListPropsBuilder::from(props)
|
||||
.with_files(files)
|
||||
.with_title(hostname, Alignment::Left)
|
||||
.build();
|
||||
self.view.update(super::COMPONENT_EXPLORER_REMOTE, props)
|
||||
}
|
||||
None => None,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### update_logbox
|
||||
///
|
||||
/// Update log box
|
||||
pub(super) fn update_logbox(&mut self) -> Option<(String, Msg)> {
|
||||
match self.view.get_props(super::COMPONENT_LOG_BOX) {
|
||||
Some(props) => {
|
||||
// Make log entries
|
||||
let mut table: TableBuilder = TableBuilder::default();
|
||||
for (idx, record) in self.log_records.iter().enumerate() {
|
||||
// Add row if not first row
|
||||
if idx > 0 {
|
||||
table.add_row();
|
||||
}
|
||||
let fg = match record.level {
|
||||
LogLevel::Error => Color::Red,
|
||||
LogLevel::Warn => Color::Yellow,
|
||||
LogLevel::Info => Color::Green,
|
||||
};
|
||||
table
|
||||
.add_col(TextSpan::from(format!(
|
||||
"{}",
|
||||
record.time.format("%Y-%m-%dT%H:%M:%S%Z")
|
||||
)))
|
||||
.add_col(TextSpan::from(" ["))
|
||||
.add_col(
|
||||
TextSpan::new(
|
||||
format!(
|
||||
"{:5}",
|
||||
match record.level {
|
||||
LogLevel::Error => "ERROR",
|
||||
LogLevel::Warn => "WARN",
|
||||
LogLevel::Info => "INFO",
|
||||
}
|
||||
)
|
||||
.as_str(),
|
||||
)
|
||||
.fg(fg),
|
||||
)
|
||||
.add_col(TextSpan::from("]: "))
|
||||
.add_col(TextSpan::from(record.msg.as_ref()));
|
||||
}
|
||||
let table = table.build();
|
||||
let props = LogboxPropsBuilder::from(props).with_log(table).build();
|
||||
self.view.update(super::COMPONENT_LOG_BOX, props)
|
||||
}
|
||||
None => None,
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn update_progress_bar(&mut self, filename: String) -> Option<(String, Msg)> {
|
||||
if let Some(props) = self.view.get_props(COMPONENT_PROGRESS_BAR_FULL) {
|
||||
let props = ProgressBarPropsBuilder::from(props)
|
||||
.with_label(self.transfer.full.to_string())
|
||||
.with_progress(self.transfer.full.calc_progress())
|
||||
.build();
|
||||
let _ = self.view.update(COMPONENT_PROGRESS_BAR_FULL, props);
|
||||
}
|
||||
match self.view.get_props(COMPONENT_PROGRESS_BAR_PARTIAL) {
|
||||
Some(props) => {
|
||||
let props = ProgressBarPropsBuilder::from(props)
|
||||
.with_title(filename, Alignment::Center)
|
||||
.with_label(self.transfer.partial.to_string())
|
||||
.with_progress(self.transfer.partial.calc_progress())
|
||||
.build();
|
||||
self.view.update(COMPONENT_PROGRESS_BAR_PARTIAL, props)
|
||||
}
|
||||
None => None,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### finalize_find
|
||||
///
|
||||
/// Finalize find process
|
||||
fn finalize_find(&mut self) {
|
||||
// Set found to none
|
||||
self.browser.del_found();
|
||||
// Restore tab
|
||||
self.browser.change_tab(match self.browser.tab() {
|
||||
FileExplorerTab::FindLocal => FileExplorerTab::Local,
|
||||
FileExplorerTab::FindRemote => FileExplorerTab::Remote,
|
||||
_ => FileExplorerTab::Local,
|
||||
});
|
||||
}
|
||||
|
||||
fn update_find_list(&mut self) -> Option<(String, Msg)> {
|
||||
match self.view.get_props(COMPONENT_EXPLORER_FIND) {
|
||||
None => None,
|
||||
Some(props) => {
|
||||
// Prepare files
|
||||
let files: Vec<String> = self
|
||||
.found()
|
||||
.unwrap()
|
||||
.iter_files()
|
||||
.map(|x: &FsEntry| self.found().unwrap().fmt_file(x))
|
||||
.collect();
|
||||
let props = FileListPropsBuilder::from(props).with_files(files).build();
|
||||
self.view.update(COMPONENT_EXPLORER_FIND, props)
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
1116
src/ui/activities/filetransfer/view.rs
Normal file
@@ -1,640 +0,0 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// locals
|
||||
use super::{FileExplorerTab, FileTransferActivity, FsEntry, LogLevel};
|
||||
use crate::ui::layout::Payload;
|
||||
// externals
|
||||
use std::path::PathBuf;
|
||||
|
||||
impl FileTransferActivity {
|
||||
/// ### action_change_local_dir
|
||||
///
|
||||
/// Change local directory reading value from input
|
||||
pub(super) fn action_change_local_dir(&mut self, input: String) {
|
||||
let dir_path: PathBuf = PathBuf::from(input.as_str());
|
||||
let abs_dir_path: PathBuf = match dir_path.is_relative() {
|
||||
true => {
|
||||
let mut d: PathBuf = self.local.wrkdir.clone();
|
||||
d.push(dir_path);
|
||||
d
|
||||
}
|
||||
false => dir_path,
|
||||
};
|
||||
self.local_changedir(abs_dir_path.as_path(), true);
|
||||
}
|
||||
|
||||
/// ### action_change_remote_dir
|
||||
///
|
||||
/// Change remote directory reading value from input
|
||||
pub(super) fn action_change_remote_dir(&mut self, input: String) {
|
||||
let dir_path: PathBuf = PathBuf::from(input.as_str());
|
||||
let abs_dir_path: PathBuf = match dir_path.is_relative() {
|
||||
true => {
|
||||
let mut wrkdir: PathBuf = self.remote.wrkdir.clone();
|
||||
wrkdir.push(dir_path);
|
||||
wrkdir
|
||||
}
|
||||
false => dir_path,
|
||||
};
|
||||
self.remote_changedir(abs_dir_path.as_path(), true);
|
||||
}
|
||||
|
||||
/// ### action_local_copy
|
||||
///
|
||||
/// Copy file on local
|
||||
pub(super) fn action_local_copy(&mut self, input: String) {
|
||||
if let Some(idx) = self.get_local_file_idx() {
|
||||
let dest_path: PathBuf = PathBuf::from(input);
|
||||
let entry: FsEntry = self.local.get(idx).unwrap().clone();
|
||||
if let Some(ctx) = self.context.as_mut() {
|
||||
match ctx.local.copy(&entry, dest_path.as_path()) {
|
||||
Ok(_) => {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!(
|
||||
"Copied \"{}\" to \"{}\"",
|
||||
entry.get_abs_path().display(),
|
||||
dest_path.display()
|
||||
)
|
||||
.as_str(),
|
||||
);
|
||||
// Reload entries
|
||||
let wrkdir: PathBuf = self.local.wrkdir.clone();
|
||||
self.local_scan(wrkdir.as_path());
|
||||
}
|
||||
Err(err) => self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not copy \"{}\" to \"{}\": {}",
|
||||
entry.get_abs_path().display(),
|
||||
dest_path.display(),
|
||||
err
|
||||
),
|
||||
),
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### action_remote_copy
|
||||
///
|
||||
/// Copy file on remote
|
||||
pub(super) fn action_remote_copy(&mut self, input: String) {
|
||||
if let Some(idx) = self.get_remote_file_idx() {
|
||||
let dest_path: PathBuf = PathBuf::from(input);
|
||||
let entry: FsEntry = self.remote.get(idx).unwrap().clone();
|
||||
match self.client.as_mut().copy(&entry, dest_path.as_path()) {
|
||||
Ok(_) => {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!(
|
||||
"Copied \"{}\" to \"{}\"",
|
||||
entry.get_abs_path().display(),
|
||||
dest_path.display()
|
||||
)
|
||||
.as_str(),
|
||||
);
|
||||
self.reload_remote_dir();
|
||||
}
|
||||
Err(err) => self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not copy \"{}\" to \"{}\": {}",
|
||||
entry.get_abs_path().display(),
|
||||
dest_path.display(),
|
||||
err
|
||||
),
|
||||
),
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_local_mkdir(&mut self, input: String) {
|
||||
match self
|
||||
.context
|
||||
.as_mut()
|
||||
.unwrap()
|
||||
.local
|
||||
.mkdir(PathBuf::from(input.as_str()).as_path())
|
||||
{
|
||||
Ok(_) => {
|
||||
// Reload files
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Created directory \"{}\"", input).as_ref(),
|
||||
);
|
||||
let wrkdir: PathBuf = self.local.wrkdir.clone();
|
||||
self.local_scan(wrkdir.as_path());
|
||||
}
|
||||
Err(err) => {
|
||||
// Report err
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not create directory \"{}\": {}", input, err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
pub(super) fn action_remote_mkdir(&mut self, input: String) {
|
||||
match self
|
||||
.client
|
||||
.as_mut()
|
||||
.mkdir(PathBuf::from(input.as_str()).as_path())
|
||||
{
|
||||
Ok(_) => {
|
||||
// Reload files
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Created directory \"{}\"", input).as_ref(),
|
||||
);
|
||||
self.reload_remote_dir();
|
||||
}
|
||||
Err(err) => {
|
||||
// Report err
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not create directory \"{}\": {}", input, err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_local_rename(&mut self, input: String) {
|
||||
let entry: Option<FsEntry> = self.get_local_file_entry().cloned();
|
||||
if let Some(entry) = entry {
|
||||
let mut dst_path: PathBuf = PathBuf::from(input);
|
||||
// Check if path is relative
|
||||
if dst_path.as_path().is_relative() {
|
||||
let mut wrkdir: PathBuf = self.local.wrkdir.clone();
|
||||
wrkdir.push(dst_path);
|
||||
dst_path = wrkdir;
|
||||
}
|
||||
let full_path: PathBuf = entry.get_abs_path();
|
||||
// Rename file or directory and report status as popup
|
||||
match self
|
||||
.context
|
||||
.as_mut()
|
||||
.unwrap()
|
||||
.local
|
||||
.rename(&entry, dst_path.as_path())
|
||||
{
|
||||
Ok(_) => {
|
||||
// Reload files
|
||||
let path: PathBuf = self.local.wrkdir.clone();
|
||||
self.local_scan(path.as_path());
|
||||
// Log
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!(
|
||||
"Renamed file \"{}\" to \"{}\"",
|
||||
full_path.display(),
|
||||
dst_path.display()
|
||||
)
|
||||
.as_ref(),
|
||||
);
|
||||
}
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not rename file \"{}\": {}", full_path.display(), err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_remote_rename(&mut self, input: String) {
|
||||
if let Some(idx) = self.get_remote_file_idx() {
|
||||
if let Some(entry) = self.remote.get(idx) {
|
||||
let dst_path: PathBuf = PathBuf::from(input);
|
||||
let full_path: PathBuf = entry.get_abs_path();
|
||||
// Rename file or directory and report status as popup
|
||||
match self.client.as_mut().rename(entry, dst_path.as_path()) {
|
||||
Ok(_) => {
|
||||
// Reload files
|
||||
let path: PathBuf = self.remote.wrkdir.clone();
|
||||
self.remote_scan(path.as_path());
|
||||
// Log
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!(
|
||||
"Renamed file \"{}\" to \"{}\"",
|
||||
full_path.display(),
|
||||
dst_path.display()
|
||||
)
|
||||
.as_ref(),
|
||||
);
|
||||
}
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not rename file \"{}\": {}", full_path.display(), err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_local_delete(&mut self) {
|
||||
let entry: Option<FsEntry> = self.get_local_file_entry().cloned();
|
||||
if let Some(entry) = entry {
|
||||
let full_path: PathBuf = entry.get_abs_path();
|
||||
// Delete file or directory and report status as popup
|
||||
match self.context.as_mut().unwrap().local.remove(&entry) {
|
||||
Ok(_) => {
|
||||
// Reload files
|
||||
let p: PathBuf = self.local.wrkdir.clone();
|
||||
self.local_scan(p.as_path());
|
||||
// Log
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Removed file \"{}\"", full_path.display()).as_ref(),
|
||||
);
|
||||
}
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not delete file \"{}\": {}", full_path.display(), err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_remote_delete(&mut self) {
|
||||
if let Some(idx) = self.get_remote_file_idx() {
|
||||
// Check if file entry exists
|
||||
if let Some(entry) = self.remote.get(idx) {
|
||||
let full_path: PathBuf = entry.get_abs_path();
|
||||
// Delete file
|
||||
match self.client.remove(entry) {
|
||||
Ok(_) => {
|
||||
self.reload_remote_dir();
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Removed file \"{}\"", full_path.display()).as_ref(),
|
||||
);
|
||||
}
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not delete file \"{}\": {}", full_path.display(), err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_local_saveas(&mut self, input: String) {
|
||||
if let Some(idx) = self.get_local_file_idx() {
|
||||
// Get pwd
|
||||
let wrkdir: PathBuf = self.remote.wrkdir.clone();
|
||||
if self.local.get(idx).is_some() {
|
||||
let file: FsEntry = self.local.get(idx).unwrap().clone();
|
||||
// Call upload; pass realfile, keep link name
|
||||
self.filetransfer_send(&file.get_realfile(), wrkdir.as_path(), Some(input));
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_remote_saveas(&mut self, input: String) {
|
||||
if let Some(idx) = self.get_remote_file_idx() {
|
||||
// Get pwd
|
||||
let wrkdir: PathBuf = self.local.wrkdir.clone();
|
||||
if self.remote.get(idx).is_some() {
|
||||
let file: FsEntry = self.remote.get(idx).unwrap().clone();
|
||||
// Call upload; pass realfile, keep link name
|
||||
self.filetransfer_recv(&file.get_realfile(), wrkdir.as_path(), Some(input));
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_local_newfile(&mut self, input: String) {
|
||||
// Check if file exists
|
||||
let mut file_exists: bool = false;
|
||||
for file in self.local.iter_files_all() {
|
||||
if input == file.get_name() {
|
||||
file_exists = true;
|
||||
}
|
||||
}
|
||||
if file_exists {
|
||||
self.log_and_alert(
|
||||
LogLevel::Warn,
|
||||
format!("File \"{}\" already exists", input,),
|
||||
);
|
||||
return;
|
||||
}
|
||||
// Create file
|
||||
let file_path: PathBuf = PathBuf::from(input.as_str());
|
||||
if let Some(ctx) = self.context.as_mut() {
|
||||
if let Err(err) = ctx.local.open_file_write(file_path.as_path()) {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not create file \"{}\": {}", file_path.display(), err),
|
||||
);
|
||||
} else {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Created file \"{}\"", file_path.display()).as_str(),
|
||||
);
|
||||
}
|
||||
// Reload files
|
||||
let path: PathBuf = self.local.wrkdir.clone();
|
||||
self.local_scan(path.as_path());
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_remote_newfile(&mut self, input: String) {
|
||||
// Check if file exists
|
||||
let mut file_exists: bool = false;
|
||||
for file in self.remote.iter_files_all() {
|
||||
if input == file.get_name() {
|
||||
file_exists = true;
|
||||
}
|
||||
}
|
||||
if file_exists {
|
||||
self.log_and_alert(
|
||||
LogLevel::Warn,
|
||||
format!("File \"{}\" already exists", input,),
|
||||
);
|
||||
return;
|
||||
}
|
||||
// Get path on remote
|
||||
let file_path: PathBuf = PathBuf::from(input.as_str());
|
||||
// Create file (on local)
|
||||
match tempfile::NamedTempFile::new() {
|
||||
Err(err) => self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not create tempfile: {}", err),
|
||||
),
|
||||
Ok(tfile) => {
|
||||
// Stat tempfile
|
||||
if let Some(ctx) = self.context.as_mut() {
|
||||
let local_file: FsEntry = match ctx.local.stat(tfile.path()) {
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not stat tempfile: {}", err),
|
||||
);
|
||||
return;
|
||||
}
|
||||
Ok(f) => f,
|
||||
};
|
||||
if let FsEntry::File(local_file) = local_file {
|
||||
// Create file
|
||||
match self.client.send_file(&local_file, file_path.as_path()) {
|
||||
Err(err) => self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not create file \"{}\": {}",
|
||||
file_path.display(),
|
||||
err
|
||||
),
|
||||
),
|
||||
Ok(writer) => {
|
||||
// Finalize write
|
||||
if let Err(err) = self.client.on_sent(writer) {
|
||||
self.log_and_alert(
|
||||
LogLevel::Warn,
|
||||
format!("Could not finalize file: {}", err),
|
||||
);
|
||||
} else {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Created file \"{}\"", file_path.display())
|
||||
.as_str(),
|
||||
);
|
||||
}
|
||||
// Reload files
|
||||
let path: PathBuf = self.remote.wrkdir.clone();
|
||||
self.remote_scan(path.as_path());
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_local_exec(&mut self, input: String) {
|
||||
match self.context.as_mut().unwrap().local.exec(input.as_str()) {
|
||||
Ok(output) => {
|
||||
// Reload files
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("\"{}\": {}", input, output).as_ref(),
|
||||
);
|
||||
let wrkdir: PathBuf = self.local.wrkdir.clone();
|
||||
self.local_scan(wrkdir.as_path());
|
||||
}
|
||||
Err(err) => {
|
||||
// Report err
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not execute command \"{}\": {}", input, err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_remote_exec(&mut self, input: String) {
|
||||
match self.client.as_mut().exec(input.as_str()) {
|
||||
Ok(output) => {
|
||||
// Reload files
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("\"{}\": {}", input, output).as_ref(),
|
||||
);
|
||||
self.reload_remote_dir();
|
||||
}
|
||||
Err(err) => {
|
||||
// Report err
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not execute command \"{}\": {}", input, err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_local_find(&mut self, input: String) -> Result<Vec<FsEntry>, String> {
|
||||
match self.context.as_mut().unwrap().local.find(input.as_str()) {
|
||||
Ok(entries) => Ok(entries),
|
||||
Err(err) => Err(format!("Could not search for files: {}", err)),
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_remote_find(&mut self, input: String) -> Result<Vec<FsEntry>, String> {
|
||||
match self.client.as_mut().find(input.as_str()) {
|
||||
Ok(entries) => Ok(entries),
|
||||
Err(err) => Err(format!("Could not search for files: {}", err)),
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_find_changedir(&mut self, idx: usize) {
|
||||
// Match entry
|
||||
if let Some(entry) = self.found.as_ref().unwrap().get(idx) {
|
||||
// Get path: if a directory, use directory path; if it is a File, get parent path
|
||||
let path: PathBuf = match entry {
|
||||
FsEntry::Directory(dir) => dir.abs_path.clone(),
|
||||
FsEntry::File(file) => match file.abs_path.parent() {
|
||||
None => PathBuf::from("."),
|
||||
Some(p) => p.to_path_buf(),
|
||||
},
|
||||
};
|
||||
// Change directory
|
||||
match self.tab {
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::Local => {
|
||||
self.local_changedir(path.as_path(), true)
|
||||
}
|
||||
FileExplorerTab::FindRemote | FileExplorerTab::Remote => {
|
||||
self.remote_changedir(path.as_path(), true)
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_find_transfer(&mut self, idx: usize, name: Option<String>) {
|
||||
let entry: Option<FsEntry> = self.found.as_ref().unwrap().get(idx).cloned();
|
||||
if let Some(entry) = entry {
|
||||
// Download file
|
||||
match self.tab {
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::Local => {
|
||||
let wrkdir: PathBuf = self.remote.wrkdir.clone();
|
||||
self.filetransfer_send(&entry.get_realfile(), wrkdir.as_path(), name);
|
||||
}
|
||||
FileExplorerTab::FindRemote | FileExplorerTab::Remote => {
|
||||
let wrkdir: PathBuf = self.local.wrkdir.clone();
|
||||
self.filetransfer_recv(&entry.get_realfile(), wrkdir.as_path(), name);
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn action_find_delete(&mut self, idx: usize) {
|
||||
let entry: Option<FsEntry> = self.found.as_ref().unwrap().get(idx).cloned();
|
||||
if let Some(entry) = entry {
|
||||
// Download file
|
||||
match self.tab {
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::Local => {
|
||||
let full_path: PathBuf = entry.get_abs_path();
|
||||
// Delete file or directory and report status as popup
|
||||
match self.context.as_mut().unwrap().local.remove(&entry) {
|
||||
Ok(_) => {
|
||||
// Reload files
|
||||
let p: PathBuf = self.local.wrkdir.clone();
|
||||
self.local_scan(p.as_path());
|
||||
// Log
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Removed file \"{}\"", full_path.display()).as_ref(),
|
||||
);
|
||||
}
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not delete file \"{}\": {}",
|
||||
full_path.display(),
|
||||
err
|
||||
),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
FileExplorerTab::FindRemote | FileExplorerTab::Remote => {
|
||||
let full_path: PathBuf = entry.get_abs_path();
|
||||
// Delete file
|
||||
match self.client.remove(&entry) {
|
||||
Ok(_) => {
|
||||
self.reload_remote_dir();
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Removed file \"{}\"", full_path.display()).as_ref(),
|
||||
);
|
||||
}
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not delete file \"{}\": {}",
|
||||
full_path.display(),
|
||||
err
|
||||
),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### get_local_file_entry
|
||||
///
|
||||
/// Get local file entry
|
||||
pub(super) fn get_local_file_entry(&self) -> Option<&FsEntry> {
|
||||
match self.get_local_file_idx() {
|
||||
None => None,
|
||||
Some(idx) => self.local.get(idx),
|
||||
}
|
||||
}
|
||||
|
||||
/// ### get_remote_file_entry
|
||||
///
|
||||
/// Get remote file entry
|
||||
pub(super) fn get_remote_file_entry(&self) -> Option<&FsEntry> {
|
||||
match self.get_remote_file_idx() {
|
||||
None => None,
|
||||
Some(idx) => self.remote.get(idx),
|
||||
}
|
||||
}
|
||||
|
||||
// -- private
|
||||
|
||||
/// ### get_local_file_idx
|
||||
///
|
||||
/// Get index of selected file in the local tab
|
||||
fn get_local_file_idx(&self) -> Option<usize> {
|
||||
match self.view.get_value(super::COMPONENT_EXPLORER_LOCAL) {
|
||||
Some(Payload::Unsigned(idx)) => Some(idx),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### get_remote_file_idx
|
||||
///
|
||||
/// Get index of selected file in the remote file
|
||||
fn get_remote_file_idx(&self) -> Option<usize> {
|
||||
match self.view.get_value(super::COMPONENT_EXPLORER_REMOTE) {
|
||||
Some(Payload::Unsigned(idx)) => Some(idx),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
}
|
||||
@@ -1,856 +0,0 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// Deps
|
||||
extern crate bytesize;
|
||||
extern crate content_inspector;
|
||||
extern crate crossterm;
|
||||
extern crate tempfile;
|
||||
|
||||
// Locals
|
||||
use super::{FileTransferActivity, LogLevel};
|
||||
use crate::fs::{FsEntry, FsFile};
|
||||
use crate::utils::fmt::fmt_millis;
|
||||
|
||||
// Ext
|
||||
use bytesize::ByteSize;
|
||||
use crossterm::terminal::{disable_raw_mode, enable_raw_mode};
|
||||
use std::fs::OpenOptions;
|
||||
use std::io::{Read, Seek, Write};
|
||||
use std::path::{Path, PathBuf};
|
||||
use std::time::{Instant, SystemTime};
|
||||
|
||||
impl FileTransferActivity {
|
||||
/// ### connect
|
||||
///
|
||||
/// Connect to remote
|
||||
pub(super) fn connect(&mut self) {
|
||||
let params = self.context.as_ref().unwrap().ft_params.as_ref().unwrap();
|
||||
let addr: String = params.address.clone();
|
||||
let entry_dir: Option<PathBuf> = params.entry_directory.clone();
|
||||
// Connect to remote
|
||||
match self.client.connect(
|
||||
params.address.clone(),
|
||||
params.port,
|
||||
params.username.clone(),
|
||||
params.password.clone(),
|
||||
) {
|
||||
Ok(welcome) => {
|
||||
if let Some(banner) = welcome {
|
||||
// Log welcome
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Established connection with '{}': \"{}\"", addr, banner).as_ref(),
|
||||
);
|
||||
}
|
||||
// Try to change directory to entry directory
|
||||
let mut remote_chdir: Option<PathBuf> = None;
|
||||
if let Some(entry_directory) = &entry_dir {
|
||||
remote_chdir = Some(entry_directory.clone());
|
||||
}
|
||||
if let Some(entry_directory) = remote_chdir {
|
||||
self.remote_changedir(entry_directory.as_path(), false);
|
||||
}
|
||||
// Set state to explorer
|
||||
self.umount_wait();
|
||||
self.reload_remote_dir();
|
||||
// Update file lists
|
||||
self.update_local_filelist();
|
||||
self.update_remote_filelist();
|
||||
}
|
||||
Err(err) => {
|
||||
// Set popup fatal error
|
||||
self.mount_fatal(&err.to_string());
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### disconnect
|
||||
///
|
||||
/// disconnect from remote
|
||||
pub(super) fn disconnect(&mut self) {
|
||||
let params = self.context.as_ref().unwrap().ft_params.as_ref().unwrap();
|
||||
let msg: String = format!("Disconnecting from {}...", params.address);
|
||||
// Show popup disconnecting
|
||||
self.mount_wait(msg.as_str());
|
||||
// Disconnect
|
||||
let _ = self.client.disconnect();
|
||||
// Quit
|
||||
self.exit_reason = Some(super::ExitReason::Disconnect);
|
||||
}
|
||||
|
||||
/// ### disconnect_and_quit
|
||||
///
|
||||
/// disconnect from remote and then quit
|
||||
pub(super) fn disconnect_and_quit(&mut self) {
|
||||
self.disconnect();
|
||||
self.exit_reason = Some(super::ExitReason::Quit);
|
||||
}
|
||||
|
||||
/// ### reload_remote_dir
|
||||
///
|
||||
/// Reload remote directory entries
|
||||
pub(super) fn reload_remote_dir(&mut self) {
|
||||
// Get current entries
|
||||
if let Ok(pwd) = self.client.pwd() {
|
||||
self.remote_scan(pwd.as_path());
|
||||
// Set wrkdir
|
||||
self.remote.wrkdir = pwd;
|
||||
}
|
||||
}
|
||||
|
||||
/// ### filetransfer_send
|
||||
///
|
||||
/// Send fs entry to remote.
|
||||
/// If dst_name is Some, entry will be saved with a different name.
|
||||
/// If entry is a directory, this applies to directory only
|
||||
pub(super) fn filetransfer_send(
|
||||
&mut self,
|
||||
entry: &FsEntry,
|
||||
curr_remote_path: &Path,
|
||||
dst_name: Option<String>,
|
||||
) {
|
||||
// Write popup
|
||||
let file_name: String = match entry {
|
||||
FsEntry::Directory(dir) => dir.name.clone(),
|
||||
FsEntry::File(file) => file.name.clone(),
|
||||
};
|
||||
// Get remote path
|
||||
let mut remote_path: PathBuf = PathBuf::from(curr_remote_path);
|
||||
let remote_file_name: PathBuf = match dst_name {
|
||||
Some(s) => PathBuf::from(s.as_str()),
|
||||
None => PathBuf::from(file_name.as_str()),
|
||||
};
|
||||
remote_path.push(remote_file_name);
|
||||
// Match entry
|
||||
match entry {
|
||||
FsEntry::File(file) => {
|
||||
let _ = self.filetransfer_send_file(file, remote_path.as_path(), file_name);
|
||||
}
|
||||
FsEntry::Directory(dir) => {
|
||||
// Create directory on remote
|
||||
match self.client.mkdir(remote_path.as_path()) {
|
||||
Ok(_) => {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Created directory \"{}\"", remote_path.display()).as_ref(),
|
||||
);
|
||||
// Get files in dir
|
||||
match self
|
||||
.context
|
||||
.as_ref()
|
||||
.unwrap()
|
||||
.local
|
||||
.scan_dir(dir.abs_path.as_path())
|
||||
{
|
||||
Ok(entries) => {
|
||||
// Iterate over files
|
||||
for entry in entries.iter() {
|
||||
// If aborted; break
|
||||
if self.transfer.aborted {
|
||||
break;
|
||||
}
|
||||
// Send entry; name is always None after first call
|
||||
self.filetransfer_send(&entry, remote_path.as_path(), None);
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not scan directory \"{}\": {}",
|
||||
dir.abs_path.display(),
|
||||
err
|
||||
),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Failed to create directory \"{}\": {}",
|
||||
remote_path.display(),
|
||||
err
|
||||
),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
// Scan dir on remote
|
||||
let path: PathBuf = self.remote.wrkdir.clone();
|
||||
self.remote_scan(path.as_path());
|
||||
// If aborted; show popup
|
||||
if self.transfer.aborted {
|
||||
// Log abort
|
||||
self.log_and_alert(
|
||||
LogLevel::Warn,
|
||||
format!("Upload aborted for \"{}\"!", entry.get_abs_path().display()),
|
||||
);
|
||||
// Set aborted to false
|
||||
self.transfer.aborted = false;
|
||||
} else {
|
||||
// @! Successful
|
||||
// Eventually, Remove progress bar
|
||||
self.umount_progress_bar();
|
||||
}
|
||||
}
|
||||
|
||||
/// ### filetransfer_recv
|
||||
///
|
||||
/// Recv fs entry from remote.
|
||||
/// If dst_name is Some, entry will be saved with a different name.
|
||||
/// If entry is a directory, this applies to directory only
|
||||
pub(super) fn filetransfer_recv(
|
||||
&mut self,
|
||||
entry: &FsEntry,
|
||||
local_path: &Path,
|
||||
dst_name: Option<String>,
|
||||
) {
|
||||
// Write popup
|
||||
let file_name: String = match entry {
|
||||
FsEntry::Directory(dir) => dir.name.clone(),
|
||||
FsEntry::File(file) => file.name.clone(),
|
||||
};
|
||||
// Match entry
|
||||
match entry {
|
||||
FsEntry::File(file) => {
|
||||
// Get local file
|
||||
let mut local_file_path: PathBuf = PathBuf::from(local_path);
|
||||
let local_file_name: String = match dst_name {
|
||||
Some(n) => n,
|
||||
None => file.name.clone(),
|
||||
};
|
||||
local_file_path.push(local_file_name.as_str());
|
||||
// Download file
|
||||
if let Err(err) =
|
||||
self.filetransfer_recv_file(local_file_path.as_path(), file, file_name)
|
||||
{
|
||||
self.log_and_alert(LogLevel::Error, err);
|
||||
}
|
||||
}
|
||||
FsEntry::Directory(dir) => {
|
||||
// Get dir name
|
||||
let mut local_dir_path: PathBuf = PathBuf::from(local_path);
|
||||
match dst_name {
|
||||
Some(name) => local_dir_path.push(name),
|
||||
None => local_dir_path.push(dir.name.as_str()),
|
||||
}
|
||||
// Create directory on local
|
||||
match self
|
||||
.context
|
||||
.as_mut()
|
||||
.unwrap()
|
||||
.local
|
||||
.mkdir_ex(local_dir_path.as_path(), true)
|
||||
{
|
||||
Ok(_) => {
|
||||
// Apply file mode to directory
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
if let Some(pex) = dir.unix_pex {
|
||||
if let Err(err) = self
|
||||
.context
|
||||
.as_ref()
|
||||
.unwrap()
|
||||
.local
|
||||
.chmod(local_dir_path.as_path(), pex)
|
||||
{
|
||||
self.log(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not apply file mode {:?} to \"{}\": {}",
|
||||
pex,
|
||||
local_dir_path.display(),
|
||||
err
|
||||
)
|
||||
.as_ref(),
|
||||
);
|
||||
}
|
||||
}
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Created directory \"{}\"", local_dir_path.display()).as_ref(),
|
||||
);
|
||||
// Get files in dir
|
||||
match self.client.list_dir(dir.abs_path.as_path()) {
|
||||
Ok(entries) => {
|
||||
// Iterate over files
|
||||
for entry in entries.iter() {
|
||||
// If transfer has been aborted; break
|
||||
if self.transfer.aborted {
|
||||
break;
|
||||
}
|
||||
// Receive entry; name is always None after first call
|
||||
// Local path becomes local_dir_path
|
||||
self.filetransfer_recv(&entry, local_dir_path.as_path(), None);
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not scan directory \"{}\": {}",
|
||||
dir.abs_path.display(),
|
||||
err
|
||||
),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
self.log(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Failed to create directory \"{}\": {}",
|
||||
local_dir_path.display(),
|
||||
err
|
||||
)
|
||||
.as_ref(),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
// Reload directory on local
|
||||
self.local_scan(local_path);
|
||||
// if aborted; show alert
|
||||
if self.transfer.aborted {
|
||||
// Log abort
|
||||
self.log_and_alert(
|
||||
LogLevel::Warn,
|
||||
format!(
|
||||
"Download aborted for \"{}\"!",
|
||||
entry.get_abs_path().display()
|
||||
),
|
||||
);
|
||||
// Reset aborted to false
|
||||
self.transfer.aborted = false;
|
||||
} else {
|
||||
// Eventually, Reset input mode to explorer
|
||||
self.umount_progress_bar();
|
||||
}
|
||||
}
|
||||
|
||||
/// ### filetransfer_send_file
|
||||
///
|
||||
/// Send local file and write it to remote path
|
||||
fn filetransfer_send_file(
|
||||
&mut self,
|
||||
local: &FsFile,
|
||||
remote: &Path,
|
||||
file_name: String,
|
||||
) -> Result<(), String> {
|
||||
// Upload file
|
||||
// Try to open local file
|
||||
match self
|
||||
.context
|
||||
.as_ref()
|
||||
.unwrap()
|
||||
.local
|
||||
.open_file_read(local.abs_path.as_path())
|
||||
{
|
||||
Ok(mut fhnd) => match self.client.send_file(local, remote) {
|
||||
Ok(mut rhnd) => {
|
||||
// Write file
|
||||
let file_size: usize =
|
||||
fhnd.seek(std::io::SeekFrom::End(0)).unwrap_or(0) as usize;
|
||||
// rewind
|
||||
if let Err(err) = fhnd.seek(std::io::SeekFrom::Start(0)) {
|
||||
return Err(format!("Could not rewind local file: {}", err));
|
||||
}
|
||||
// Write remote file
|
||||
let mut total_bytes_written: usize = 0;
|
||||
// Reset transfer states
|
||||
self.transfer.reset();
|
||||
let mut last_progress_val: f64 = 0.0;
|
||||
let mut last_input_event_fetch: Instant = Instant::now();
|
||||
// Mount progress bar
|
||||
self.mount_progress_bar();
|
||||
// While the entire file hasn't been completely written,
|
||||
// Or filetransfer has been aborted
|
||||
while total_bytes_written < file_size && !self.transfer.aborted {
|
||||
// Handle input events (each 500ms)
|
||||
if last_input_event_fetch.elapsed().as_millis() >= 500 {
|
||||
// Read events
|
||||
self.read_input_event();
|
||||
// Reset instant
|
||||
last_input_event_fetch = Instant::now();
|
||||
}
|
||||
// Read till you can
|
||||
let mut buffer: [u8; 65536] = [0; 65536];
|
||||
match fhnd.read(&mut buffer) {
|
||||
Ok(bytes_read) => {
|
||||
total_bytes_written += bytes_read;
|
||||
if bytes_read == 0 {
|
||||
continue;
|
||||
} else {
|
||||
let mut buf_start: usize = 0;
|
||||
while buf_start < bytes_read {
|
||||
// Write bytes
|
||||
match rhnd.write(&buffer[buf_start..bytes_read]) {
|
||||
Ok(bytes) => {
|
||||
buf_start += bytes;
|
||||
}
|
||||
Err(err) => {
|
||||
self.umount_progress_bar();
|
||||
return Err(format!(
|
||||
"Could not write remote file: {}",
|
||||
err
|
||||
));
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
self.umount_progress_bar();
|
||||
return Err(format!("Could not read local file: {}", err));
|
||||
}
|
||||
}
|
||||
// Increase progress
|
||||
self.transfer.set_progress(total_bytes_written, file_size);
|
||||
// Draw only if a significant progress has been made (performance improvement)
|
||||
if last_progress_val < self.transfer.progress - 1.0 {
|
||||
// Draw
|
||||
self.update_progress_bar(format!("Uploading \"{}\"...", file_name));
|
||||
self.view();
|
||||
last_progress_val = self.transfer.progress;
|
||||
}
|
||||
}
|
||||
// Umount progress bar
|
||||
self.umount_progress_bar();
|
||||
// Finalize stream
|
||||
if let Err(err) = self.client.on_sent(rhnd) {
|
||||
self.log(
|
||||
LogLevel::Warn,
|
||||
format!("Could not finalize remote stream: \"{}\"", err).as_str(),
|
||||
);
|
||||
}
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!(
|
||||
"Saved file \"{}\" to \"{}\" (took {} seconds; at {}/s)",
|
||||
local.abs_path.display(),
|
||||
remote.display(),
|
||||
fmt_millis(self.transfer.started.elapsed()),
|
||||
ByteSize(self.transfer.bytes_per_second()),
|
||||
)
|
||||
.as_ref(),
|
||||
);
|
||||
}
|
||||
Err(err) => {
|
||||
return Err(format!(
|
||||
"Failed to upload file \"{}\": {}",
|
||||
local.abs_path.display(),
|
||||
err
|
||||
))
|
||||
}
|
||||
},
|
||||
Err(err) => {
|
||||
return Err(format!(
|
||||
"Failed to open file \"{}\": {}",
|
||||
local.abs_path.display(),
|
||||
err
|
||||
))
|
||||
}
|
||||
}
|
||||
Ok(())
|
||||
}
|
||||
|
||||
/// ### filetransfer_recv_file
|
||||
///
|
||||
/// Receive file from remote and write it to local path
|
||||
fn filetransfer_recv_file(
|
||||
&mut self,
|
||||
local: &Path,
|
||||
remote: &FsFile,
|
||||
file_name: String,
|
||||
) -> Result<(), String> {
|
||||
// Try to open local file
|
||||
match self.context.as_ref().unwrap().local.open_file_write(local) {
|
||||
Ok(mut local_file) => {
|
||||
// Download file from remote
|
||||
match self.client.recv_file(remote) {
|
||||
Ok(mut rhnd) => {
|
||||
let mut total_bytes_written: usize = 0;
|
||||
// Reset transfer states
|
||||
self.transfer.reset();
|
||||
// Write local file
|
||||
let mut last_progress_val: f64 = 0.0;
|
||||
let mut last_input_event_fetch: Instant = Instant::now();
|
||||
// Mount progress bar
|
||||
self.mount_progress_bar();
|
||||
// While the entire file hasn't been completely read,
|
||||
// Or filetransfer has been aborted
|
||||
while total_bytes_written < remote.size && !self.transfer.aborted {
|
||||
// Handle input events (each 500 ms)
|
||||
if last_input_event_fetch.elapsed().as_millis() >= 500 {
|
||||
// Read events
|
||||
self.read_input_event();
|
||||
// Reset instant
|
||||
last_input_event_fetch = Instant::now();
|
||||
}
|
||||
// Read till you can
|
||||
let mut buffer: [u8; 65536] = [0; 65536];
|
||||
match rhnd.read(&mut buffer) {
|
||||
Ok(bytes_read) => {
|
||||
total_bytes_written += bytes_read;
|
||||
if bytes_read == 0 {
|
||||
continue;
|
||||
} else {
|
||||
let mut buf_start: usize = 0;
|
||||
while buf_start < bytes_read {
|
||||
// Write bytes
|
||||
match local_file.write(&buffer[buf_start..bytes_read]) {
|
||||
Ok(bytes) => buf_start += bytes,
|
||||
Err(err) => {
|
||||
self.umount_progress_bar();
|
||||
return Err(format!(
|
||||
"Could not write local file: {}",
|
||||
err
|
||||
));
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
self.umount_progress_bar();
|
||||
return Err(format!("Could not read remote file: {}", err));
|
||||
}
|
||||
}
|
||||
// Set progress
|
||||
self.transfer.set_progress(total_bytes_written, remote.size);
|
||||
// Draw only if a significant progress has been made (performance improvement)
|
||||
if last_progress_val < self.transfer.progress - 1.0 {
|
||||
// Draw
|
||||
self.update_progress_bar(format!("Downloading \"{}\"", file_name));
|
||||
self.view();
|
||||
last_progress_val = self.transfer.progress;
|
||||
}
|
||||
}
|
||||
// Umount progress bar
|
||||
self.umount_progress_bar();
|
||||
// Finalize stream
|
||||
if let Err(err) = self.client.on_recv(rhnd) {
|
||||
self.log(
|
||||
LogLevel::Warn,
|
||||
format!("Could not finalize remote stream: \"{}\"", err).as_str(),
|
||||
);
|
||||
}
|
||||
// Apply file mode to file
|
||||
#[cfg(any(target_os = "unix", target_os = "macos", target_os = "linux"))]
|
||||
if let Some(pex) = remote.unix_pex {
|
||||
if let Err(err) = self.context.as_ref().unwrap().local.chmod(local, pex)
|
||||
{
|
||||
self.log(
|
||||
LogLevel::Error,
|
||||
format!(
|
||||
"Could not apply file mode {:?} to \"{}\": {}",
|
||||
pex,
|
||||
local.display(),
|
||||
err
|
||||
)
|
||||
.as_ref(),
|
||||
);
|
||||
}
|
||||
}
|
||||
// Log
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!(
|
||||
"Saved file \"{}\" to \"{}\" (took {} seconds; at {}/s)",
|
||||
remote.abs_path.display(),
|
||||
local.display(),
|
||||
fmt_millis(self.transfer.started.elapsed()),
|
||||
ByteSize(self.transfer.bytes_per_second()),
|
||||
)
|
||||
.as_ref(),
|
||||
);
|
||||
}
|
||||
Err(err) => {
|
||||
return Err(format!(
|
||||
"Failed to download file \"{}\": {}",
|
||||
remote.abs_path.display(),
|
||||
err
|
||||
))
|
||||
}
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
return Err(format!(
|
||||
"Failed to open local file for write \"{}\": {}",
|
||||
local.display(),
|
||||
err
|
||||
))
|
||||
}
|
||||
}
|
||||
Ok(())
|
||||
}
|
||||
|
||||
/// ### local_scan
|
||||
///
|
||||
/// Scan current local directory
|
||||
pub(super) fn local_scan(&mut self, path: &Path) {
|
||||
match self.context.as_ref().unwrap().local.scan_dir(path) {
|
||||
Ok(files) => {
|
||||
// Set files and sort (sorting is implicit)
|
||||
self.local.set_files(files);
|
||||
}
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not scan current directory: {}", err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### remote_scan
|
||||
///
|
||||
/// Scan current remote directory
|
||||
pub(super) fn remote_scan(&mut self, path: &Path) {
|
||||
match self.client.list_dir(path) {
|
||||
Ok(files) => {
|
||||
// Set files and sort (sorting is implicit)
|
||||
self.remote.set_files(files);
|
||||
}
|
||||
Err(err) => {
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not scan current directory: {}", err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### local_changedir
|
||||
///
|
||||
/// Change directory for local
|
||||
pub(super) fn local_changedir(&mut self, path: &Path, push: bool) {
|
||||
// Get current directory
|
||||
let prev_dir: PathBuf = self.local.wrkdir.clone();
|
||||
// Change directory
|
||||
match self.context.as_mut().unwrap().local.change_wrkdir(path) {
|
||||
Ok(_) => {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Changed directory on local: {}", path.display()).as_str(),
|
||||
);
|
||||
// Reload files
|
||||
self.local_scan(path);
|
||||
// Set wrkdir
|
||||
self.local.wrkdir = PathBuf::from(path);
|
||||
// Push prev_dir to stack
|
||||
if push {
|
||||
self.local.pushd(prev_dir.as_path())
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
// Report err
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not change working directory: {}", err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn remote_changedir(&mut self, path: &Path, push: bool) {
|
||||
// Get current directory
|
||||
let prev_dir: PathBuf = self.remote.wrkdir.clone();
|
||||
// Change directory
|
||||
match self.client.as_mut().change_dir(path) {
|
||||
Ok(_) => {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Changed directory on remote: {}", path.display()).as_str(),
|
||||
);
|
||||
// Update files
|
||||
self.remote_scan(path);
|
||||
// Set wrkdir
|
||||
self.remote.wrkdir = PathBuf::from(path);
|
||||
// Push prev_dir to stack
|
||||
if push {
|
||||
self.remote.pushd(prev_dir.as_path())
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
// Report err
|
||||
self.log_and_alert(
|
||||
LogLevel::Error,
|
||||
format!("Could not change working directory: {}", err),
|
||||
);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### edit_local_file
|
||||
///
|
||||
/// Edit a file on localhost
|
||||
pub(super) fn edit_local_file(&mut self, path: &Path) -> Result<(), String> {
|
||||
// Read first 2048 bytes or less from file to check if it is textual
|
||||
match OpenOptions::new().read(true).open(path) {
|
||||
Ok(mut f) => {
|
||||
// Read
|
||||
let mut buff: [u8; 2048] = [0; 2048];
|
||||
match f.read(&mut buff) {
|
||||
Ok(size) => {
|
||||
if content_inspector::inspect(&buff[0..size]).is_binary() {
|
||||
return Err("Could not open file in editor: file is binary".to_string());
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
return Err(format!("Could not read file: {}", err));
|
||||
}
|
||||
}
|
||||
}
|
||||
Err(err) => {
|
||||
return Err(format!("Could not read file: {}", err));
|
||||
}
|
||||
}
|
||||
// Put input mode back to normal
|
||||
let _ = disable_raw_mode();
|
||||
// Leave alternate mode
|
||||
if let Some(ctx) = self.context.as_mut() {
|
||||
ctx.leave_alternate_screen();
|
||||
}
|
||||
// Open editor
|
||||
match edit::edit_file(path) {
|
||||
Ok(_) => self.log(
|
||||
LogLevel::Info,
|
||||
format!(
|
||||
"Changes performed through editor saved to \"{}\"!",
|
||||
path.display()
|
||||
)
|
||||
.as_str(),
|
||||
),
|
||||
Err(err) => return Err(format!("Could not open editor: {}", err)),
|
||||
}
|
||||
if let Some(ctx) = self.context.as_mut() {
|
||||
// Clear screen
|
||||
ctx.clear_screen();
|
||||
// Enter alternate mode
|
||||
ctx.enter_alternate_screen();
|
||||
}
|
||||
// Re-enable raw mode
|
||||
let _ = enable_raw_mode();
|
||||
Ok(())
|
||||
}
|
||||
|
||||
/// ### edit_remote_file
|
||||
///
|
||||
/// Edit file on remote host
|
||||
pub(super) fn edit_remote_file(&mut self, file: &FsFile) -> Result<(), String> {
|
||||
// Create temp file
|
||||
let tmpfile: tempfile::NamedTempFile = match tempfile::NamedTempFile::new() {
|
||||
Ok(f) => f,
|
||||
Err(err) => {
|
||||
return Err(format!("Could not create temporary file: {}", err));
|
||||
}
|
||||
};
|
||||
// Download file
|
||||
if let Err(err) = self.filetransfer_recv_file(tmpfile.path(), file, file.name.clone()) {
|
||||
return Err(err);
|
||||
}
|
||||
// Get current file modification time
|
||||
let prev_mtime: SystemTime = match self.context.as_ref().unwrap().local.stat(tmpfile.path())
|
||||
{
|
||||
Ok(e) => e.get_last_change_time(),
|
||||
Err(err) => {
|
||||
return Err(format!(
|
||||
"Could not stat \"{}\": {}",
|
||||
tmpfile.path().display(),
|
||||
err
|
||||
))
|
||||
}
|
||||
};
|
||||
// Edit file
|
||||
if let Err(err) = self.edit_local_file(tmpfile.path()) {
|
||||
return Err(err);
|
||||
}
|
||||
// Get local fs entry
|
||||
let tmpfile_entry: FsEntry = match self.context.as_ref().unwrap().local.stat(tmpfile.path())
|
||||
{
|
||||
Ok(e) => e,
|
||||
Err(err) => {
|
||||
return Err(format!(
|
||||
"Could not stat \"{}\": {}",
|
||||
tmpfile.path().display(),
|
||||
err
|
||||
))
|
||||
}
|
||||
};
|
||||
// Check if file has changed
|
||||
match prev_mtime != tmpfile_entry.get_last_change_time() {
|
||||
true => {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!(
|
||||
"File \"{}\" has changed; writing changes to remote",
|
||||
file.abs_path.display()
|
||||
)
|
||||
.as_ref(),
|
||||
);
|
||||
// Get local fs entry
|
||||
let tmpfile_entry: FsEntry =
|
||||
match self.context.as_ref().unwrap().local.stat(tmpfile.path()) {
|
||||
Ok(e) => e,
|
||||
Err(err) => {
|
||||
return Err(format!(
|
||||
"Could not stat \"{}\": {}",
|
||||
tmpfile.path().display(),
|
||||
err
|
||||
))
|
||||
}
|
||||
};
|
||||
// Write file
|
||||
let tmpfile_entry: &FsFile = match &tmpfile_entry {
|
||||
FsEntry::Directory(_) => panic!("tempfile is a directory for some reason"),
|
||||
FsEntry::File(f) => f,
|
||||
};
|
||||
// Send file
|
||||
if let Err(err) = self.filetransfer_send_file(
|
||||
tmpfile_entry,
|
||||
file.abs_path.as_path(),
|
||||
file.name.clone(),
|
||||
) {
|
||||
return Err(err);
|
||||
}
|
||||
}
|
||||
false => {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("File \"{}\" hasn't changed", file.abs_path.display()).as_ref(),
|
||||
);
|
||||
}
|
||||
}
|
||||
Ok(())
|
||||
}
|
||||
}
|
||||
@@ -1,991 +0,0 @@
|
||||
//! ## FileTransferActivity
|
||||
//!
|
||||
//! `filetransfer_activiy` is the module which implements the Filetransfer activity, which is the main activity afterall
|
||||
|
||||
/**
|
||||
* MIT License
|
||||
*
|
||||
* termscp - Copyright (c) 2021 Christian Visintin
|
||||
*
|
||||
* Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
* of this software and associated documentation files (the "Software"), to deal
|
||||
* in the Software without restriction, including without limitation the rights
|
||||
* to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
* copies of the Software, and to permit persons to whom the Software is
|
||||
* furnished to do so, subject to the following conditions:
|
||||
*
|
||||
* The above copyright notice and this permission notice shall be included in all
|
||||
* copies or substantial portions of the Software.
|
||||
*
|
||||
* THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
* IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
* FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
* AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
* LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
* OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
* SOFTWARE.
|
||||
*/
|
||||
// deps
|
||||
extern crate bytesize;
|
||||
// locals
|
||||
use super::{
|
||||
FileExplorerTab, FileTransferActivity, LogLevel, COMPONENT_EXPLORER_FIND,
|
||||
COMPONENT_EXPLORER_LOCAL, COMPONENT_EXPLORER_REMOTE, COMPONENT_INPUT_COPY,
|
||||
COMPONENT_INPUT_EXEC, COMPONENT_INPUT_FIND, COMPONENT_INPUT_GOTO, COMPONENT_INPUT_MKDIR,
|
||||
COMPONENT_INPUT_NEWFILE, COMPONENT_INPUT_RENAME, COMPONENT_INPUT_SAVEAS,
|
||||
COMPONENT_LIST_FILEINFO, COMPONENT_LOG_BOX, COMPONENT_PROGRESS_BAR, COMPONENT_RADIO_DELETE,
|
||||
COMPONENT_RADIO_DISCONNECT, COMPONENT_RADIO_QUIT, COMPONENT_RADIO_SORTING,
|
||||
COMPONENT_TEXT_ERROR, COMPONENT_TEXT_FATAL, COMPONENT_TEXT_HELP,
|
||||
};
|
||||
use crate::fs::explorer::FileSorting;
|
||||
use crate::fs::FsEntry;
|
||||
use crate::ui::activities::keymap::*;
|
||||
use crate::ui::layout::props::{
|
||||
PropValue, PropsBuilder, TableBuilder, TextParts, TextSpan, TextSpanBuilder,
|
||||
};
|
||||
use crate::ui::layout::{Msg, Payload};
|
||||
// externals
|
||||
use bytesize::ByteSize;
|
||||
use std::path::{Path, PathBuf};
|
||||
use tui::style::Color;
|
||||
|
||||
impl FileTransferActivity {
|
||||
// -- update
|
||||
|
||||
/// ### update
|
||||
///
|
||||
/// Update auth activity model based on msg
|
||||
/// The function exits when returns None
|
||||
pub(super) fn update(&mut self, msg: Option<(String, Msg)>) -> Option<(String, Msg)> {
|
||||
let ref_msg: Option<(&str, &Msg)> = msg.as_ref().map(|(s, msg)| (s.as_str(), msg));
|
||||
// Match msg
|
||||
match ref_msg {
|
||||
None => None, // Exit after None
|
||||
Some(msg) => match msg {
|
||||
// -- local tab
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_RIGHT) => {
|
||||
// Change tab
|
||||
self.view.active(COMPONENT_EXPLORER_REMOTE);
|
||||
self.tab = FileExplorerTab::Remote;
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_BACKSPACE) => {
|
||||
// Go to previous directory
|
||||
if let Some(d) = self.local.popd() {
|
||||
self.local_changedir(d.as_path(), false);
|
||||
}
|
||||
// Reload file list component
|
||||
self.update_local_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, Msg::OnSubmit(Payload::Unsigned(idx))) => {
|
||||
// Match selected file
|
||||
let mut entry: Option<FsEntry> = None;
|
||||
if let Some(e) = self.local.get(*idx) {
|
||||
entry = Some(e.clone());
|
||||
}
|
||||
if let Some(entry) = entry {
|
||||
// If directory, enter directory, otherwise check if symlink
|
||||
match entry {
|
||||
FsEntry::Directory(dir) => {
|
||||
self.local_changedir(dir.abs_path.as_path(), true);
|
||||
self.update_local_filelist()
|
||||
}
|
||||
FsEntry::File(file) => {
|
||||
// Check if symlink
|
||||
match &file.symlink {
|
||||
Some(pointer) => match &**pointer {
|
||||
FsEntry::Directory(dir) => {
|
||||
self.local_changedir(dir.abs_path.as_path(), true);
|
||||
self.update_local_filelist()
|
||||
}
|
||||
_ => None,
|
||||
},
|
||||
None => None,
|
||||
}
|
||||
}
|
||||
}
|
||||
} else {
|
||||
None
|
||||
}
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_SPACE) => {
|
||||
// Get pwd
|
||||
let wrkdir: PathBuf = self.remote.wrkdir.clone();
|
||||
// Get file and clone (due to mutable / immutable stuff...)
|
||||
if self.get_local_file_entry().is_some() {
|
||||
let file: FsEntry = self.get_local_file_entry().unwrap().clone();
|
||||
let name: String = file.get_name().to_string();
|
||||
// Call upload; pass realfile, keep link name
|
||||
self.filetransfer_send(&file.get_realfile(), wrkdir.as_path(), Some(name));
|
||||
self.update_remote_filelist()
|
||||
} else {
|
||||
None
|
||||
}
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_A) => {
|
||||
// Toggle hidden files
|
||||
self.local.toggle_hidden_files();
|
||||
// Reload file list component
|
||||
self.update_local_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_I) => {
|
||||
let file: Option<FsEntry> = self.get_local_file_entry().cloned();
|
||||
if let Some(file) = file {
|
||||
self.mount_file_info(&file);
|
||||
}
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_L) => {
|
||||
// Reload directory
|
||||
let pwd: PathBuf = self.local.wrkdir.clone();
|
||||
self.local_scan(pwd.as_path());
|
||||
// Reload file list component
|
||||
self.update_local_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_O) => {
|
||||
// Clone entry due to mutable stuff...
|
||||
if self.get_local_file_entry().is_some() {
|
||||
let fsentry: FsEntry = self.get_local_file_entry().unwrap().clone();
|
||||
// Check if file
|
||||
if fsentry.is_file() {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Opening file \"{}\"...", fsentry.get_abs_path().display())
|
||||
.as_str(),
|
||||
);
|
||||
// Edit file
|
||||
match self.edit_local_file(fsentry.get_abs_path().as_path()) {
|
||||
Ok(_) => {
|
||||
// Reload directory
|
||||
let pwd: PathBuf = self.local.wrkdir.clone();
|
||||
self.local_scan(pwd.as_path());
|
||||
}
|
||||
Err(err) => self.log_and_alert(LogLevel::Error, err),
|
||||
}
|
||||
}
|
||||
}
|
||||
// Reload file list component
|
||||
self.update_local_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_U) => {
|
||||
// Get pwd
|
||||
let path: PathBuf = self.local.wrkdir.clone();
|
||||
// Go to parent directory
|
||||
if let Some(parent) = path.as_path().parent() {
|
||||
self.local_changedir(parent, true);
|
||||
// Reload file list component
|
||||
}
|
||||
self.update_local_filelist()
|
||||
}
|
||||
// -- remote tab
|
||||
(COMPONENT_EXPLORER_REMOTE, &MSG_KEY_LEFT) => {
|
||||
// Change tab
|
||||
self.view.active(COMPONENT_EXPLORER_LOCAL);
|
||||
self.tab = FileExplorerTab::Local;
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, Msg::OnSubmit(Payload::Unsigned(idx))) => {
|
||||
// Match selected file
|
||||
let mut entry: Option<FsEntry> = None;
|
||||
if let Some(e) = self.remote.get(*idx) {
|
||||
entry = Some(e.clone());
|
||||
}
|
||||
if let Some(entry) = entry {
|
||||
// If directory, enter directory; if file, check if is symlink
|
||||
match entry {
|
||||
FsEntry::Directory(dir) => {
|
||||
self.remote_changedir(dir.abs_path.as_path(), true);
|
||||
self.update_remote_filelist()
|
||||
}
|
||||
FsEntry::File(file) => {
|
||||
match &file.symlink {
|
||||
Some(symlink_entry) => {
|
||||
// If symlink and is directory, point to symlink
|
||||
match &**symlink_entry {
|
||||
FsEntry::Directory(dir) => {
|
||||
self.remote_changedir(dir.abs_path.as_path(), true);
|
||||
self.update_remote_filelist()
|
||||
}
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
None => None,
|
||||
}
|
||||
}
|
||||
}
|
||||
} else {
|
||||
None
|
||||
}
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, &MSG_KEY_SPACE) => {
|
||||
// Get file and clone (due to mutable / immutable stuff...)
|
||||
if self.get_remote_file_entry().is_some() {
|
||||
let file: FsEntry = self.get_remote_file_entry().unwrap().clone();
|
||||
let name: String = file.get_name().to_string();
|
||||
// Call upload; pass realfile, keep link name
|
||||
let wrkdir: PathBuf = self.local.wrkdir.clone();
|
||||
self.filetransfer_recv(&file.get_realfile(), wrkdir.as_path(), Some(name));
|
||||
self.update_local_filelist()
|
||||
} else {
|
||||
None
|
||||
}
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, &MSG_KEY_BACKSPACE) => {
|
||||
// Go to previous directory
|
||||
if let Some(d) = self.remote.popd() {
|
||||
self.remote_changedir(d.as_path(), false);
|
||||
}
|
||||
// Reload file list component
|
||||
self.update_remote_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_A) => {
|
||||
// Toggle hidden files
|
||||
self.remote.toggle_hidden_files();
|
||||
// Reload file list component
|
||||
self.update_remote_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_I) => {
|
||||
let file: Option<FsEntry> = self.get_remote_file_entry().cloned();
|
||||
if let Some(file) = file {
|
||||
self.mount_file_info(&file);
|
||||
}
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_L) => {
|
||||
// Reload directory
|
||||
let pwd: PathBuf = self.remote.wrkdir.clone();
|
||||
self.remote_scan(pwd.as_path());
|
||||
// Reload file list component
|
||||
self.update_remote_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_O) => {
|
||||
// Clone entry due to mutable stuff...
|
||||
if self.get_remote_file_entry().is_some() {
|
||||
let fsentry: FsEntry = self.get_remote_file_entry().unwrap().clone();
|
||||
// Check if file
|
||||
if let FsEntry::File(file) = fsentry.clone() {
|
||||
self.log(
|
||||
LogLevel::Info,
|
||||
format!("Opening file \"{}\"...", fsentry.get_abs_path().display())
|
||||
.as_str(),
|
||||
);
|
||||
// Edit file
|
||||
match self.edit_remote_file(&file) {
|
||||
Ok(_) => {
|
||||
// Reload directory
|
||||
let pwd: PathBuf = self.remote.wrkdir.clone();
|
||||
self.remote_scan(pwd.as_path());
|
||||
}
|
||||
Err(err) => self.log_and_alert(LogLevel::Error, err),
|
||||
}
|
||||
}
|
||||
}
|
||||
// Reload file list component
|
||||
self.update_remote_filelist()
|
||||
}
|
||||
(COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_U) => {
|
||||
// Get pwd
|
||||
let path: PathBuf = self.remote.wrkdir.clone();
|
||||
// Go to parent directory
|
||||
if let Some(parent) = path.as_path().parent() {
|
||||
self.remote_changedir(parent, true);
|
||||
}
|
||||
// Reload file list component
|
||||
self.update_remote_filelist()
|
||||
}
|
||||
// -- common explorer keys
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_B)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_B) => {
|
||||
// Show sorting file
|
||||
self.mount_file_sorting();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_C)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_C) => {
|
||||
self.mount_copy();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_D)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_D) => {
|
||||
self.mount_mkdir();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_F)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_F) => {
|
||||
self.mount_find_input();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_G)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_G) => {
|
||||
self.mount_goto();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_H)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_H) => {
|
||||
self.mount_help();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_N)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_N) => {
|
||||
self.mount_newfile();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_Q)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_Q)
|
||||
| (COMPONENT_LOG_BOX, &MSG_KEY_CHAR_Q) => {
|
||||
self.mount_quit();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_R)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_R) => {
|
||||
// Mount rename
|
||||
self.mount_rename();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_S)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_S)
|
||||
| (COMPONENT_EXPLORER_FIND, &MSG_KEY_CHAR_S) => {
|
||||
// Mount save as
|
||||
self.mount_saveas();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_X)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_X) => {
|
||||
// Mount exec
|
||||
self.mount_exec();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_ESC)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_ESC)
|
||||
| (COMPONENT_LOG_BOX, &MSG_KEY_ESC) => {
|
||||
self.mount_disconnect();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_DEL)
|
||||
| (COMPONENT_EXPLORER_LOCAL, &MSG_KEY_CHAR_E)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_DEL)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_CHAR_E)
|
||||
| (COMPONENT_EXPLORER_FIND, &MSG_KEY_DEL)
|
||||
| (COMPONENT_EXPLORER_FIND, &MSG_KEY_CHAR_E) => {
|
||||
self.mount_radio_delete();
|
||||
None
|
||||
}
|
||||
// -- find result explorer
|
||||
(COMPONENT_EXPLORER_FIND, &MSG_KEY_ESC) => {
|
||||
// Umount find
|
||||
self.umount_find();
|
||||
// Finalize find
|
||||
self.finalize_find();
|
||||
None
|
||||
}
|
||||
(COMPONENT_EXPLORER_FIND, Msg::OnSubmit(Payload::Unsigned(idx))) => {
|
||||
// Find changedir
|
||||
self.action_find_changedir(*idx);
|
||||
// Umount find
|
||||
self.umount_find();
|
||||
// Finalize find
|
||||
self.finalize_find();
|
||||
// Reload files
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
(COMPONENT_EXPLORER_FIND, &MSG_KEY_SPACE) => {
|
||||
// Get entry
|
||||
match self.view.get_value(COMPONENT_EXPLORER_FIND) {
|
||||
Some(Payload::Unsigned(idx)) => {
|
||||
self.action_find_transfer(idx, None);
|
||||
// Reload files
|
||||
match self.tab {
|
||||
// NOTE: swapped by purpose
|
||||
FileExplorerTab::FindLocal => self.update_remote_filelist(),
|
||||
FileExplorerTab::FindRemote => self.update_local_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
// -- switch to log
|
||||
(COMPONENT_EXPLORER_LOCAL, &MSG_KEY_TAB)
|
||||
| (COMPONENT_EXPLORER_REMOTE, &MSG_KEY_TAB) => {
|
||||
self.view.active(COMPONENT_LOG_BOX); // Active log box
|
||||
None
|
||||
}
|
||||
// -- Log box
|
||||
(COMPONENT_LOG_BOX, &MSG_KEY_TAB) => {
|
||||
self.view.blur(); // Blur log box
|
||||
None
|
||||
}
|
||||
// -- copy popup
|
||||
(COMPONENT_INPUT_COPY, &MSG_KEY_ESC) => {
|
||||
self.umount_copy();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_COPY, Msg::OnSubmit(Payload::Text(input))) => {
|
||||
// Copy file
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.action_local_copy(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_remote_copy(input.to_string()),
|
||||
_ => panic!("Found tab doesn't support COPY"),
|
||||
}
|
||||
self.umount_copy();
|
||||
// Reload files
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
// -- exec popup
|
||||
(COMPONENT_INPUT_EXEC, &MSG_KEY_ESC) => {
|
||||
self.umount_exec();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_EXEC, Msg::OnSubmit(Payload::Text(input))) => {
|
||||
// Exex command
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.action_local_exec(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_remote_exec(input.to_string()),
|
||||
_ => panic!("Found tab doesn't support EXEC"),
|
||||
}
|
||||
self.umount_exec();
|
||||
// Reload files
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
// -- find popup
|
||||
(COMPONENT_INPUT_FIND, &MSG_KEY_ESC) => {
|
||||
self.umount_find_input();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_FIND, Msg::OnSubmit(Payload::Text(input))) => {
|
||||
self.umount_find_input();
|
||||
// Find
|
||||
let res: Result<Vec<FsEntry>, String> = match self.tab {
|
||||
FileExplorerTab::Local => self.action_local_find(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_remote_find(input.to_string()),
|
||||
_ => panic!("Trying to search for files, while already in a find result"),
|
||||
};
|
||||
// Match result
|
||||
match res {
|
||||
Err(err) => {
|
||||
// Mount error
|
||||
self.mount_error(err.as_str());
|
||||
}
|
||||
Ok(files) => {
|
||||
// Create explorer and load files
|
||||
let mut explorer = Self::build_found_explorer();
|
||||
explorer.set_files(files);
|
||||
self.found = Some(explorer);
|
||||
// Mount result widget
|
||||
self.mount_find(input);
|
||||
self.update_find_list();
|
||||
// Initialize tab
|
||||
self.tab = match self.tab {
|
||||
FileExplorerTab::Local => FileExplorerTab::FindLocal,
|
||||
FileExplorerTab::Remote => FileExplorerTab::FindRemote,
|
||||
_ => FileExplorerTab::FindLocal,
|
||||
};
|
||||
}
|
||||
}
|
||||
None
|
||||
}
|
||||
// -- goto popup
|
||||
(COMPONENT_INPUT_GOTO, &MSG_KEY_ESC) => {
|
||||
self.umount_goto();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_GOTO, Msg::OnSubmit(Payload::Text(input))) => {
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.action_change_local_dir(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_change_remote_dir(input.to_string()),
|
||||
_ => panic!("Found tab doesn't support GOTO"),
|
||||
}
|
||||
// Umount
|
||||
self.umount_goto();
|
||||
// Reload files
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
// -- make directory
|
||||
(COMPONENT_INPUT_MKDIR, &MSG_KEY_ESC) => {
|
||||
self.umount_mkdir();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_MKDIR, Msg::OnSubmit(Payload::Text(input))) => {
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.action_local_mkdir(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_remote_mkdir(input.to_string()),
|
||||
_ => panic!("Found tab doesn't support MKDIR"),
|
||||
}
|
||||
self.umount_mkdir();
|
||||
// Reload files
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
// -- new file
|
||||
(COMPONENT_INPUT_NEWFILE, &MSG_KEY_ESC) => {
|
||||
self.umount_newfile();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_NEWFILE, Msg::OnSubmit(Payload::Text(input))) => {
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.action_local_newfile(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_remote_newfile(input.to_string()),
|
||||
_ => panic!("Found tab doesn't support NEWFILE"),
|
||||
}
|
||||
self.umount_newfile();
|
||||
// Reload files
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
// -- rename
|
||||
(COMPONENT_INPUT_RENAME, &MSG_KEY_ESC) => {
|
||||
self.umount_rename();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_RENAME, Msg::OnSubmit(Payload::Text(input))) => {
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.action_local_rename(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_remote_rename(input.to_string()),
|
||||
_ => panic!("Found tab doesn't support RENAME"),
|
||||
}
|
||||
self.umount_rename();
|
||||
// Reload files
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
// -- save as
|
||||
(COMPONENT_INPUT_SAVEAS, &MSG_KEY_ESC) => {
|
||||
self.umount_saveas();
|
||||
None
|
||||
}
|
||||
(COMPONENT_INPUT_SAVEAS, Msg::OnSubmit(Payload::Text(input))) => {
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.action_local_saveas(input.to_string()),
|
||||
FileExplorerTab::Remote => self.action_remote_saveas(input.to_string()),
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::FindRemote => {
|
||||
// Get entry
|
||||
if let Some(Payload::Unsigned(idx)) =
|
||||
self.view.get_value(COMPONENT_EXPLORER_FIND)
|
||||
{
|
||||
self.action_find_transfer(idx, Some(input.to_string()));
|
||||
}
|
||||
}
|
||||
}
|
||||
self.umount_saveas();
|
||||
// Reload files
|
||||
match self.tab {
|
||||
// NOTE: Swapped is intentional
|
||||
FileExplorerTab::Local => self.update_remote_filelist(),
|
||||
FileExplorerTab::Remote => self.update_local_filelist(),
|
||||
FileExplorerTab::FindLocal => self.update_remote_filelist(),
|
||||
FileExplorerTab::FindRemote => self.update_local_filelist(),
|
||||
}
|
||||
}
|
||||
// -- fileinfo
|
||||
(COMPONENT_LIST_FILEINFO, &MSG_KEY_ENTER)
|
||||
| (COMPONENT_LIST_FILEINFO, &MSG_KEY_ESC) => {
|
||||
self.umount_file_info();
|
||||
None
|
||||
}
|
||||
// -- delete
|
||||
(COMPONENT_RADIO_DELETE, &MSG_KEY_ESC)
|
||||
| (COMPONENT_RADIO_DELETE, Msg::OnSubmit(Payload::Unsigned(1))) => {
|
||||
self.umount_radio_delete();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_DELETE, Msg::OnSubmit(Payload::Unsigned(0))) => {
|
||||
// Choice is 'YES'
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.action_local_delete(),
|
||||
FileExplorerTab::Remote => self.action_remote_delete(),
|
||||
FileExplorerTab::FindLocal | FileExplorerTab::FindRemote => {
|
||||
// Get entry
|
||||
if let Some(Payload::Unsigned(idx)) =
|
||||
self.view.get_value(COMPONENT_EXPLORER_FIND)
|
||||
{
|
||||
self.action_find_delete(idx);
|
||||
// Reload entries
|
||||
self.found.as_mut().unwrap().del_entry(idx);
|
||||
self.update_find_list();
|
||||
}
|
||||
}
|
||||
}
|
||||
self.umount_radio_delete();
|
||||
// Reload files
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
FileExplorerTab::FindLocal => self.update_local_filelist(),
|
||||
FileExplorerTab::FindRemote => self.update_remote_filelist(),
|
||||
}
|
||||
}
|
||||
// -- disconnect
|
||||
(COMPONENT_RADIO_DISCONNECT, &MSG_KEY_ESC)
|
||||
| (COMPONENT_RADIO_DISCONNECT, Msg::OnSubmit(Payload::Unsigned(1))) => {
|
||||
self.umount_disconnect();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_DISCONNECT, Msg::OnSubmit(Payload::Unsigned(0))) => {
|
||||
self.disconnect();
|
||||
self.umount_disconnect();
|
||||
None
|
||||
}
|
||||
// -- quit
|
||||
(COMPONENT_RADIO_QUIT, &MSG_KEY_ESC)
|
||||
| (COMPONENT_RADIO_QUIT, Msg::OnSubmit(Payload::Unsigned(1))) => {
|
||||
self.umount_quit();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_QUIT, Msg::OnSubmit(Payload::Unsigned(0))) => {
|
||||
self.disconnect_and_quit();
|
||||
self.umount_quit();
|
||||
None
|
||||
}
|
||||
// -- sorting
|
||||
(COMPONENT_RADIO_SORTING, &MSG_KEY_ESC) => {
|
||||
self.umount_file_sorting();
|
||||
None
|
||||
}
|
||||
(COMPONENT_RADIO_SORTING, Msg::OnSubmit(Payload::Unsigned(mode))) => {
|
||||
// Get sorting mode
|
||||
let sorting: FileSorting = match mode {
|
||||
1 => FileSorting::ByModifyTime,
|
||||
2 => FileSorting::ByCreationTime,
|
||||
3 => FileSorting::BySize,
|
||||
_ => FileSorting::ByName,
|
||||
};
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.local.sort_by(sorting),
|
||||
FileExplorerTab::Remote => self.remote.sort_by(sorting),
|
||||
_ => panic!("Found result doesn't support SORTING"),
|
||||
}
|
||||
self.umount_file_sorting();
|
||||
// Reload files
|
||||
match self.tab {
|
||||
FileExplorerTab::Local => self.update_local_filelist(),
|
||||
FileExplorerTab::Remote => self.update_remote_filelist(),
|
||||
_ => None,
|
||||
}
|
||||
}
|
||||
// -- error
|
||||
(COMPONENT_TEXT_ERROR, &MSG_KEY_ESC) | (COMPONENT_TEXT_ERROR, &MSG_KEY_ENTER) => {
|
||||
self.umount_error();
|
||||
None
|
||||
}
|
||||
// -- fatal
|
||||
(COMPONENT_TEXT_FATAL, &MSG_KEY_ESC) | (COMPONENT_TEXT_FATAL, &MSG_KEY_ENTER) => {
|
||||
self.exit_reason = Some(super::ExitReason::Disconnect);
|
||||
None
|
||||
}
|
||||
// -- help
|
||||
(COMPONENT_TEXT_HELP, &MSG_KEY_ESC) | (COMPONENT_TEXT_HELP, &MSG_KEY_ENTER) => {
|
||||
self.umount_help();
|
||||
None
|
||||
}
|
||||
// -- progress bar
|
||||
(COMPONENT_PROGRESS_BAR, &MSG_KEY_CTRL_C) => {
|
||||
// Set transfer aborted to True
|
||||
self.transfer.aborted = true;
|
||||
None
|
||||
}
|
||||
// -- fallback
|
||||
(_, _) => None, // Nothing to do
|
||||
},
|
||||
}
|
||||
}
|
||||
|
||||
/// ### update_local_filelist
|
||||
///
|
||||
/// Update local file list
|
||||
pub(super) fn update_local_filelist(&mut self) -> Option<(String, Msg)> {
|
||||
match self
|
||||
.view
|
||||
.get_props(super::COMPONENT_EXPLORER_LOCAL)
|
||||
.as_mut()
|
||||
{
|
||||
Some(props) => {
|
||||
// Get width
|
||||
let width: usize = self
|
||||
.context
|
||||
.as_ref()
|
||||
.unwrap()
|
||||
.store
|
||||
.get_unsigned(super::STORAGE_EXPLORER_WIDTH)
|
||||
.unwrap_or(256);
|
||||
let hostname: String = match hostname::get() {
|
||||
Ok(h) => {
|
||||
let hostname: String = h.as_os_str().to_string_lossy().to_string();
|
||||
let tokens: Vec<&str> = hostname.split('.').collect();
|
||||
String::from(*tokens.get(0).unwrap_or(&"localhost"))
|
||||
}
|
||||
Err(_) => String::from("localhost"),
|
||||
};
|
||||
let hostname: String = format!(
|
||||
"{}:{} ",
|
||||
hostname,
|
||||
FileTransferActivity::elide_wrkdir_path(
|
||||
self.local.wrkdir.as_path(),
|
||||
hostname.as_str(),
|
||||
width
|
||||
)
|
||||
.display()
|
||||
);
|
||||
let files: Vec<TextSpan> = self
|
||||
.local
|
||||
.iter_files()
|
||||
.map(|x: &FsEntry| TextSpan::from(self.local.fmt_file(x)))
|
||||
.collect();
|
||||
// Update
|
||||
let props = props
|
||||
.with_texts(TextParts::new(Some(hostname), Some(files)))
|
||||
.build();
|
||||
// Update
|
||||
self.view.update(super::COMPONENT_EXPLORER_LOCAL, props)
|
||||
}
|
||||
None => None,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### update_remote_filelist
|
||||
///
|
||||
/// Update remote file list
|
||||
pub(super) fn update_remote_filelist(&mut self) -> Option<(String, Msg)> {
|
||||
match self
|
||||
.view
|
||||
.get_props(super::COMPONENT_EXPLORER_REMOTE)
|
||||
.as_mut()
|
||||
{
|
||||
Some(props) => {
|
||||
// Get width
|
||||
let width: usize = self
|
||||
.context
|
||||
.as_ref()
|
||||
.unwrap()
|
||||
.store
|
||||
.get_unsigned(super::STORAGE_EXPLORER_WIDTH)
|
||||
.unwrap_or(256);
|
||||
let params = self.context.as_ref().unwrap().ft_params.as_ref().unwrap();
|
||||
let hostname: String = format!(
|
||||
"{}:{} ",
|
||||
params.address,
|
||||
FileTransferActivity::elide_wrkdir_path(
|
||||
self.remote.wrkdir.as_path(),
|
||||
params.address.as_str(),
|
||||
width
|
||||
)
|
||||
.display()
|
||||
);
|
||||
let files: Vec<TextSpan> = self
|
||||
.remote
|
||||
.iter_files()
|
||||
.map(|x: &FsEntry| TextSpan::from(self.remote.fmt_file(x)))
|
||||
.collect();
|
||||
// Update
|
||||
let props = props
|
||||
.with_texts(TextParts::new(Some(hostname), Some(files)))
|
||||
.build();
|
||||
self.view.update(super::COMPONENT_EXPLORER_REMOTE, props)
|
||||
}
|
||||
None => None,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### update_logbox
|
||||
///
|
||||
/// Update log box
|
||||
pub(super) fn update_logbox(&mut self) -> Option<(String, Msg)> {
|
||||
match self.view.get_props(super::COMPONENT_LOG_BOX).as_mut() {
|
||||
Some(props) => {
|
||||
// Get width
|
||||
let width: usize = self
|
||||
.context
|
||||
.as_ref()
|
||||
.unwrap()
|
||||
.store
|
||||
.get_unsigned(super::STORAGE_LOGBOX_WIDTH)
|
||||
.unwrap_or(256);
|
||||
// Make log entries
|
||||
let mut table: TableBuilder = TableBuilder::default();
|
||||
for (idx, record) in self.log_records.iter().enumerate() {
|
||||
// Split rows by width NOTE: -37 'cause log prefix -3 cause of log line cursor
|
||||
let record_rows = textwrap::wrap(record.msg.as_str(), (width as usize) - 40);
|
||||
// Add row if not first row
|
||||
if idx > 0 {
|
||||
table.add_row();
|
||||
}
|
||||
let fg = match record.level {
|
||||
LogLevel::Error => Color::Red,
|
||||
LogLevel::Warn => Color::Yellow,
|
||||
LogLevel::Info => Color::Green,
|
||||
};
|
||||
for (idx, row) in record_rows.iter().enumerate() {
|
||||
match idx {
|
||||
0 => {
|
||||
// First row
|
||||
table
|
||||
.add_col(TextSpan::from(format!(
|
||||
"{}",
|
||||
record.time.format("%Y-%m-%dT%H:%M:%S%Z")
|
||||
)))
|
||||
.add_col(TextSpan::from(" ["))
|
||||
.add_col(
|
||||
TextSpanBuilder::new(
|
||||
format!(
|
||||
"{:5}",
|
||||
match record.level {
|
||||
LogLevel::Error => "ERROR",
|
||||
LogLevel::Warn => "WARN",
|
||||
LogLevel::Info => "INFO",
|
||||
}
|
||||
)
|
||||
.as_str(),
|
||||
)
|
||||
.with_foreground(fg)
|
||||
.build(),
|
||||
)
|
||||
.add_col(TextSpan::from("]: "))
|
||||
.add_col(TextSpan::from(row.as_ref()));
|
||||
}
|
||||
_ => {
|
||||
table.add_col(TextSpan::from(textwrap::indent(
|
||||
row.as_ref(),
|
||||
" ",
|
||||
)));
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
let table = table.build();
|
||||
let props = props
|
||||
.with_texts(TextParts::table(Some(String::from("Log")), table))
|
||||
.build();
|
||||
self.view.update(super::COMPONENT_LOG_BOX, props)
|
||||
}
|
||||
None => None,
|
||||
}
|
||||
}
|
||||
|
||||
pub(super) fn update_progress_bar(&mut self, text: String) -> Option<(String, Msg)> {
|
||||
match self.view.get_props(COMPONENT_PROGRESS_BAR).as_mut() {
|
||||
Some(props) => {
|
||||
// Calculate ETA
|
||||
let elapsed_secs: u64 = self.transfer.started.elapsed().as_secs();
|
||||
let eta: String = match self.transfer.progress as u64 {
|
||||
0 => String::from("--:--"), // NOTE: would divide by 0 :D
|
||||
_ => {
|
||||
let eta: u64 =
|
||||
((elapsed_secs * 100) / (self.transfer.progress as u64)) - elapsed_secs;
|
||||
format!("{:0width$}:{:0width$}", (eta / 60), (eta % 60), width = 2)
|
||||
}
|
||||
};
|
||||
// Calculate bytes/s
|
||||
let label = format!(
|
||||
"{:.2}% - ETA {} ({}/s)",
|
||||
self.transfer.progress,
|
||||
eta,
|
||||
ByteSize(self.transfer.bytes_per_second())
|
||||
);
|
||||
let props = props
|
||||
.with_texts(TextParts::new(
|
||||
Some(text),
|
||||
Some(vec![TextSpan::from(label)]),
|
||||
))
|
||||
.with_value(PropValue::Float(self.transfer.progress / 100.0))
|
||||
.build();
|
||||
self.view.update(COMPONENT_PROGRESS_BAR, props)
|
||||
}
|
||||
None => None,
|
||||
}
|
||||
}
|
||||
|
||||
/// ### finalize_find
|
||||
///
|
||||
/// Finalize find process
|
||||
fn finalize_find(&mut self) {
|
||||
// Set found to none
|
||||
self.found = None;
|
||||
// Restore tab
|
||||
self.tab = match self.tab {
|
||||
FileExplorerTab::FindLocal => FileExplorerTab::Local,
|
||||
FileExplorerTab::FindRemote => FileExplorerTab::Remote,
|
||||
_ => FileExplorerTab::Local,
|
||||
};
|
||||
}
|
||||
|
||||
fn update_find_list(&mut self) -> Option<(String, Msg)> {
|
||||
match self.view.get_props(COMPONENT_EXPLORER_FIND).as_mut() {
|
||||
None => None,
|
||||
Some(props) => {
|
||||
let props = props.build();
|
||||
let title: String = props.texts.title.clone().unwrap_or_default();
|
||||
let mut props = PropsBuilder::from(props);
|
||||
// Prepare files
|
||||
let file_texts: Vec<TextSpan> = self
|
||||
.found
|
||||
.as_ref()
|
||||
.unwrap()
|
||||
.iter_files()
|
||||
.map(|x: &FsEntry| TextSpan::from(self.found.as_ref().unwrap().fmt_file(x)))
|
||||
.collect();
|
||||
let props = props
|
||||
.with_texts(TextParts::new(Some(title), Some(file_texts)))
|
||||
.build();
|
||||
self.view.update(COMPONENT_EXPLORER_FIND, props)
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
/// ### elide_wrkdir_path
|
||||
///
|
||||
/// Elide working directory path if longer than width + host.len
|
||||
/// In this case, the path is formatted to {ANCESTOR[0]}/.../{PARENT[0]}/{BASENAME}
|
||||
fn elide_wrkdir_path(wrkdir: &Path, host: &str, width: usize) -> PathBuf {
|
||||
let fmt_path: String = format!("{}", wrkdir.display());
|
||||
// NOTE: +5 is const
|
||||
match fmt_path.len() + host.len() + 5 > width {
|
||||
false => PathBuf::from(wrkdir),
|
||||
true => {
|
||||
// Elide
|
||||
let ancestors_len: usize = wrkdir.ancestors().count();
|
||||
let mut ancestors = wrkdir.ancestors();
|
||||
let mut elided_path: PathBuf = PathBuf::new();
|
||||
// If ancestors_len's size is bigger than 2, push count - 2
|
||||
if ancestors_len > 2 {
|
||||
elided_path.push(ancestors.nth(ancestors_len - 2).unwrap());
|
||||
}
|
||||
// If ancestors_len is bigger than 3, push '...' and parent too
|
||||
if ancestors_len > 3 {
|
||||
elided_path.push("...");
|
||||
if let Some(parent) = wrkdir.ancestors().nth(1) {
|
||||
elided_path.push(parent.file_name().unwrap());
|
||||
}
|
||||
}
|
||||
// Push file_name
|
||||
if let Some(name) = wrkdir.file_name() {
|
||||
elided_path.push(name);
|
||||
}
|
||||
elided_path
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||